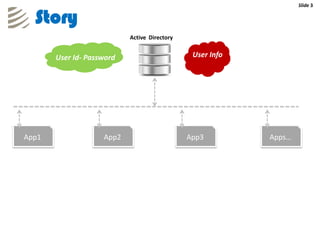
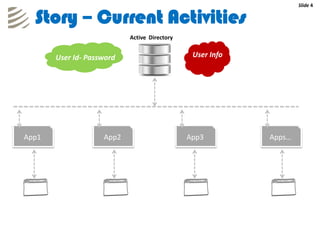
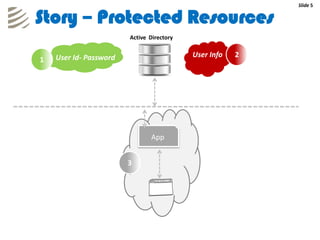
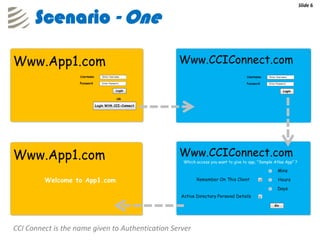
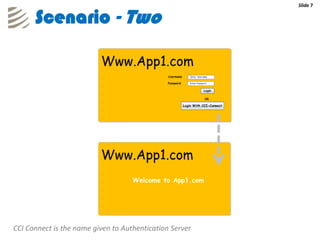
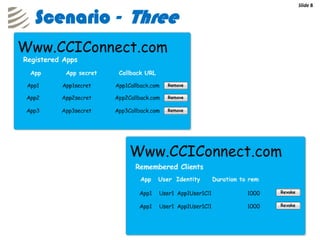
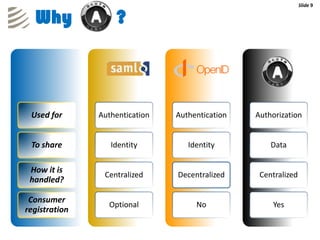
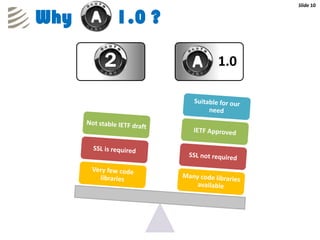
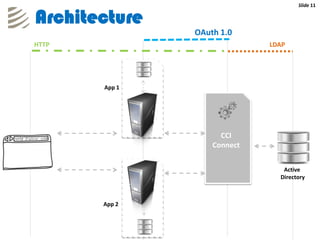
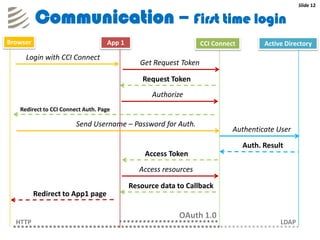
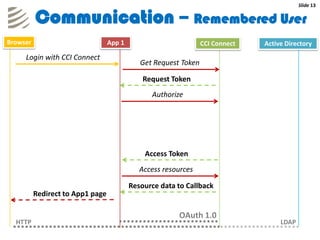
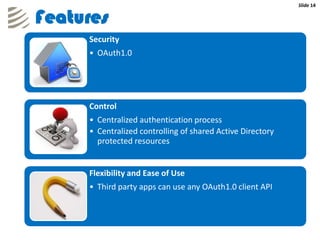
The document outlines the implementation of a web-based authentication provider called 'CCI Connect' that authenticates users against an LDAP server using OAuth 1.0. It highlights features such as centralized control of user access, security mechanisms, and flexibility for third-party applications. Users only log in once, as their authentication details are not shared with third-party apps, and they can revoke access when needed.