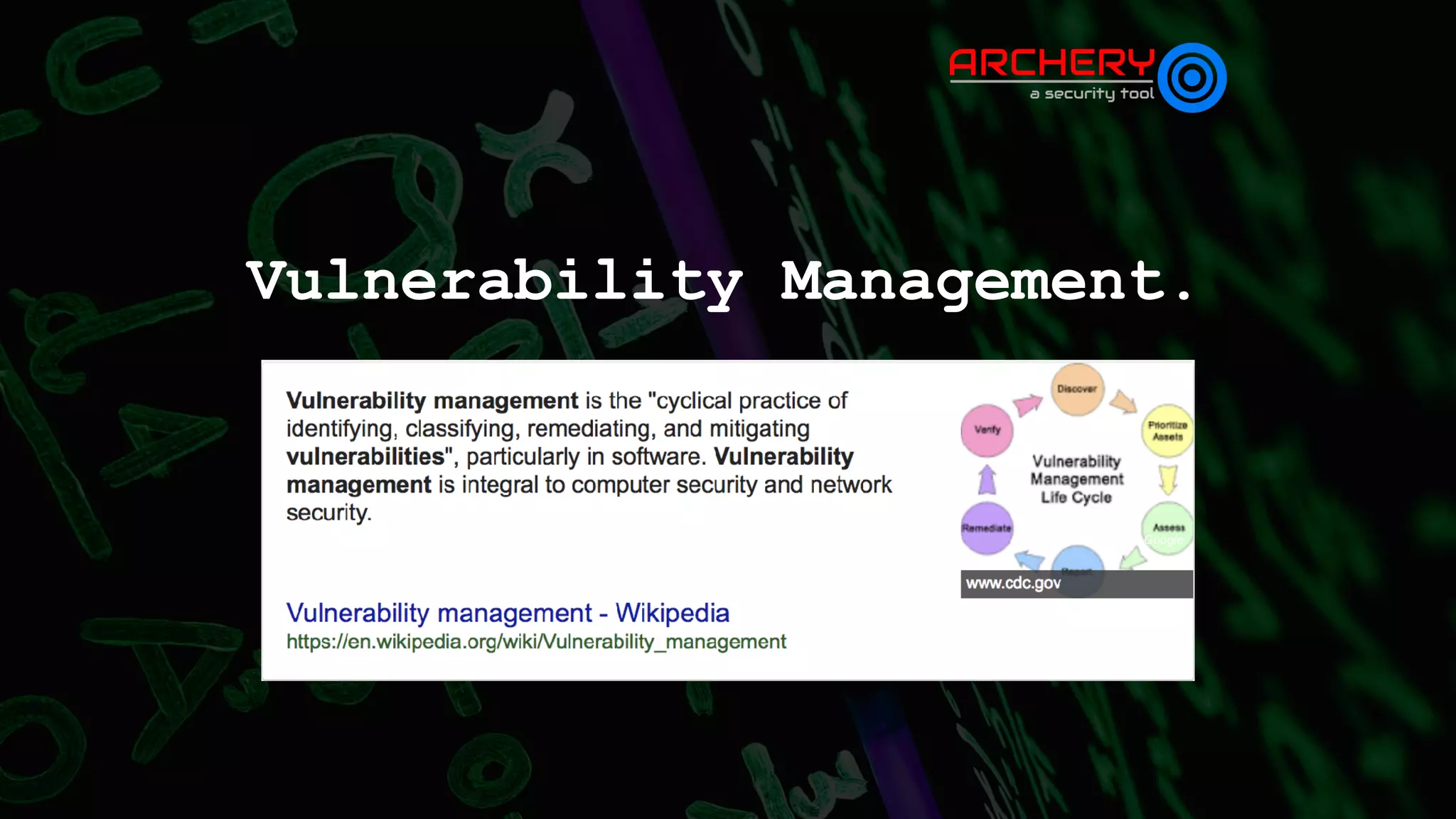
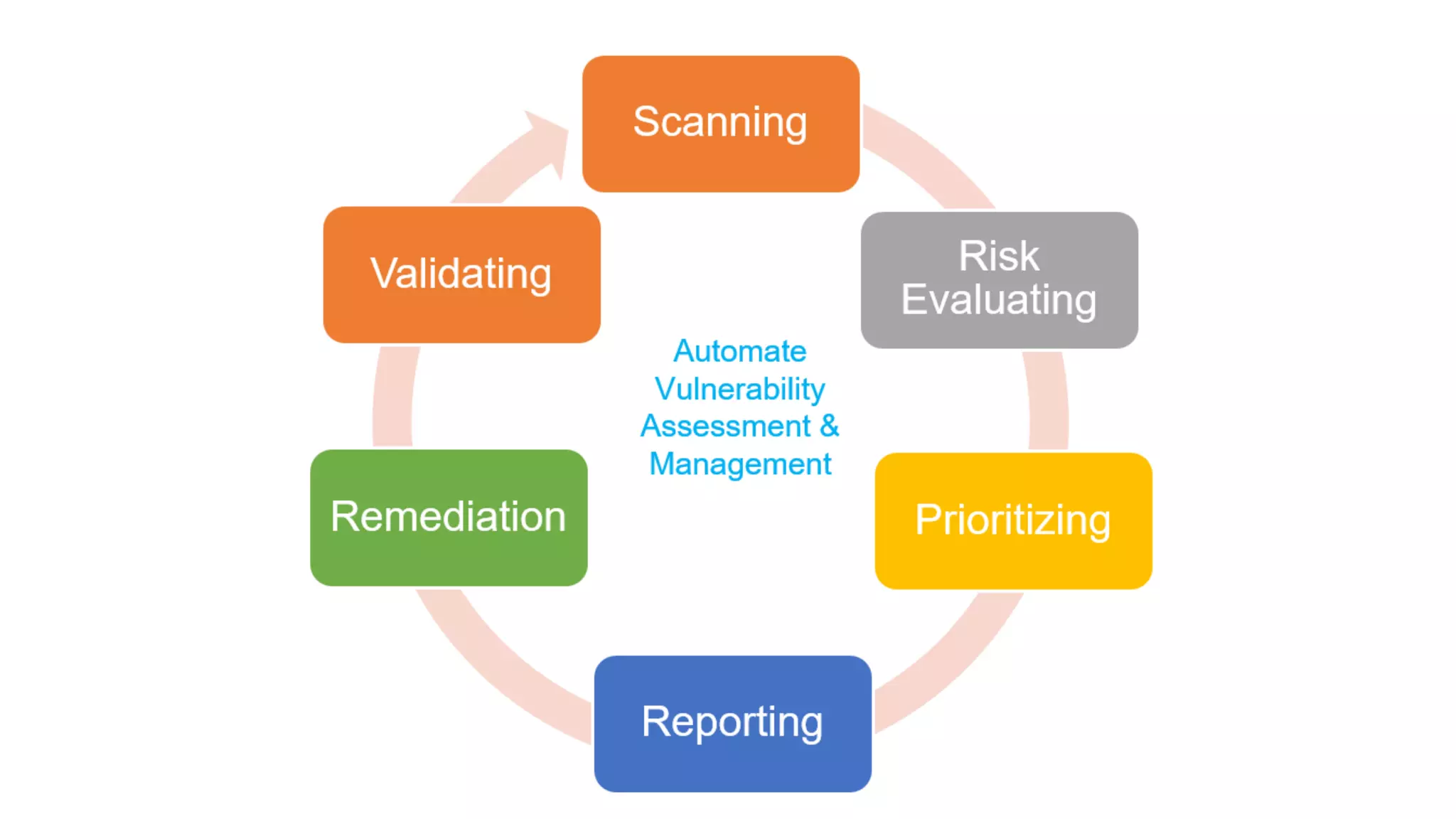
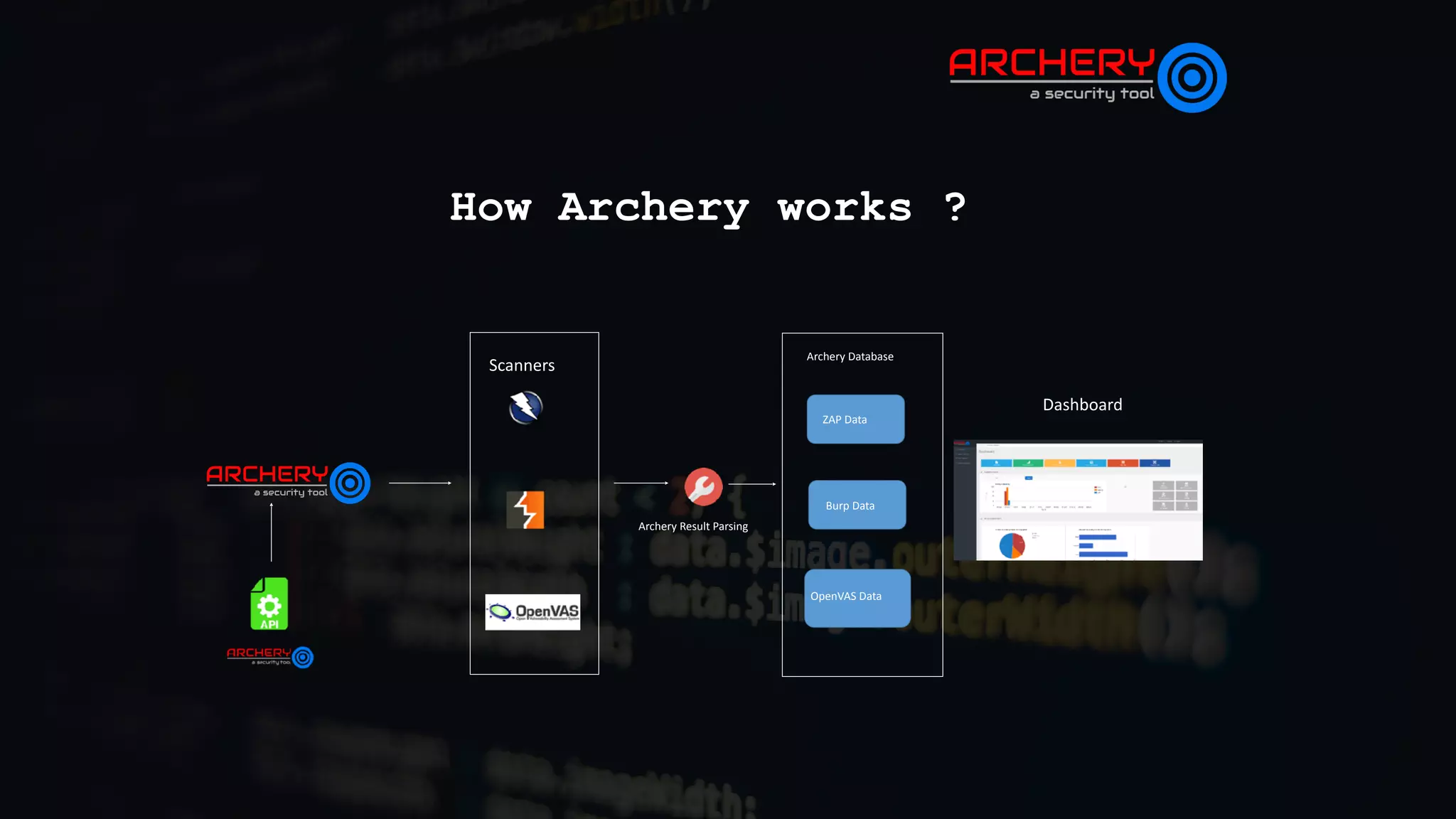
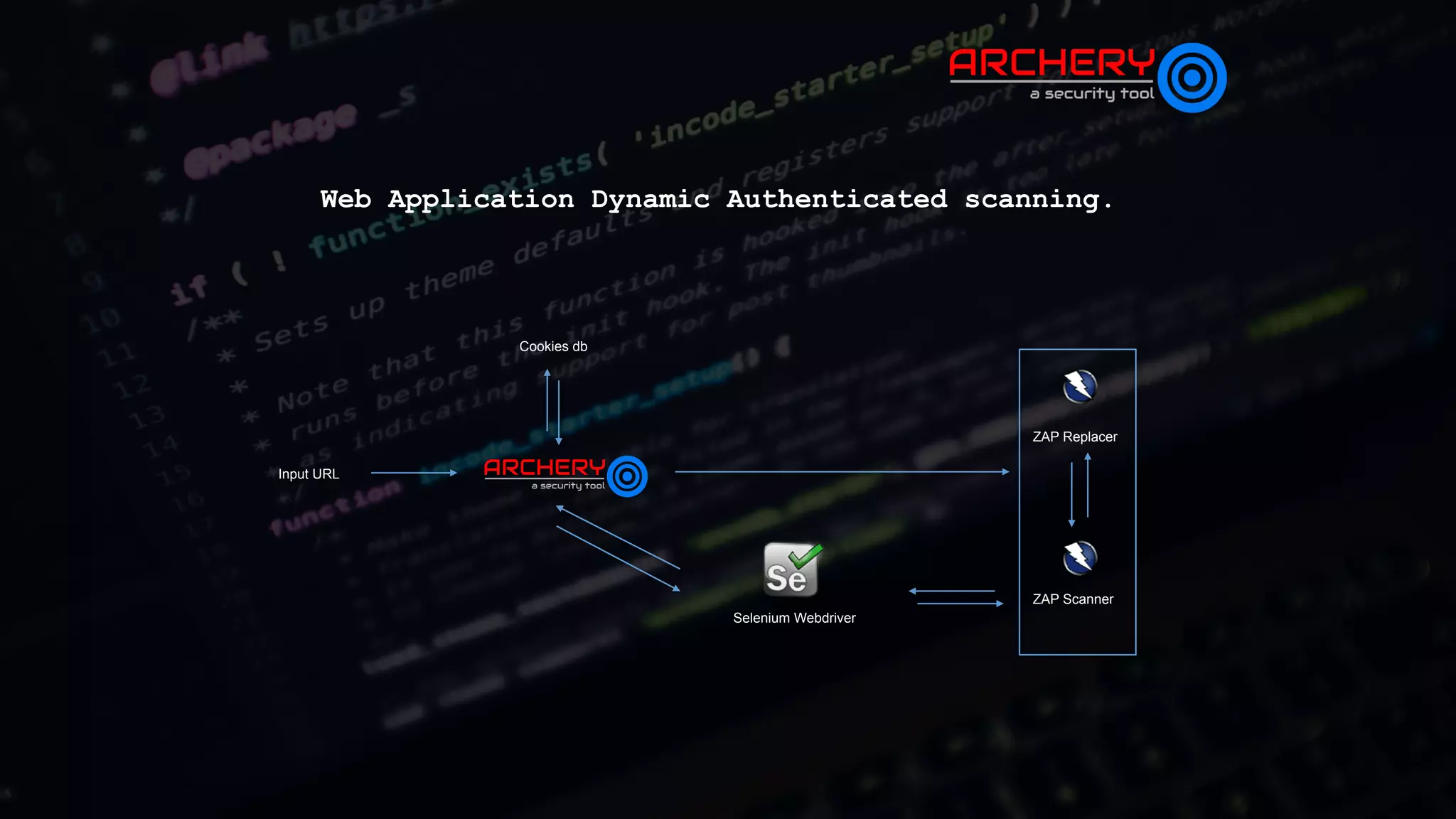
The document presents an overview of automated vulnerability assessment and management, introduced by Anand Tiwari, a pentester with experience in various areas of cybersecurity. It discusses the open-source tool 'Archery' for managing vulnerabilities, its functionalities, challenges in vulnerability assessment, and offers a roadmap for future developments. Additionally, it invites contributions and provides resource links for documentation and contact information.