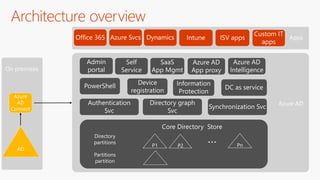
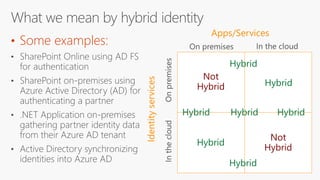
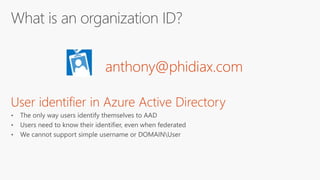
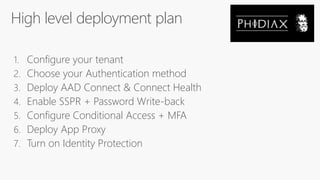
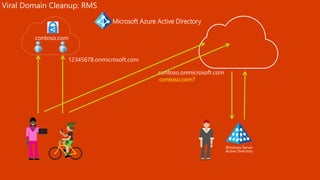
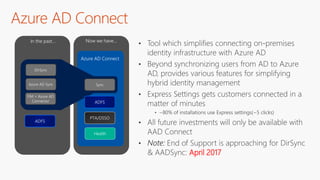
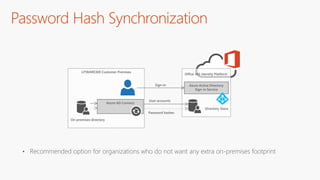
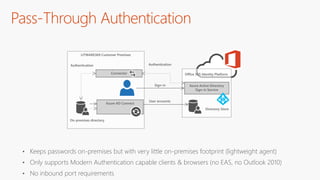
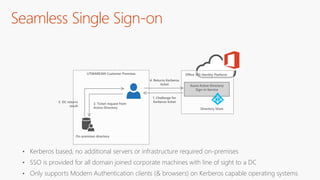
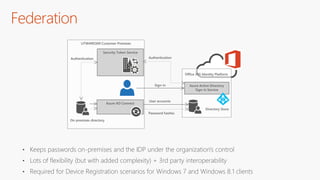
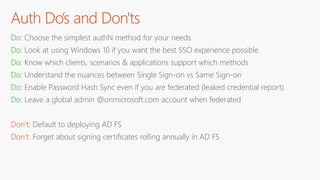
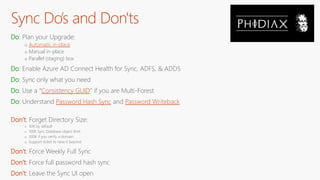
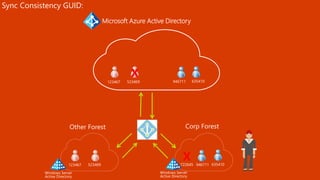
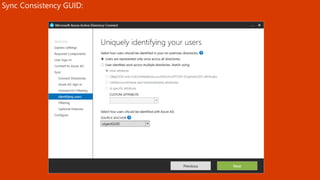
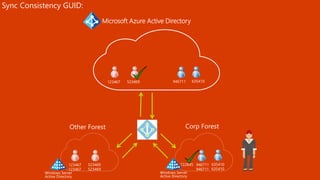
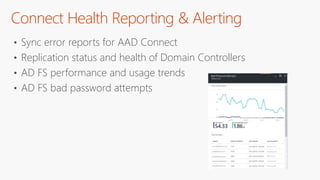
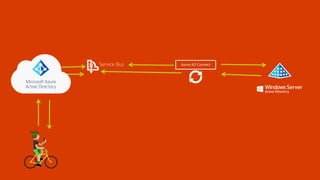
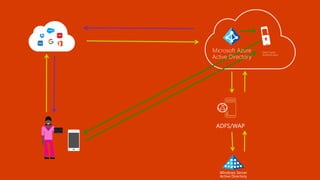
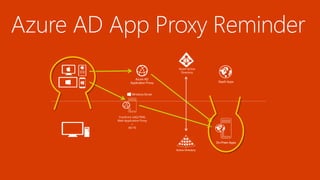
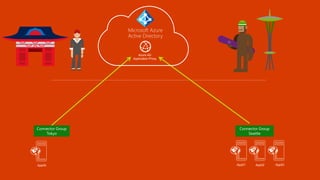
The document outlines a comprehensive guide for deploying Azure Active Directory (Azure AD), covering essential topics such as deployment strategies, authentication options, and critical lessons learned. It includes practical do's and don'ts for tenant configuration, security measures, and application management, emphasizing the importance of planning and monitoring. Key features discussed involve multi-factor authentication, password management, and identity protection to enhance user experience and security in cloud environments.