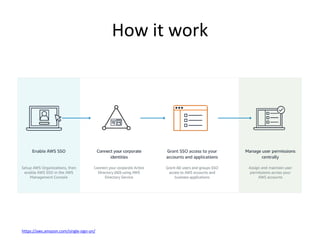
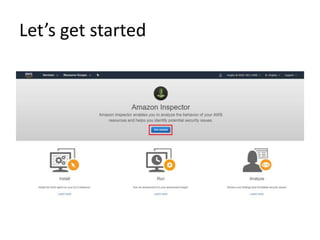
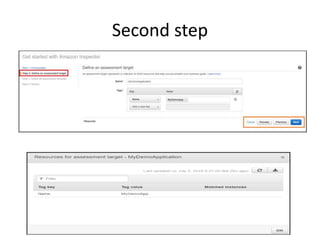
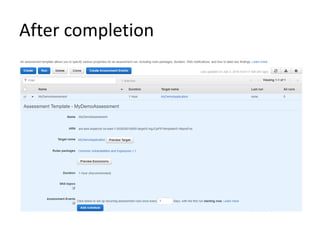
AWS SSO allows users to access multiple AWS accounts and applications using a single set of corporate credentials. It enables centralized management of user access and permissions. AWS Inspector is an automated security assessment service that helps increase security by scanning applications and services and generating detailed reports on vulnerabilities and best practices. It streamlines compliance, enforcement of standards, and integration with other AWS services.