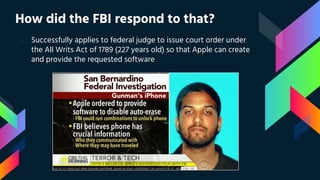
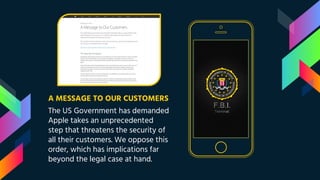
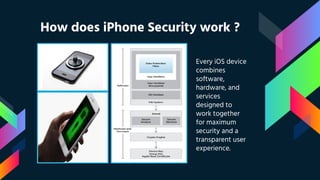
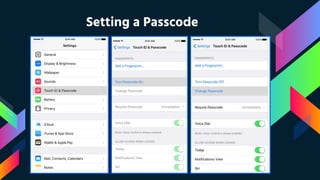
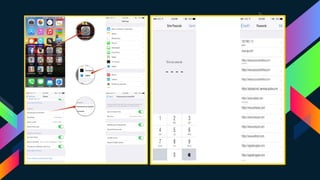
This document summarizes the dispute between Apple and the FBI over unlocking an iPhone used by one of the San Bernardino shooters. It describes the 2015 terrorist attack, the FBI's request that Apple create a backdoor to unlock the shooter's work iPhone, and Apple's refusal on security grounds. It also discusses the FBI obtaining a court order, concerns over data privacy and security if backdoors are created, and support for Apple's position from privacy advocates like Edward Snowden.