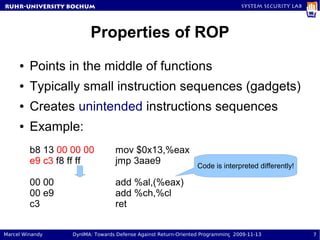
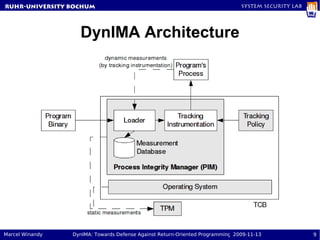
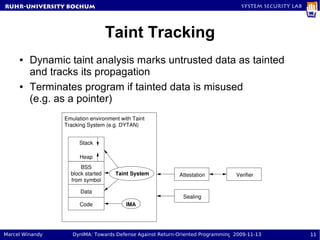
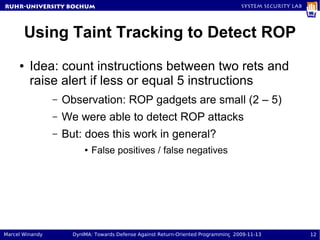
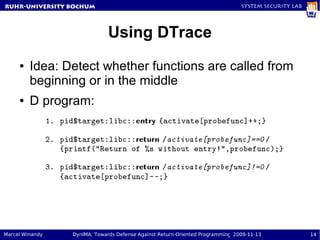
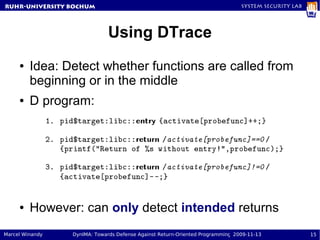
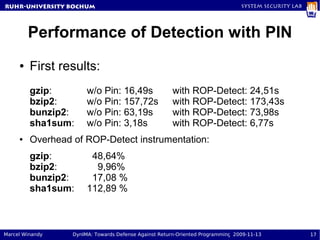
The document presents a proposal called DynIMA that uses dynamic instrumentation and integrity measurement to detect return-oriented programming (ROP) attacks. DynIMA instruments code at load time to perform integrity checks at runtime. Two approaches are examined: taint tracking and dynamic tracing using DTrace. Preliminary results show the instrumentation detects ROP attacks but with an overhead of up to 112% for some programs. Future work is needed to improve performance and analyze detection capabilities.