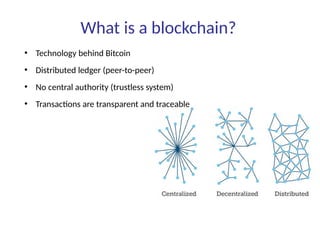
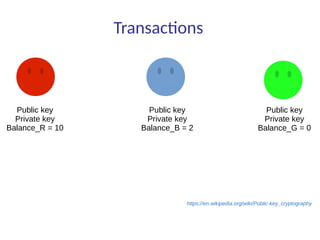
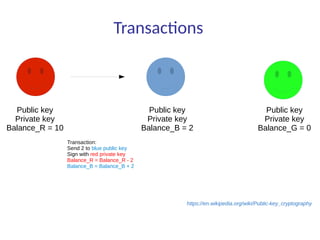
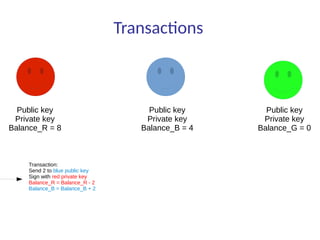
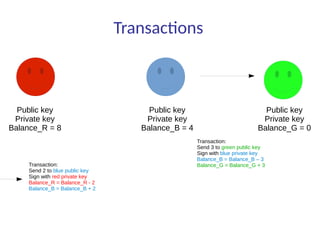
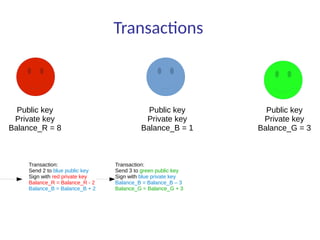
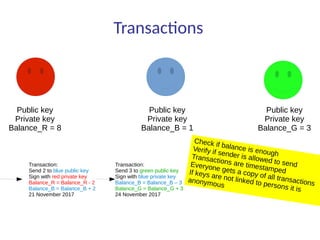
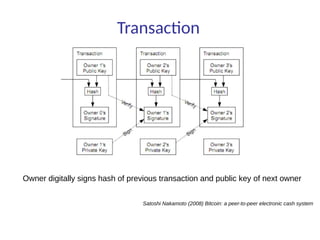
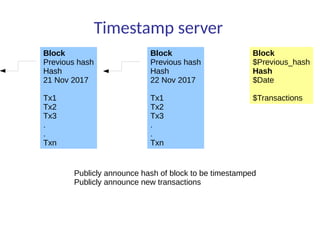
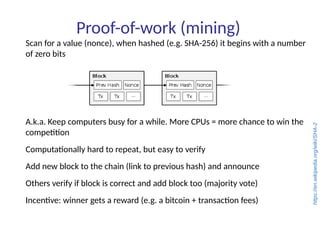
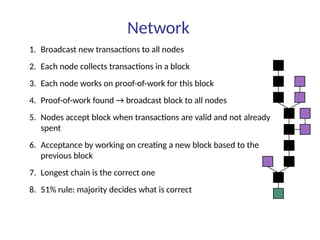
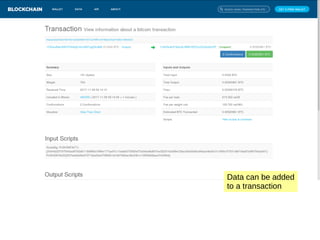
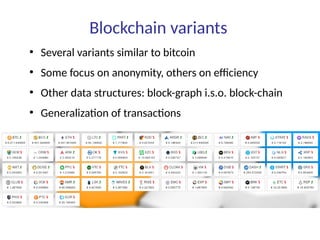
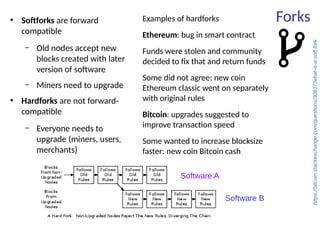
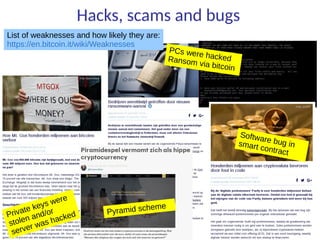
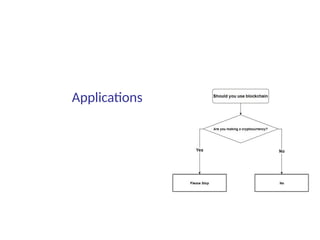
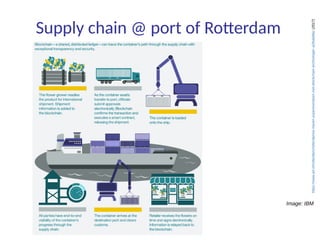
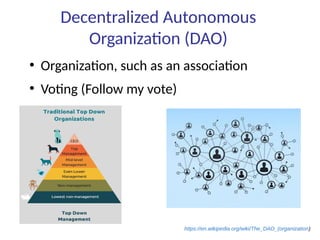
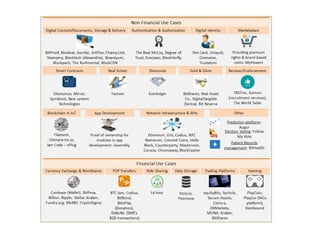
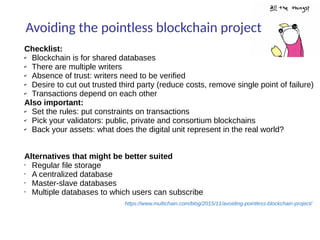
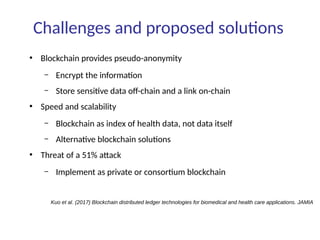
This document summarizes key aspects of blockchain technology. It begins by explaining what a blockchain is and how transactions work, using public/private keys to securely transfer balances. It describes how blocks of transactions are timestamped and added to the chain through a proof-of-work process. Examples of blockchain applications include supply chain management, solar energy sharing, and decentralized autonomous organizations. The document cautions that blockchain may not always be the best solution and provides tips to avoid pointless blockchain projects. It also discusses challenges like scalability that proposed solutions are aiming to address.