Embed presentation
Download to read offline


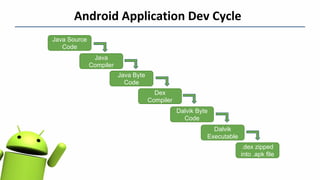
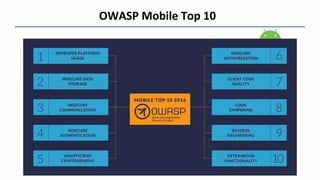


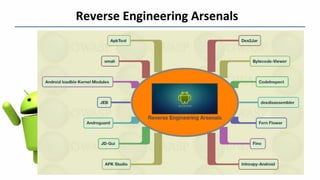
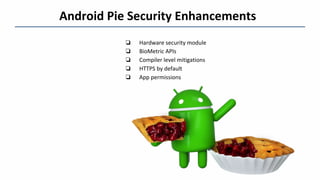

This document summarizes information from a presentation on pen testing Android apps. It discusses the Android application development cycle, the OWASP Mobile Top 10 security risks, additional focus areas beyond the top 10 like secure data storage and preventing reverse engineering. It also outlines some Android Pie security enhancements like the hardware security module and defaulting to HTTPS. The presentation concludes by thanking the audience.








