This document summarizes an advanced Apache web server training session covering security and performance tuning. The key points discussed include:
1) Methods for securing an Apache server such as restricting access, disabling unneeded server technologies, running as a non-root user, using firewalls and encryption.
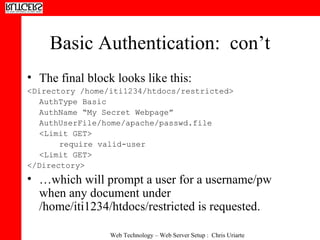
2) Configuring password-based authentication for protected directories using modules like mod_auth and storing passwords in text files created by the htpasswd utility.
3) An exercise where attendees set up password protection on their local Apache server website using a .htaccess file and htpasswd.
4) Restricting access to protected directories by IP, hostname or domain using directives in httpd.conf or .








![Creating a Password File htpasswd is a utility for generating encrypted passwords and creating a password file Part of apache distribution, located in : {SERVER ROOT}/bin/htpasswd Usage: htpasswd [-c] password-file username The –c flag creates a new password file. Example, adds a user myname and creates a new password file (type all on one line): /home/iti1234/bin/htpasswd -c /home/iti1234/apache/passwdfile username](https://image.slidesharecdn.com/520-meeting4-100511094918-phpapp02/85/Apache-Web-Server-Setup-4-12-320.jpg)