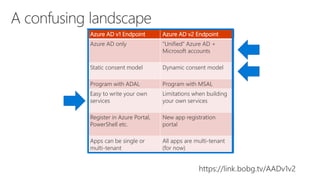
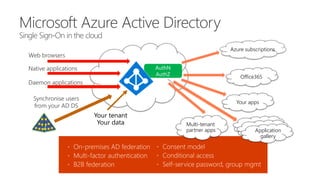
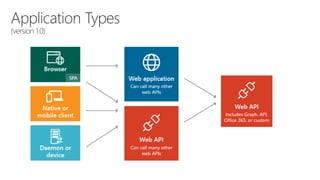
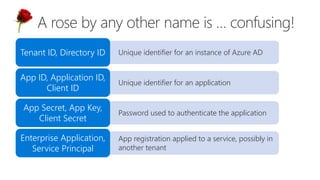
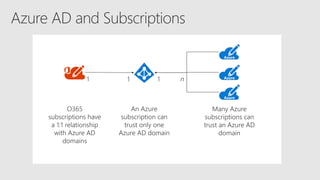
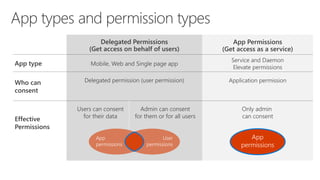
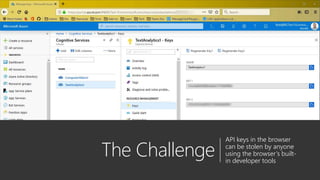
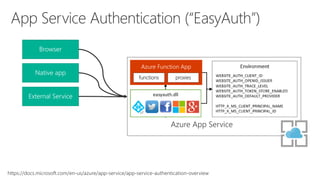
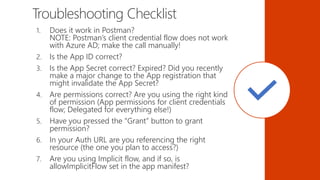
The document serves as a comprehensive troubleshooting checklist for securely handling API keys and integrating with Azure services like Azure Active Directory and Microsoft Graph API. It outlines key concepts, common confusions, and various authentication flows, along with best practices for app registration and permission settings. Additionally, it provides links to sample code and documentation to assist users in understanding and implementing these services effectively.