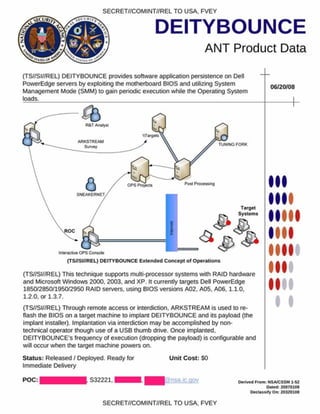
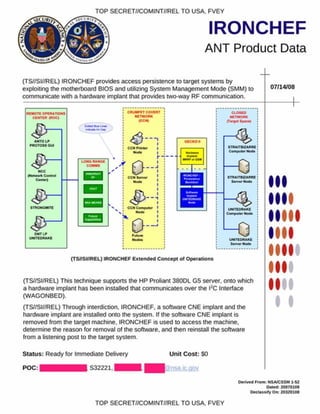
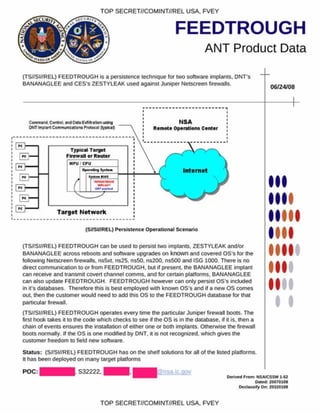
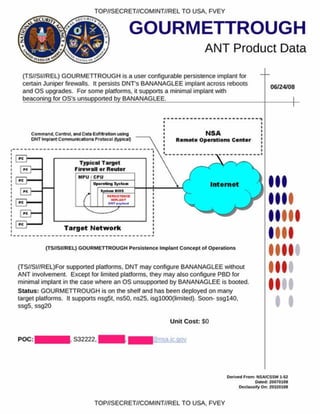
SCHOOLMONTANA provides persistence for DNT implants on Juniper routers. It modifies the router's BIOS to execute the SCHOOLMONTANA implant at the end of the System Management Mode handler. This allows DNT implants like VALIDATOR to survive upgrades or replacements of the operating system, including physically replacing the router's compact flash card. SCHOOLMONTANA must support all modern versions of JUNOS, the operating system used on Juniper routers.