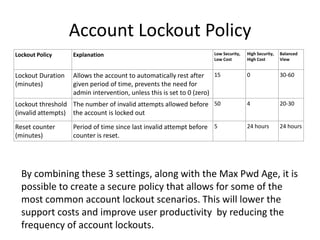
The document discusses active directory password policies aimed at preventing account lockout issues in enterprise environments through various components that balance security and user convenience. It highlights common causes of account lockouts such as cached credentials, system errors, and user mistakes, while suggesting strategies for effective password policies. The author recommends using specific settings to mitigate lockouts and improve user productivity, encouraging administrators to adjust policies for optimal security and usability.