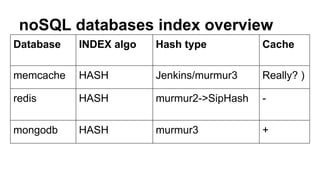
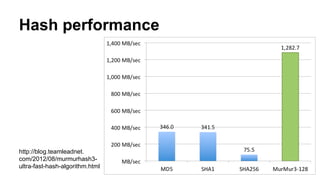
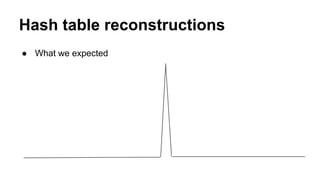
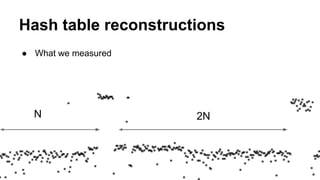
This document discusses timing attacks on (no)SQL databases. It begins by explaining how the execution time of a database function like SELECT can depend on both the search string and private data, allowing an attacker to determine private data by measuring timing differences for different search strings. It then provides examples of related work on timing attacks and an overview of indexing algorithms and hash types used by various SQL and noSQL databases. The document discusses how caching, cache warming, and hash table reconstruction can be used in timing attacks. It concludes by mentioning a proof-of-concept tool for timing attacks and an example of a real timing attack case involving session entropy reduction and password hash reduction.