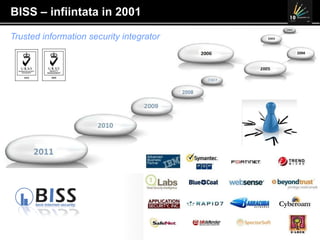
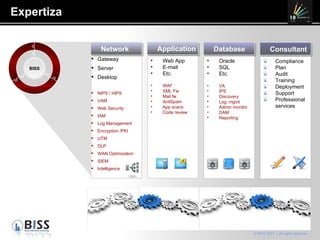
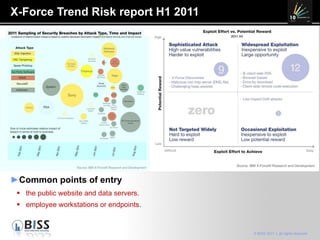
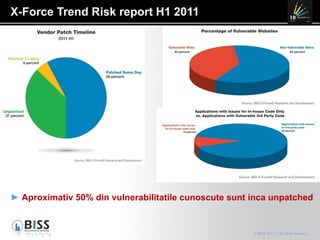
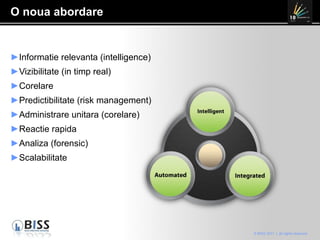
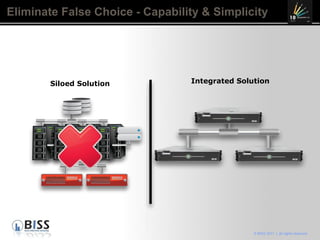
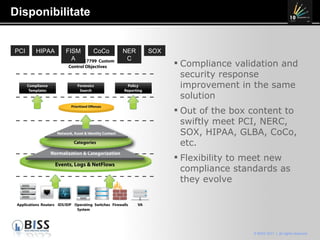
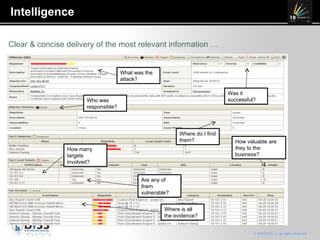
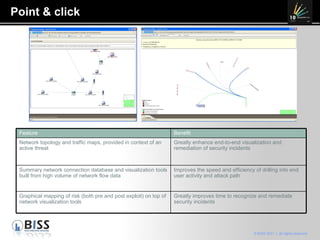
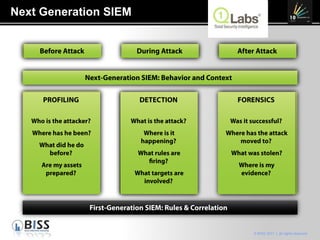
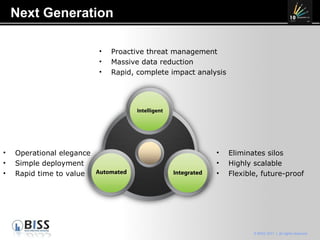
The document discusses the 10 year anniversary of BISS, an IT security company in Romania. It provides an overview of BISS's services and expertise in areas like firewalls, encryption, vulnerability management and compliance. It also discusses the growing need for security due to factors like increasing network complexity, rapidly changing technologies, and a large number of unpatched vulnerabilities. Common security threats include attacks on websites, employee devices, and databases. The document promotes BISS's integrated security solutions and intelligence-driven approach to help customers address security challenges.








![Sample Slide Bullet Points The text demonstrates how your own text will look when you replace the placeholder with your own text. This is a placeholder text. This text can be replaced with your own text. If you don’t want to use the style and size of the fonts as used in this placeholder it is possible to replace it by selecting different options. For replacing the placeholder text you need to click on the placeholder text and insert your own text. The text that you insert will retain the same style and format as the placeholder text. MULŢUMESC Bogdan Toporan │ BISS [email_address] www.biss.ro 1.11.’11](https://image.slidesharecdn.com/biss-11nov2011-111116083456-phpapp02/85/BISS-11nov2011-25-320.jpg)