1. There are three main types of user accounts - local user accounts that access resources on a single computer, domain user accounts that access resources across a network domain, and built-in accounts like Administrator and Guest.
2. Group accounts allow efficient administration by assigning permissions to collections of users rather than individual accounts. Domain local groups can be used to share resources by adding global groups of users.
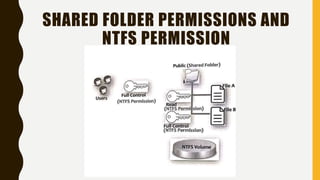
3. Shared folders allow authorized users to access files from their own computers. Shared folder permissions control access but provide less security than NTFS permissions on individual files. When both are applied, the more restrictive permission takes precedence.