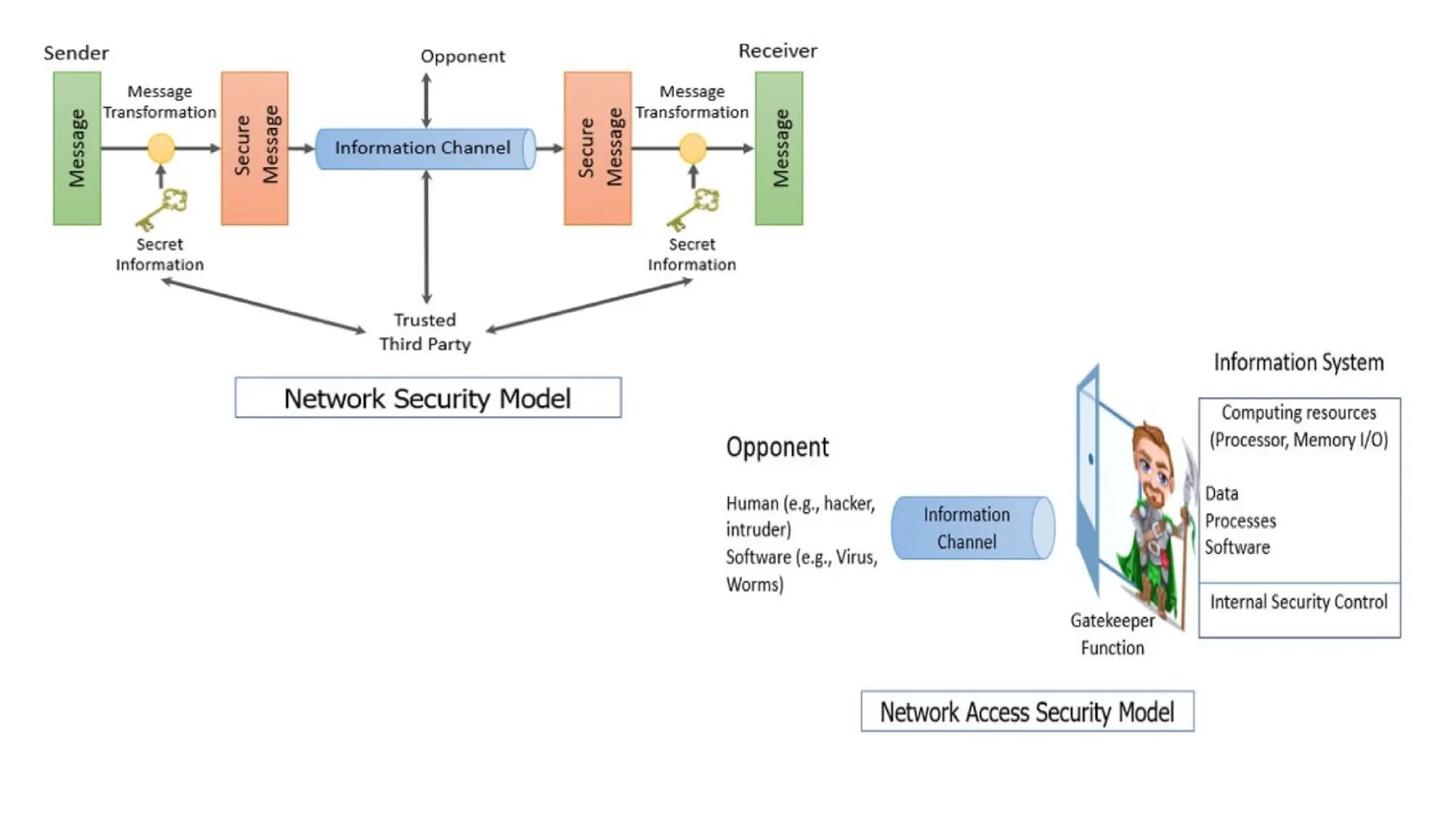
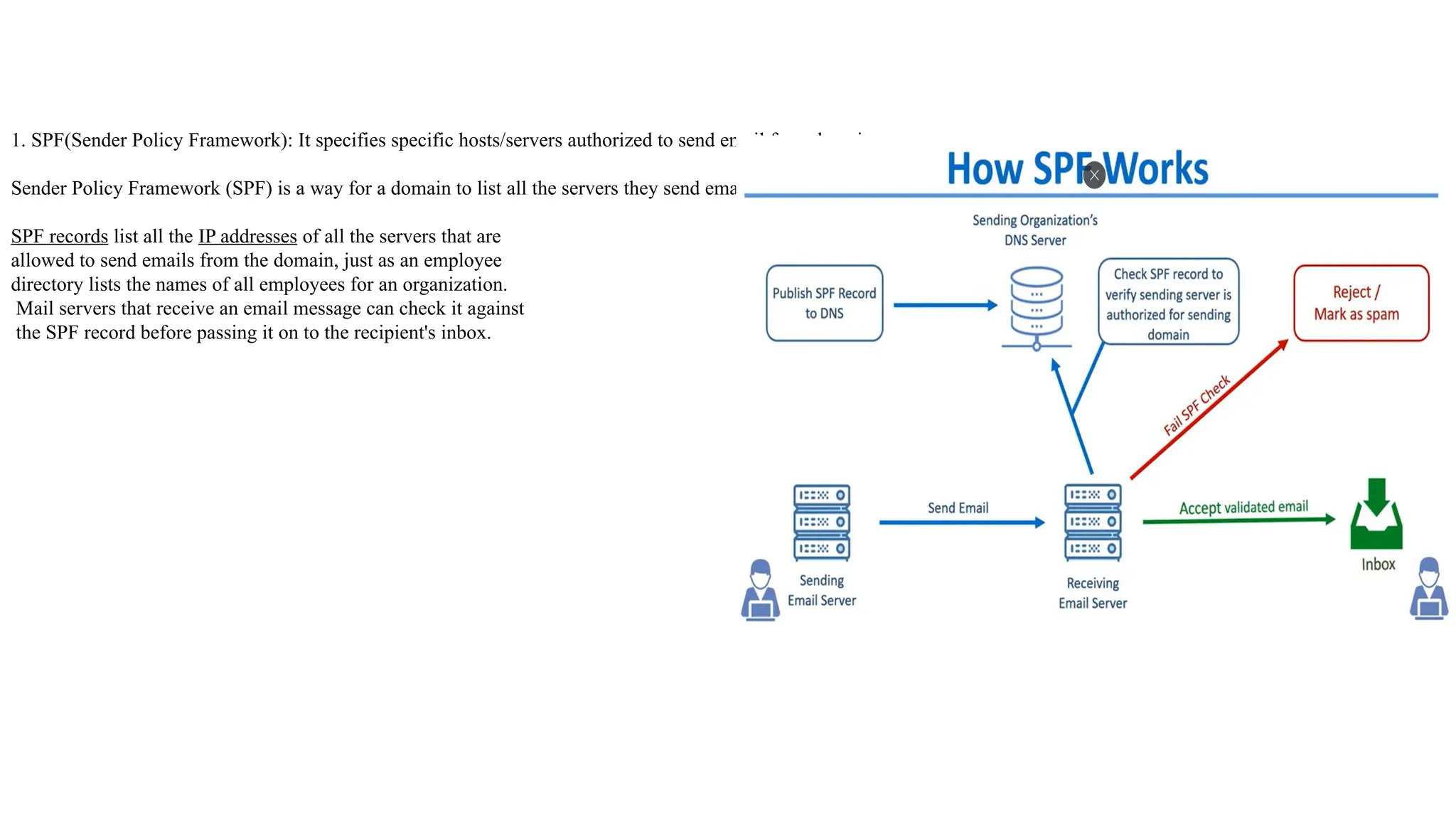
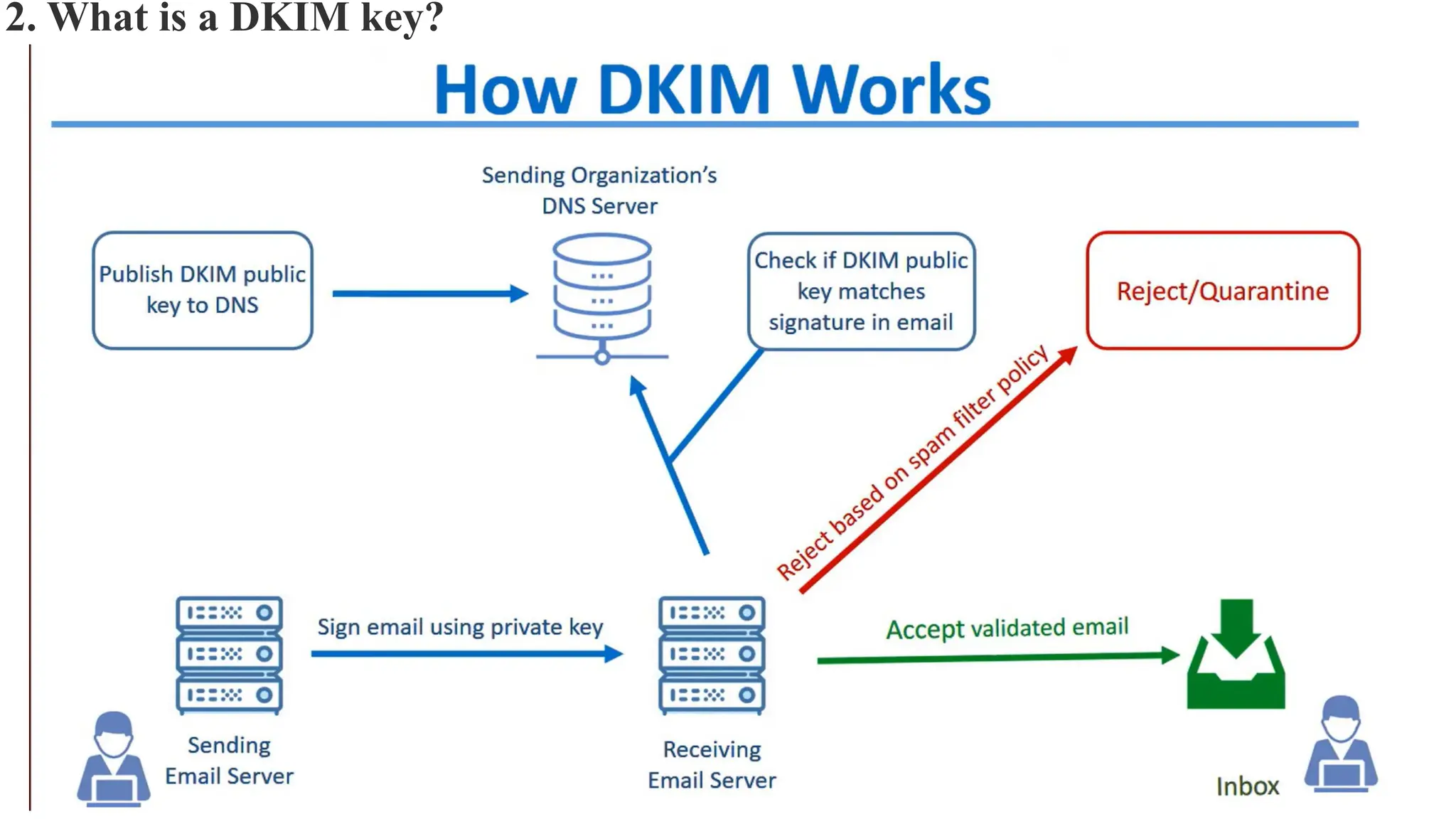
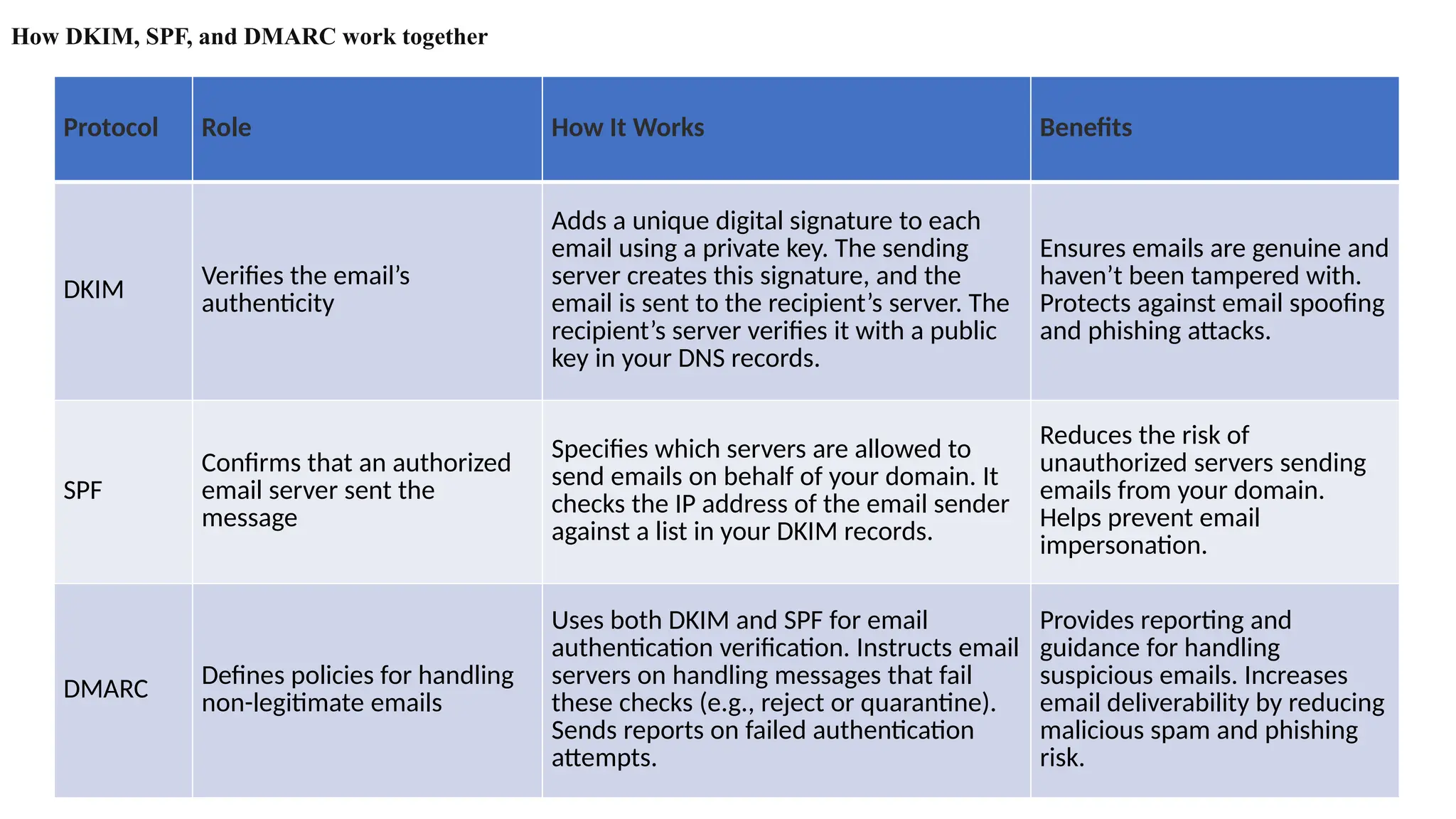
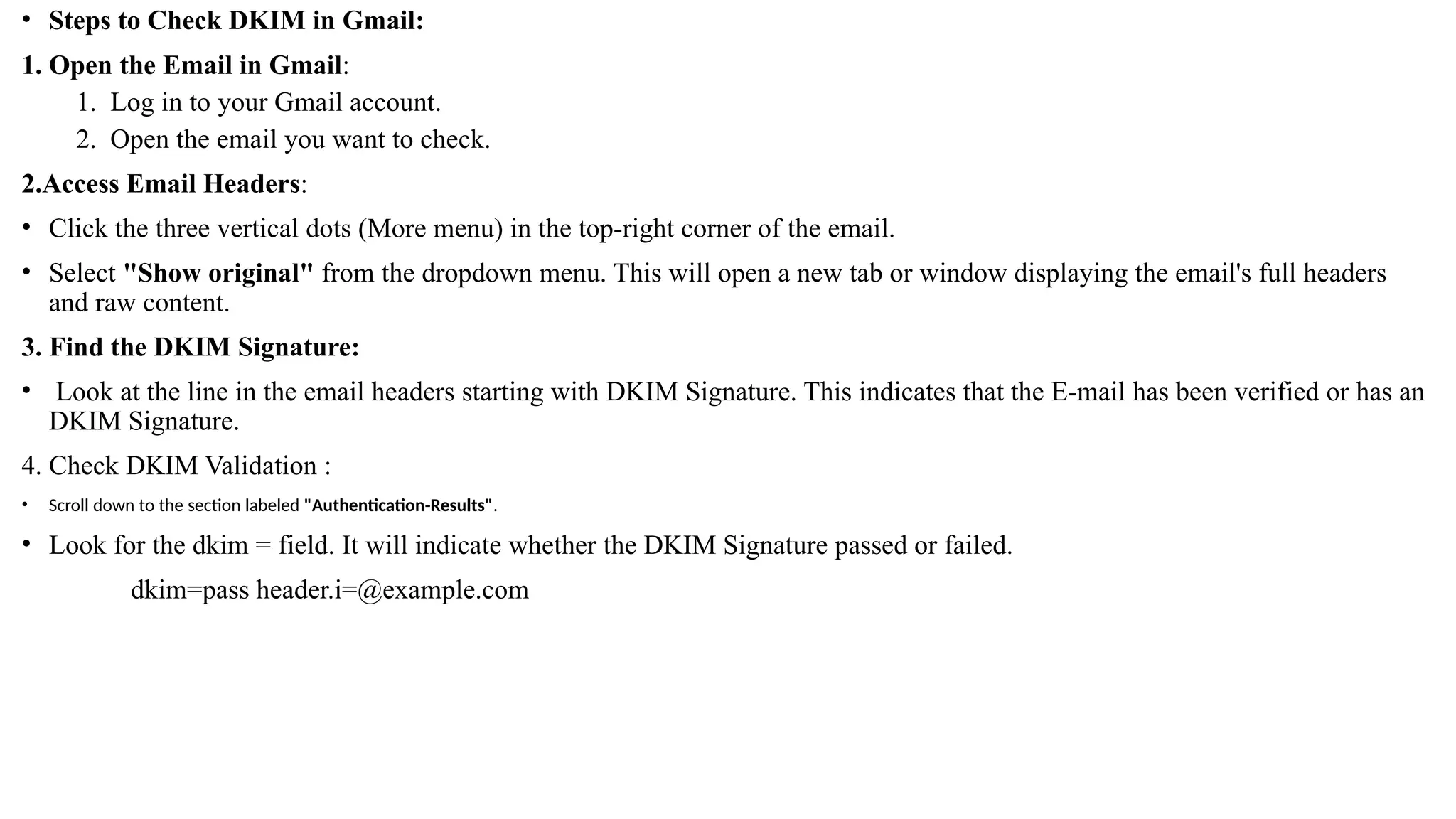
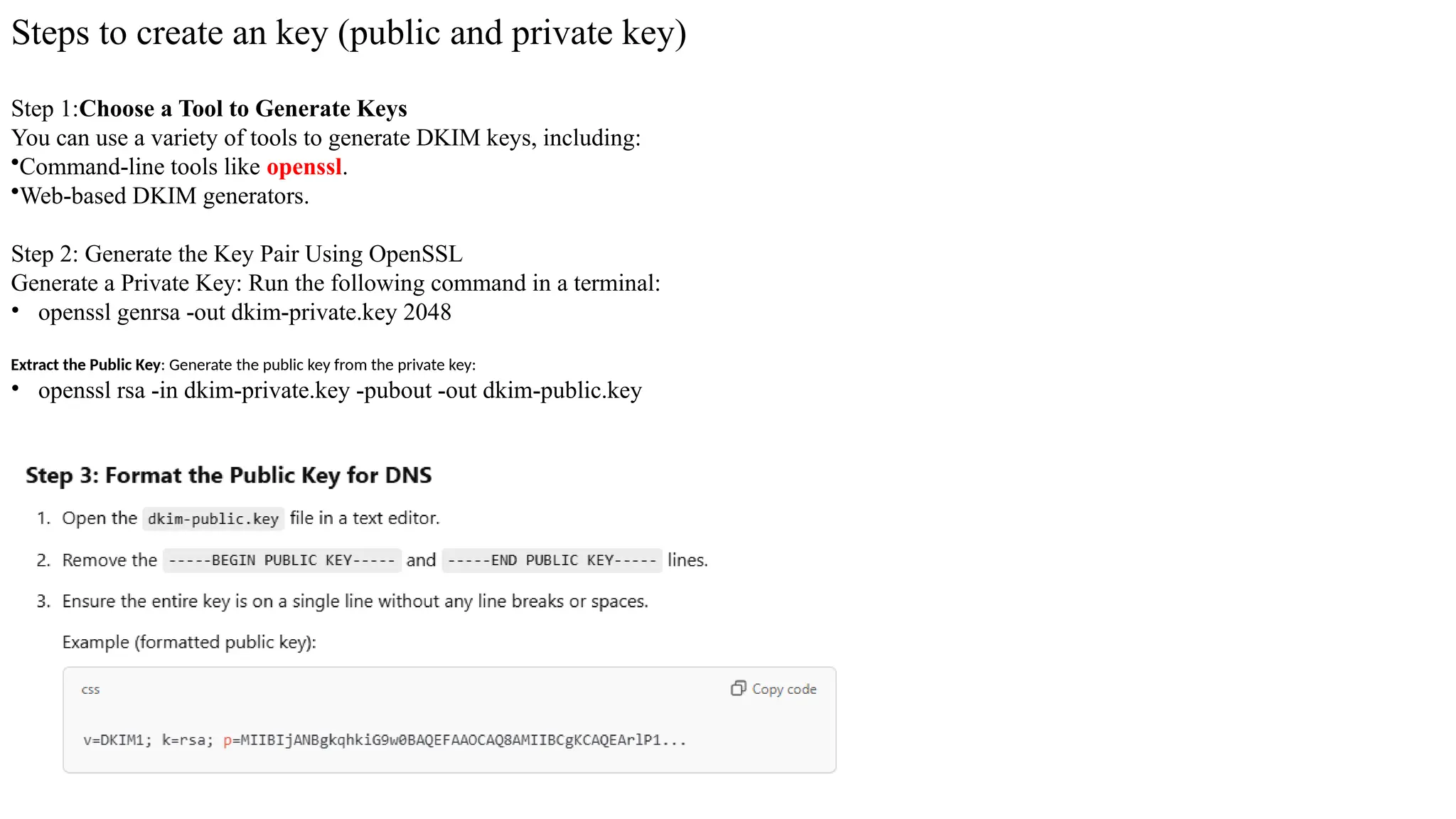
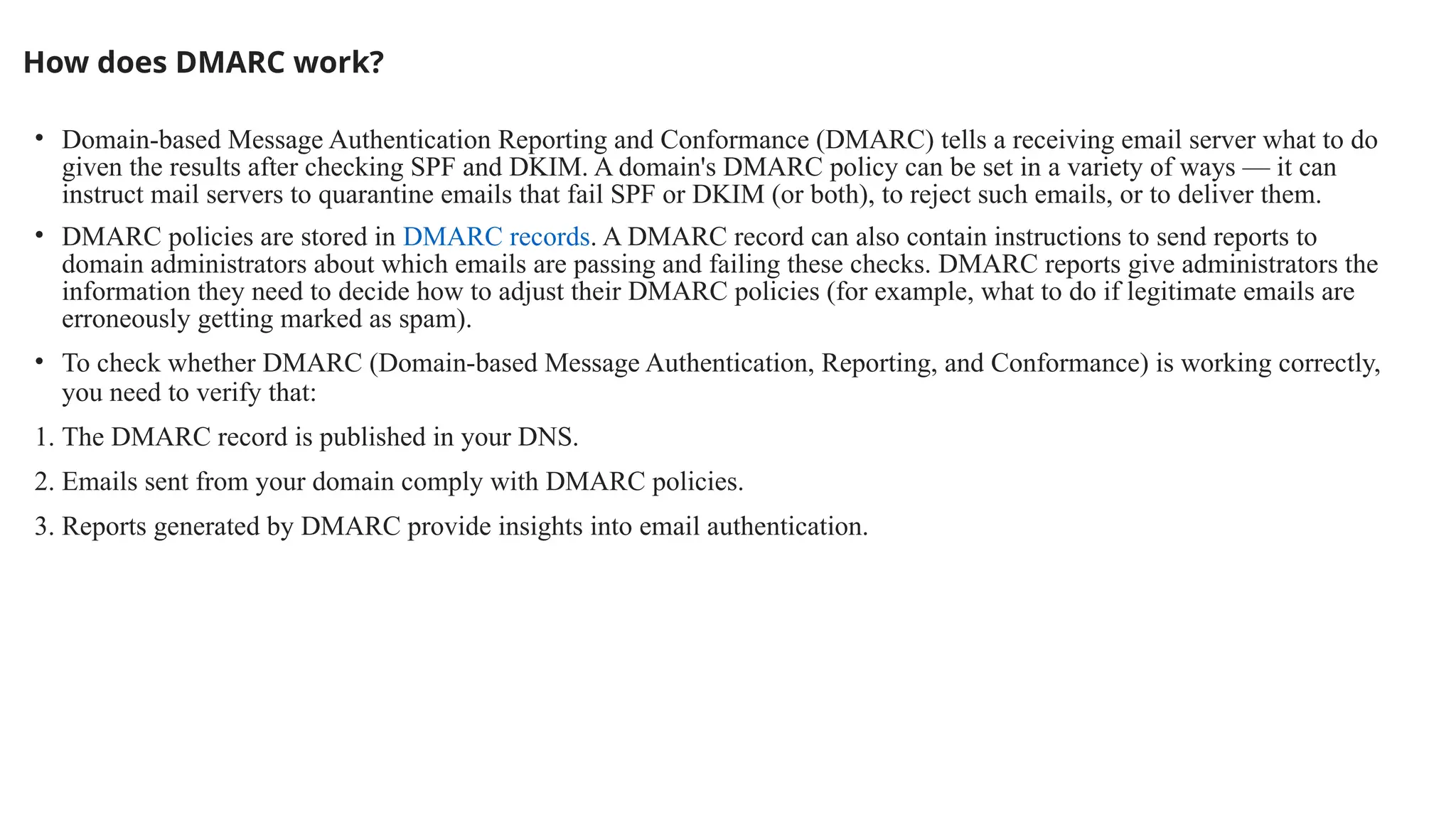
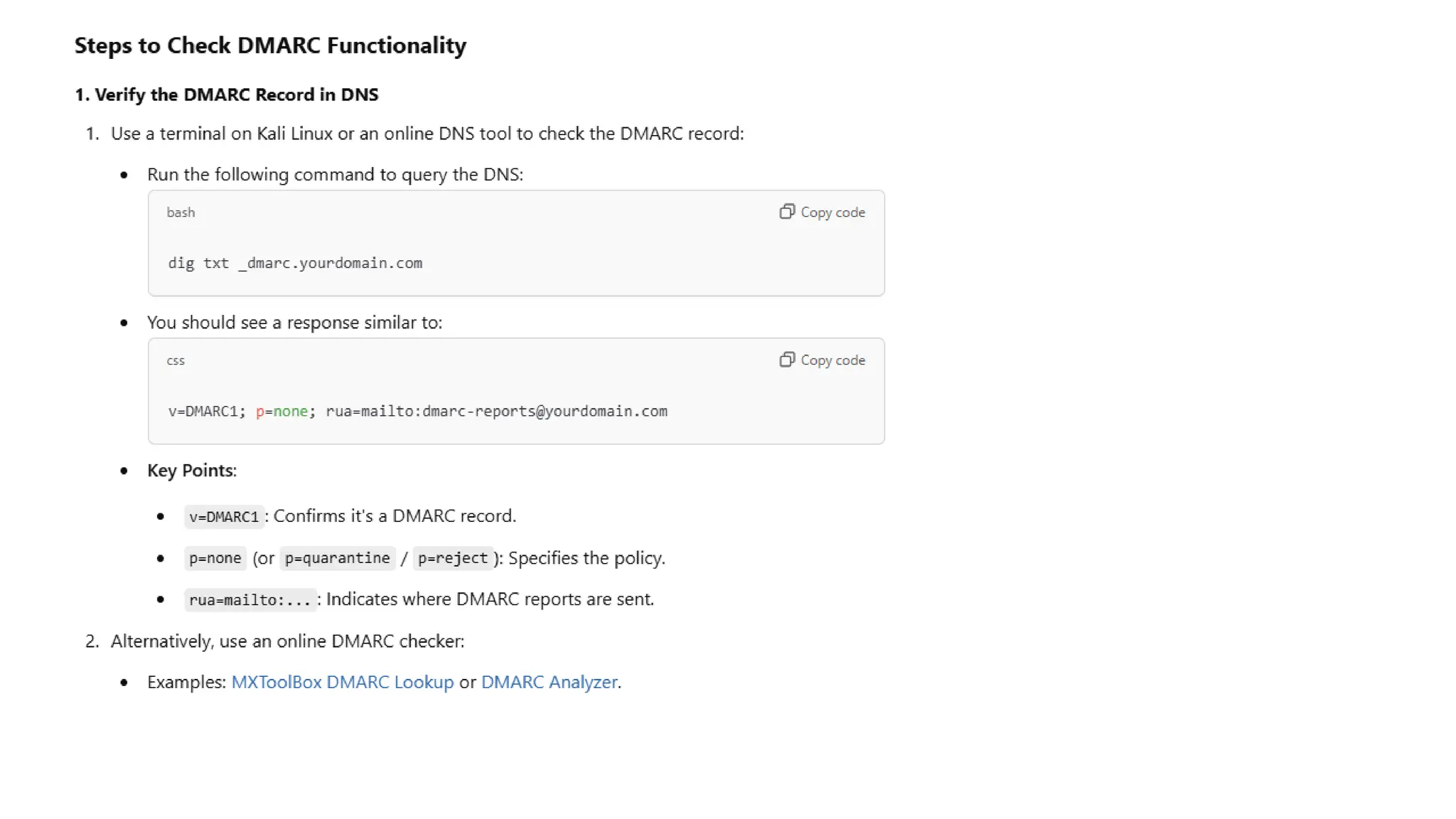
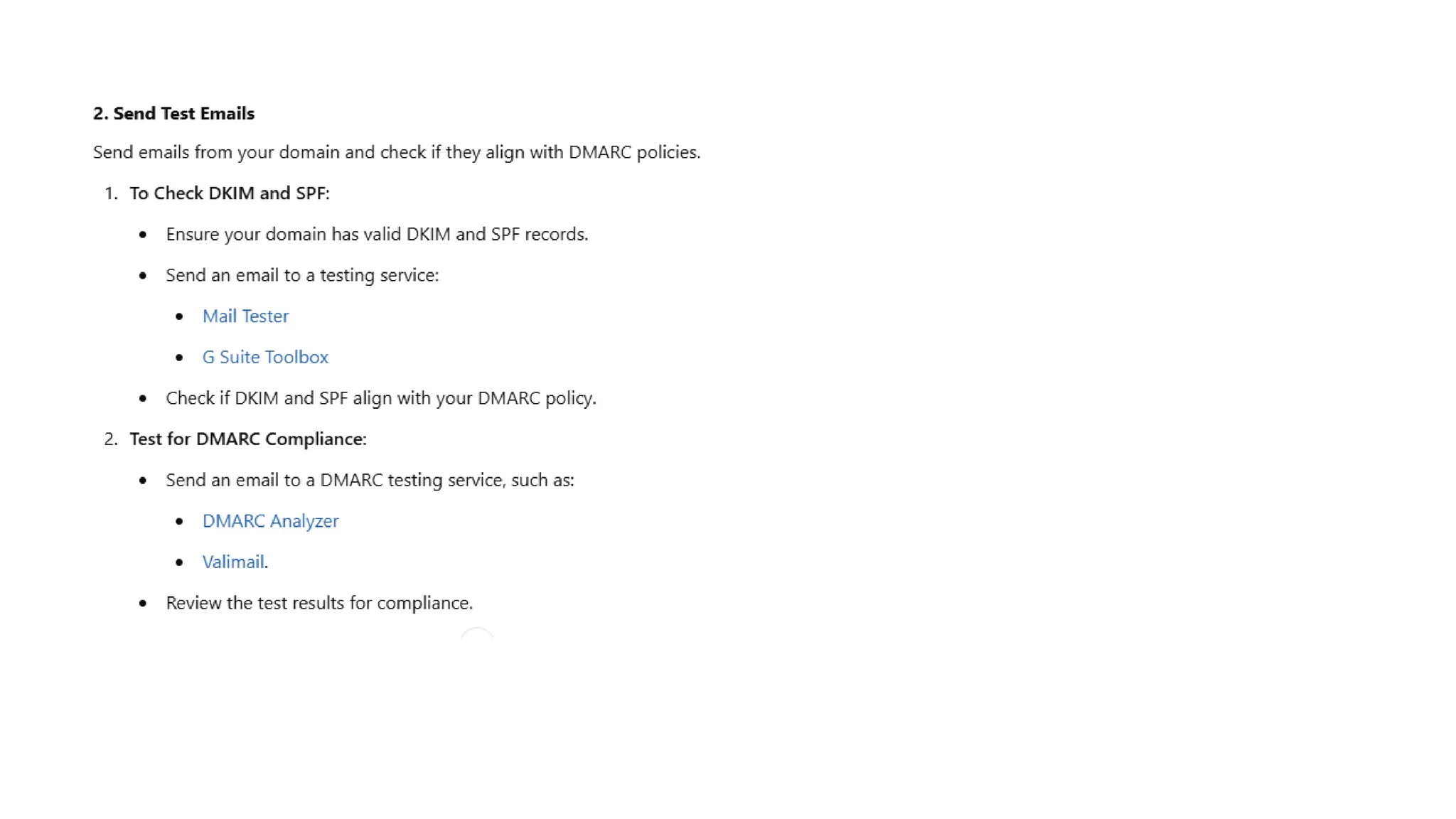
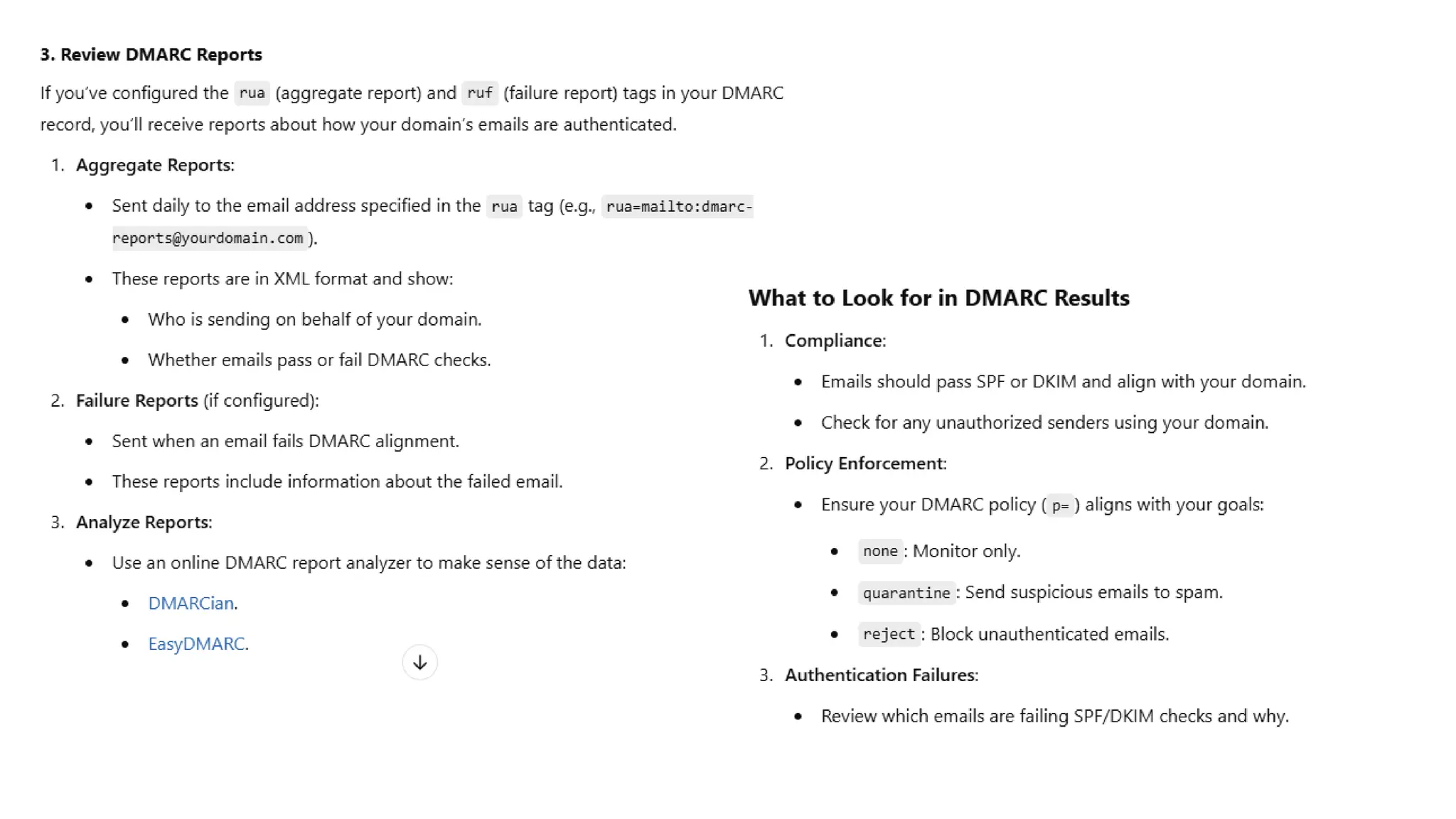
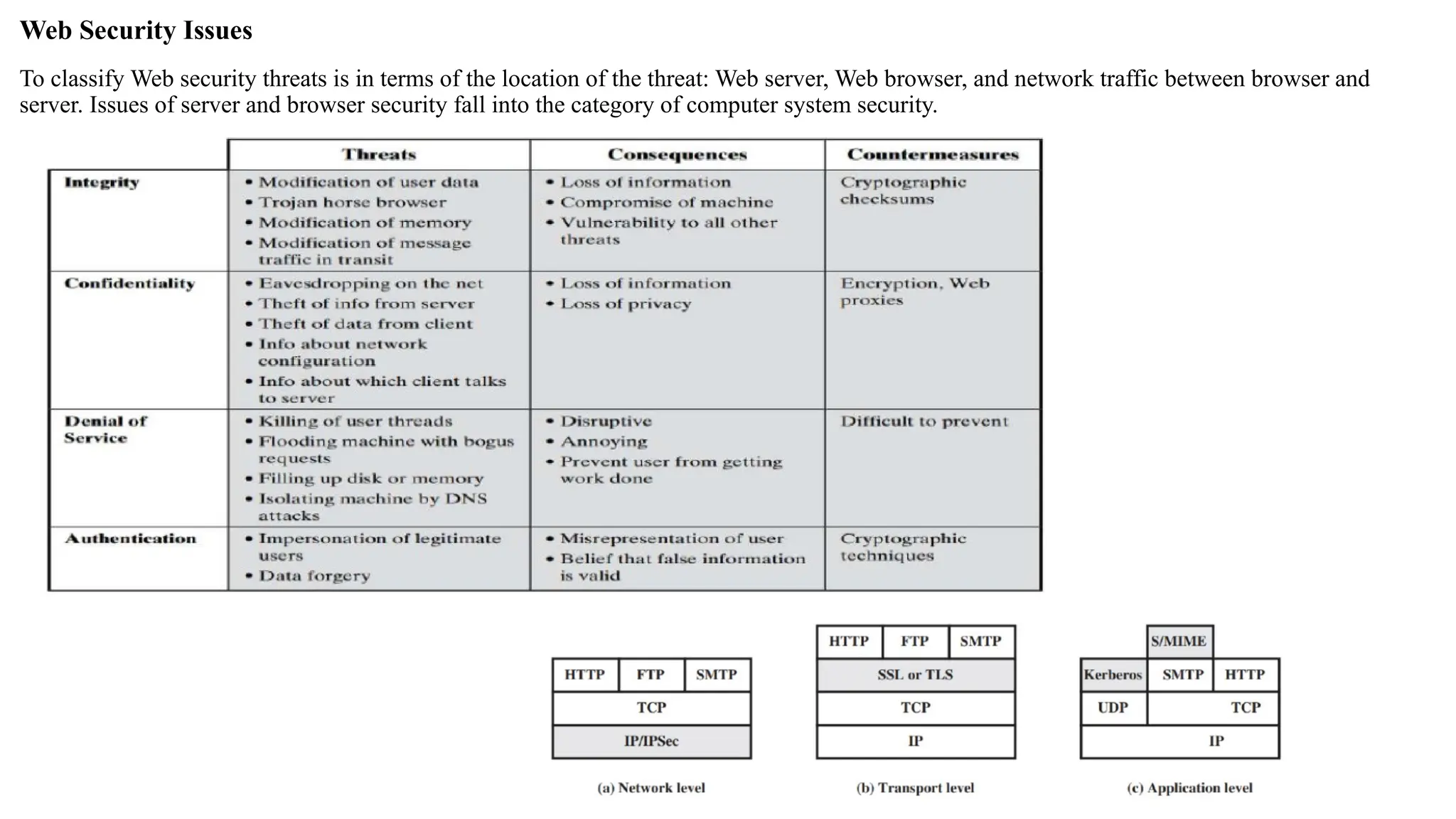
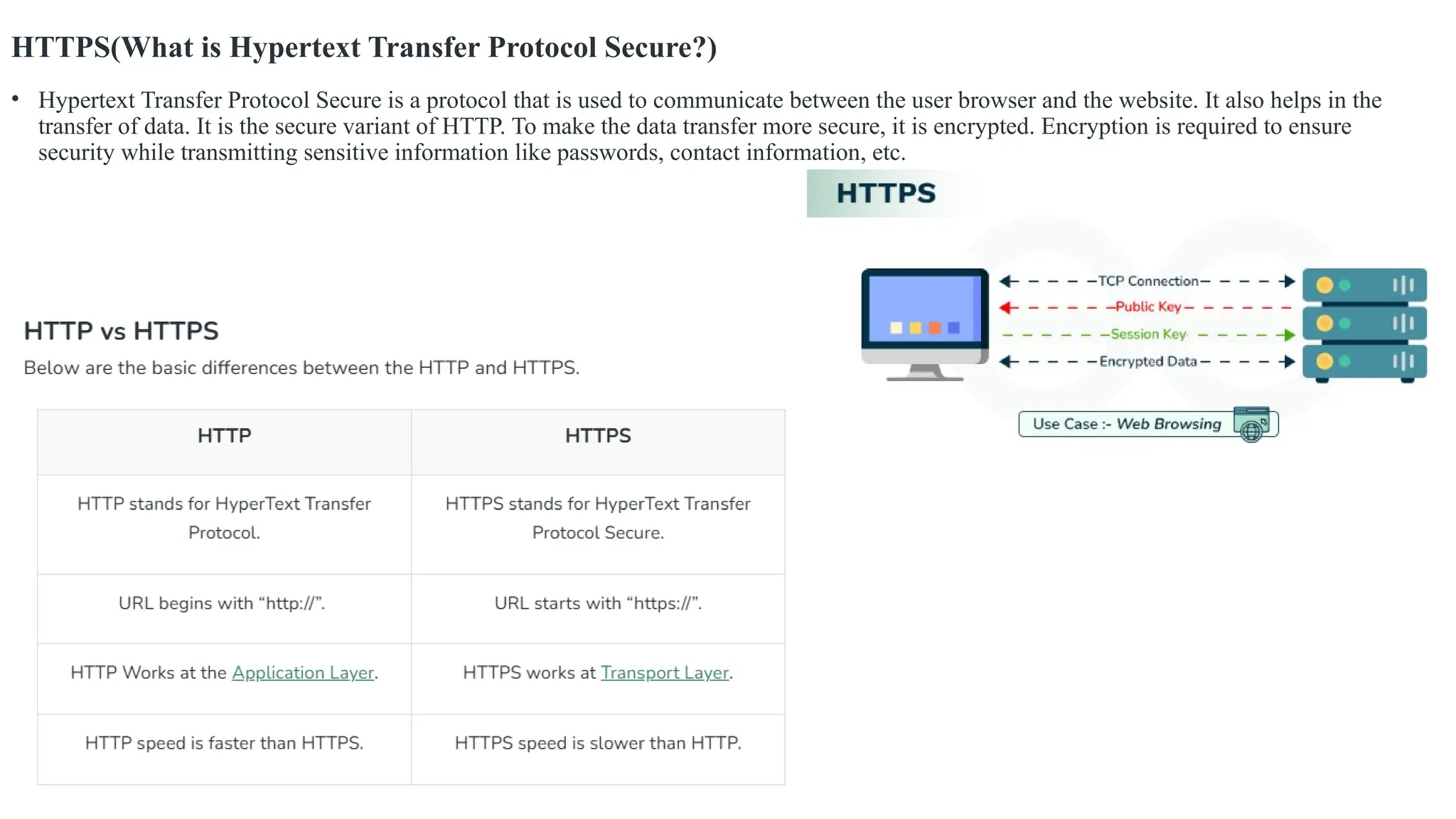
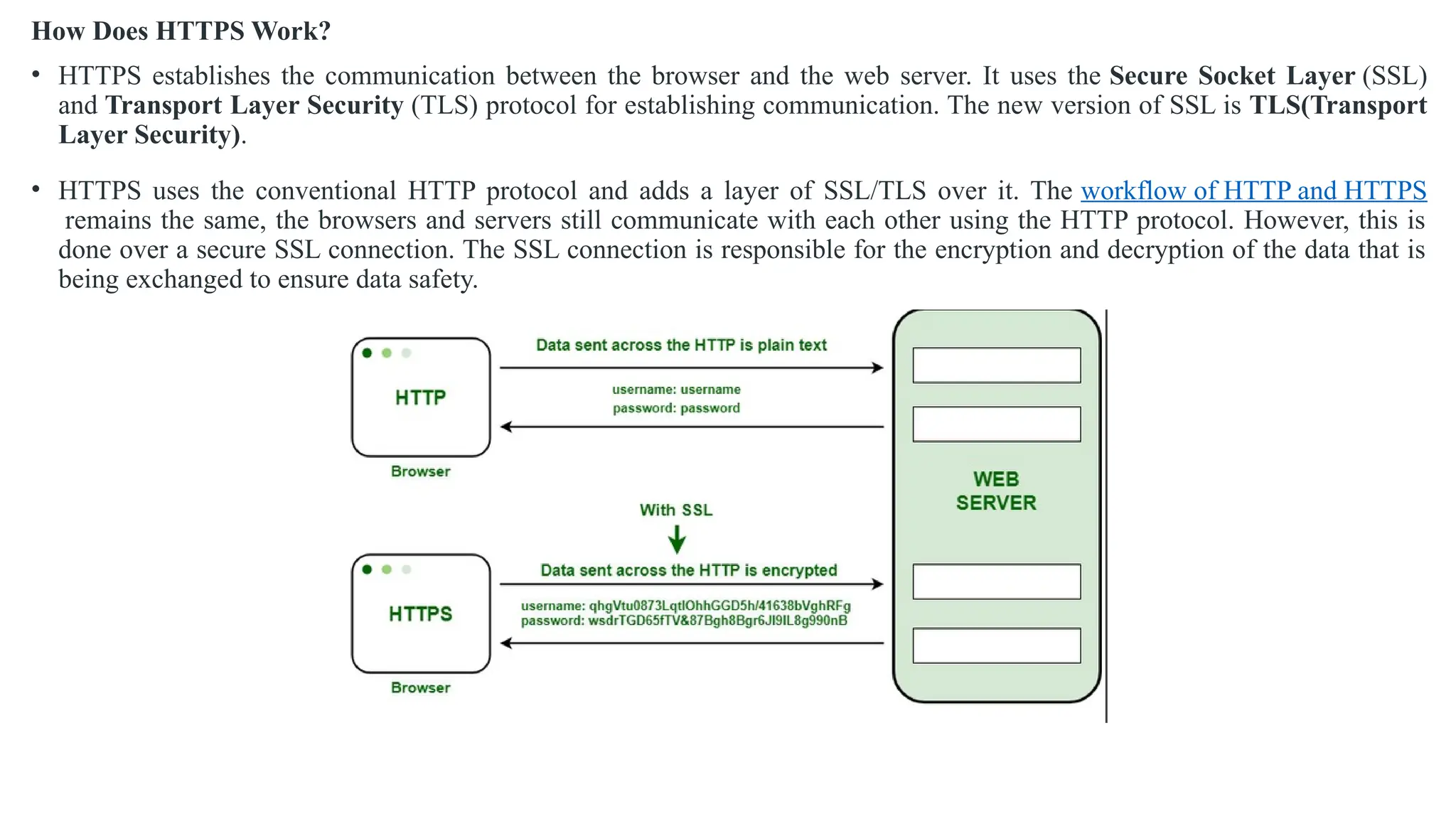
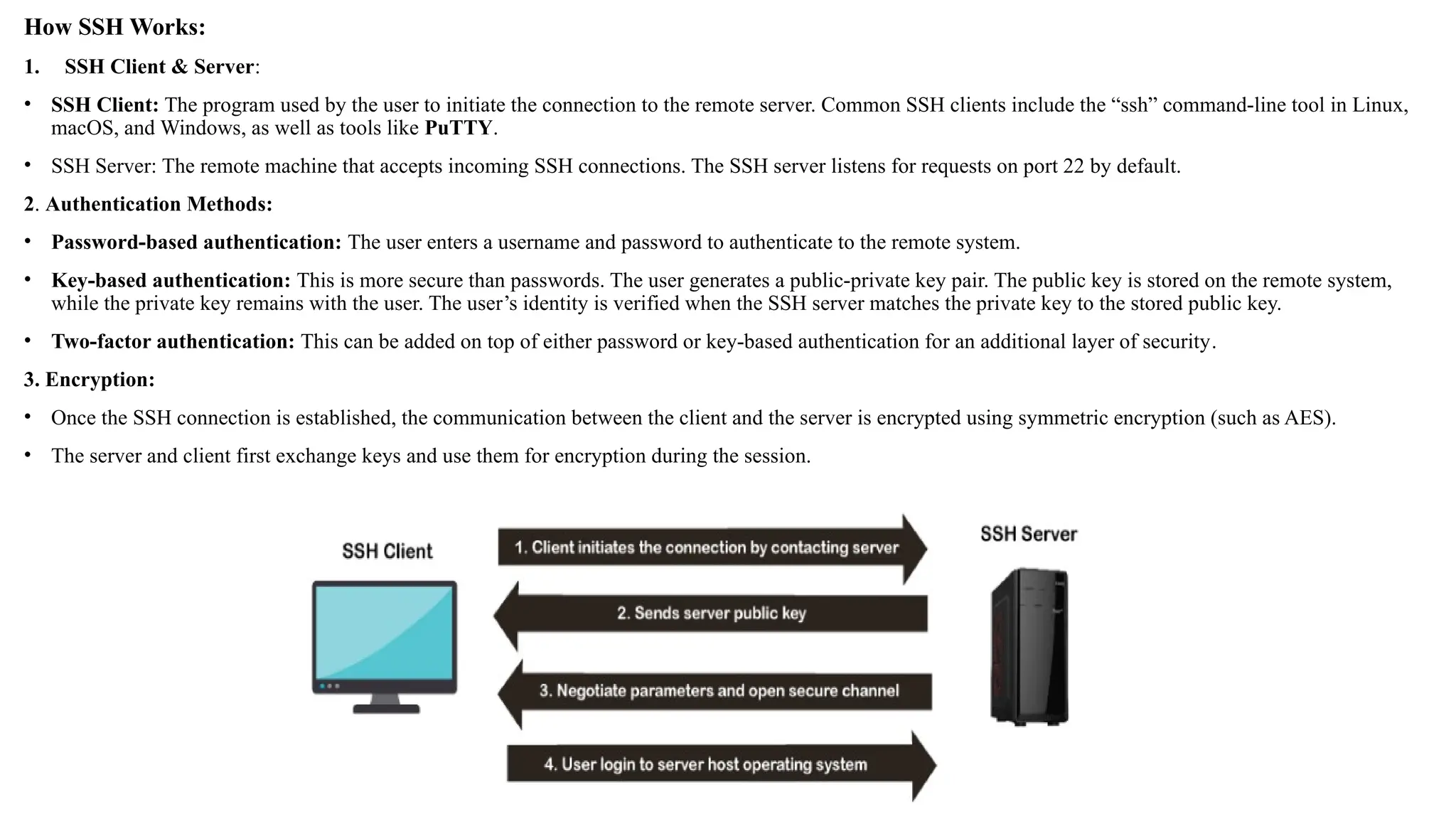
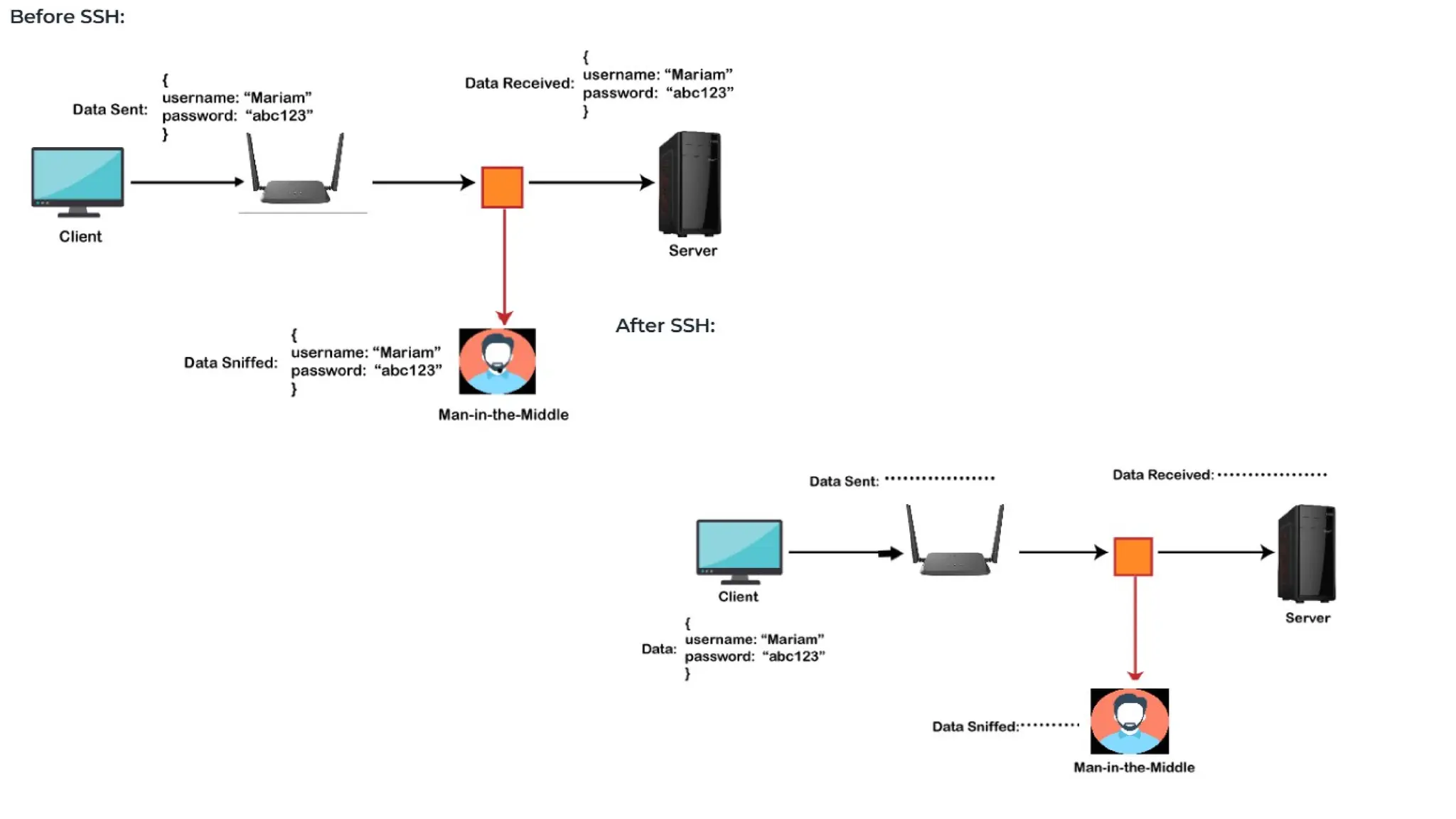
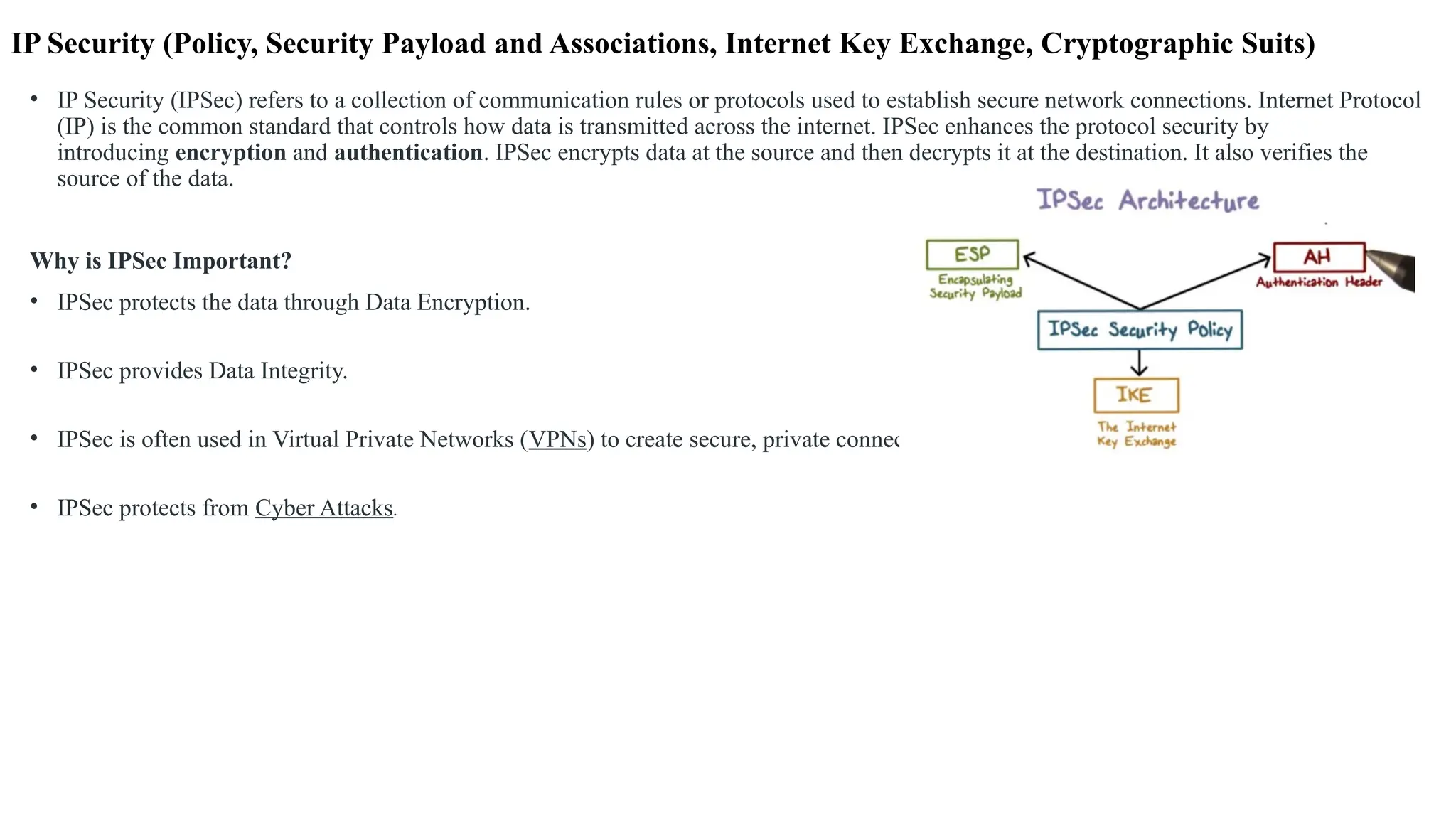
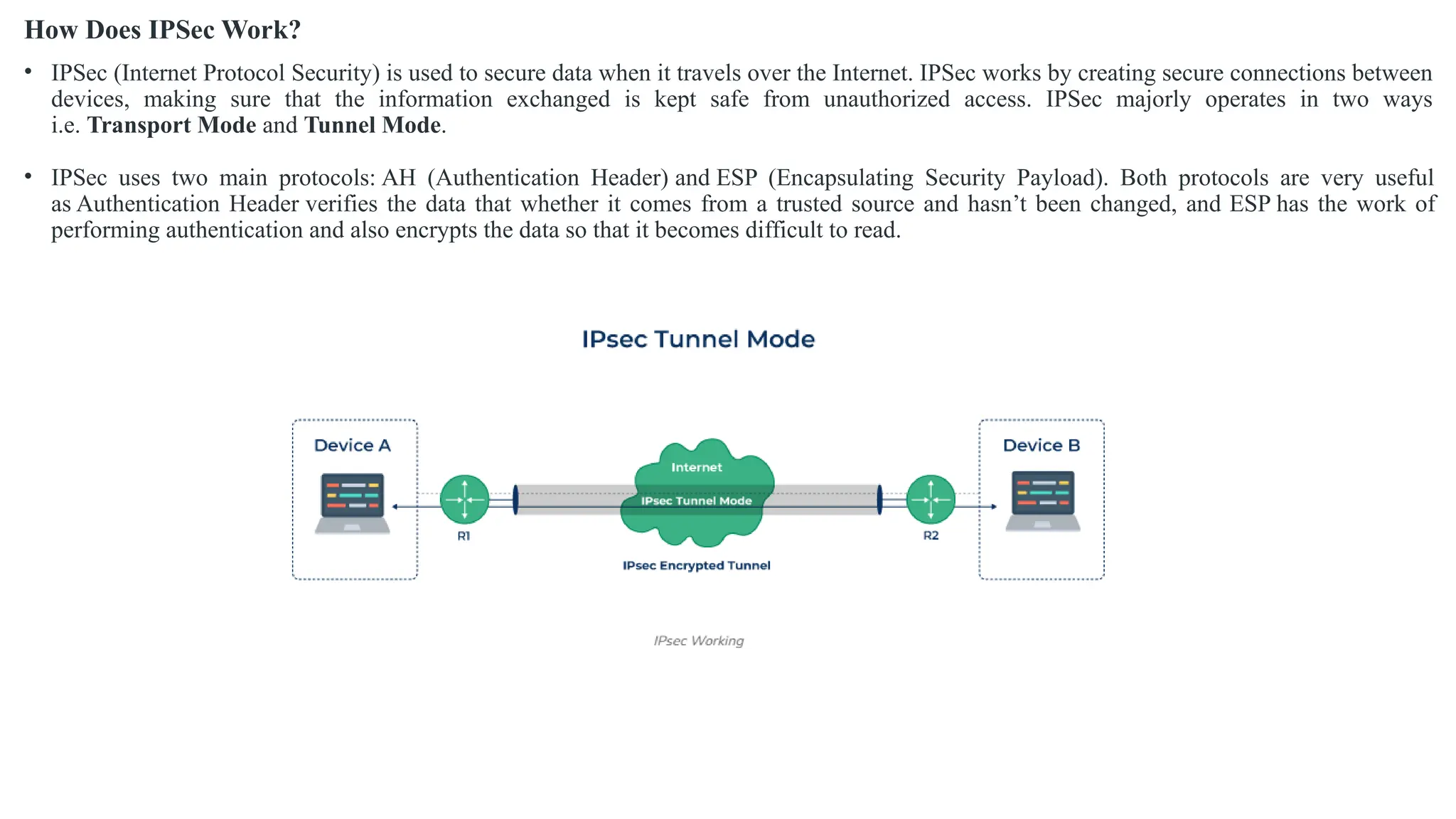
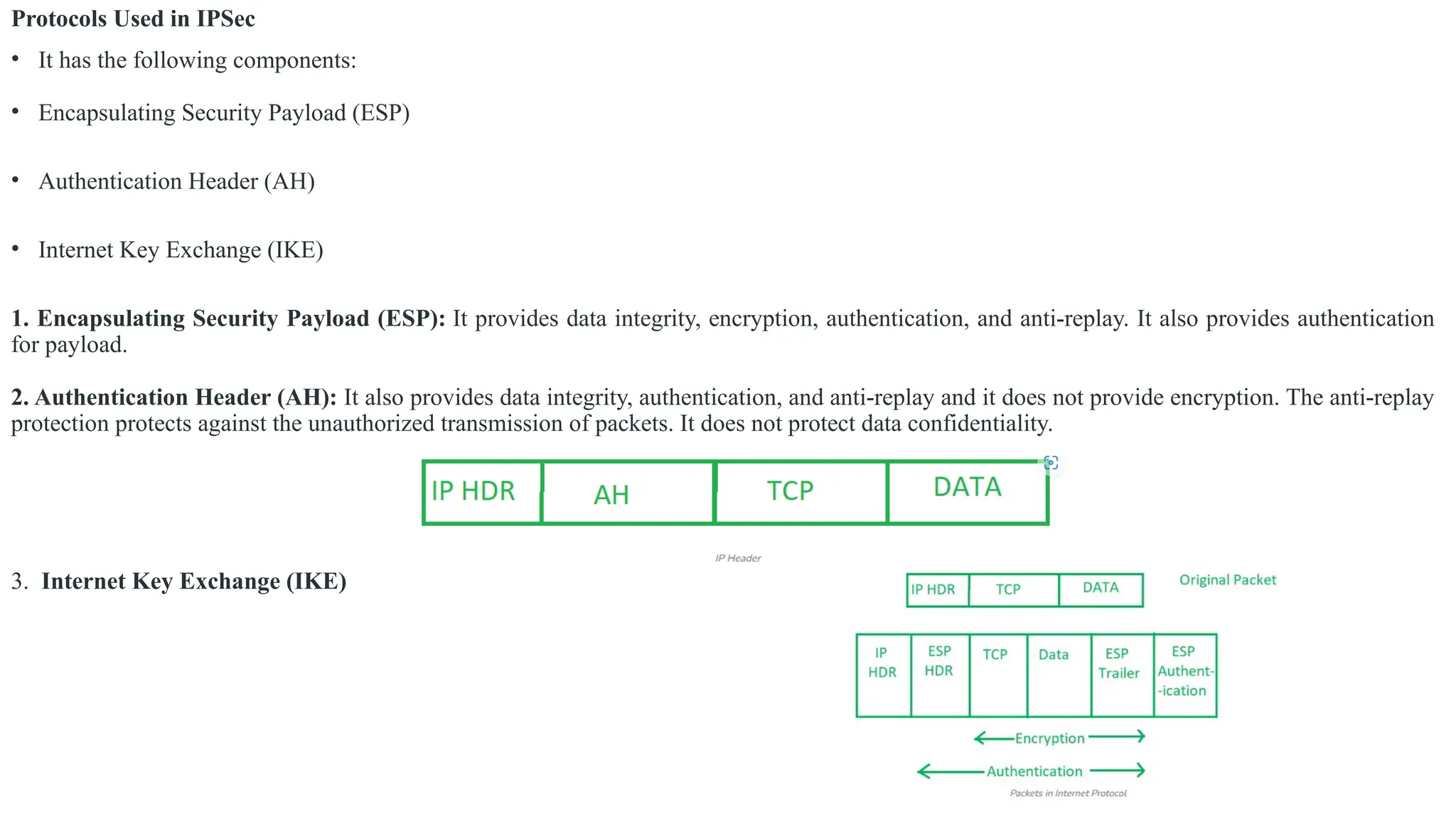
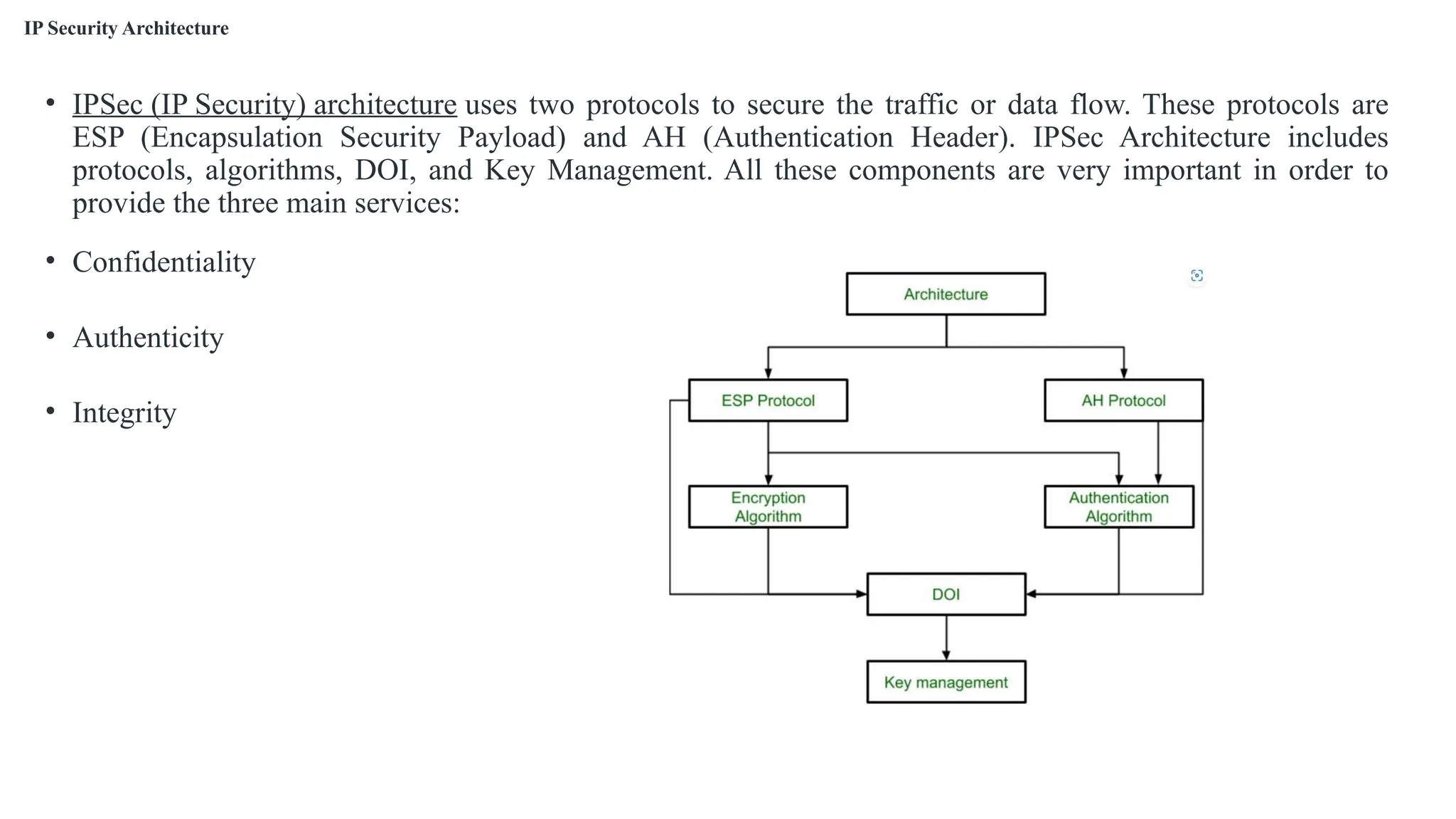
The document outlines network and internet security, emphasizing the importance of security models that encrypt communication to protect confidentiality and authenticity against threats. It details key components such as perimeter security, access control, and data protection, alongside email security protocols like DKIM, SPF, and DMARC that authenticate messages. Additionally, it covers transport layer security, including HTTPS and SSH protocols, which secure data transmission and remote access over the internet.