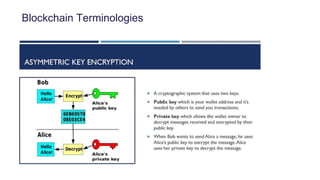
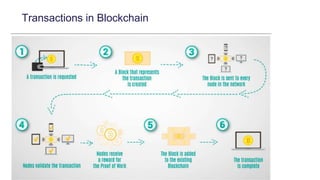
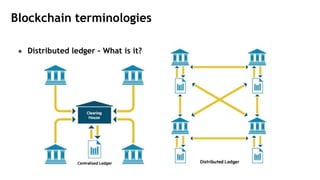
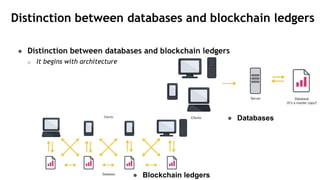
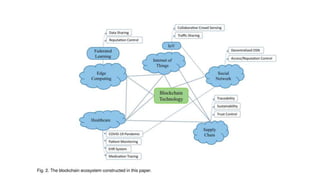
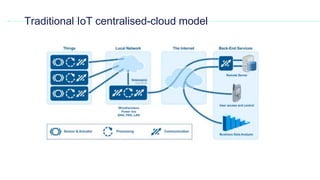
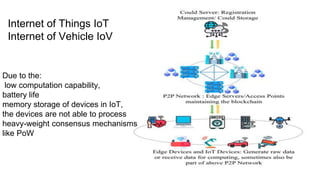
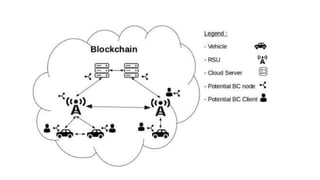
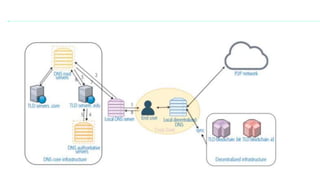
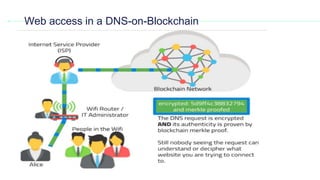
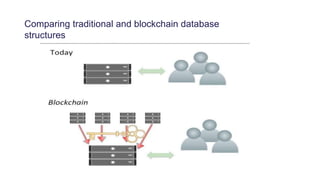
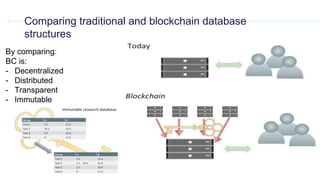
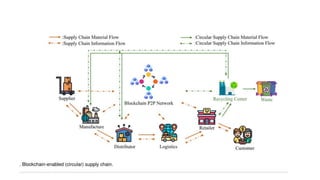
This document provides an overview of blockchain technology and its applications. It begins with an introduction to blockchain and how it works. It then discusses the advantages of blockchain over traditional technologies, including its trustless, confidential, and robust nature. Various consensus mechanisms are explained, including proof of work and proof of stake. Applications of blockchain in areas like IoT, DNS, data storage, healthcare and supply chains are covered. Weaknesses of blockchain like scalability issues are also outlined. The document concludes with a discussion of lowering costs to promote adoption and addressing security challenges from external attacks.

































![References
[1] Dylan Rafferty, Kevin Curran, “The Role of Blockchain in Cyber Security”, Semiconductor
Science and Information Devices, VOL. 3, NO. 1, (2021).
[2] Xaio Li, Weili Wu, “Recent Advances of Blockchain and its Applications” (2022).](https://image.slidesharecdn.com/blockchainadvancesitsapplications-230409085955-9a4ef549/85/Blockchain-Advances-its-Applications-pptx-79-320.jpg)

