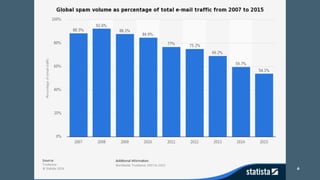
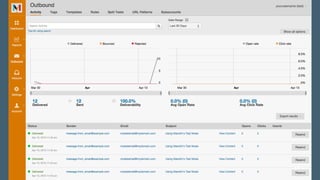
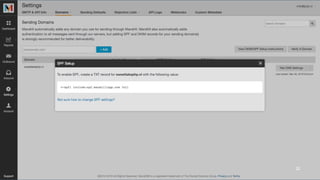
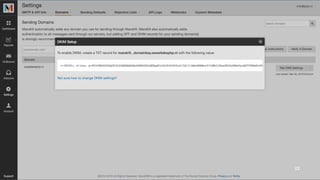
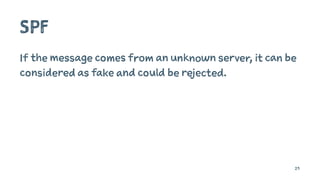
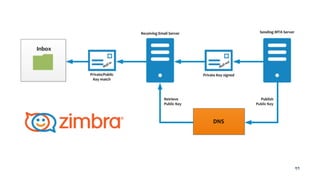
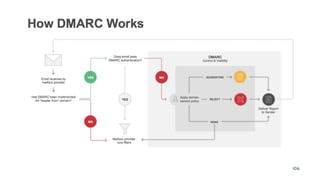
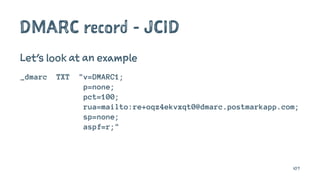
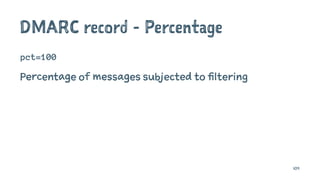
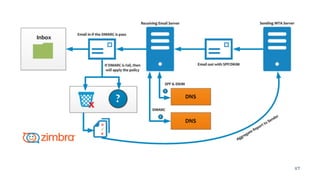
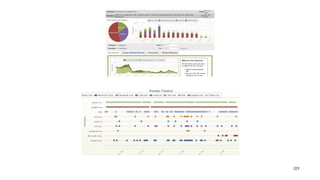
The document discusses the importance of combating email spam, focusing on email authentication methods like SPF, DKIM, and DMARC to enhance security and trust. It explains how these protocols work and their configuration, providing examples and potential outcomes of their implementation. Additionally, the text highlights the consequences of phishing and other email-related threats, and offers insights on how to improve email delivery and prevent forgery.



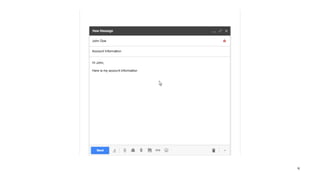
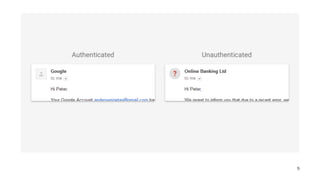





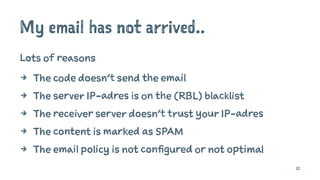
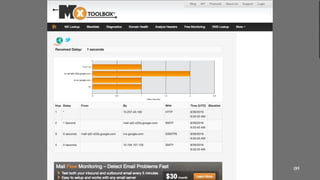
![My email has not arrived..
What can we do about it?
4 Check the function of the script
4 Check the server IP-adres on the (RBL) blacklist
4 Submit for removal
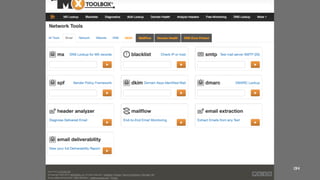
4 Checking the email policies [SPF/DKIM]
4 Using email services providers
13](https://image.slidesharecdn.com/presentatie-161103104630/85/Join-the-fight-against-email-spam-EmmenPHP-13-320.jpg)
![How we did it the old days
2016-04-01 05:00:13 [1487] 1Ov4tU-0000Nz-Rm H=mailhost.domain.com [208.42.54.2]:51792 I=[67.215.162.175]:25 Warning: "SpamAssassin as theuser detected message as NOT spam (0.0)"
2016-04-01 05:00:13 [1487] 1Ov4tU-0000Nz-Rm <= maillinglist@domain.com H=mailhost.domain.com [208.42.54.2]:51792 I=[67.215.162.175]:25 P=esmtps X=TLSv1:AES256-SHA:256 CV=no
S=21778 id=384a86a39e83be0d9b3a94d1feb3119f@domain.com T="Daily Science Maillinglist: Chameleon" from for user@example.com
2016-04-01 05:00:14 [1534] 1Ov4tU-0000Nz-Rm => user F= P= R=virtual_user T=virtual_userdelivery S=21902 QT=6s DT=0s
2016-04-01 05:00:15 [1534] 1Ov4tU-0000Nz-Rm Completed QT=7s
14](https://image.slidesharecdn.com/presentatie-161103104630/85/Join-the-fight-against-email-spam-EmmenPHP-14-320.jpg)

































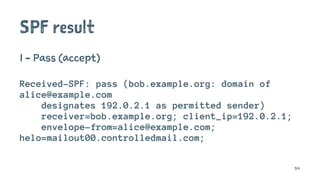


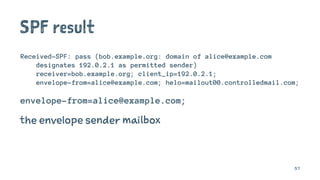



















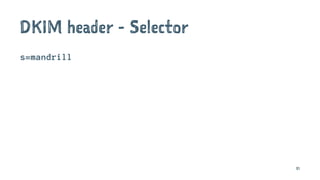
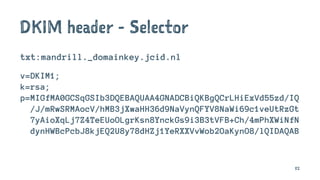


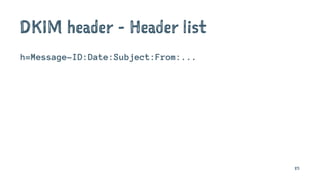



































![Delivered-To: jeffrey@jcid.nl
Received: by 10.194.157.102 with SMTP id wl6csp186952wjb;
Fri, 26 Aug 2016 02:33:43 -0700 (PDT)
X-Received: by 10.55.120.195 with SMTP id t186mr2016594qkc.118.1472204023376;
Fri, 26 Aug 2016 02:33:43 -0700 (PDT)
Return-Path: <martynminnis@gmail.com>
Received: from mail-qt0-x22a.google.com (mail-qt0-x22a.google.com. [2607:f8b0:400d:c0d::22a])
by mx.google.com with ESMTPS id u126si7830854qkf.92.2016.08.26.02.33.43
for <jeffrey@jcid.nl>
(version=TLS1_2 cipher=ECDHE-RSA-AES128-GCM-SHA256 bits=128/128);
Fri, 26 Aug 2016 02:33:43 -0700 (PDT)
Received-SPF: pass (google.com: domain of martynminnis@gmail.com designates 2607:f8b0:400d:c0d::22a as permitted sender) client-ip=2607:f8b0:400d:c0d::22a;
Authentication-Results: mx.google.com;
dkim=pass header.i=@gmail.com;
spf=pass (google.com: domain of martynminnis@gmail.com designates 2607:f8b0:400d:c0d::22a as permitted sender) smtp.mailfrom=martynminnis@gmail.com;
dmarc=pass (p=NONE dis=NONE) header.from=gmail.com
Received: by mail-qt0-x22a.google.com with SMTP id u25so35076163qtb.1
for <jeffrey@jcid.nl>; Fri, 26 Aug 2016 02:33:43 -0700 (PDT)
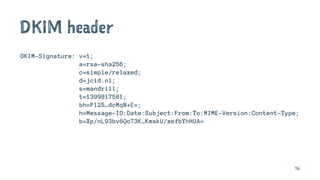
DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/relaxed;
d=gmail.com; s=20120113;
h=mime-version:from:date:message-id:subject:to;
bh=Kq6G9vieA14XMBGjPWOQiNs68KLd8OmUbmtlbrM4Oqk=;
b=w8wBPP18htjzrPTh82kQttpVKLoEbgCTkMuBkhAzwHmOJIrDv4FwXonYO7ERv0fOg9
t2A0Kia+9NISRHS5X8HTUdJz50PE7YMOE0le34QZ320cjbdb1AYcFE4VJ+499XJ9nVEg
OodIcjlqtPTUwhnF+RJc8D7O8Rfr3ZhBBB9d7cdCtVxpljB+nNEErbWyRYREHEK0hczd
Rf2b1FG2N1iKiXV0DuSF/rjnxHcQAhxRojiYuRkuKPYHADcQezwJVbLPbYjmYNrEaLlD
OZeOiov5co25DZs9Lf6HfEQ0qWVgmzt9jDJaBTzzpweWjMpS7L5cDAgfiH4zuXCLt8CZ
IZ3A==
X-Google-DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/relaxed;
d=1e100.net; s=20130820;
h=x-gm-message-state:mime-version:from:date:message-id:subject:to;
bh=Kq6G9vieA14XMBGjPWOQiNs68KLd8OmUbmtlbrM4Oqk=;
b=VnjcGHkQIBznyNC9OhUhs9OJj9qhS8WdQ9zK2dqQiVyZ6/rC28SWeV5XNr1iQT/FNp
qyTaunNDplNrVrlnkl+NSxWiGNH10se5nVVbJ7ArSSAkoGRQwo+CfxoIbwU9CVVeNNpL
l01B5DFSeom7pL9lUpr7n6trxKg11vUXbIAp/DYbhRTc0LBU4VI8T4w+PBKdnV2Hvzai
oRUIrz9f/ykGV4bmpktOAFhKCZoYpL3tKJ65BpV/f9bp/aOFTx0azHUjZ31GtfS7z2Mc
DmWdfoLtkcriTnpDPCHxzKrLkS/dyN9hCFSYfyBwe6SgnvUqzKmYRME2jDf5pcGdHtDd
dJmw==
X-Gm-Message-State: AE9vXwOuiQZPoxCvQafsQevD9jy8ypQcaPZipkQnyeANw4f5dVvaU4jmBXgj1S6YxNvjp9jmDRESpEEq+Qscwg==
X-Received: by 10.200.43.105 with SMTP id 38mr2091543qtv.73.1472204022848; Fri, 26 Aug 2016 02:33:42 -0700 (PDT)
MIME-Version: 1.0
Received: by 10.237.43.163 with HTTP; Fri, 26 Aug 2016 02:33:42 -0700 (PDT)
From: Martijn Minnis <martynminnis@gmail.com>
Date: Fri, 26 Aug 2016 11:33:42 +0200
Message-ID: <CABe801A=t8StMzGqpWcut8uWAbfnopVP63nDi5g+Nq7n0cTz3A@mail.gmail.com>
Subject: EmmenPHP - looking for speakers
To: jeffrey@jcid.nl
Content-Type: multipart/alternative; boundary=001a113d00a6d1a568053af6359c
138](https://image.slidesharecdn.com/presentatie-161103104630/85/Join-the-fight-against-email-spam-EmmenPHP-138-320.jpg)