This article presents the findings of one hundred errors identified through static code analysis in open-source C/C++ projects using the PVS-Studio analyzer. It categorizes various error samples, including array handling issues, string miscalculations, and examples of undefined behavior, highlighting notable cases from specific projects like Wolfenstein 3D and Chromium. The authors emphasize the prevalence of such defects and the potential implications for programmers, encouraging awareness and best practices in coding.
![The error was found through the V568 diagnostic: It's odd that the argument of sizeof() operator is the
'&itemInfo' expression. cgame cg_weapons.c 1467.
The sizeof() operator calculates the size of the pointer instead of the 'itemInfo_t' structure's size. It is
"sizeof(*itemInfo)" that must be written.
Example 2. Wolfenstein 3D project. Only part of a matrix is cleared.
ID_INLINE mat3_t::mat3_t( float src[ 3 ][ 3 ] ) {
memcpy( mat, src, sizeof( src ) );
}
The error was found through the V511: The sizeof() operator returns size of the pointer, and not of the
array, in 'sizeof(src)' expression. Splines math_matrix.h 94
Usually programmers expect 'sizeof(src)' to return the size of an array equal to "3*3*sizeof(float)" bytes.
But according to the language standard, 'src' is just a pointer, not an array. Thus, the matrix will be
copied only partly. The 'memcpy' function will copy 4 or 8 bytes (the pointer size) depending on whether
the code is 32-bit or 64-bit.
If you want the whole matrix to be copied, you may pass a reference to the array into the function. This
is the correct code:
ID_INLINE mat3_t::mat3_t( float (&src)[3][3] )
{
memcpy( mat, src, sizeof( src ) );
}
Example 3. FAR Manager project. Only part of an array is cleared.
struct TreeItem
{
int *Last;
size_t LastCount;
...
void Clear()
{
strName.Clear();
memset(Last, 0, sizeof(Last));](https://image.slidesharecdn.com/bugs-100-130729071042-phpapp02/75/100-bugs-in-Open-Source-C-C-projects-3-2048.jpg)

![Example 5. VirtualDub project. Array overrun (explicit index).
struct ConvoluteFilterData {
long m[9];
long bias;
void *dyna_func;
DWORD dyna_size;
DWORD dyna_old_protect;
BOOL fClip;
};
static unsigned long __fastcall do_conv(
unsigned long *data,
const ConvoluteFilterData *cfd,
long sflags, long pit)
{
long rt0=cfd->m[9], gt0=cfd->m[9], bt0=cfd->m[9];
...
}
The code was found through the V557 diagnostic: Array overrun is possible. The '9' index is pointing
beyond array bound. VirtualDub f_convolute.cpp 73
It is not a real error, but good diagnostic. Explanation: http://www.viva64.com/go.php?url=756.
Example 6. CPU Identifying Tool project. Array overrun (index in a macro).
#define FINDBUFFLEN 64 // Max buffer find/replace size
...
int WINAPI Sticky (...)
{
...
static char findWhat[FINDBUFFLEN] = {'0'};](https://image.slidesharecdn.com/bugs-100-130729071042-phpapp02/75/100-bugs-in-Open-Source-C-C-projects-5-2048.jpg)
![...
findWhat[FINDBUFFLEN] = '0';
...
}
The error was found through the V557 diagnostic: Array overrun is possible. The '64' index is pointing
beyond array bound. stickies stickies.cpp 7947
This error is a kind of the previous one. The terminal null is written outside the array. The correct code
is: "findWhat[FINDBUFFLEN - 1] = '0';".
Example 7. Wolfenstein 3D project. Array overrun (incorrect expression).
typedef struct bot_state_s
{
...
char teamleader[32]; //netname of the team leader
...
} bot_state_t;
void BotTeamAI( bot_state_t *bs ) {
...
bs->teamleader[sizeof( bs->teamleader )] = '0';
...
}
The error was found through the V557 diagnostic: Array overrun is possible. The 'sizeof (bs-
>teamleader)' index is pointing beyond array bound. game ai_team.c 548
Here is one more example of an array overrun when using an explicitly declared index. These samples
show that such simple at first sight errors are much more widely-spread than it may seem.
The terminal null is written outside the 'teamleader' array. This is the correct code:
bs->teamleader[
sizeof(bs->teamleader) / sizeof(bs->teamleader[0]) - 1
] = '0';](https://image.slidesharecdn.com/bugs-100-130729071042-phpapp02/75/100-bugs-in-Open-Source-C-C-projects-6-2048.jpg)
![Example 8. Miranda IM project. Only part of a string is copied.
typedef struct _textrangew
{
CHARRANGE chrg;
LPWSTR lpstrText;
} TEXTRANGEW;
const wchar_t* Utils::extractURLFromRichEdit(...)
{
...
::CopyMemory(tr.lpstrText, L"mailto:", 7);
...
}
The error was found through the V512 diagnostic: A call of the 'memcpy' function will lead to a buffer
overflow or underflow. tabsrmm utils.cpp 1080
If Unicode-strings are used, one character occupies 2 or 4 bytes (depending on the data model being
used in compiler) instead of one byte. Unfortunately, programmers easily forget about it, and you can
often see defects like our example in programs.
The 'CopyMemory' function will copy only part of the L"mailto:" string since it handles bytes, not
characters. You can fix the code by using a more appropriate function for string copying or, at least,
multiplying number 7 by sizeof(wchar_t).
Example 9. CMake project. Array overrun inside a loop.
static const struct {
DWORD winerr;
int doserr;
} doserrors[] =
{
...
};](https://image.slidesharecdn.com/bugs-100-130729071042-phpapp02/75/100-bugs-in-Open-Source-C-C-projects-7-2048.jpg)
![static void
la_dosmaperr(unsigned long e)
{
...
for (i = 0; i < sizeof(doserrors); i++)
{
if (doserrors[i].winerr == e)
{
errno = doserrors[i].doserr;
return;
}
}
...
}
The error was found through the V557 diagnostic: Array overrun is possible. The value of 'i' index could
reach 367. cmlibarchive archive_windows.c 1140, 1142
The error handler itself contains an error. The sizeof() operator returns the array size in bytes and not
the number of items inside it. As a result, the program will try to search much more items than it should
in the loop. This is the correct loop:
for (i = 0; i < sizeof(doserrors) / sizeof(*doserrors); i++)
Example 10. CPU Identifying Tool project. A string is printed into itself.
char * OSDetection ()
{
...
sprintf(szOperatingSystem,
"%sversion %d.%d %s (Build %d)",
szOperatingSystem,
osvi.dwMajorVersion,
osvi.dwMinorVersion,
osvi.szCSDVersion,](https://image.slidesharecdn.com/bugs-100-130729071042-phpapp02/75/100-bugs-in-Open-Source-C-C-projects-8-2048.jpg)
![osvi.dwBuildNumber & 0xFFFF);
...
sprintf (szOperatingSystem, "%s%s(Build %d)",
szOperatingSystem, osvi.szCSDVersion,
osvi.dwBuildNumber & 0xFFFF);
...
}
This error was found through the V541 diagnostic: It is dangerous to print the string 'szOperatingSystem'
into itself. stickies camel.cpp 572, 603
An attempt of formatted printing of a string into itself can lead to bad consequences. The result of
executing this code depends on the input data, and you cannot predict what will happen. Most likely,
the result will be a meaningless string or an Access Violation will occur.
This error can be referred to the category "code vulnerabilities". In some programs, by feeding special
data to code, you can exploit such code fragments to cause a buffer overflow or other effects an
intruder needs.
Example 11. FCE Ultra project. A string gets less memory than needed.
int FCEUI_SetCheat(...)
{
...
if((t=(char *)realloc(next->name,strlen(name+1))))
...
}
The error was found through the V518 diagnostic: The 'realloc' function allocates strange amount of
memory calculated by 'strlen(expr)'. Perhaps the correct variant is 'strlen(expr) + 1'. fceux cheat.cpp 609
This error is caused by a misprint. It is the 'name' pointer instead of the "name+1" expression that must
be the argument of the strlen() function. As a result, the realloc function allocates 2 bytes less memory
than needed: one byte is lost because 1 is not added to the string length; another byte is lost because
the 'strlen' function calculates the string length skipping the first character.
Example 12. Notepad++ project. Partial array clearing.
#define CONT_MAP_MAX 50
int _iContMap[CONT_MAP_MAX];](https://image.slidesharecdn.com/bugs-100-130729071042-phpapp02/75/100-bugs-in-Open-Source-C-C-projects-9-2048.jpg)
![...
DockingManager::DockingManager()
{
...
memset(_iContMap, -1, CONT_MAP_MAX);
...
}
The error was found through the V512 diagnostic: A call of the memset function will lead to a buffer
overflow or underflow. notepadPlus DockingManager.cpp 60
That's one more example of how the number of array items is mixed up with an array size. A
multiplication by sizeof(int) is missing.
We can go on and on showing you errors of array handling we have found in various programs. But we
have to stop somewhere.
Undefined behavior
A bit of theory at first.
Undefined behavior is a property of certain programming languages (most prominent in C and C++) to
produce a result in certain situations that depends on compiler implementation or specified
optimization switches. In other words, the specification does not define the language's behavior in any
possible situations but says: "at A condition, the result of B operation is undefined". It is considered a
mistake to allow such a situation in your program even if it is executed well at some particular compiler.
Such a program will not be crossplatform and may cause failures on a different computer, operating
system and even at different compiler's settings.
A sequence point in programming is any point in a program where it is guaranteed that the side effects
of all the previous calculations have already emerged while there are no side effects of the following
calculations yet. To learn more about sequence points and cases of undefined behavior related to
sequence points, see this post: http://www.viva64.com/en/t/0065/.
Example 1. Chromium project. Incorrect use of smart pointer.
void AccessibleContainsAccessible(...)
{
...
auto_ptr<VARIANT> child_array(new VARIANT[child_count]);](https://image.slidesharecdn.com/bugs-100-130729071042-phpapp02/75/100-bugs-in-Open-Source-C-C-projects-10-2048.jpg)
![...
}
The error was found through the V554 diagnostic: Incorrect use of auto_ptr. The memory allocated with
'new []' will be cleaned using 'delete'. interactive_ui_tests accessibility_win_browsertest.cc 171
This example demonstrates the case when using a smart pointer can cause undefined behavior. It may
be expressed through heap damage, program crash, incomplete object destruction or any other failure.
The error is this: memory is allocated by the new [] operator and released by the delete operator in the
'auto_ptr' class' destructor:
~auto_ptr() {
delete _Myptr;
}
To fix these issues, you should use a more appropriate class, for instance, boost::scoped_array.
Example 2. IPP Samples project. Classic Undefined behavior.
template<typename T, Ipp32s size> void HadamardFwdFast(...)
{
Ipp32s *pTemp;
...
for(j=0;j<4;j++) {
a[0] = pTemp[0*4] + pTemp[1*4];
a[1] = pTemp[0*4] - pTemp[1*4];
a[2] = pTemp[2*4] + pTemp[3*4];
a[3] = pTemp[2*4] - pTemp[3*4];
pTemp = pTemp++;
...
}
...
}
The error was found through the V567 diagnostic: Undefined behavior. The 'pTemp' variable is modified
while being used twice between sequence points. me umc_me_cost_func.h 168
This is a classic example of undefined program behavior. It is this construct which is used to
demonstrate Undefined behavior in various articles. It is unknown whether 'pTemp' will be incremented](https://image.slidesharecdn.com/bugs-100-130729071042-phpapp02/75/100-bugs-in-Open-Source-C-C-projects-11-2048.jpg)
![by one or not. Two actions of changing pTemp variable's value are located in one sequence point. It
means that the compiler may create the following code:
pTemp = pTemp + 1;
pTemp = pTemp;
Or it may create another version of the code:
TMP = pTemp;
pTemp = pTemp + 1;
pTemp = TMP;
Which of the two code versions will be created depends on the compiler and optimization switches.
Example 3. Fennec Media Project project. Complex expression.
uint32 CUnBitArrayOld::DecodeValueRiceUnsigned(uint32 k)
{
...
while (!(m_pBitArray[m_nCurrentBitIndex >> 5] &
Powers_of_Two_Reversed[m_nCurrentBitIndex++ & 31])) {}
...
}
The error was found through the V567 diagnostic: Undefined behavior. The 'm_nCurrentBitIndex'
variable is modified while being used twice at single sequence point. MACLib unbitarrayold.cpp 78
There are no sequence points between two instances of using the 'm_nCurrentBitIndex' variable. It
means that the standard does not specify the moment when this variable is incremented.
Correspondingly, this code may work differently depending on the compiler and optimization switches.
Example 4. Miranda IM project. Complex expression.
short ezxml_internal_dtd(ezxml_root_t root,
char *s, size_t len)
{
...
while (*(n = ++s + strspn(s, EZXML_WS)) && *n != '>') {
...](https://image.slidesharecdn.com/bugs-100-130729071042-phpapp02/75/100-bugs-in-Open-Source-C-C-projects-12-2048.jpg)


![return;
} else {
if(!original_space_accelerators) return;
}
}
Example 5. IPP Samples project. Priorities of ?: and | operations.
vm_file* vm_file_fopen(...)
{
...
mds[3] = FILE_ATTRIBUTE_NORMAL |
(islog == 0) ? 0 : FILE_FLAG_NO_BUFFERING;
...
}
The error was found through the V502 diagnostic: Perhaps the '?:' operator works in a different way
than it was expected. The '?:' operator has a lower priority than the '|' operator. vm vm_file_win.c 393
Depending on the 'islog' variable's value, the expression must be either equal to
"FILE_ATTRIBUTE_NORMAL" or "FILE_ATTRIBUTE_NORMAL | FILE_FLAG_NO_BUFFERING". But it does
not happen. Priority of the '?:' operation is lower than that of '|'. As a result, the code acts as follows:
mds[3] = (FILE_ATTRIBUTE_NORMAL | (islog == 0)) ?
0 : FILE_FLAG_NO_BUFFERING;
Let's simplify the expression:
mds[3] = (0x00000080 | ...) ? 0 : FILE_FLAG_NO_BUFFERING;
Since FILE_ATTRIBUTE_NORMAL equals 0x00000080, the condition is always true. It means that 0 will
always be written into mds[3].
Example 6. Newton Game Dynamics project. Priorities of ?: and * operations.
dgInt32 CalculateConvexShapeIntersection (...)
{
...
den = dgFloat32 (1.0e-24f) *](https://image.slidesharecdn.com/bugs-100-130729071042-phpapp02/75/100-bugs-in-Open-Source-C-C-projects-16-2048.jpg)
![(den > dgFloat32 (0.0f)) ?
dgFloat32 (1.0f) : dgFloat32 (-1.0f);
...
}
The error was found through the V502 diagnostic: Perhaps the '?:' operator works in a different way
than it was expected. The '?:' operator has a lower priority than the '*' operator. physics
dgminkowskiconv.cpp 1061
The error in this code again relates to the low priority of the '?:' operation. The condition for the '?:'
operator is expressed by a meaningless subexpression "dgFloat32 (1.0e-24f) * (den > dgFloat32 (0.0f))".
Adding parentheses will solve the issue.
By the way, programmers often forget how cunning the '?:' operator is. Here is a post on this topic:
"How to make fewer errors at the stage of code writing. Part N2".
Formatted output errors
Examples of these errors are boring and alike, so we will examine only a few samples. The point is that
functions with a variable number of arguments accept actual arguments incompatible with the format
string. Any programmer who uses such functions as printf() is familiar with this type of errors.
Example 1. ReactOS project. Incorrect printing of a WCHAR-character.
static void REGPROC_unescape_string(WCHAR* str)
{
...
default:
fprintf(stderr,
"Warning! Unrecognized escape sequence: %c'n",
str[str_idx]);
...
}
The error was found through the V576 diagnostic: Incorrect format. Consider checking the third actual
argument of the 'fprintf' function. The char type argument is expected. regedit regproc.c 293](https://image.slidesharecdn.com/bugs-100-130729071042-phpapp02/75/100-bugs-in-Open-Source-C-C-projects-17-2048.jpg)
![The fprinf() function must print a character of the char type. But the third argument is a character of the
WCHAR type. The user will get an incorrectly generated message. To fix the code, we should replace '%c'
with '%C' in the format string.
Example 2. Intel AMT SDK project. Character '%' missing.
void addAttribute(...)
{
...
int index = _snprintf(temp, 1023,
"%02x%02x:%02x%02x:%02x%02x:%02x%02x:"
"%02x%02x:02x%02x:%02x%02x:%02x%02x",
value[0],value[1],value[2],value[3],value[4],
value[5],value[6],value[7],value[8],
value[9],value[10],value[11],value[12],
value[13],value[14],value[15]);
...
}
The error was found through the V576 diagnostic: Incorrect format. A different number of actual
arguments is expected while calling '_snprintf' function. Expected: 18. Present: 19. mod_pvs
mod_pvs.cpp 308
It is not easy to find an error here at first sight. However, the PVS-Studio analyzer does not get tired and
notices that the function takes more actual arguments than specified in the format string. The reason is
that the '%' character is missing in one place. Let's single out this fragment:
"%02x%02x:[HERE]02x%02x:%02x%02x:%02x%02x",
Example 3. Intel AMT SDK project. Unused argument.
bool GetUserValues(...)
{
...
printf("Error: illegal value. Aborting.n", tmp);
return false;
}](https://image.slidesharecdn.com/bugs-100-130729071042-phpapp02/75/100-bugs-in-Open-Source-C-C-projects-18-2048.jpg)
![The error was found through the V576 diagnostic: Incorrect format. A different number of actual
arguments is expected while calling 'printf' function. Expected: 1. Present: 2. RemoteControlSample
remotecontrolsample.cpp 792
The error is this: the 'tmp' variable is not used in any way when printing the information message.
Example 4. G3D Content Pak project. Printing of meaningless data.
class Matrix3 {
...
inline float* operator[] (int iRow) {
...
};
void AnyVal::serialize(G3D::TextOutput& t) const {
...
const Matrix3& m = *(Matrix3*)m_value;
...
t.printf("%10.5f, %10.5f, %10.5f,n
%10.5f, %10.5f, %10.5f,n
%10.5f, %10.5f, %10.5f)",
m[0, 0], m[0, 1], m[0, 2],
m[1, 0], m[1, 1], m[1, 2],
m[2, 0], m[2, 1], m[2, 2]);
...
}
The error was found through the V520 diagnostic: The comma operator ',' in array index expression '[0,
0]'. graphics3D anyval.cpp 275
The program prints meaningless values instead of the matrix. You may write such a code when you work
with different programming languages and sometimes forget how to access an item in a two-
dimensional array in the C language.
Let's see how the 'm[0, 1]' expression works. At first, expression"0, 1" is calculated. The result of this
expression is 1. Then the 'operator[]' function is called in the Matrix3 class. The function takes the actual
argument 1 and returns the pointer to the first string in the matrix. It is the value of this pointer that will
be printed by the 'printf()' function though it expects a value of the float-type.](https://image.slidesharecdn.com/bugs-100-130729071042-phpapp02/75/100-bugs-in-Open-Source-C-C-projects-19-2048.jpg)
![This is the correct code:
t.printf("%10.5f, %10.5f, %10.5f,n
%10.5f, %10.5f, %10.5f,n
%10.5f, %10.5f, %10.5f)",
m[0][0], m[0][1], m[0][2],
m[1][0], m[1][1], m[1][2],
m[2][0], m[2][1], m[2][2]);
Examples of misprints found in code
A lot of programming errors are caused by misprints. Most of these errors are quickly detected at the
early stages of testing. But there are some defects of this kind that remain in code for a long time
causing troubles both to programmers and users.
You can make these errors much fewer using the PVS-Studio analyzer. It will find them before testing
starts, which will significantly reduce the cost of defect detection and elimination.
Example 1. Miranda IM project. Assignment inside IF.
void CIcqProto::handleUserOffline(BYTE *buf, WORD wLen)
{
...
else if (wTLVType = 0x29 && wTLVLen == sizeof(DWORD))
...
}
The error was found through the V560 diagnostic: A part of conditional expression is always true: 0x29.
icqoscar8 fam_03buddy.cpp 632
Because of a misprint, there is an assignment taking place inside the condition of the 'if' operator. This is
the correct condition: "if (wTLVType == 0x29 && wTLVLen == sizeof(DWORD))".
Example 2. ReactOS project. Assignment error.
BOOL WINAPI GetMenuItemInfoA(...)
{
...
mii->cch = mii->cch;](https://image.slidesharecdn.com/bugs-100-130729071042-phpapp02/75/100-bugs-in-Open-Source-C-C-projects-20-2048.jpg)
![The error was found through the V501 diagnostic: There are identical sub-expressions to the left and to
the right of the '&&' operator. _isPointXValid && _isPointXValid
The name '_isPointXValid' is used twice. The function must actually return this code: "_isPointXValid &&
_isPointYValid".
Example 5. StrongDC++ project. Unsuccessful check of rn.
static void getContentLengthAndHeaderLength(...)
{
...
while(line[linelen] != 'r' && line[linelen] != 'r')
...
}
The error was found through the V501 diagnostic: There are identical sub-expressions 'line [linelen] !=
'r'' to the left and to the right of the '&&' operator. miniupnpc miniupnpc.c 153
Because of a misprint, presence of the 'r' character is checked twice. Actually presence of the 'n'
character must be checked too.
Example 6. G3D Content Pak project. A closing parenthesis in a wrong place.
bool Matrix4::operator==(const Matrix4& other) const {
if (memcmp(this, &other, sizeof(Matrix4) == 0)) {
return true;
}
...
}
The error was found through the V575 diagnostic: The 'memcmp' function processes '0' elements.
Inspect the 'third' argument. graphics3D matrix4.cpp 269
One closing parenthesis is in a wrong place. It turns out that the size of the memory area being
compared is calculated by the "sizeof(Matrix4) == 0" expression. This expression always has the 'false'
result. Then 'false' turns into an integer value equal to 0. This is the correct code:
if (memcmp(this, &other, sizeof(Matrix4)) == 0) {
Example 7. QT project. Error of structure member copying.](https://image.slidesharecdn.com/bugs-100-130729071042-phpapp02/75/100-bugs-in-Open-Source-C-C-projects-22-2048.jpg)
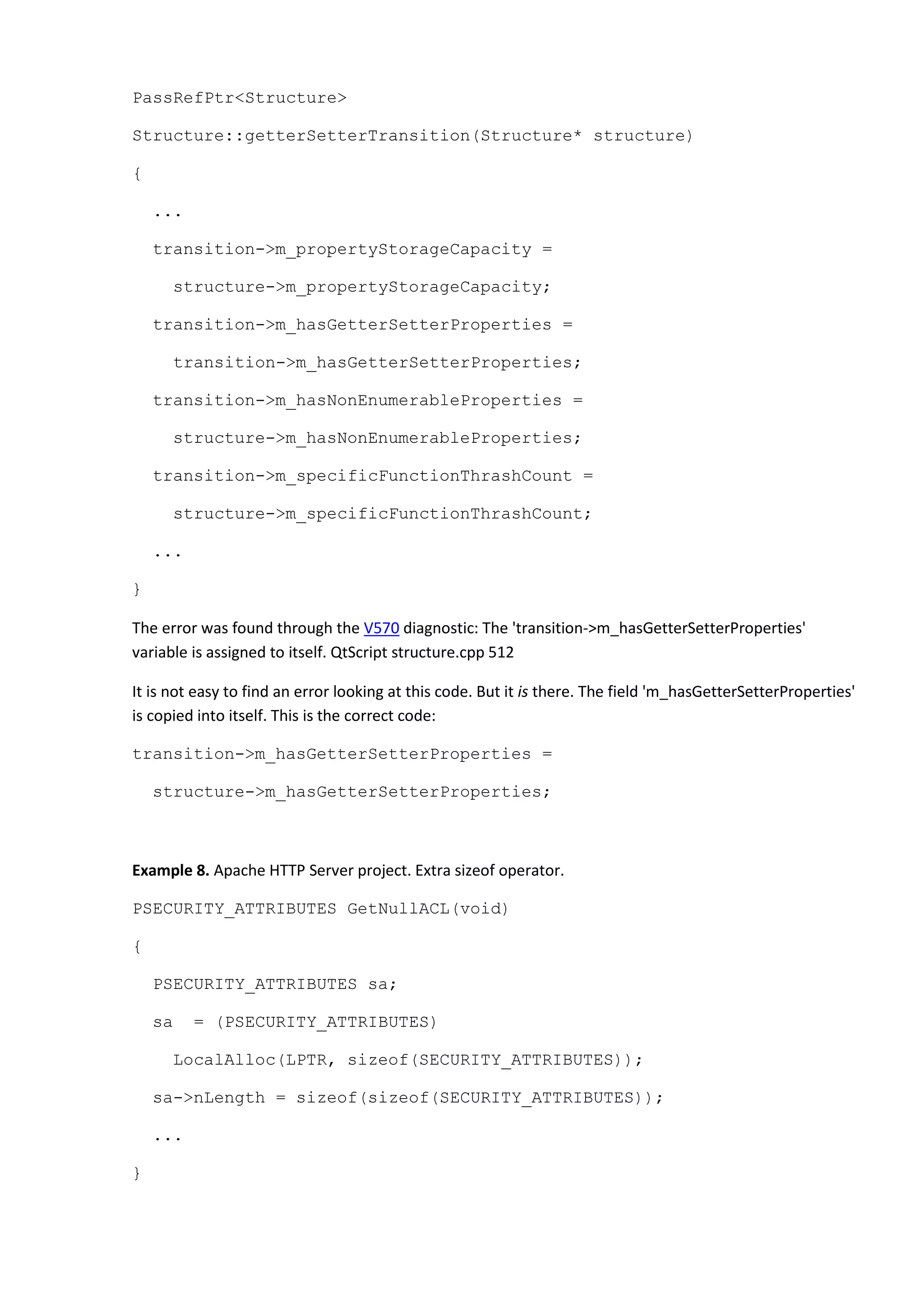
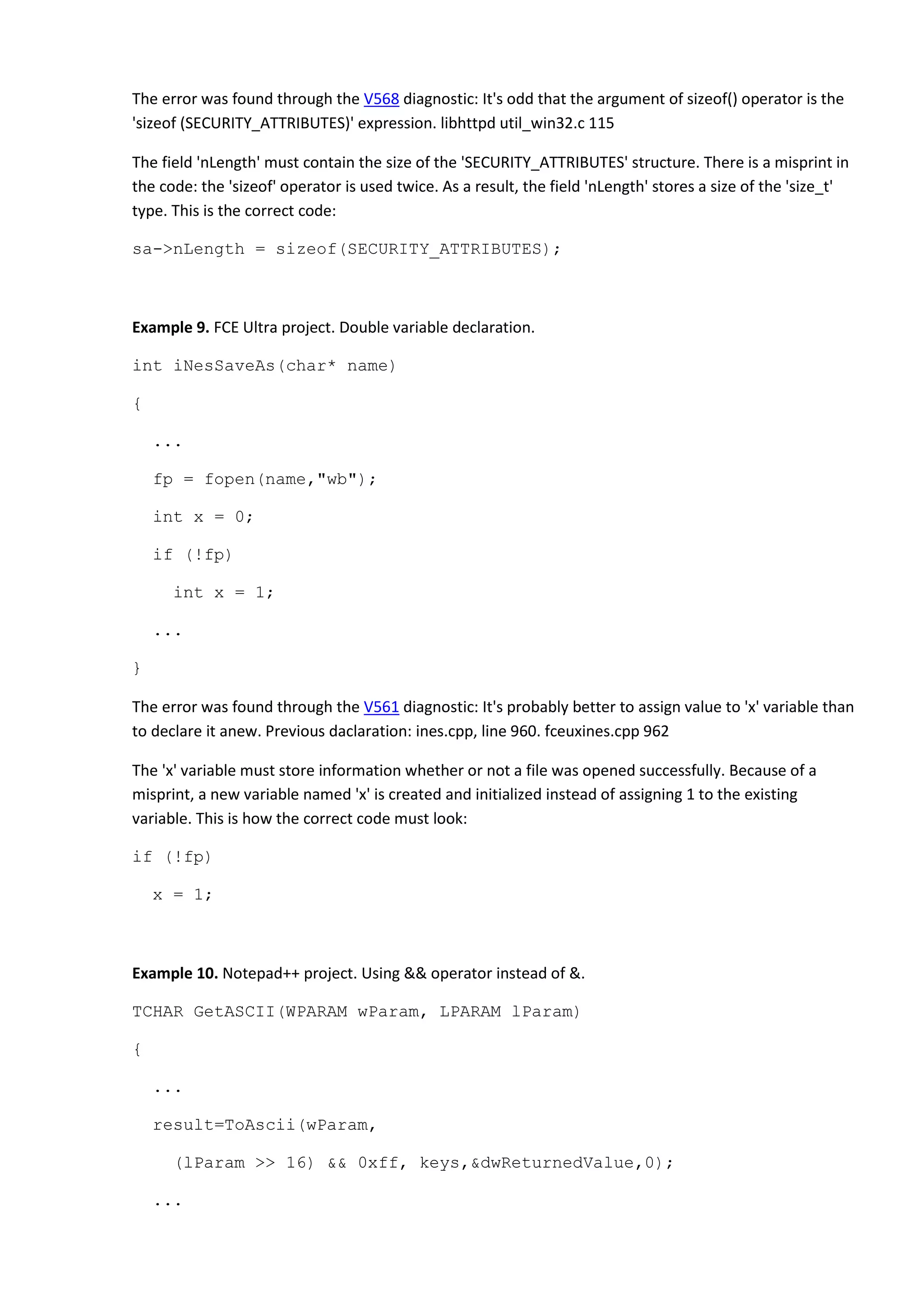
![}
The error was found through the V560 diagnostic: A part of conditional expression is always true: 0xff.
notepadPlus babygrid.cpp 694
The "(lParam >> 16) && 0xff" expression is meaningless and is always equal to 1 (true). A misprint here
is in using the '&&' operator instead of '&'.
Example 11. WinDjView project. Incomplete condition.
inline bool IsValidChar(int c)
{
return c == 0x9 || 0xA || c == 0xD || c >= 0x20 &&
c <= 0xD7FF || c >= 0xE000 && c <= 0xFFFD ||
c >= 0x10000 && c <= 0x10FFFF;
}
The error was found through the V560 diagnostic: A part of conditional expression is always true: 0xA.
WinDjView xmlparser.cpp 45 False
The IsValidChar function always returns 'true'. Comparison is missing in one place because of a misprint:
"... || 0xA || ...".
Example 12. Fennec Media Project project. Extra semicolon.
int settings_default(void)
{
...
for(i=0; i<16; i++);
for(j=0; j<32; j++)
{
settings.conversion.equalizer_bands.boost[i][j] = 0.0;
settings.conversion.equalizer_bands.preamp[i] = 0.0;
}
}
The error was found through the V529 diagnostic: Odd semicolon ';' after 'for' operator. settings.c 483](https://image.slidesharecdn.com/bugs-100-130729071042-phpapp02/75/100-bugs-in-Open-Source-C-C-projects-25-2048.jpg)
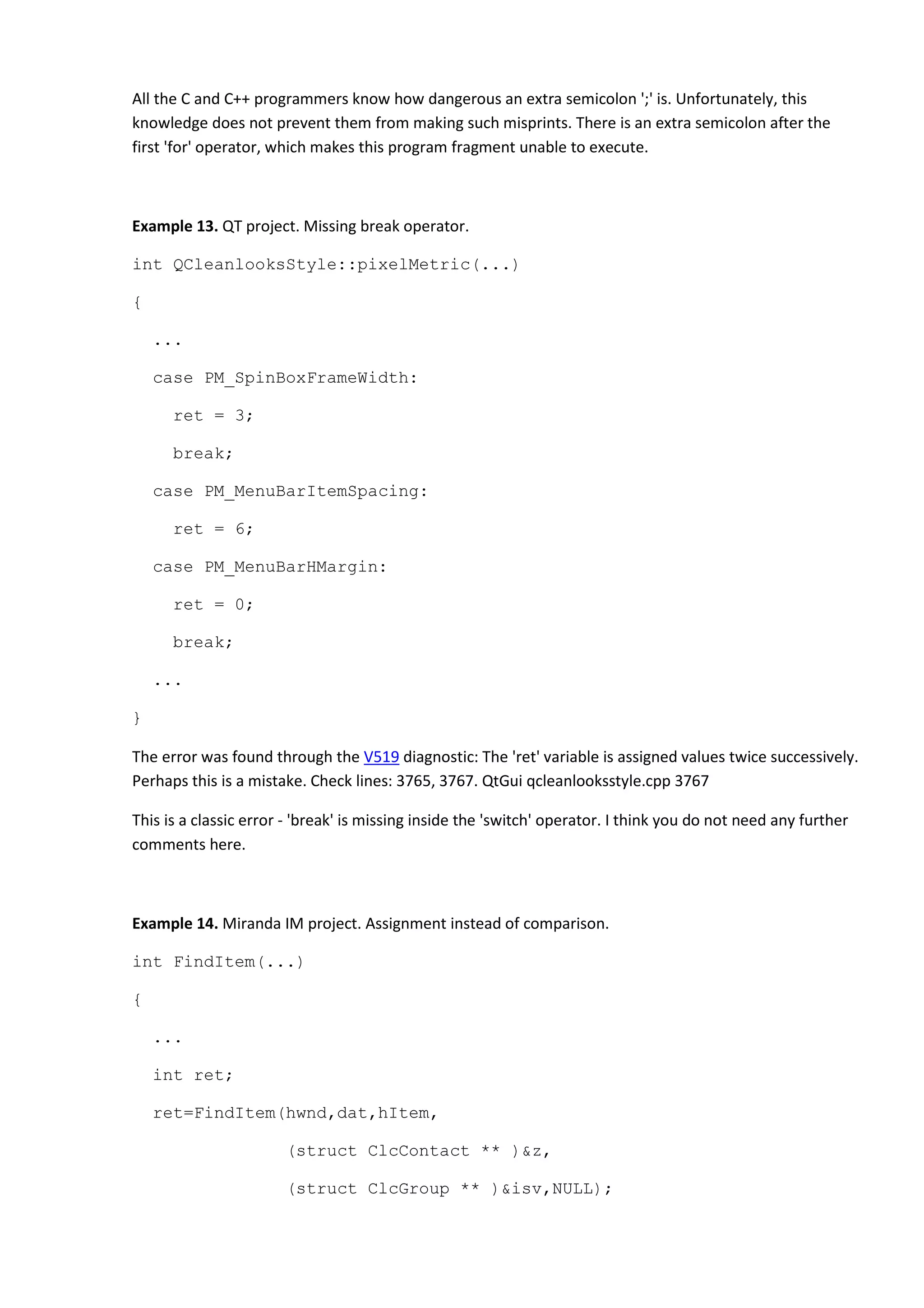
![if (ret=0) {return (0);}
...
}
The error was found through the V559 diagnostic: Suspicious assignment inside the condition expression
of 'if' operator: ret = 0. clist_mw clcidents.c 179
There is a misprint inside the condition of the 'if' operator: '=' is written instead of '=='. The function will
handle the situation incorrectly when a certain item is not found.
Example 15. IPP Samples project. Incorrect index.
struct AVS_MB_INFO
{
...
Ipp8u refIdx[AVS_DIRECTIONS][4];
...
};
void AVSCompressor::GetRefIndiciesBSlice(void){
...
if (m_pMbInfo->predType[0] & predType)
{
m_refIdx[iRefNum] = m_pMbInfo->refIdx[dir][0];
iRefNum += 1;
}
if (m_pMbInfo->predType[1] & predType)
{
m_refIdx[iRefNum] = m_pMbInfo->refIdx[dir][1];
iRefNum += 1;
}
if (m_pMbInfo->predType[2] & predType)
{](https://image.slidesharecdn.com/bugs-100-130729071042-phpapp02/75/100-bugs-in-Open-Source-C-C-projects-27-2048.jpg)
![m_refIdx[iRefNum] = m_pMbInfo->refIdx[dir][2];
iRefNum += 1;
}
if (m_pMbInfo->predType[3] & predType)
{
m_refIdx[iRefNum] = m_pMbInfo->refIdx[dir][30];
iRefNum += 1;
}
...
}
The error was found through the V557 diagnostic: Array overrun is possible. The '30' index is pointing
beyond array bound. avs_enc umc_avs_enc_compressor_enc_b.cpp 495
Consider this fragment: "m_pMbInfo->refIdx[dir][30]". Because of a misprint, number 30 is written
instead of index 3. By the way, this sample shows well how relative our division of errors into categories
is. This error might well be referred to the category "Errors of array and string handling". The division is
relative and is made to show diversity of errors the PVS-Studio analyzer can detect.
Example 16. ReactOS project. Misprint in a macro.
#define SWAP(a,b,c) c = a;
a = b;
a = c
The error was found through the V519 diagnostic: The 'v2' variable is assigned values twice successively.
Perhaps this is a mistake. Check lines: 343, 343. win32k gradient.c 343
It is a rather funny misprint in a macro intended to swap values in two variables. Look closely at the code
and you will see what I mean. This is the correct code:
#define SWAP(a,b,c) c = a;
a = b;
b = c
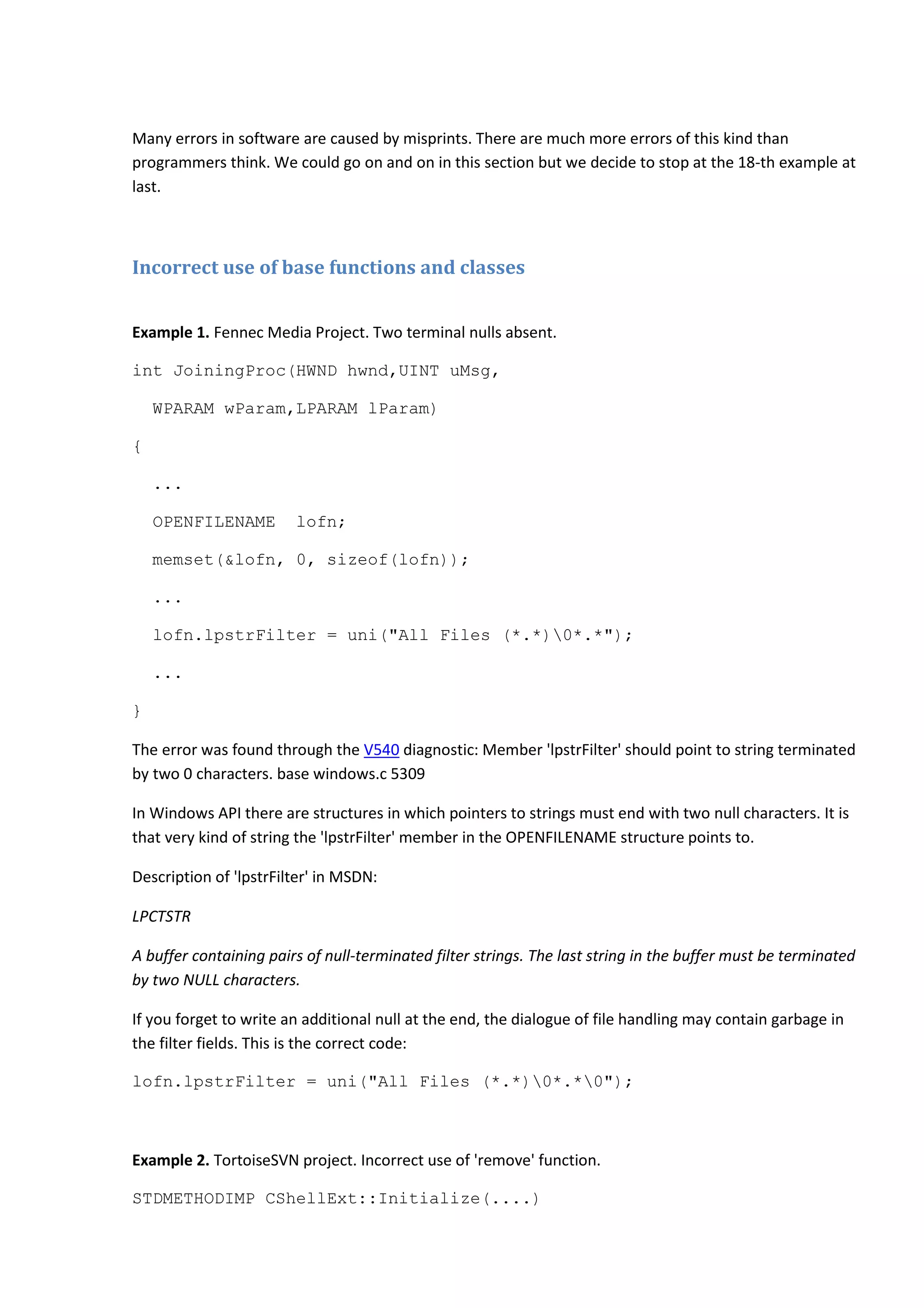
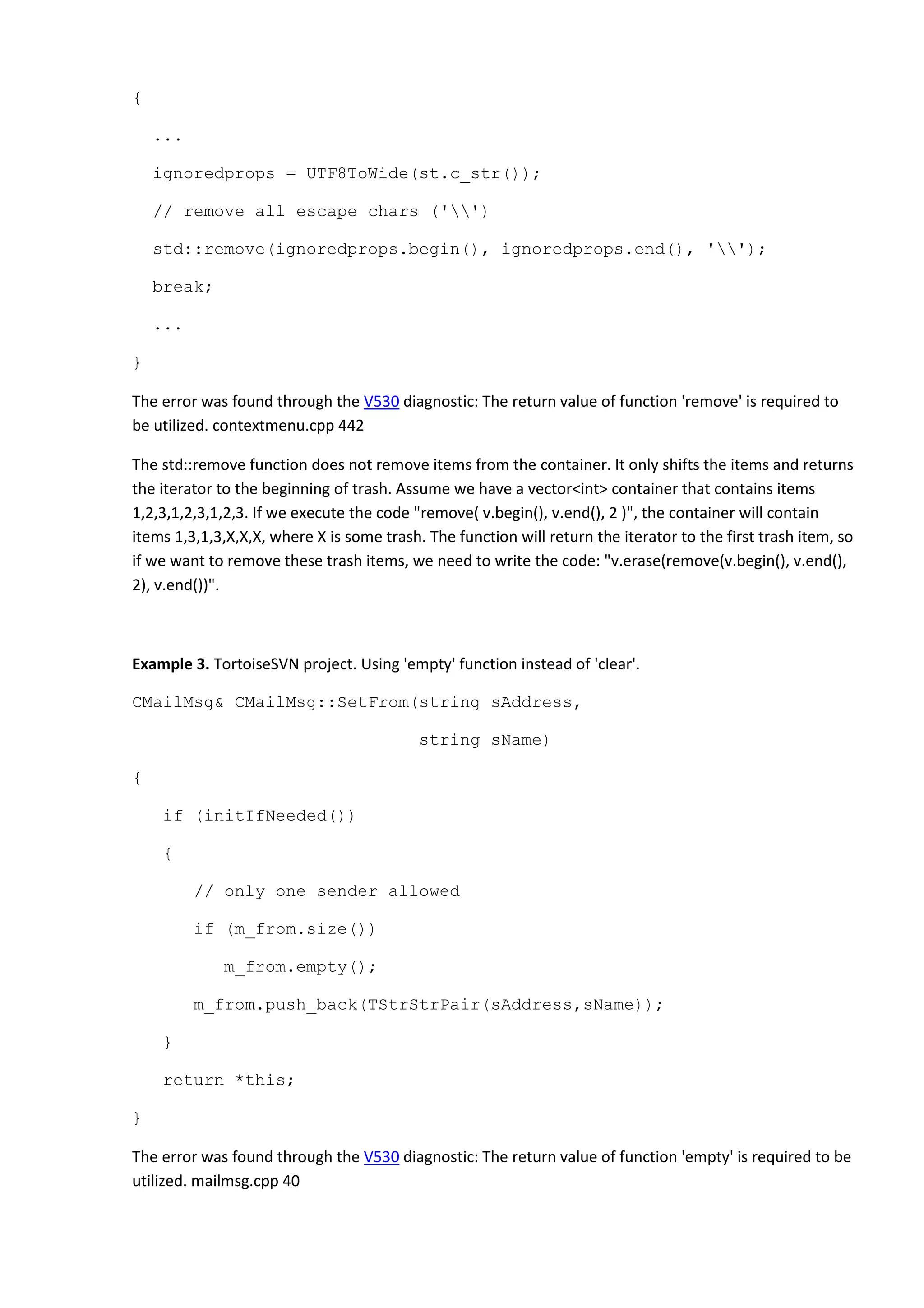
Example 17. Quake-III-Arena project. Misprint. Comma instead of multiplication operator.
void Q1_AllocMaxBSP(void)
{](https://image.slidesharecdn.com/bugs-100-130729071042-phpapp02/75/100-bugs-in-Open-Source-C-C-projects-28-2048.jpg)
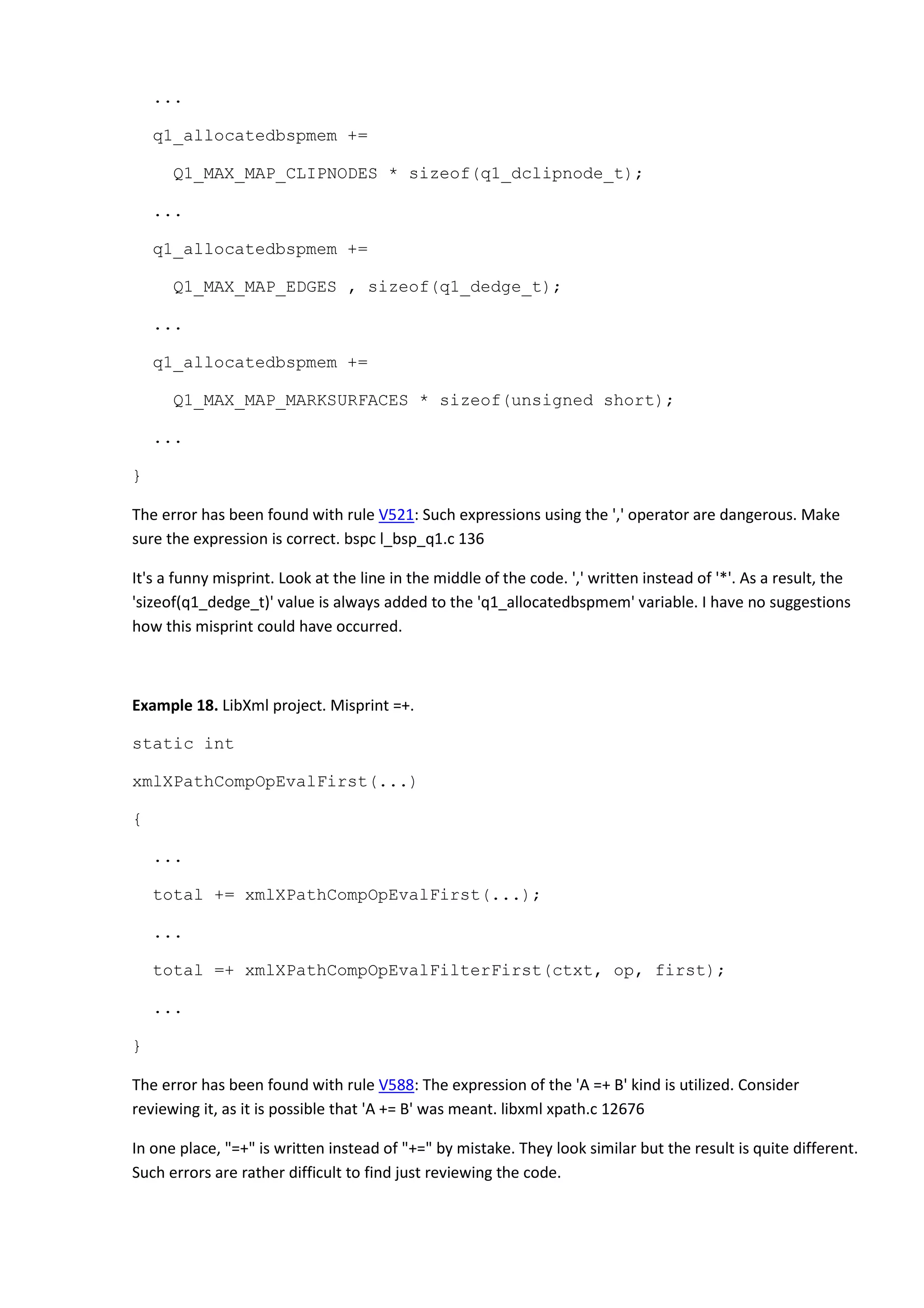

![...
do {
...
CTriVertex *snVertex =
(CTriVertex *)alloca(2*sizeof(CTriVertex));
...
} while(dVertex != loops[0]);
...
} while(sVertex != loops[i]);
...
}
...
}
The error was found through the V505 diagnostic: The 'alloca' function is used inside the loop. This can
quickly overflow stack. ri polygons.cpp 1120
The alloca function allocates memory inside the stack, so calling it many times inside the loop body may
suddenly cause a stack overflow. And we have several nested loops here. This code may exhaust stack
memory very quickly.
Example 6. Miranda IM project. Arguments mixed up.
static BOOL ImageArray_Alloc(LP_IMAGE_ARRAY_DATA iad, int size)
{
...
memset(&iad->nodes[iad->nodes_allocated_size],
(size_grow - iad->nodes_allocated_size) *
sizeof(IMAGE_ARRAY_DATA_NODE),
0);
...
}
The error was found through the V575 diagnostic: Function receives an odd argument. clist_modern
modern_image_array.cpp 59](https://image.slidesharecdn.com/bugs-100-130729071042-phpapp02/75/100-bugs-in-Open-Source-C-C-projects-33-2048.jpg)
![The 'memset' function handles 0 items, i.e. actually does nothing. The reason is in mixed up arguments.
This is how the correct call of the memset function should be written:
memset(&iad->nodes[iad->nodes_allocated_size],
0,
(size_grow - iad->nodes_allocated_size) *
sizeof(IMAGE_ARRAY_DATA_NODE));
Examples of meaningless code
Example 1. IPP Samples project. Incomplete condition.
void lNormalizeVector_32f_P3IM(Ipp32f *vec[3],
Ipp32s* mask, Ipp32s len)
{
Ipp32s i;
Ipp32f norm;
for(i=0; i<len; i++) {
if(mask<0) continue;
norm = 1.0f/sqrt(vec[0][i]*vec[0][i]+
vec[1][i]*vec[1][i]+vec[2][i]*vec[2][i]);
vec[0][i] *= norm; vec[1][i] *= norm; vec[2][i] *= norm;
}
}
The error was found through the V503 diagnostic: This is a nonsensical comparison: pointer < 0.
ipprsample ippr_sample.cpp 501
I do not know how it happened, but there are 3 characters "[i]" missing in this code. As a result, the code
performs a meaningless check that the pointer is below zero instead of checking the mask array.
The correct check should be written in this way: if(mask[i] < 0).
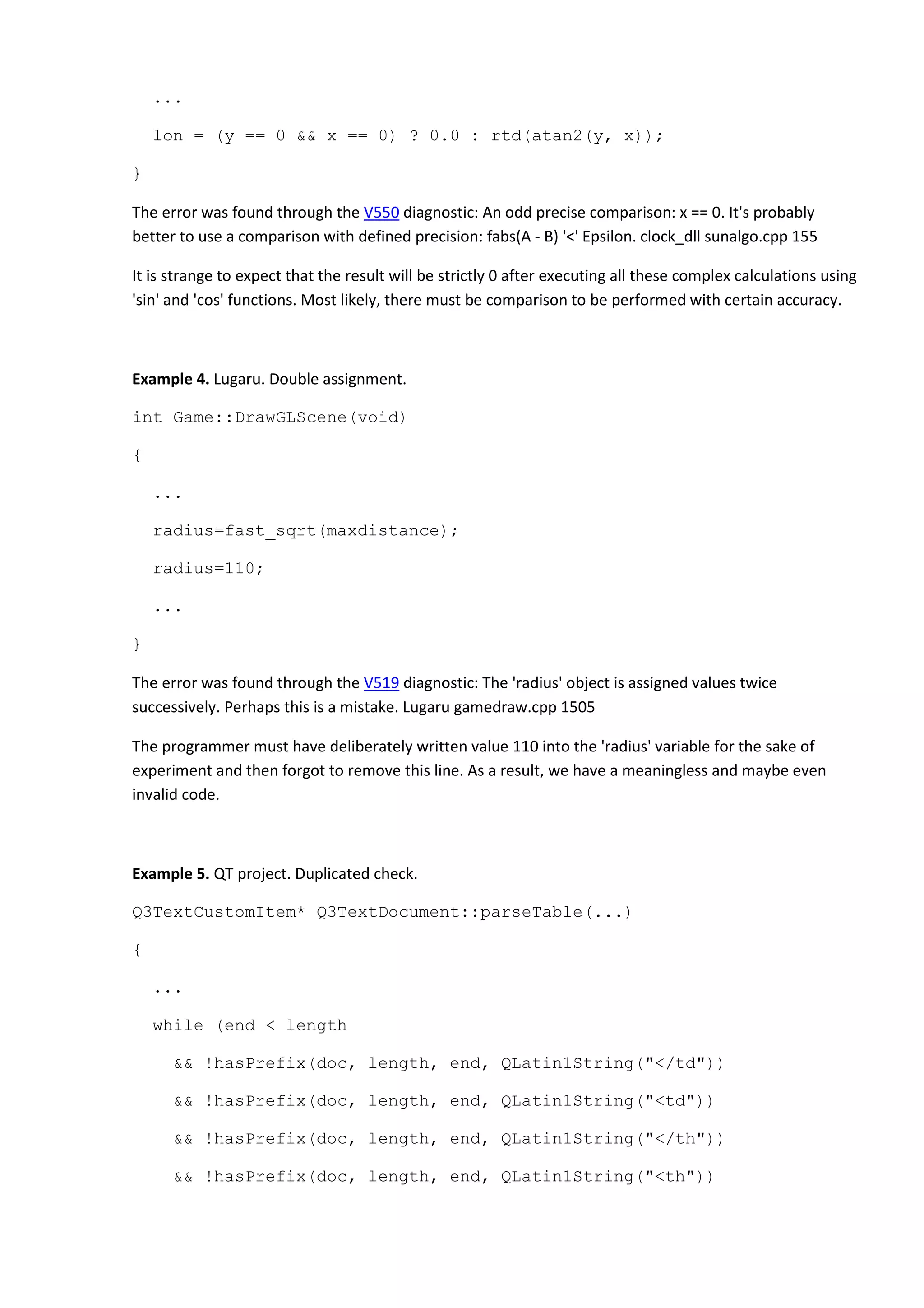
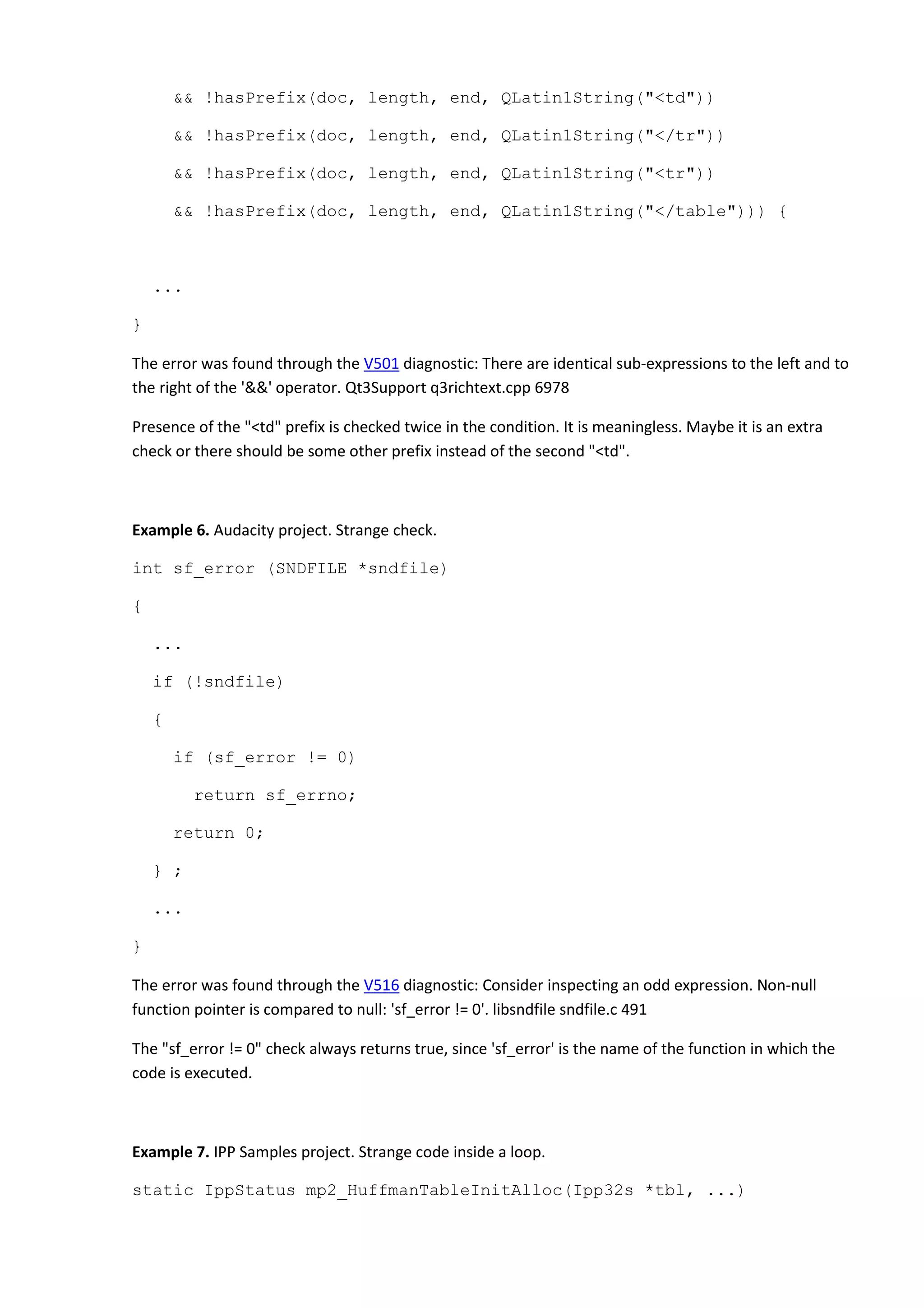
Example 2. Pc Ps2 Emulator project. Incorrect switch.
LRESULT CALLBACK IOP_DISASM(...)](https://image.slidesharecdn.com/bugs-100-130729071042-phpapp02/75/100-bugs-in-Open-Source-C-C-projects-34-2048.jpg)

![{
...
for (i = 0; i < num_tbl; i++) {
*tbl++;
}
...
}
The error was found through the V532 diagnostic: Consider inspecting the statement of '*pointer++'
pattern. Probably meant: '(*pointer)++'. mpeg2_dec umc_mpeg2_dec.cpp 59
The loop body is probably incomplete because it is meaningless in the current form.
Always true or always false conditions
It is a very large and widely-spread type of errors. These errors also vary greatly depending on the
importance level. To non-dangerous errors we may refer incorrect conditions in ASSERT that actually do
not check anything. To dangerous errors, incorrect checks of buffer size or index size are referred.
Example 1. Shareaza project. Value range of char type.
void CRemote::Output(LPCTSTR pszName)
{
...
CHAR* pBytes = new CHAR[ nBytes ];
hFile.Read( pBytes, nBytes );
...
if ( nBytes > 3 && pBytes[0] == 0xEF &&
pBytes[1] == 0xBB && pBytes[2] == 0xBF )
{
pBytes += 3;
nBytes -= 3;
bBOM = true;
}](https://image.slidesharecdn.com/bugs-100-130729071042-phpapp02/75/100-bugs-in-Open-Source-C-C-projects-38-2048.jpg)
![...
}
The error was found through the V547 diagnostic: Expression 'pBytes [ 0 ] == 0xEF' is always false. The
value range of signed char type: [-128, 127]. Shareaza remote.cpp 350
In this code, the 'TCHAR' type is the 'char' type. The value range of char is from -128 to 127 inclusive.
Value 0xEF in the variable of the char type is nothing else than number -17. When comparing the char
variable with number 0xEF, its type is extended up to the 'int' type. But the value still lies inside the
range [-128..127]. The "pBytes[0] == 0xEF" ("-17 == 0xEF") condition is always false, and the program
does not work as intended.
This is the correct comparison:
if ( nBytes > 3 && pBytes[0] == TCHAR(0xEF) &&
pBytes[1] == TCHAR(0xBB) &&
pBytes[2] == TCHAR(0xBF) )
Example 2. TortoiseSVN project. Value range of char type.
BOOL TortoiseBlame::OpenFile(const TCHAR *fileName)
{
...
// check each line for illegal utf8 sequences.
// If one is found, we treat
// the file as ASCII, otherwise we assume
// an UTF8 file.
char * utf8CheckBuf = lineptr;
while ((bUTF8)&&(*utf8CheckBuf))
{
if ((*utf8CheckBuf == 0xC0)||
(*utf8CheckBuf == 0xC1)||
(*utf8CheckBuf >= 0xF5))
{
bUTF8 = false;
break;
}](https://image.slidesharecdn.com/bugs-100-130729071042-phpapp02/75/100-bugs-in-Open-Source-C-C-projects-39-2048.jpg)
![...
}
...
}
The error was found through the V547 diagnostic: Expression '* utf8CheckBuf == 0xC0' is always false.
The value range of signed char type: [-128, 127]. tortoiseblame.cpp 310
While the defect in the previous example seems to be caused through mere inattention, in this case it is
not so. Here is another identical example where a condition is always false. This is a very widely-spread
type of errors in various projects.
Example 3. VirtualDub project. Unsigned type is always >= 0.
typedef unsigned short wint_t;
...
void lexungetc(wint_t c) {
if (c < 0)
return;
g_backstack.push_back(c);
}
The error was found through the V547 diagnostic: Expression 'c < 0' is always false. Unsigned type value
is never < 0. Ami lexer.cpp 225
The "c < 0" condition is always false because the variable of the unsigned type is always above or equal
to 0.
Example 4. Swiss-Army Knife of Trace project. Socket handling.
static UINT_PTR m_socketHandle;
void TTrace::LoopMessages(void)
{
...](https://image.slidesharecdn.com/bugs-100-130729071042-phpapp02/75/100-bugs-in-Open-Source-C-C-projects-40-2048.jpg)

![}
...
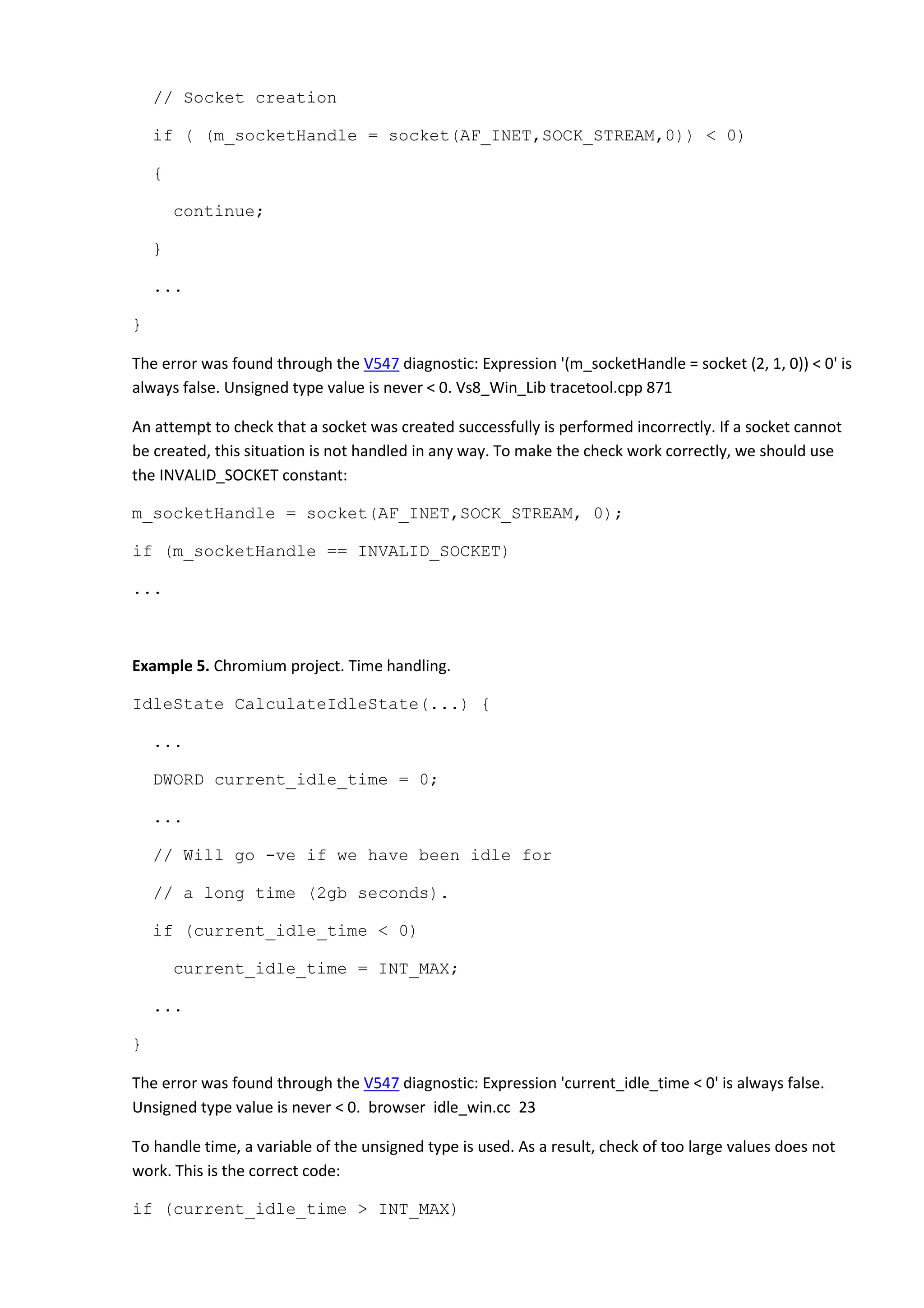
}
The error was found through the V547 diagnostic: Expression '--size >= 0' is always true. Unsigned type
value is always >= 0. QtCLucene arrays.h 154
The (--size >= 0) condition is always true, since the size variable has the unsigned type. It means that if
two sequences being compared are alike, we will get an overflow that will in its turn cause Access
Violation or other program failures.
This is the correct code:
for (size_t i = 0; i != size; i++){
if ( !comp(*itr1,*itr2) )
return false;
itr1++;
itr2++;
}
Example 8. MySQL project. Error in condition.
enum enum_mysql_timestamp_type
str_to_datetime(...)
{
...
else if (str[0] != 'a' || str[0] != 'A')
continue; /* Not AM/PM */
...
}
The error was found through the V547 diagnostic: Expression 'str [0] != 'a' || str [0] != 'A'' is always true.
Probably the '&&' operator should be used here. clientlib my_time.c 340
The condition is always true because the character is always either not equal to 'a' or to 'A'. This is the
correct check:
else if (str[0] != 'a' && str[0] != 'A')](https://image.slidesharecdn.com/bugs-100-130729071042-phpapp02/75/100-bugs-in-Open-Source-C-C-projects-43-2048.jpg)



![dereferencing operation is missing here, and it is the pointer itself which is compared to zero. This is the
correct code:
if (m_szPassword != NULL)
{
...
if (*m_szPassword != '0')
Example 2. Chromium project. Null pointer handling.
bool ChromeFrameNPAPI::Invoke(...)
{
ChromeFrameNPAPI* plugin_instance =
ChromeFrameInstanceFromNPObject(header);
if (!plugin_instance &&
(plugin_instance->automation_client_.get()))
return false;
...
}
The error was found through the V522 diagnostic: Dereferencing of the null pointer 'plugin_instance'
might take place. Check the logical condition. chrome_frame_npapi chrome_frame_npapi.cc 517
The condition that checks the null pointer is written incorrectly. As a result, we have a segmentation
error. This is the correct code:
if (plugin_instance &&
(plugin_instance->automation_client_.get()))
return false;
Example 3. SMTP Client with SSL/TLS project. Incomplete buffer clearing.
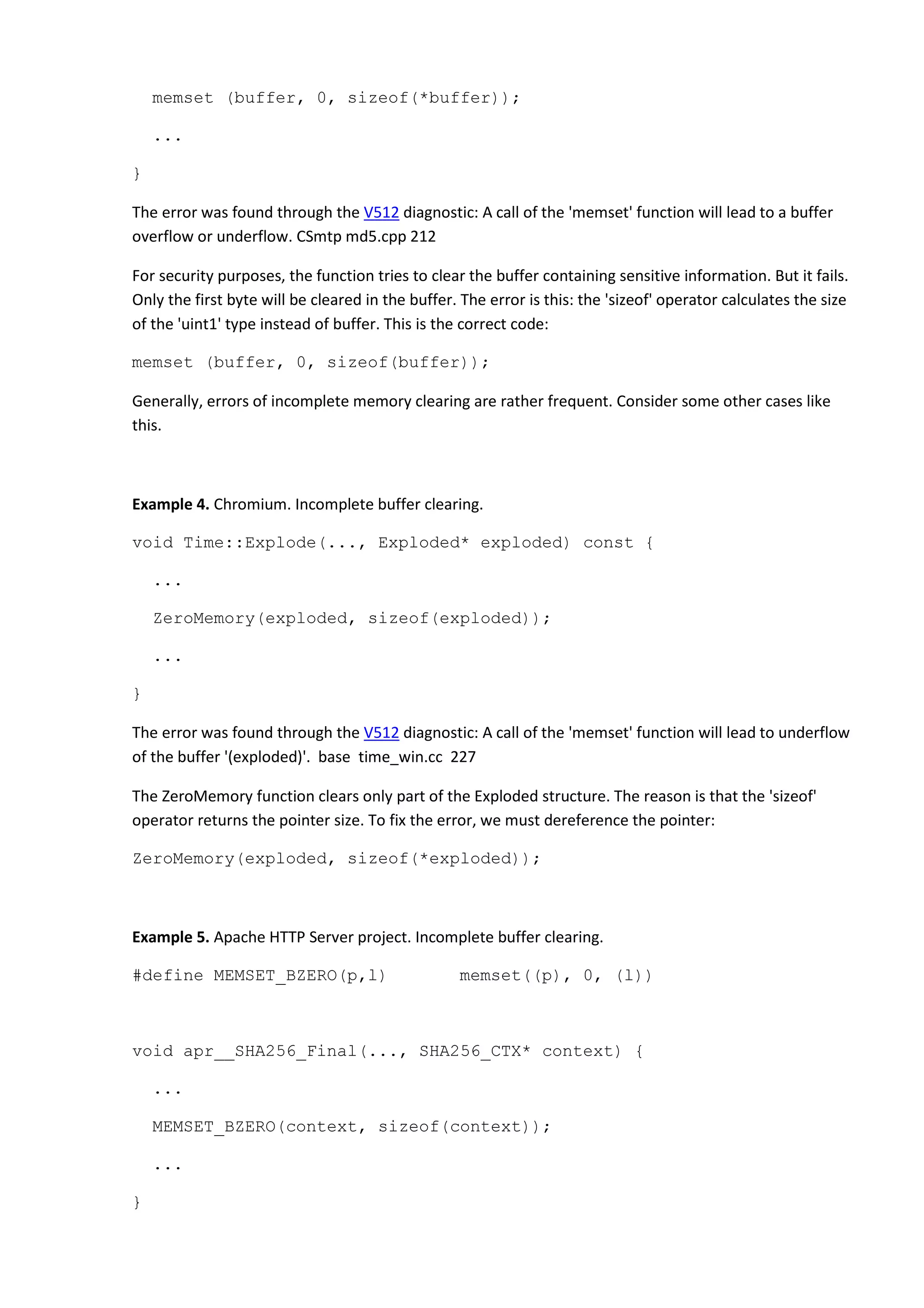
void MD5::finalize () {
...
uint1 buffer[64];
...
// Zeroize sensitive information](https://image.slidesharecdn.com/bugs-100-130729071042-phpapp02/75/100-bugs-in-Open-Source-C-C-projects-47-2048.jpg)

![...
if (key_len > 79)
{
png_warning(png_ptr, "keyword length must be 1 - 79 characters");
new_key[79] = '0';
key_len = 79;
}
...
}
The error was found through the V527 diagnostic: It is odd that the '0' value is assigned to 'char' type
pointer. Probably meant: *new_key [79] = '0'. graphics3D pngwutil.c 1283
This sample demonstrates a mistake when the programmer accidentally clears the pointer instead of
truncating the string length. The point is that 'new_key' is a pointer to a string. And it means that we
should write our code as follows to truncate it to 79 characters:
(*new_key)[79] = '0';
Example 8. Intel AMT SDK project. Unverified user name.
static void
wsman_set_subscribe_options(...)
{
...
if (options->delivery_certificatethumbprint ||
options->delivery_password ||
options->delivery_password) {
...
}
The error was found through the V501 diagnostic: There are identical sub-expressions 'options-
>delivery_password' to the left and to the right of the '||' operator. OpenWsmanLib wsman-client.c 631
Because of the developer's inattention, presence of password is checked twice, while presence of user
name is not checked at all. This is the correct code:
if (options->delivery_certificatethumbprint ||](https://image.slidesharecdn.com/bugs-100-130729071042-phpapp02/75/100-bugs-in-Open-Source-C-C-projects-50-2048.jpg)
![options->delivery_username ||
options->delivery_password) {
Example 9. Ultimate TCP/IP project. Incorrect handling of empty strings.
void CUT_StrMethods::RemoveCRLF(LPSTR buf)
{
// v4.2 changed to size_t
size_t len, indx = 1;
if(buf != NULL){
len = strlen(buf);
while((len - indx) >= 0 && indx <= 2) {
if(buf[len - indx] == 'r' ||
buf[len - indx] == 'n')
buf[len - indx] = 0;
++indx;
}
}
}
The error was found through the V547 diagnostic: Expression '(len - indx) >= 0' is always true. Unsigned
type value is always >= 0. UTDns utstrlst.cpp 58
The "len - indx" expression has the unsigned type 'size_t' and is always >= 0. Let's look what it will result
in, if we send an empty string to the input.
If the string is empty, then: len = 0, indx = 1.
The len - indx expression is equal to 0xFFFFFFFFu.
Since 0xFFFFFFFFu > 0 and indx <= 2, an array access is performed
"buf[len - indx]".
The "buf[0xFFFFFFFFu]" operation will cause Access Violation.
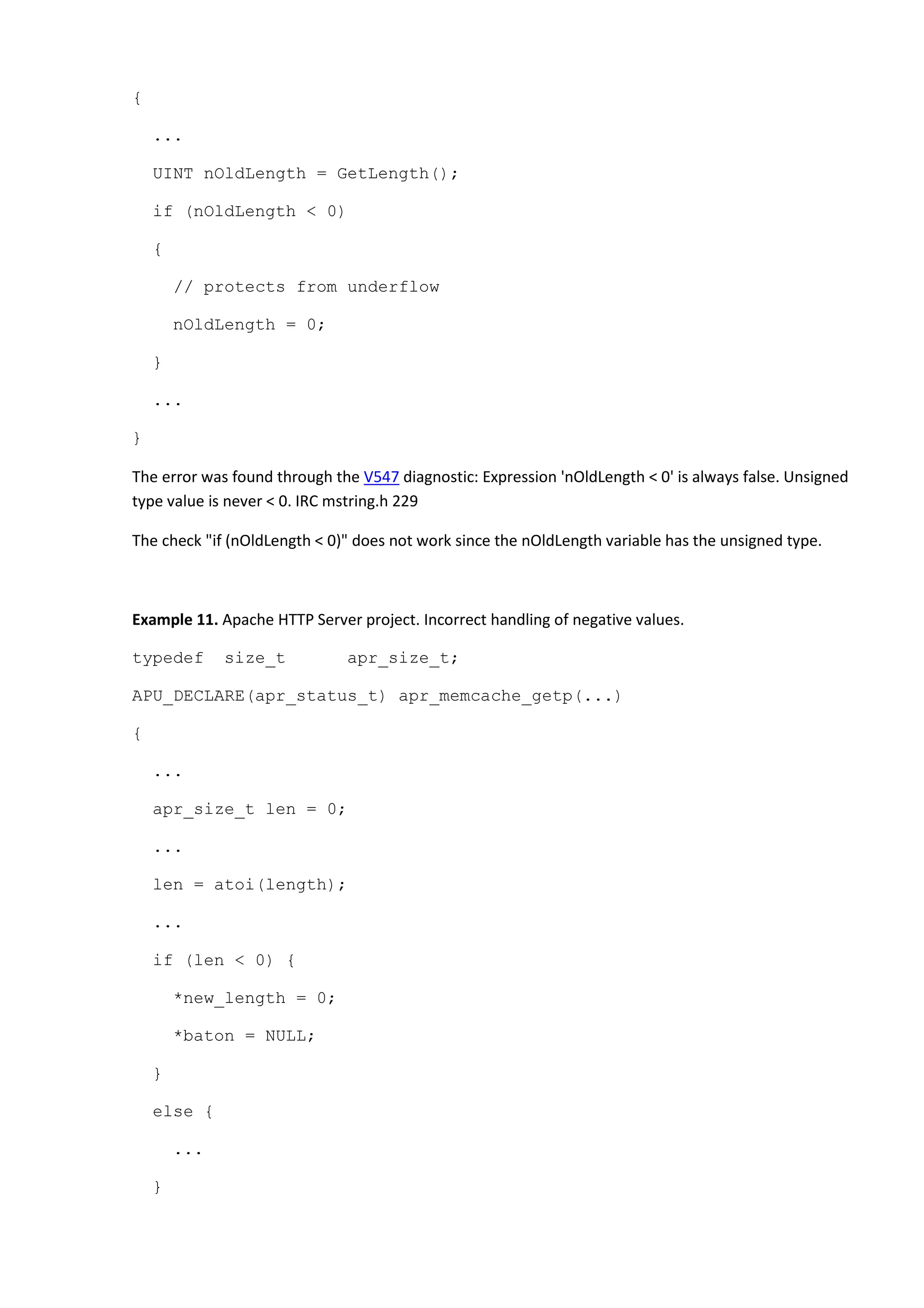
Example 10. Miranda IM project. Underflow protection does not work.
void Append( PCXSTR pszSrc, int nLength )](https://image.slidesharecdn.com/bugs-100-130729071042-phpapp02/75/100-bugs-in-Open-Source-C-C-projects-51-2048.jpg)
![}
The error was found through the V547 diagnostic: Expression 'len < 0' is always false. Unsigned type
value is never < 0. aprutil apr_memcache.c 814
The check "if (len < 0)" does not work because the 'len' variable has the unsigned type.
Example 12. Ultimate TCP/IP project. Incorrect condition of loop termination.
void CUT_StrMethods::RemoveSpaces(LPSTR szString) {
...
size_t loop, len = strlen(szString);
// Remove the trailing spaces
for(loop = (len-1); loop >= 0; loop--) {
if(szString[loop] != ' ')
break;
}
...
}
The error was found through the V547 diagnostic: Expression 'loop >= 0' is always true. Unsigned type
value is always >= 0. UTDns utstrlst.cpp 430
Suppose the whole string consists only of spaces. While searching the characters, the program will reach
the null item of the string, and the 'loop' variable will equal to zero. Then it will be decremented once
again. Since this variable is of unsigned type, its value will be 0xFFFFFFFFu or 0xFFFFFFFFFFFFFFFFu
(depending on the architecture). This value is 'naturally >= 0', and a new loop iteration will start. There
will be an attempt of memory access by szString[0xFFFFFFFFu] address - the consequences of this are
familiar to every C/C++ programmer.
Example 13. Crypto++ project. Private data clearing error.
void CAST256::Base::UncheckedSetKey(const byte *userKey,
unsigned int keylength, const NameValuePairs &)
{
AssertValidKeyLength(keylength);
word32 kappa[8];
...](https://image.slidesharecdn.com/bugs-100-130729071042-phpapp02/75/100-bugs-in-Open-Source-C-C-projects-53-2048.jpg)
![memset(kappa, 0, sizeof(kappa));
}
The error has been found with rule V597: The compiler could delete the 'memset' function call, which is
used to flush 'kappa' buffer. The RtlSecureZeroMemory() function should be used to erase the private
data. cryptlib cast.cpp 293
The problem is in the memset() function. The arguments passed into the function are correct. If a
programmer looks how the Debug-version of this code works in the debugger, he/she won't notice the
trouble either. The error occurs in the Release version of the project. The data that should have been
cleared will remain in memory. The reason is that the compiler has the right to delete the call of the
memset() function during optimization, and this is what it does. If you want know why it happens, read
the article "Overwriting memory - why?".
Copy-Paste
Developers should not also underestimate Copy-Paste errors as well as common misprints. They are
very-very numerous. Programmers spend much time on debugging them.
Of course, misprints and Copy-Paste errors are similar, but there is a difference between them that
caused us to place them into different groups in this article. Misprints often result in using a wrong
variable instead of the needed one. And in the case of copy-paste, programmers simply forget to edit
copied and pasted lines.
Example 1. Fennec Media Project project. Mistake while handling array items.
void* tag_write_setframe(char *tmem,
const char *tid, const string dstr)
{
...
if(lset)
{
fhead[11] = '0';
fhead[12] = '0';
fhead[13] = '0';
fhead[13] = '0';
}
...
}](https://image.slidesharecdn.com/bugs-100-130729071042-phpapp02/75/100-bugs-in-Open-Source-C-C-projects-54-2048.jpg)
![The error was found through the V525 diagnostic: The code containing the collection of similar blocks.
Check items '11', '12', '13', '13' in lines 716, 717, 718, 719. id3 editor.c 716
The four similar lines must have appeared in the code through the copy-paste method. When the
programmer started editing the indexes, he/she made a mistake that causes zero to be written into
'fhead[13] ' twice and not be written into 'fhead[14] '.
Example 2. MySQL project. Mistake while handling array items.
static int rr_cmp(uchar *a,uchar *b)
{
if (a[0] != b[0])
return (int) a[0] - (int) b[0];
if (a[1] != b[1])
return (int) a[1] - (int) b[1];
if (a[2] != b[2])
return (int) a[2] - (int) b[2];
if (a[3] != b[3])
return (int) a[3] - (int) b[3];
if (a[4] != b[4])
return (int) a[4] - (int) b[4];
if (a[5] != b[5])
return (int) a[1] - (int) b[5];
if (a[6] != b[6])
return (int) a[6] - (int) b[6];
return (int) a[7] - (int) b[7];
}
The error was found through the V525 diagnostic: The code containing the collection of similar blocks.
Check items '0', '1', '2', '3', '4', '1', '6' in lines 680, 682, 684, 689, 691, 693, 695. sql records.cc 680
It is not apparent at first sight, so let's single it out:
return (int) a[1] - (int) b[5];
Actually there must be the following code:
return (int) a[5] - (int) b[5];](https://image.slidesharecdn.com/bugs-100-130729071042-phpapp02/75/100-bugs-in-Open-Source-C-C-projects-55-2048.jpg)


![t=y1; y1=y2; y2=t;
Example 6. Crystal Space 3D SDK project. Identical subexpressions.
inline_ bool Contains(const LSS& lss)
{
return Contains(Sphere(lss.mP0, lss.mRadius)) &&
Contains(Sphere(lss.mP0, lss.mRadius));
}
The error was found through the V501 diagnostic: There are identical sub-expressions to the left and to
the right of the '&&' operator. plgcsopcode icelss.h 69
The error is this: the 'lss.mP0.' variable is used twice here. There must be 'lss.mP1' in the first part of the
expression.
Example 7. Notepad++ project. Setting an incorrect style.
void KeyWordsStyleDialog::updateDlg()
{
...
Style & w1Style =
_pUserLang->_styleArray.getStyler(STYLE_WORD1_INDEX);
styleUpdate(w1Style, _pFgColour[0], _pBgColour[0],
IDC_KEYWORD1_FONT_COMBO, IDC_KEYWORD1_FONTSIZE_COMBO,
IDC_KEYWORD1_BOLD_CHECK, IDC_KEYWORD1_ITALIC_CHECK,
IDC_KEYWORD1_UNDERLINE_CHECK);
Style & w2Style =
_pUserLang->_styleArray.getStyler(STYLE_WORD2_INDEX);
styleUpdate(w2Style, _pFgColour[1], _pBgColour[1],
IDC_KEYWORD2_FONT_COMBO, IDC_KEYWORD2_FONTSIZE_COMBO,
IDC_KEYWORD2_BOLD_CHECK, IDC_KEYWORD2_ITALIC_CHECK,
IDC_KEYWORD2_UNDERLINE_CHECK);](https://image.slidesharecdn.com/bugs-100-130729071042-phpapp02/75/100-bugs-in-Open-Source-C-C-projects-58-2048.jpg)
![Style & w3Style =
_pUserLang->_styleArray.getStyler(STYLE_WORD3_INDEX);
styleUpdate(w3Style, _pFgColour[2], _pBgColour[2],
IDC_KEYWORD3_FONT_COMBO, IDC_KEYWORD3_FONTSIZE_COMBO,
IDC_KEYWORD3_BOLD_CHECK, IDC_KEYWORD3_BOLD_CHECK,
IDC_KEYWORD3_UNDERLINE_CHECK);
Style & w4Style =
_pUserLang->_styleArray.getStyler(STYLE_WORD4_INDEX);
styleUpdate(w4Style, _pFgColour[3], _pBgColour[3],
IDC_KEYWORD4_FONT_COMBO, IDC_KEYWORD4_FONTSIZE_COMBO,
IDC_KEYWORD4_BOLD_CHECK, IDC_KEYWORD4_ITALIC_CHECK,
IDC_KEYWORD4_UNDERLINE_CHECK);
...
}
The error was found through the V525 diagnostic: The code containing the collection of similar blocks.
Check items '7', '7', '6', '7' in lines 576, 580, 584, 588
It is almost unreal to find this error by sight, so let's abridge the text to single out the most interesting
fragments:
styleUpdate(...
IDC_KEYWORD1_BOLD_CHECK, IDC_KEYWORD1_ITALIC_CHECK,
...);
styleUpdate(...
IDC_KEYWORD2_BOLD_CHECK, IDC_KEYWORD2_ITALIC_CHECK,
...);
styleUpdate(...
IDC_KEYWORD3_BOLD_CHECK, IDC_KEYWORD3_BOLD_CHECK, <<--
...);
styleUpdate(...
IDC_KEYWORD4_BOLD_CHECK, IDC_KEYWORD4_ITALIC_CHECK,](https://image.slidesharecdn.com/bugs-100-130729071042-phpapp02/75/100-bugs-in-Open-Source-C-C-projects-59-2048.jpg)

![standard situation. Instead of correctly processing a null pointer in normal mode, an Access Violation
will occur and an exception will be thrown.
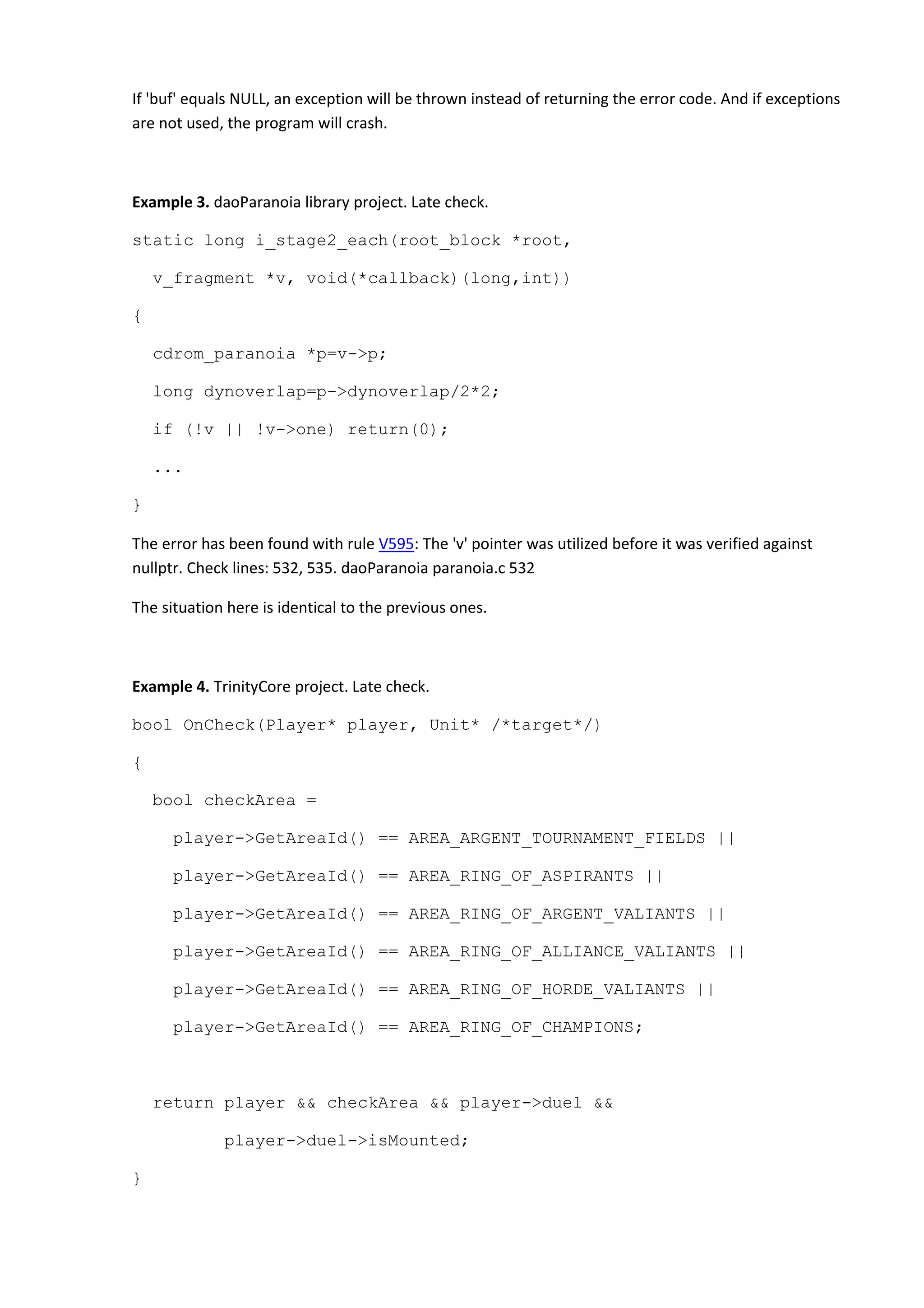
Example 1. Quake-III-Arena project. Late check.
void Item_Paint(itemDef_t *item) {
vec4_t red;
menuDef_t *parent = (menuDef_t*)item->parent;
red[0] = red[3] = 1;
red[1] = red[2] = 0;
if (item == NULL) {
return;
}
...
}
The error has been found with rule V595: The 'item' pointer was utilized before it was verified against
nullptr. Check lines: 3865, 3869. cgame ui_shared.c 3865
The 'item' pointer is used first and only then is compared to NULL.
Example 2. LAME Ain't an MP3 Encoder project. Late check.
static int
check_vbr_header(PMPSTR mp, int bytes)
{
...
buf = buf->next;
pos = buf->pos;
if(!buf) return -1; /* fatal error */
...
}
The error has been found with rule V595: The 'buf' pointer was utilized before it was verified against
nullptr. Check lines: 226, 227. mpglib interface.c 226](https://image.slidesharecdn.com/bugs-100-130729071042-phpapp02/75/100-bugs-in-Open-Source-C-C-projects-62-2048.jpg)
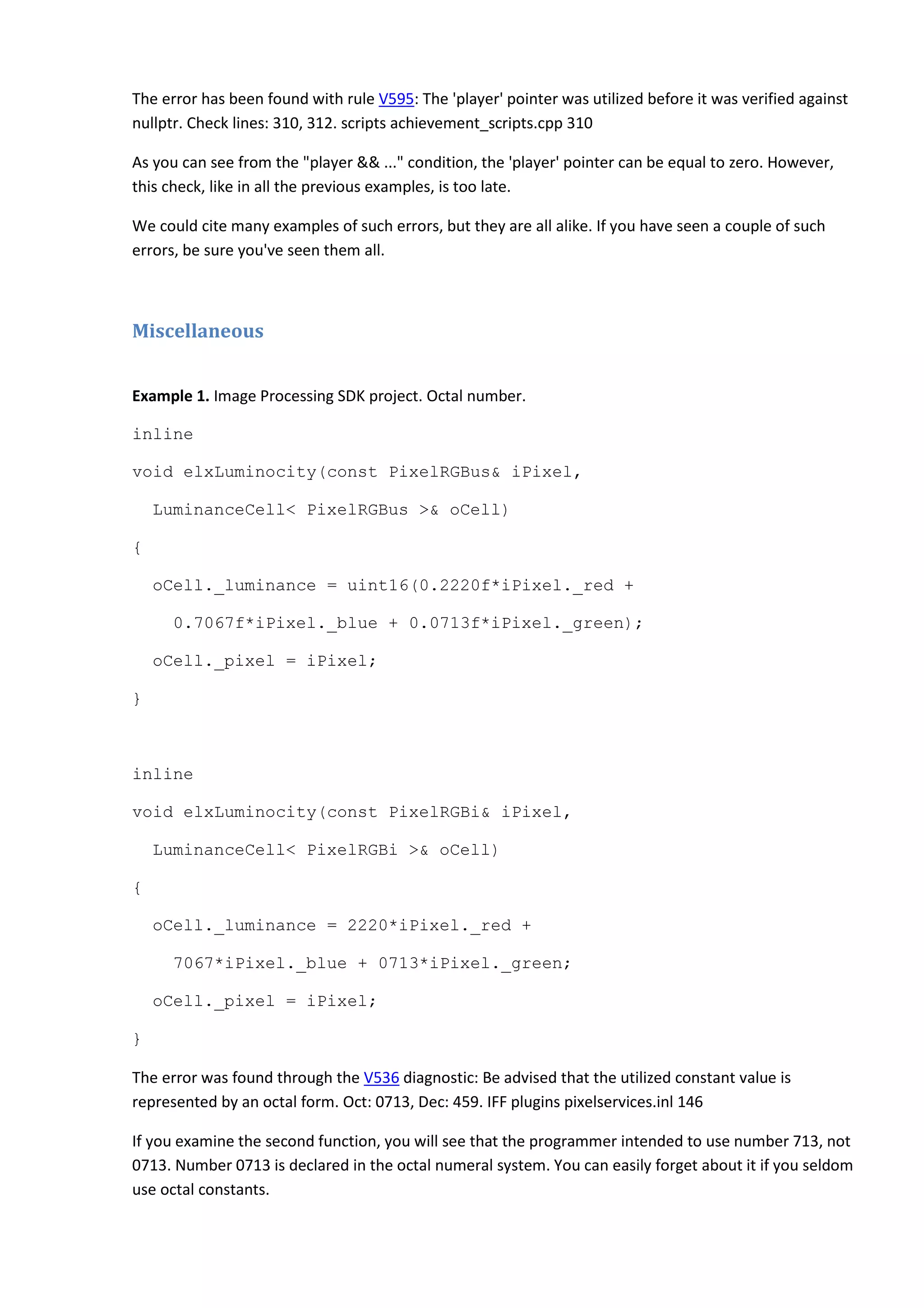
![Example 2. IPP Samples project. One variable for two loops.
JERRCODE CJPEGDecoder::DecodeScanBaselineNI(void)
{
...
for(c = 0; c < m_scan_ncomps; c++)
{
block = m_block_buffer + (DCTSIZE2*m_nblock*(j+(i*m_numxMCU)));
// skip any relevant components
for(c = 0; c < m_ccomp[m_curr_comp_no].m_comp_no; c++)
{
block += (DCTSIZE2*m_ccomp[c].m_nblocks);
}
...
}
The error was found through the V535 diagnostic: The variable 'c' is being used for this loop and for the
outer loop. jpegcodec jpegdec.cpp 4652
One and the same variable is used for the outer loop and the inner loop. As a result, this code will
handle only part of the data or cause an eternal loop.
Example 3. Quake-III-Arena project. Missing return.
static ID_INLINE int BigLong(int l)
{ LongSwap(l); }
The error has been found with rule V591: Non-void function should return a value. botlib q_shared.h
155
This code is written in C. It means that the compiler doesn't require that return should be necessarily
present. But it is really necessary here. However, the code can work well due to sheer luck. Everything
depends on what the EAX register contains. But it's just luck and nothing more. The function body
should have been written this way: { return LongSwap(l); }.
Example 4. Notepad++ project. Odd condition.](https://image.slidesharecdn.com/bugs-100-130729071042-phpapp02/75/100-bugs-in-Open-Source-C-C-projects-65-2048.jpg)
