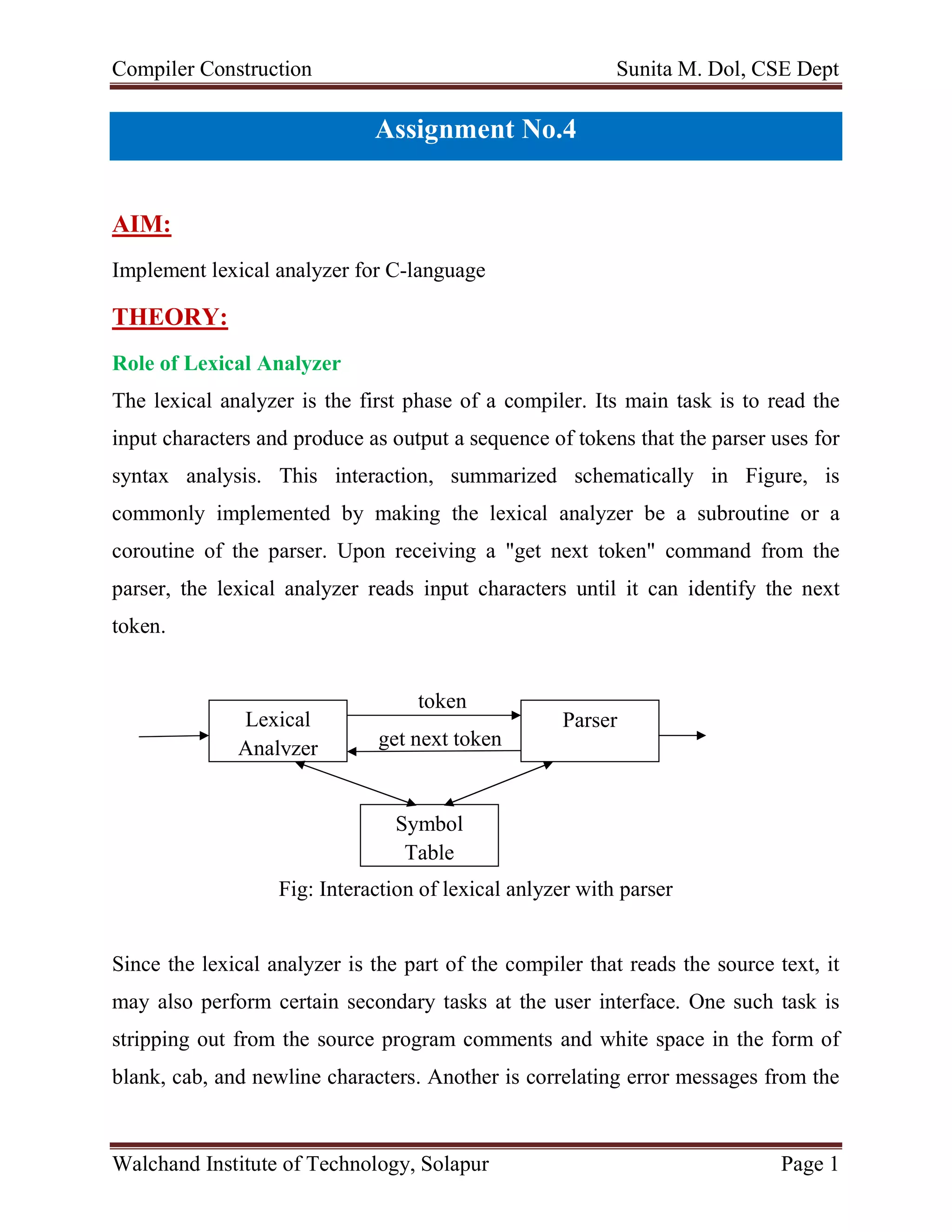
This document discusses the role and implementation of a lexical analyzer. It begins by explaining that the lexical analyzer is the first phase of a compiler that reads source code characters and produces tokens for the parser. It describes how the lexical analyzer interacts with the parser by returning tokens when requested. The document then discusses several tasks of the lexical analyzer, including stripping comments and whitespace, tracking line numbers for errors, and preprocessing macros. It also covers concepts like tokens, patterns, lexemes, and attributes. Finally, it provides an example input and output of a lexical analyzer tokenizing a C program.

![Compiler Construction Sunita M. Dol, CSE Dept
Walchand Institute of Technology, Solapur Page 3
Token, patterns & lexemes
TOKEN
• A classification for a common set of strings
• Examples Include <Identifier>, <number>, etc.
PATTERN
• The rules which characterize the set of strings for a token
• File and OS Wildcards ([A-Z]*.*)
LEXEME
• Actual sequence of characters that matches pattern and is classified by a
token
• Identifiers: x, count, name, etc…
Attributes of tokens](https://image.slidesharecdn.com/assignment4-211001092016/75/Assignment4-3-2048.jpg)