This document discusses data-oriented attacks and provides an example of a data-only attack on the ProFTPd server. It introduces the concepts of data-oriented programming (DOP) and block-oriented programming (BOP). It also describes the BOPC framework, which uses symbolic execution and abstract representations of basic blocks to automate data-only attacks by modeling data flows between program blocks.

![Reference
● [0] 2019, Exploitation Techniques and Defenses for Data-
Oriented Attacks
● [1] 2018, Block Oriented Programming - Automating
Data-Only Attacks
● [2] 2016, Data-Oriented Programming - On the
Expressiveness of Non-Control Data Attacks
● [3] BOPC, https://github.com/HexHive/BOPC](https://image.slidesharecdn.com/anintroondata-orientedattacks-200119114117/85/An-Intro-on-Data-oriented-Attacks-2-320.jpg)
![DOA Overview [0][1][2]](https://image.slidesharecdn.com/anintroondata-orientedattacks-200119114117/85/An-Intro-on-Data-oriented-Attacks-3-320.jpg)
![The ProFTPd DOP Attack [0]](https://image.slidesharecdn.com/anintroondata-orientedattacks-200119114117/85/An-Intro-on-Data-oriented-Attacks-4-320.jpg)
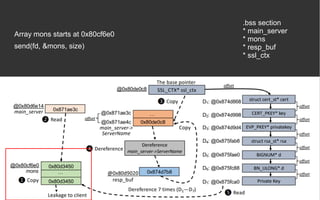
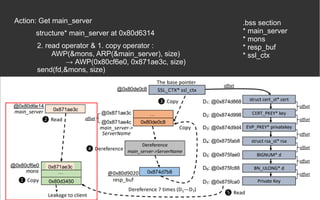
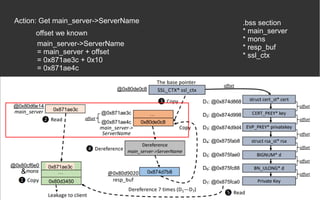
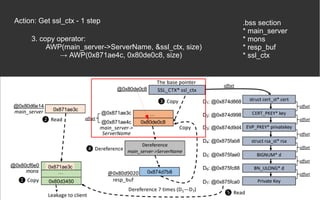
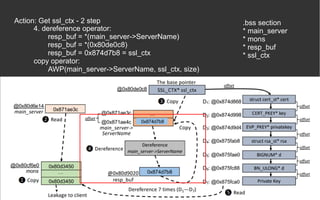
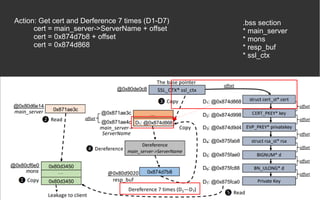
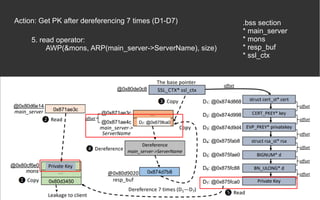
![BOPC – Block-oriented Programming
Compiler [2][3]
● AWP (hard requirement)
● Python 2
● Angr](https://image.slidesharecdn.com/anintroondata-orientedattacks-200119114117/85/An-Intro-on-Data-oriented-Attacks-12-320.jpg)
![The basic block "abstractions" [3]
● absblk.py
● Transition form a basic block to abstraction.(regwr,
splmemwr,..)](https://image.slidesharecdn.com/anintroondata-orientedattacks-200119114117/85/An-Intro-on-Data-oriented-Attacks-13-320.jpg)
![CFG -> For basic blocks -> abstractions [3]](https://image.slidesharecdn.com/anintroondata-orientedattacks-200119114117/85/An-Intro-on-Data-oriented-Attacks-14-320.jpg)
![Angr
● Block-oriented symbolic execution
● status.history.actions
– action.type == 'reg' and action.action == 'write'
– action.type == 'mem' and action.action == 'read
– action.type == 'exit' and action.exit_type == 'conditional'
● blk.vex.jumpkind == "Ijk_Sys_syscall"
– BYPASS_UNSUPPORTED_SYSCALL
● state.se.constraints (AST)
– <Bool packet_0_stdin_6_480[471:464] != 13>
● state.posix.dumps(0)
● Initial .bss/ .data section
● project.inspect.make_breakpoint('mem_read', ...)](https://image.slidesharecdn.com/anintroondata-orientedattacks-200119114117/85/An-Intro-on-Data-oriented-Attacks-15-320.jpg)
![On the Fly to Resolve the Constraints [2]](https://image.slidesharecdn.com/anintroondata-orientedattacks-200119114117/85/An-Intro-on-Data-oriented-Attacks-16-320.jpg)
![Constraint Issues [2]](https://image.slidesharecdn.com/anintroondata-orientedattacks-200119114117/85/An-Intro-on-Data-oriented-Attacks-17-320.jpg)
![simulate.py [3]](https://image.slidesharecdn.com/anintroondata-orientedattacks-200119114117/85/An-Intro-on-Data-oriented-Attacks-18-320.jpg)