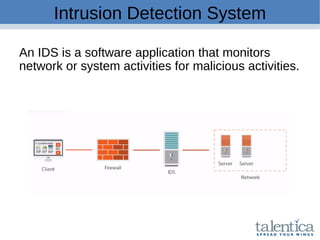
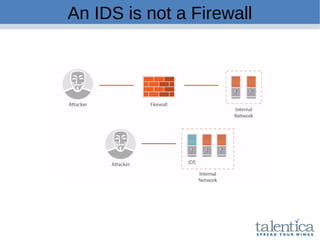
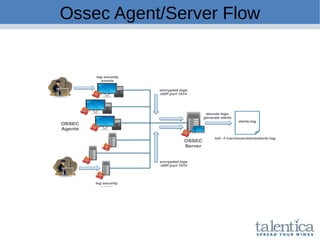
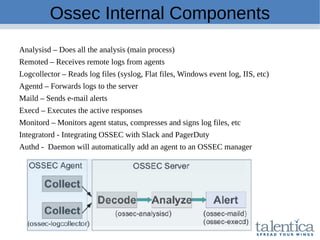
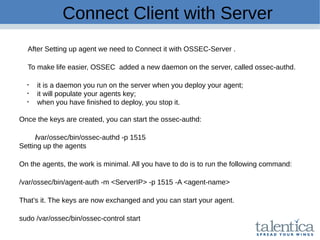
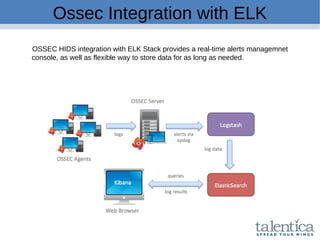
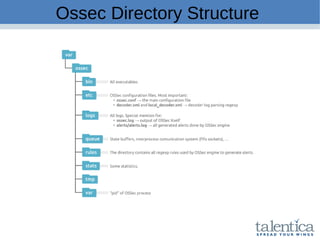
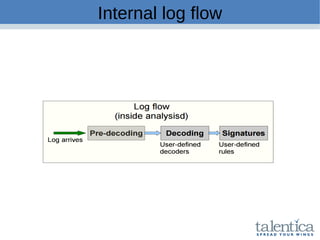
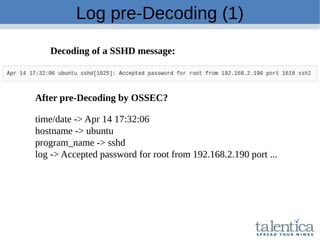
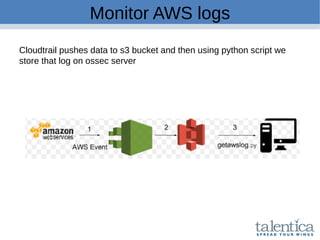
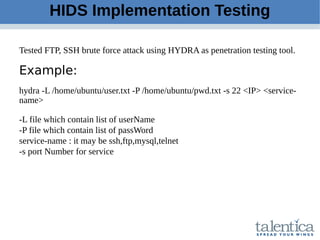
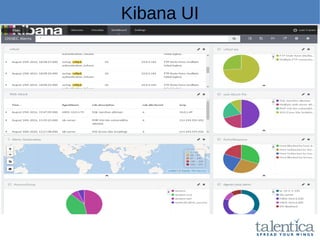
This document discusses securing AWS with a host-based intrusion detection system (HIDS) using OSSEC. It provides an overview of what an IDS is and the differences between network-based (NIDS) and host-based (HIDS) systems. OSSEC is introduced as an open-source HIDS that monitors logs, files, and processes for anomalies. The document outlines how to install and configure OSSEC servers and agents, and how OSSEC integrates with tools like Elasticsearch, Kibana, and Slack for log management and alerting. It also provides examples of how OSSEC can help with PCI compliance by detecting intrusions and policy violations.