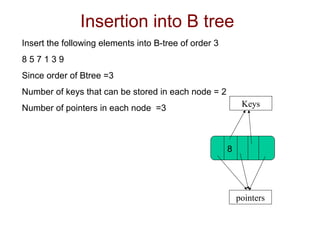
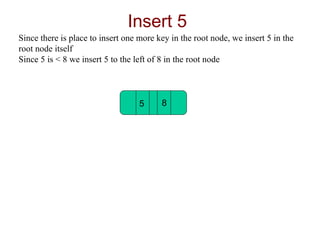
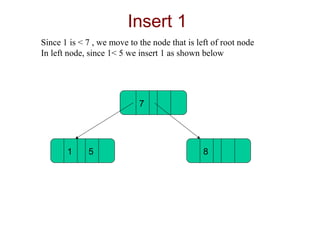
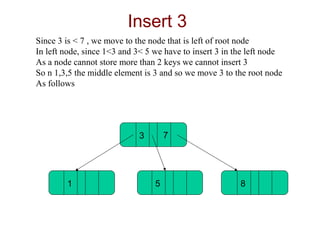
B-trees are used for indexing and have a specified order that determines the maximum number of keys per node. The document demonstrates inserting elements into an empty B-tree of order 3, showing how nodes split as they exceed the maximum 2 keys per node, with the splitting element moving up the tree. Elements are inserted into nodes based on being less than or greater than splitting keys, maintaining the binary search tree property.