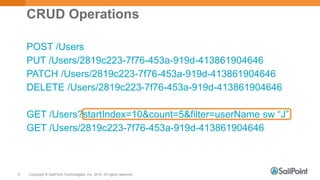
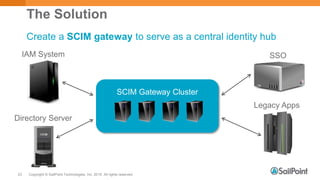
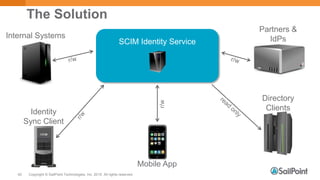
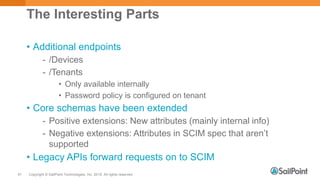
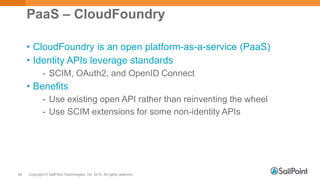
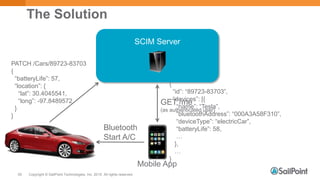
The document discusses System for Cross-domain Identity Management (SCIM), explaining its role in identity management, REST architecture, and trends in its usage across enterprises and service providers. It presents case studies showcasing SCIM's implementation as a central identity hub for various organizations, enabling extensibility and standardization in identity APIs. Current SCIM developments and future extensions are also highlighted, indicating growing adoption in the industry.






![Copyright © SailPoint Technologies, Inc. 2015 All rights reserved.7
Example – Retrieve User Response
HTTP/1.1 200 OK
Content-Type: application/scim+json
Location: https://example.com/v2/Users/2819c223-7f76-453a-919d-413861904646
{
"schemas":["urn:ietf:params:scim:schemas:core:2.0:User"],
"id": "2819c223-7f76-453a-919d-413861904646",
"name": {
"formatted": "Ms. Barbara J Jensen III",
"familyName": "Jensen",
"givenName": "Barbara“
},
"meta": {
"resourceType": "User",
"created": "2011-08-01T18:29:49.793Z",
...
}
}
Self-describing
payload
Single-valued
attribute
Complex
attribute
Many
data types](https://image.slidesharecdn.com/scimcis2015-150616043211-lva1-app6891/85/SCIM-in-the-Real-World-Adoption-is-Growing-7-320.jpg)