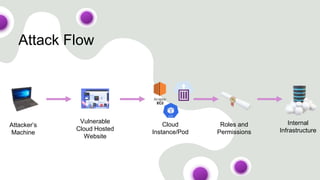
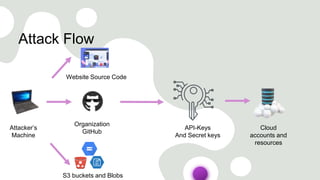
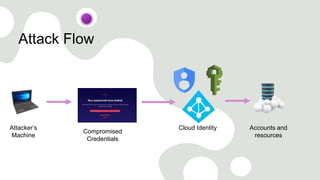
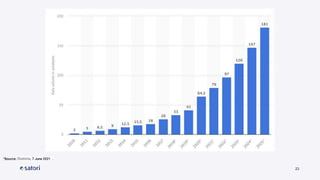
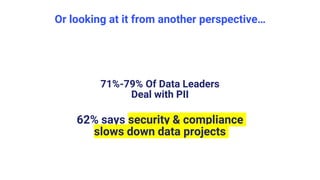
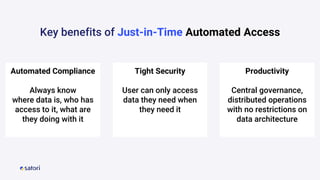
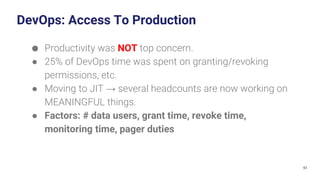
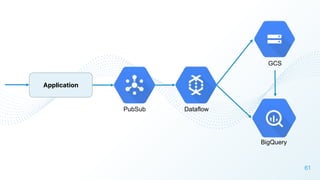
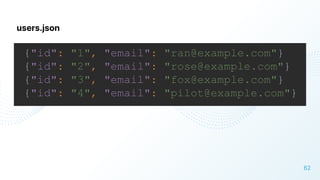
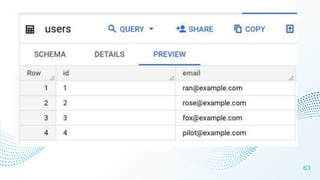
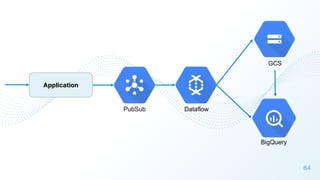
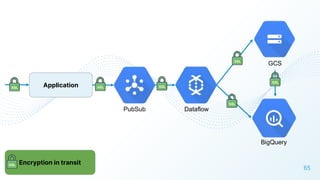
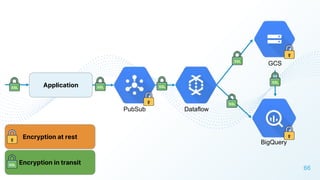
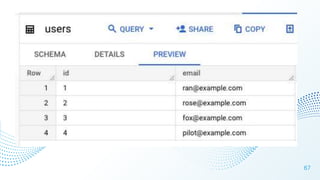
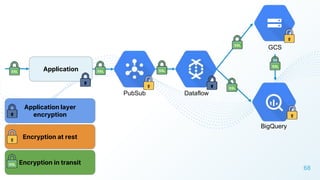
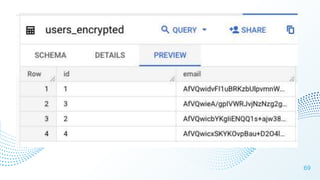
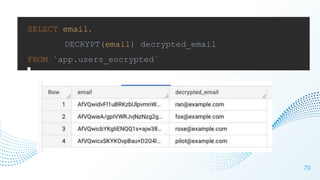
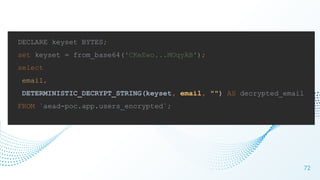
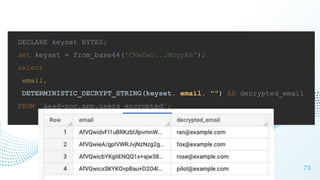
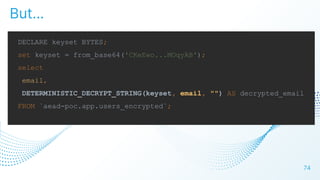
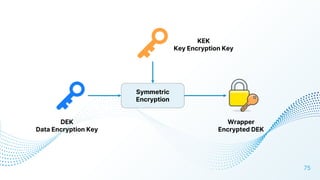
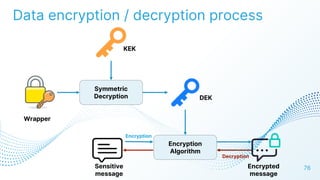
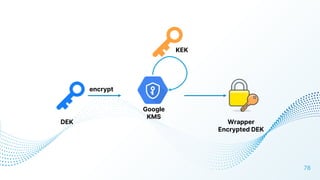
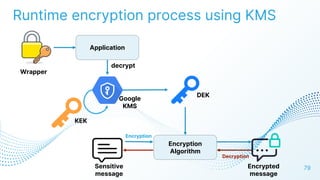
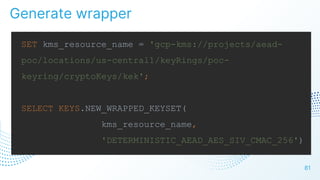
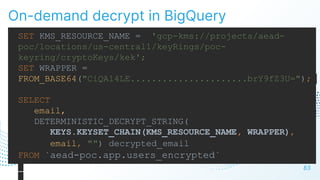
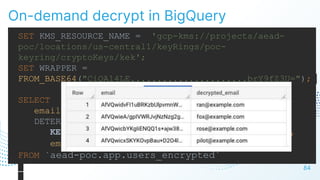
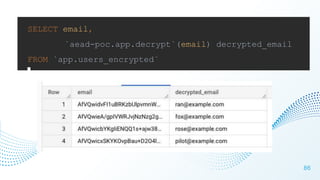
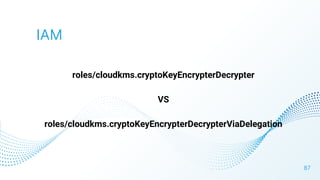
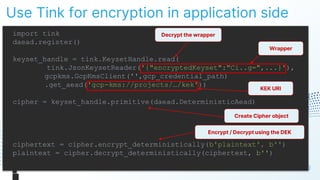
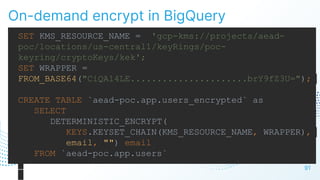
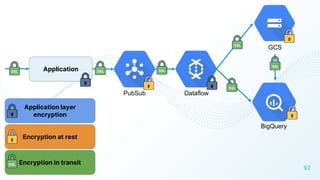
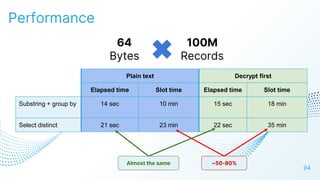
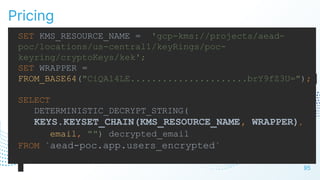
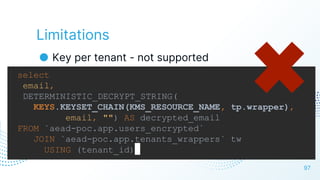
The document discusses cloud security vulnerabilities, focusing on exposed cloud instances and the risks of sensitive data leakage due to poor access controls and compromised credentials. It emphasizes the importance of automating data security, outlining a framework for DataSecOps that integrates continuous security practices within data operations. The presentation highlights the need for strong authentication measures and just-in-time access provisioning to enhance data security while facilitating productivity.