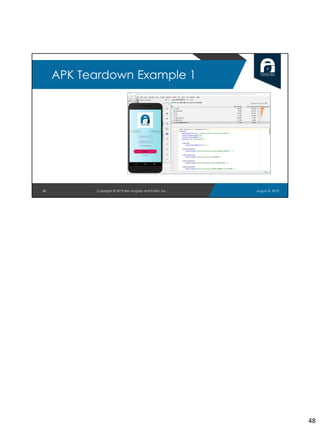
This document provides an agenda for a training session on hacking Android APK files at DEF CON 27 on August 8, 2019. The schedule includes introductions, static and dynamic analysis of APKs, forensic analysis, example teardowns, and a capture the flag exercise. The training team consists of three members - Ben Hughes, Liana Parakesyan, and Mattia Campagnano - and their bios are provided. An overview of the OWASP Mobile Top 10 security risks and the OWASP Mobile Security Testing Guide is also given to provide mobile security context. The document concludes by outlining approaches for setting up an Android testing environment including Android Studio, emulators, rooted devices, and common analysis tools.