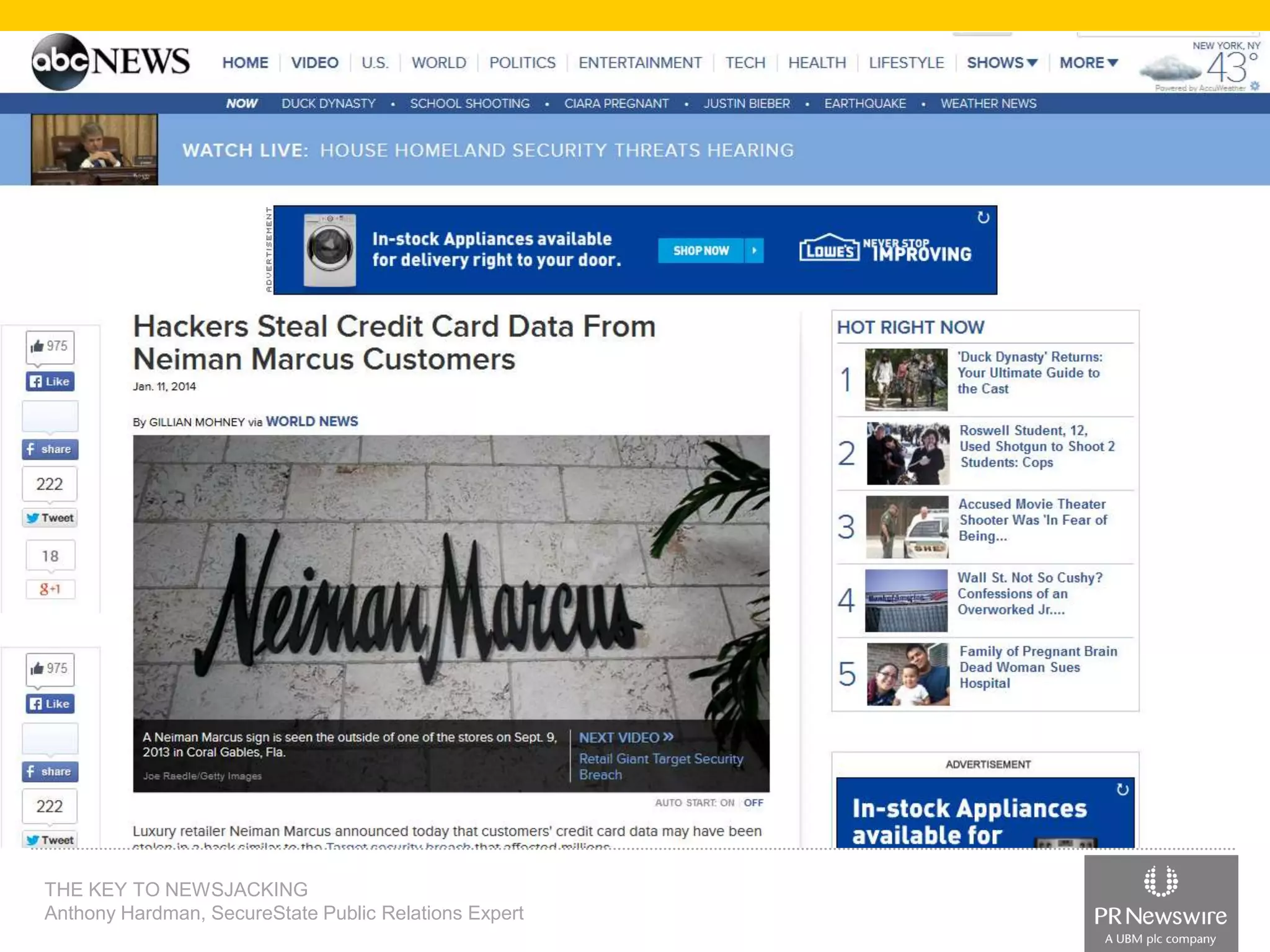
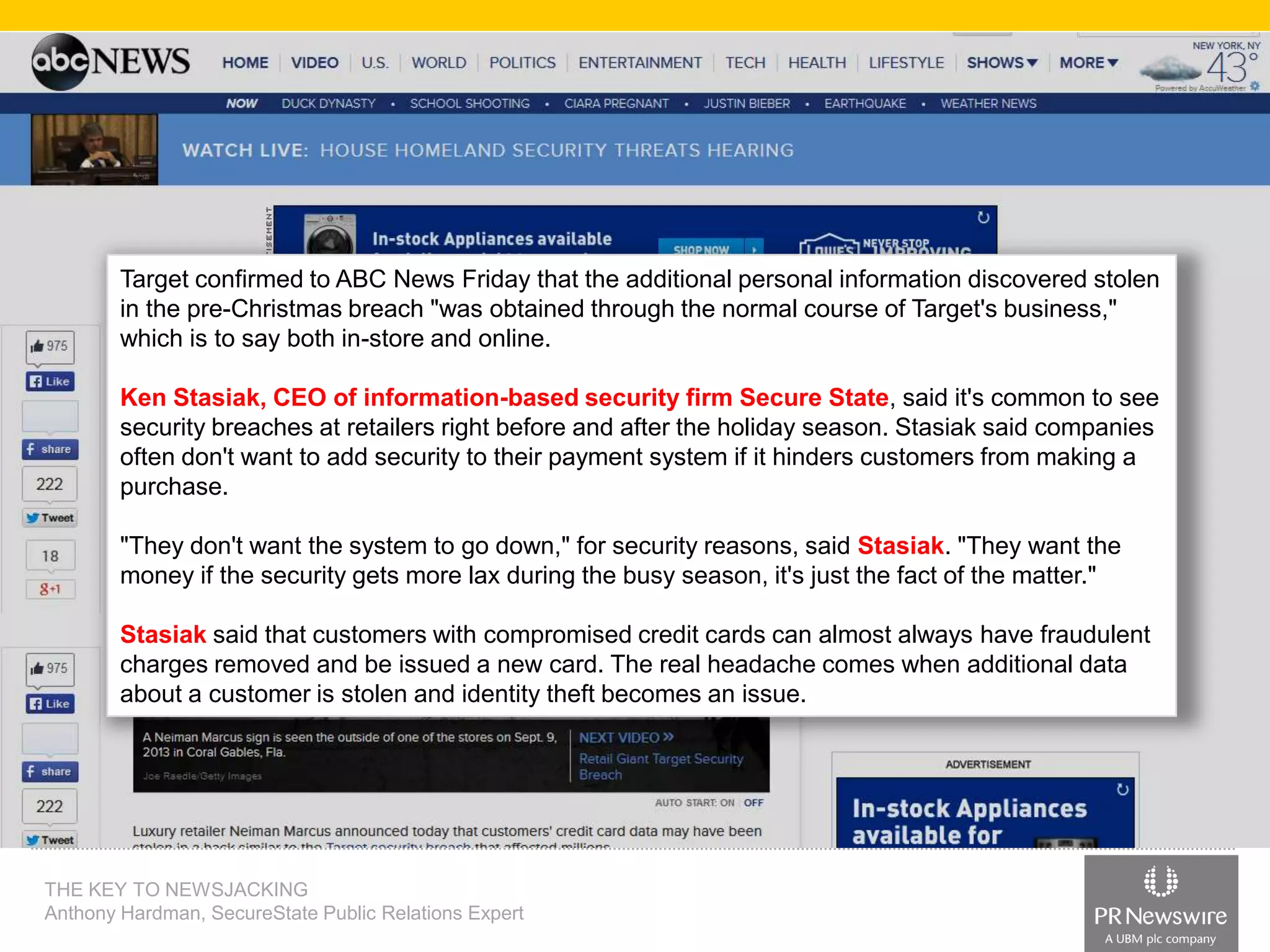
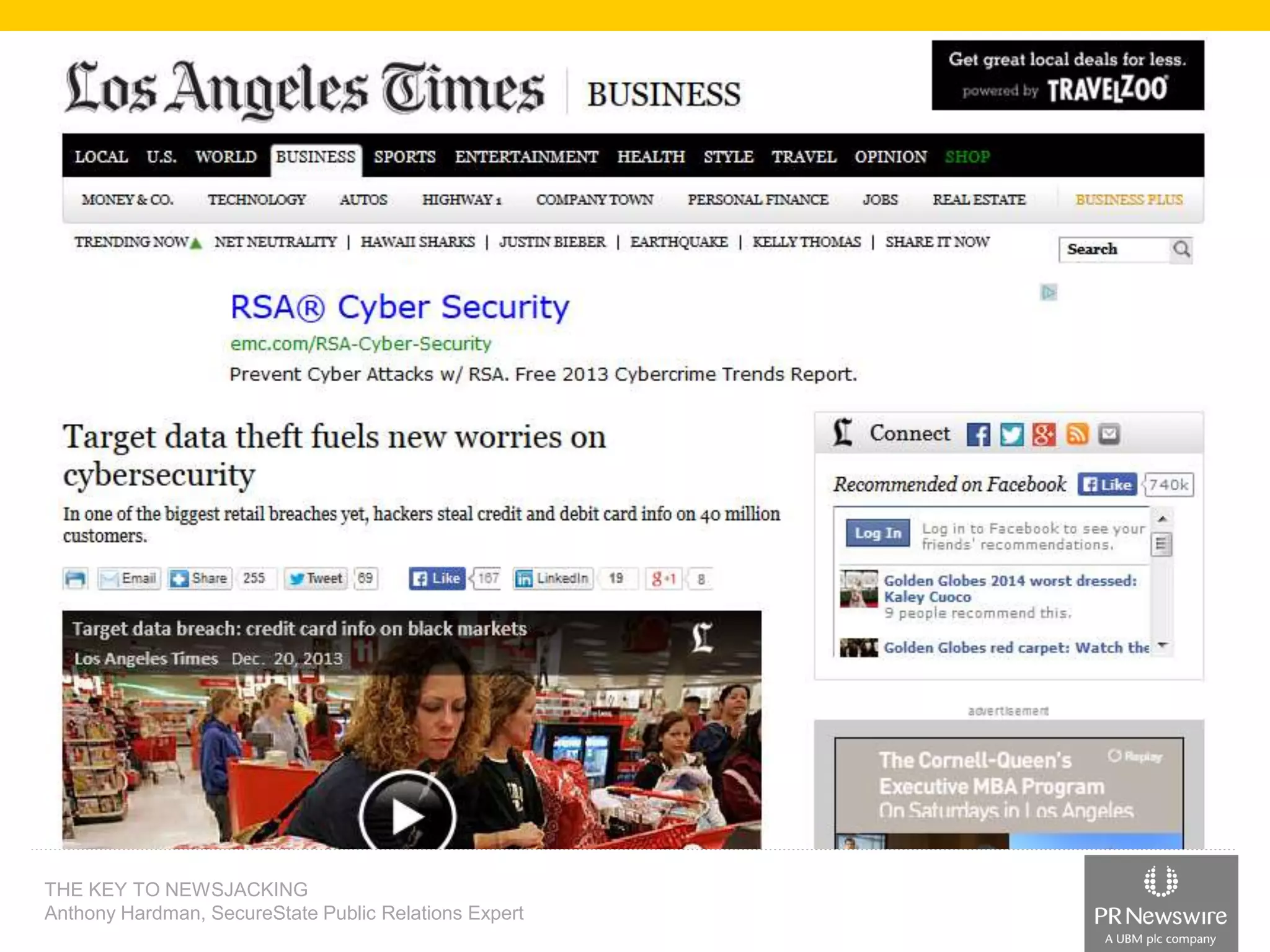
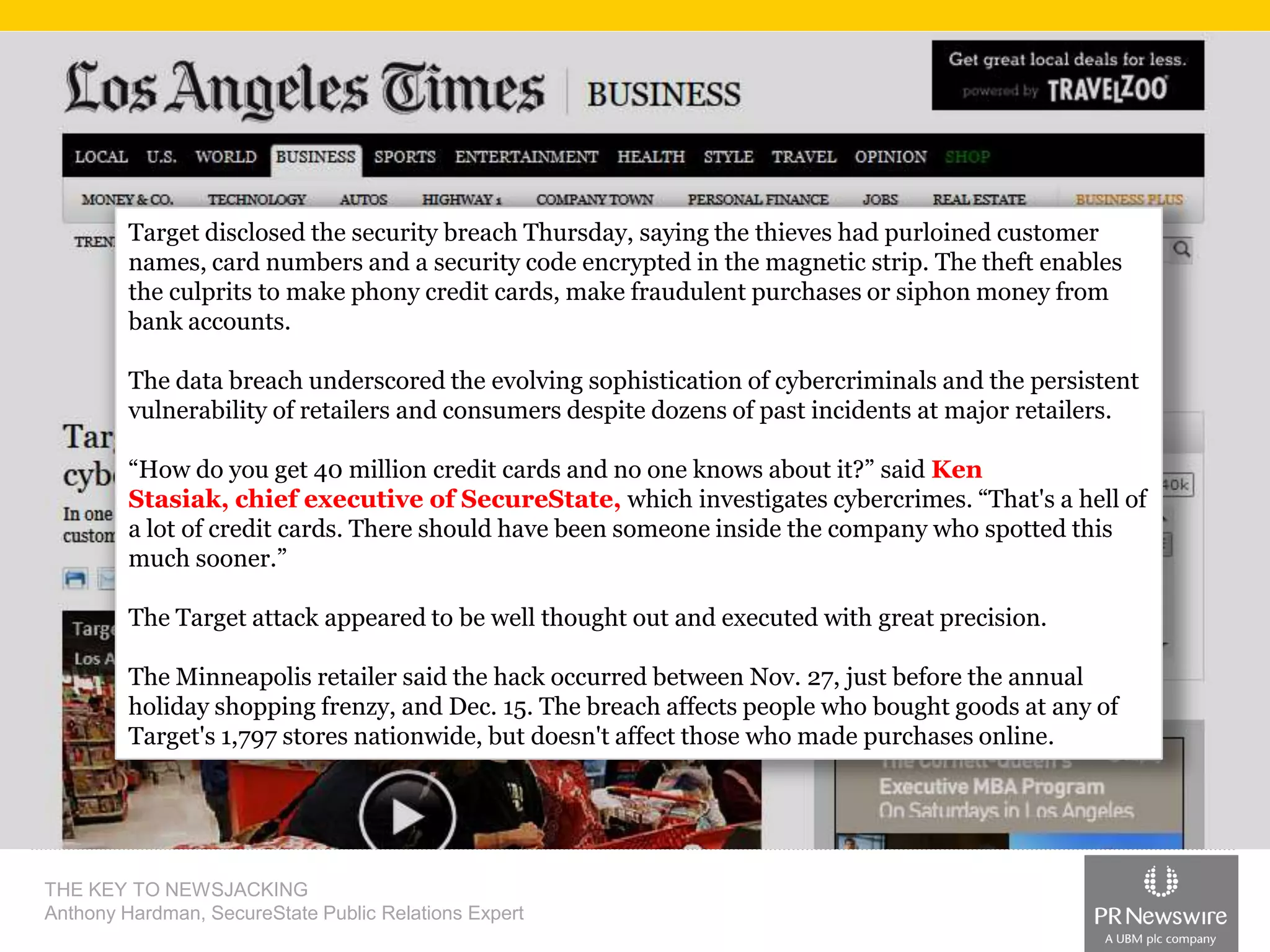
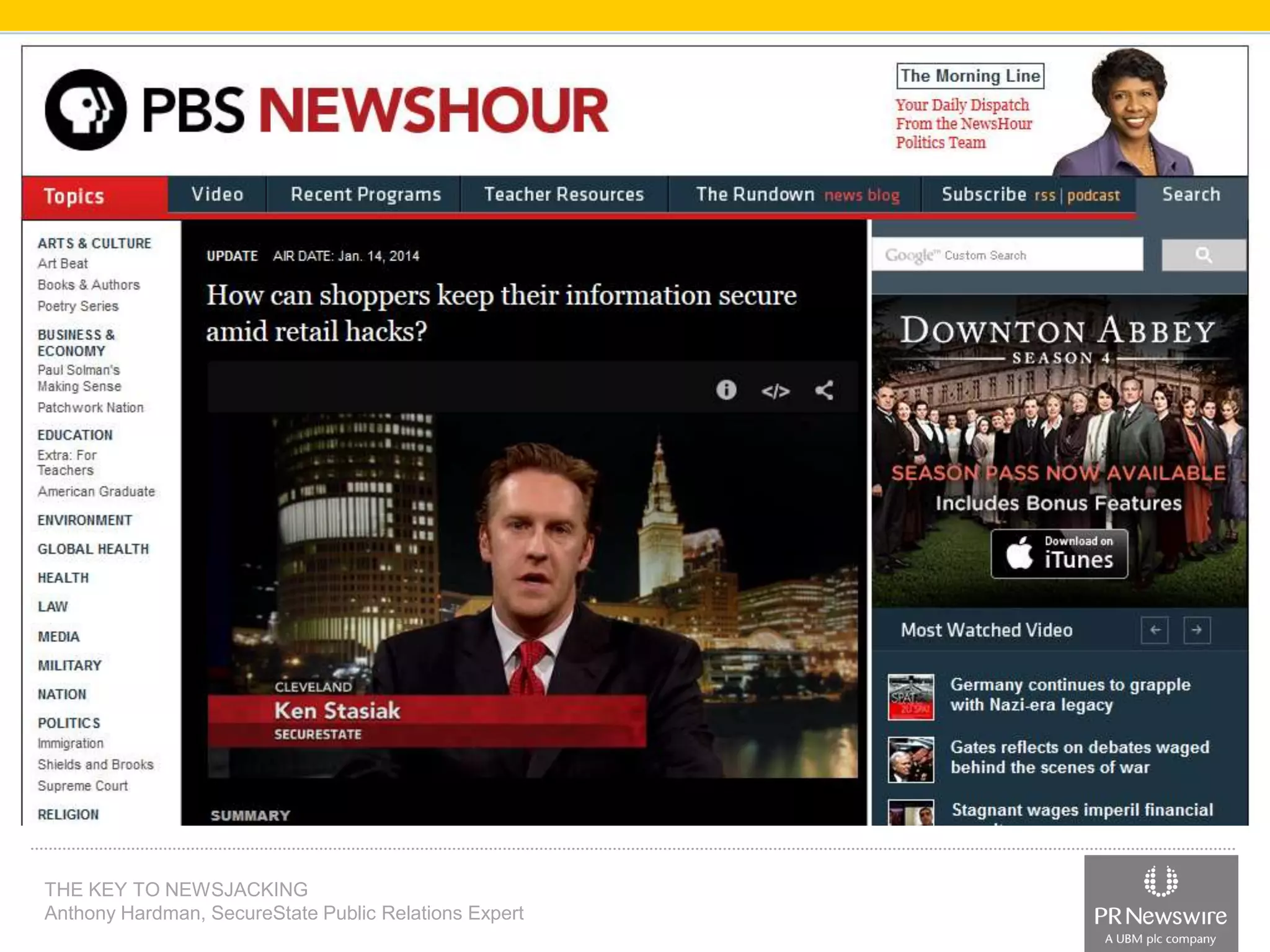
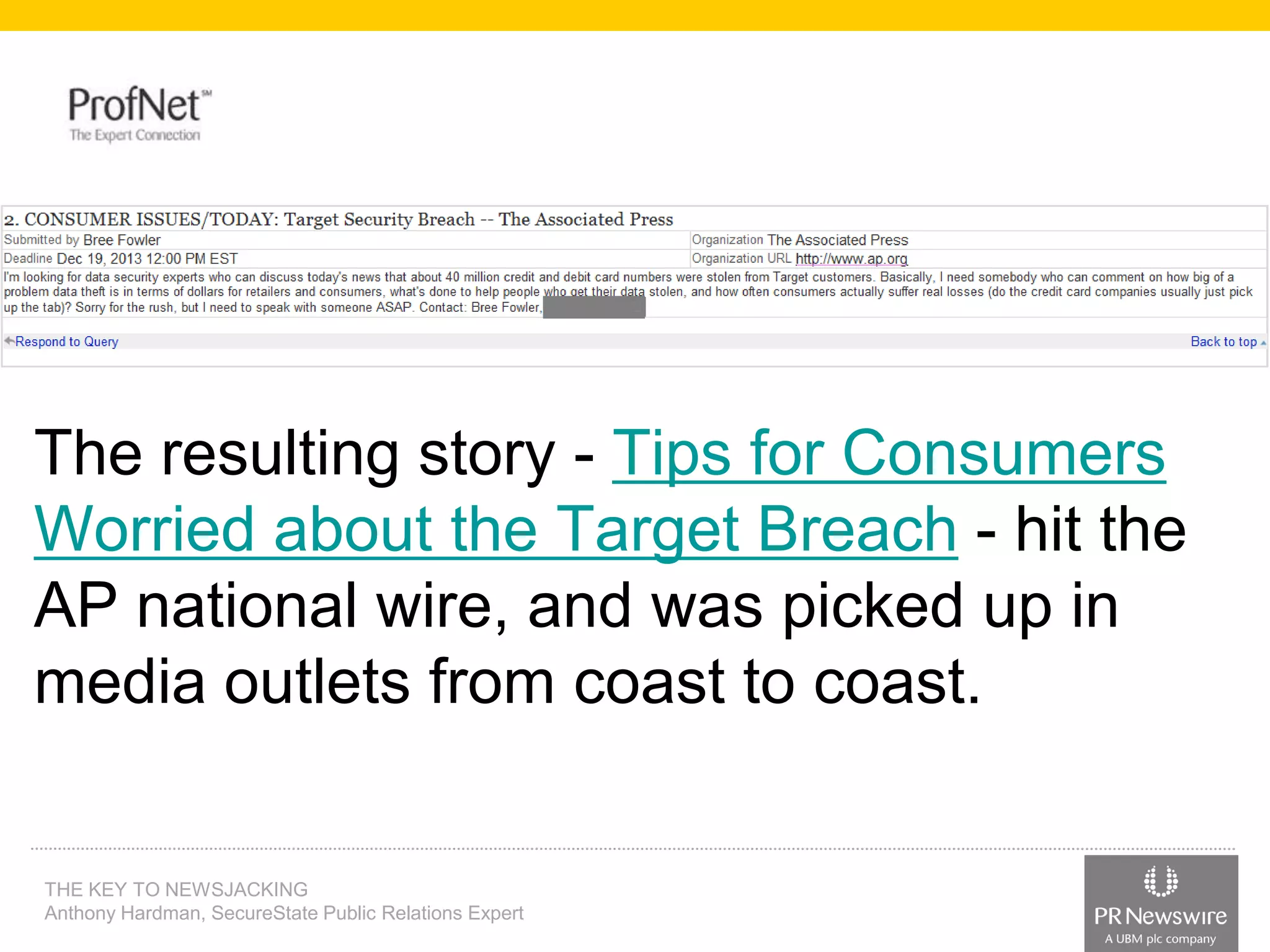
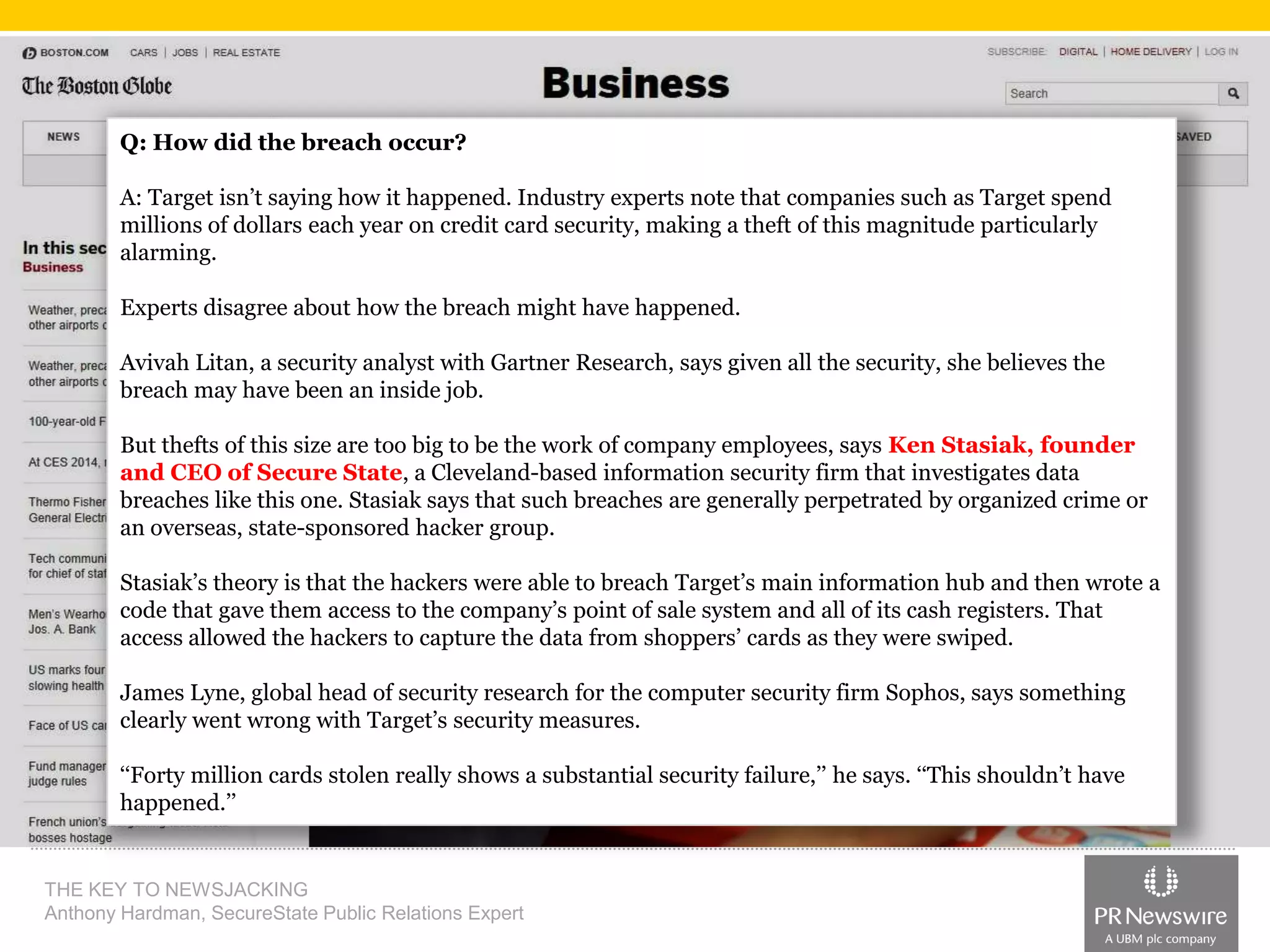
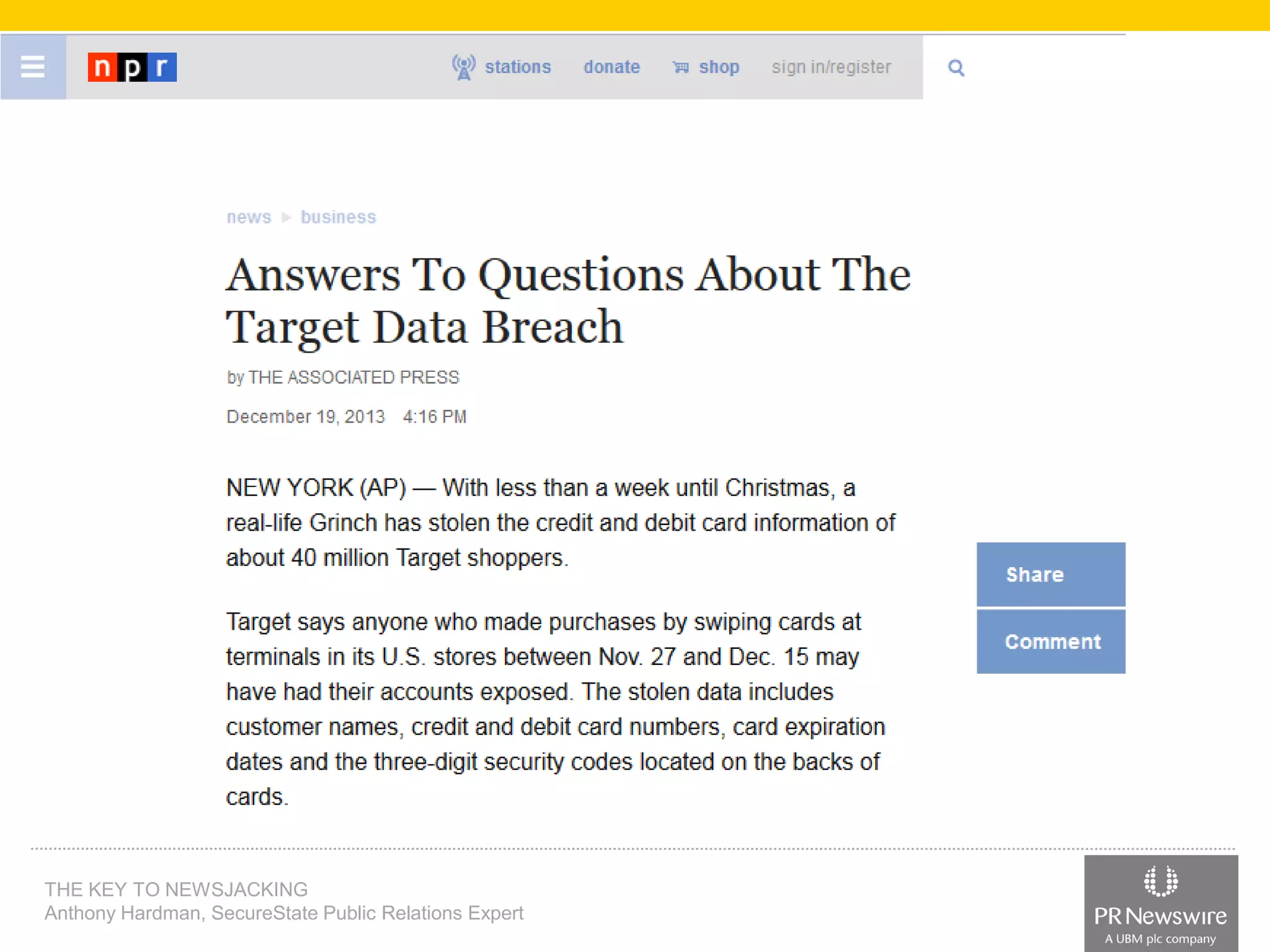
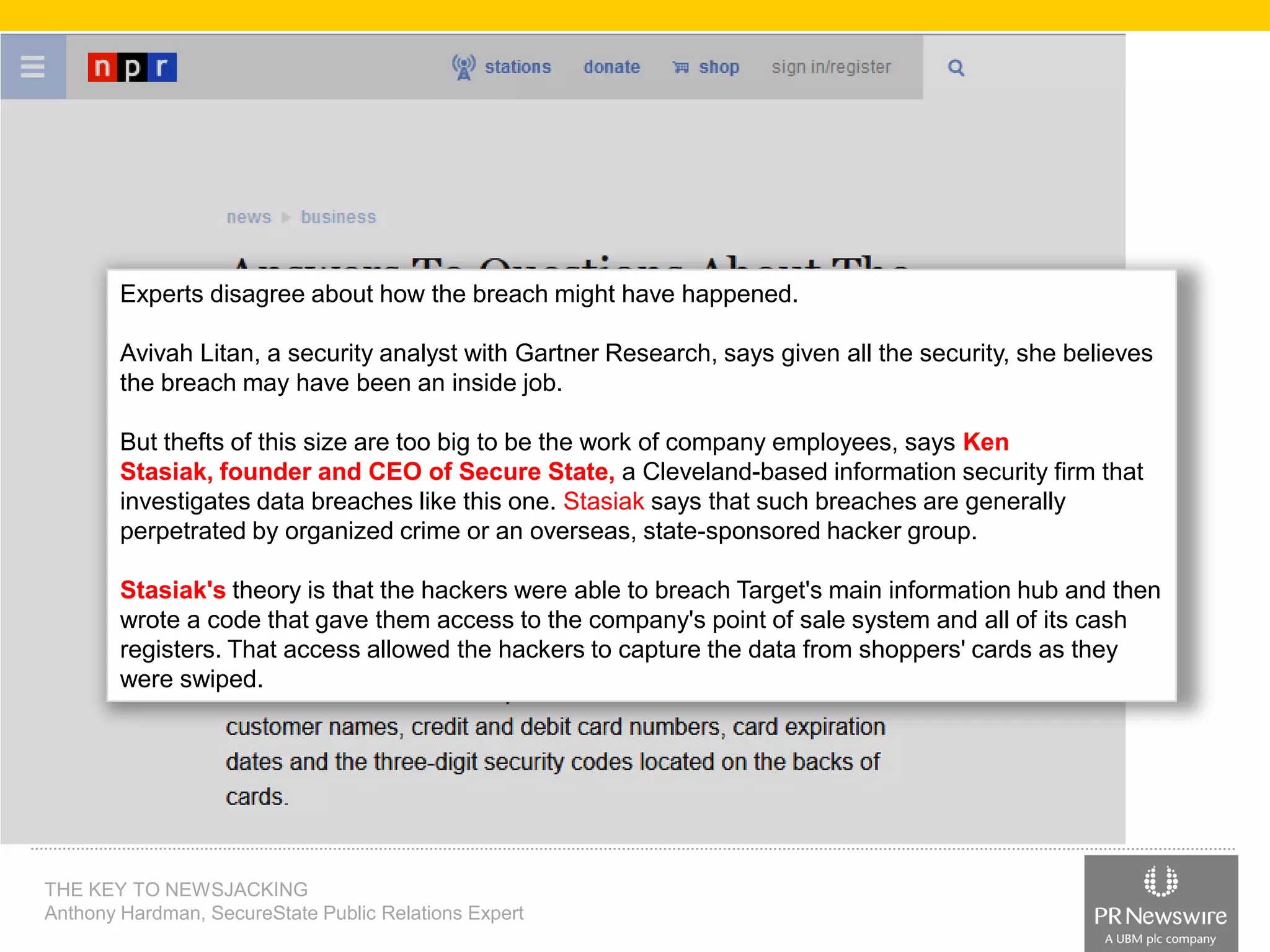
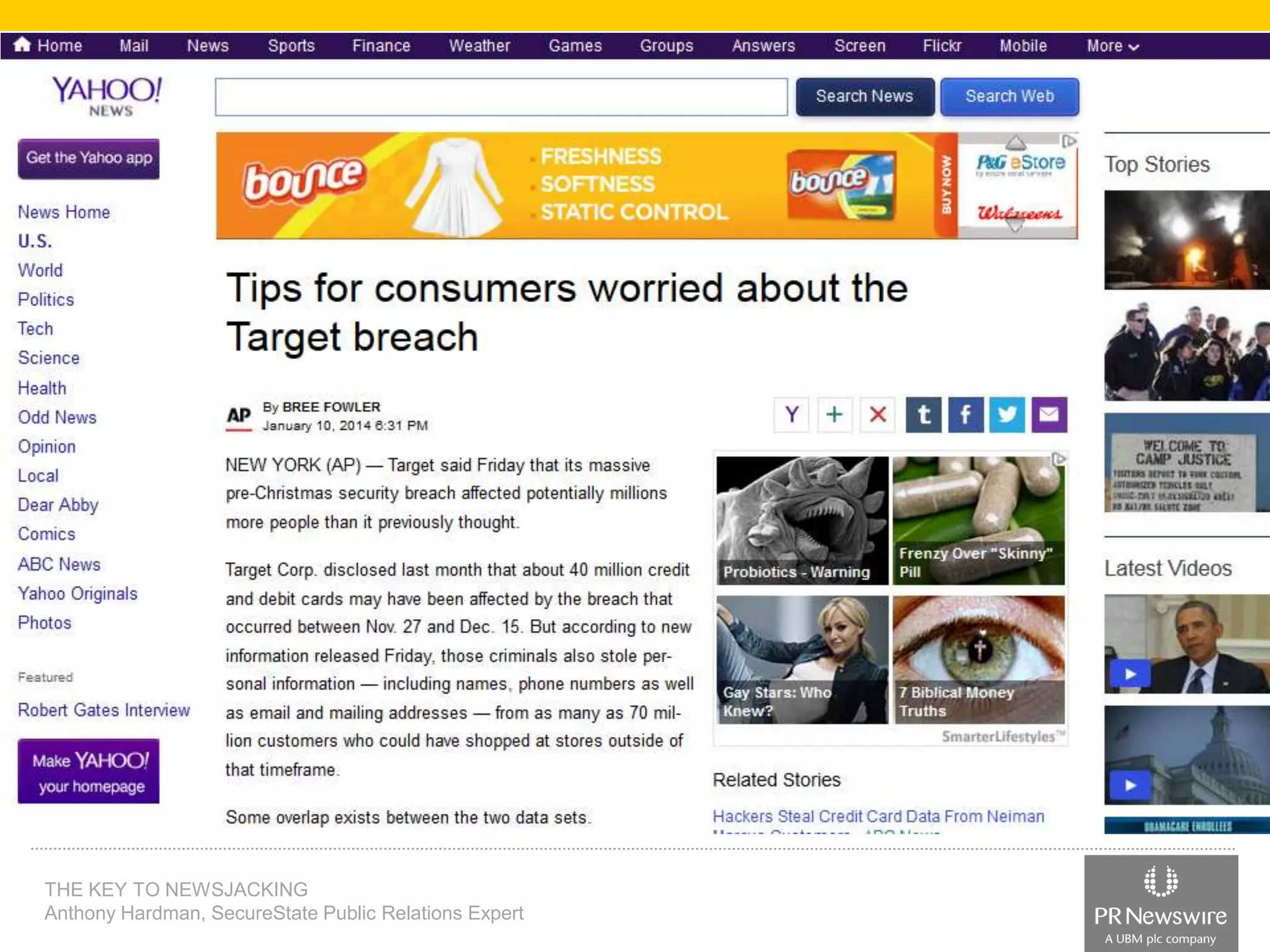
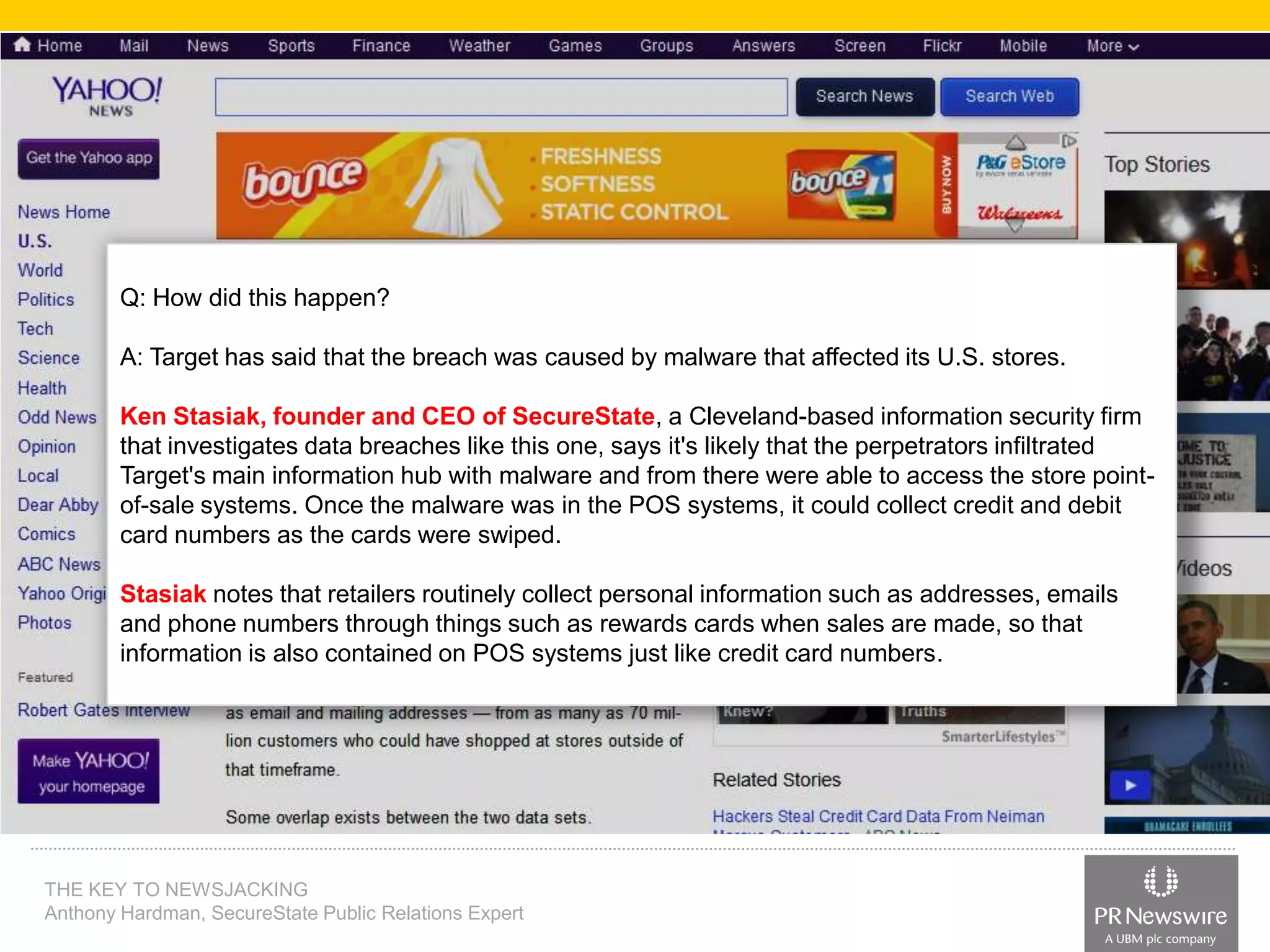
Anthony Hardman, a public relations expert at SecureState, successfully executed a newsjack during a significant data breach at Target, leveraging existing media relationships and common PR tools. His strategic approach involved creating targeted media lists, responding to journalist queries, and utilizing owned media to amplify coverage, resulting in substantial press for SecureState. The incident underscored the vulnerabilities of retailers and the importance of agile PR strategies in crisis situations.