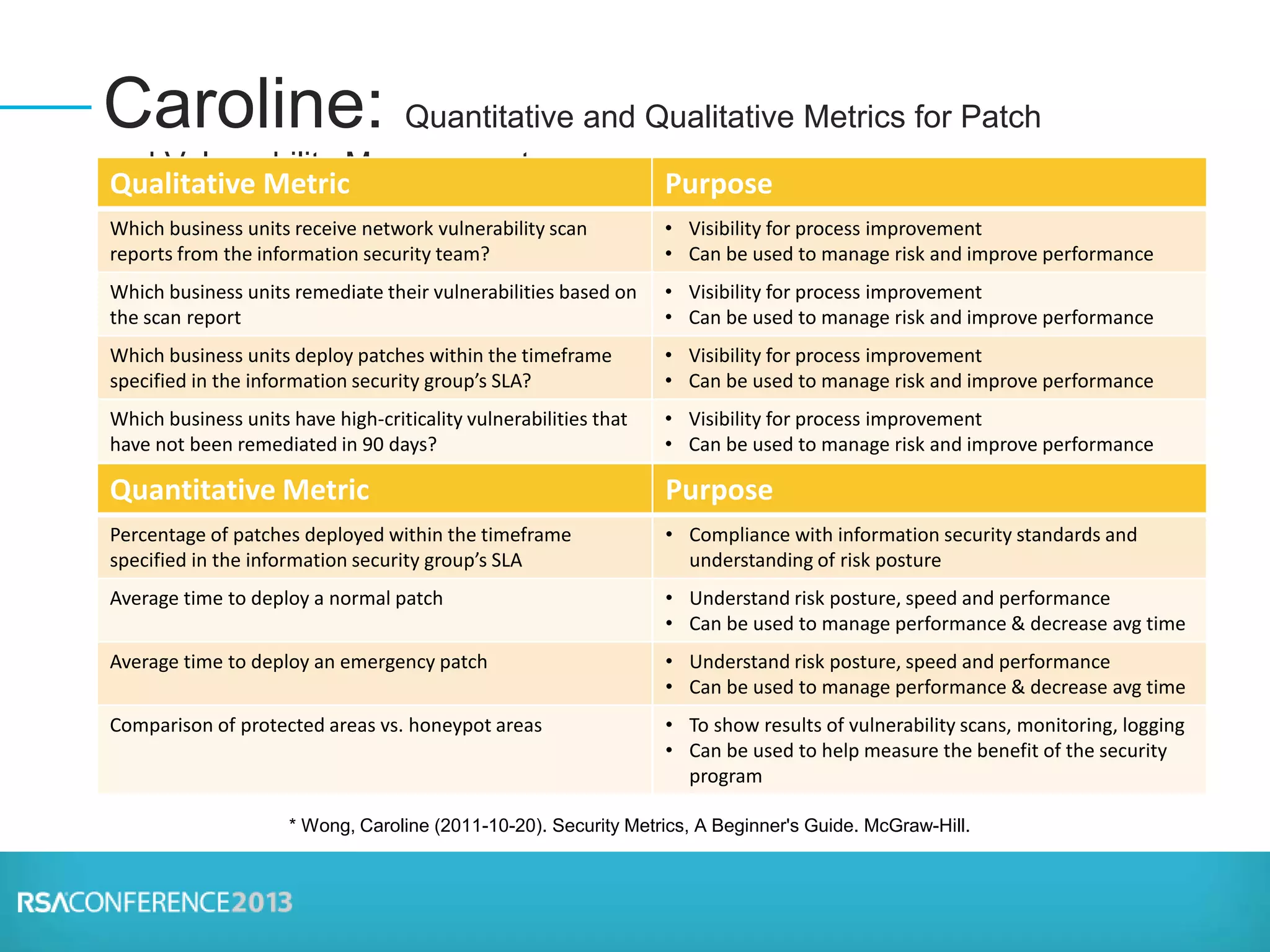
The document discusses the importance of risk management in security, defining risks, and developing meaningful metrics to enhance decision-making and reduce risk in organizations. It emphasizes the need for both qualitative and quantitative metrics to track vulnerabilities and improve governance, aligning security practices with business objectives. Key takeaways include the idea that all metrics involve risk interpretation and the necessity of robust governance supported by effective metrics.