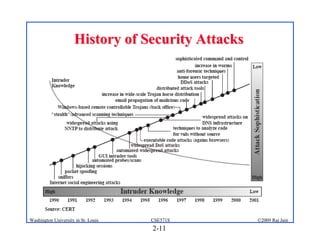
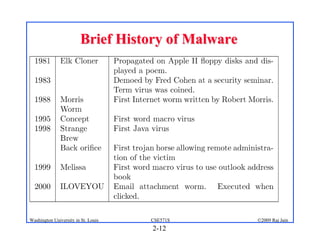
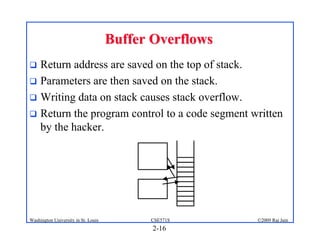
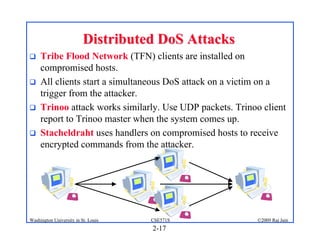
This document provides an overview of key concepts in network security. It discusses security components like confidentiality, integrity and availability. It also covers common threats like disclosure, alteration and denial of access. The document outlines elements of a security policy and different types of attacks and malware. It provides a brief history of security incidents and describes various security mechanisms used to enforce policies like encryption, access control and digital signatures.