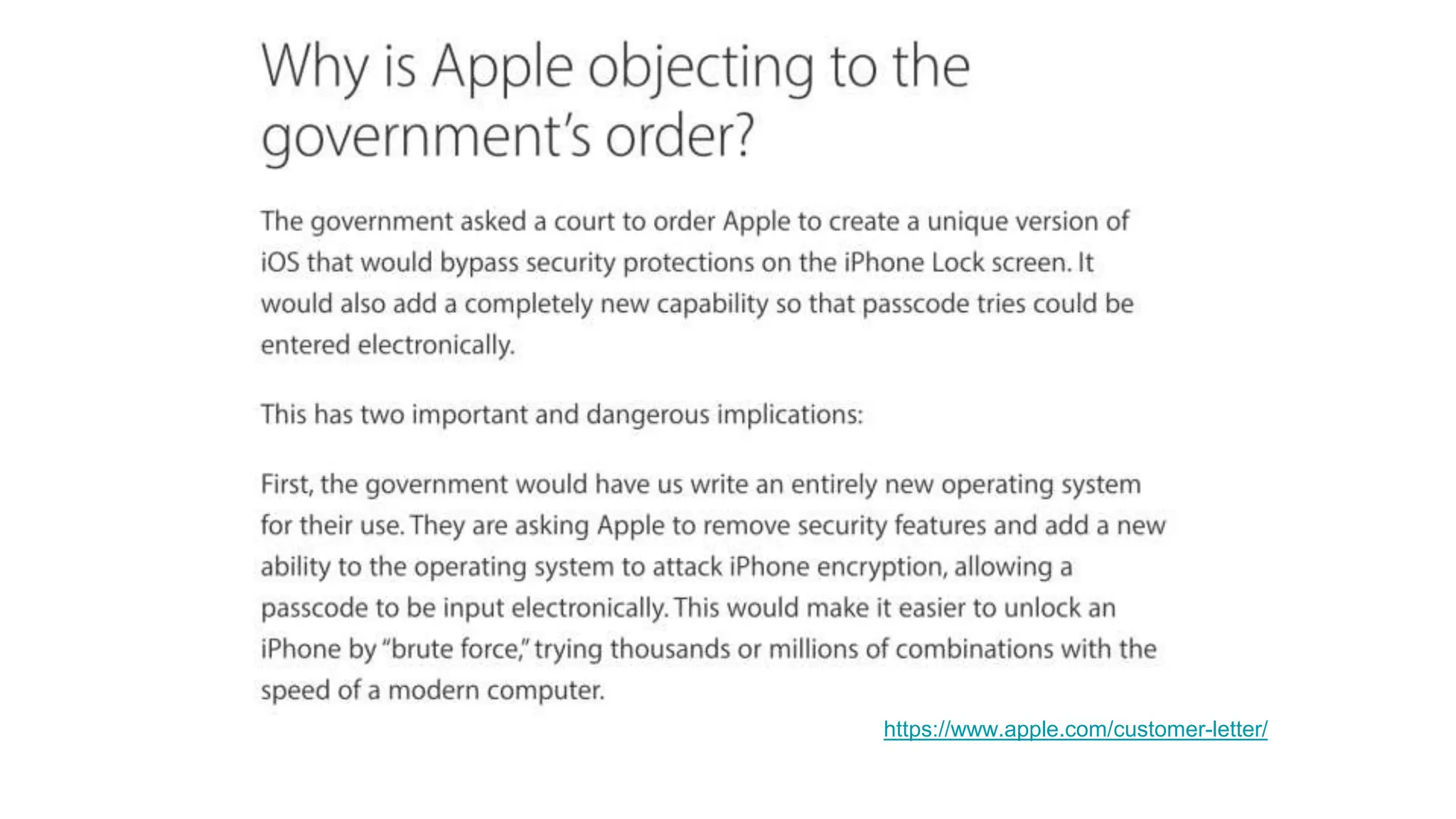
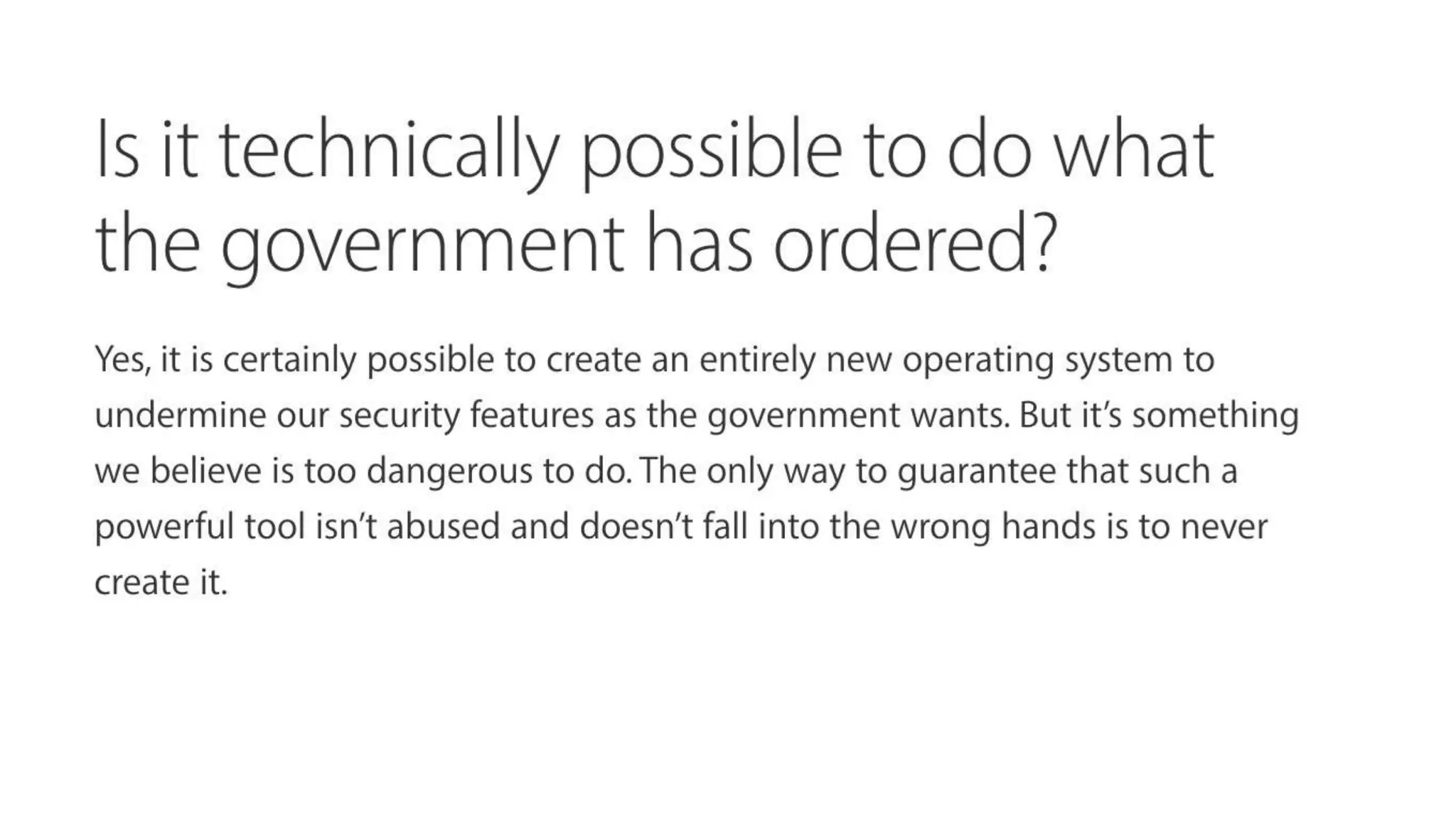
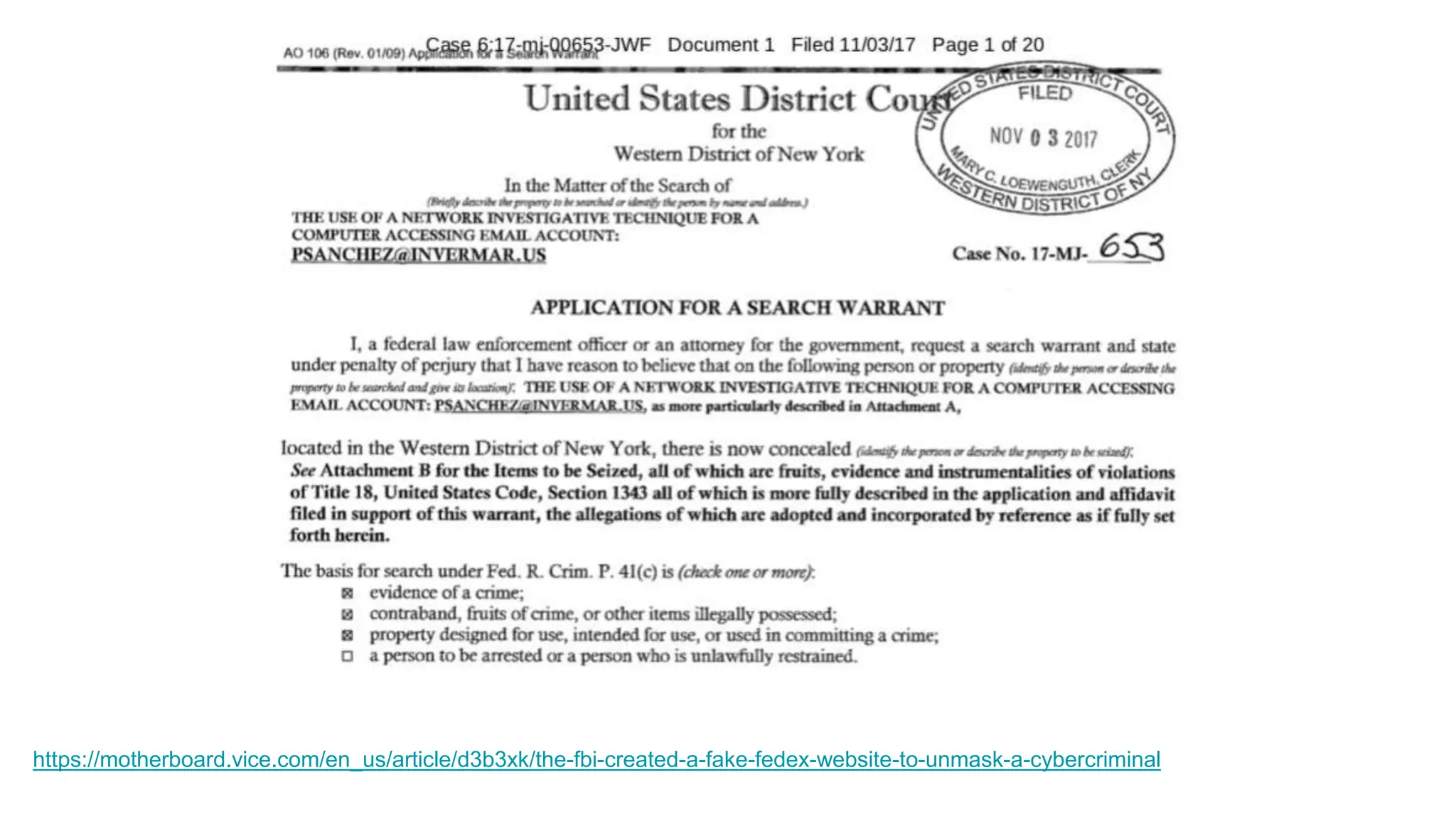
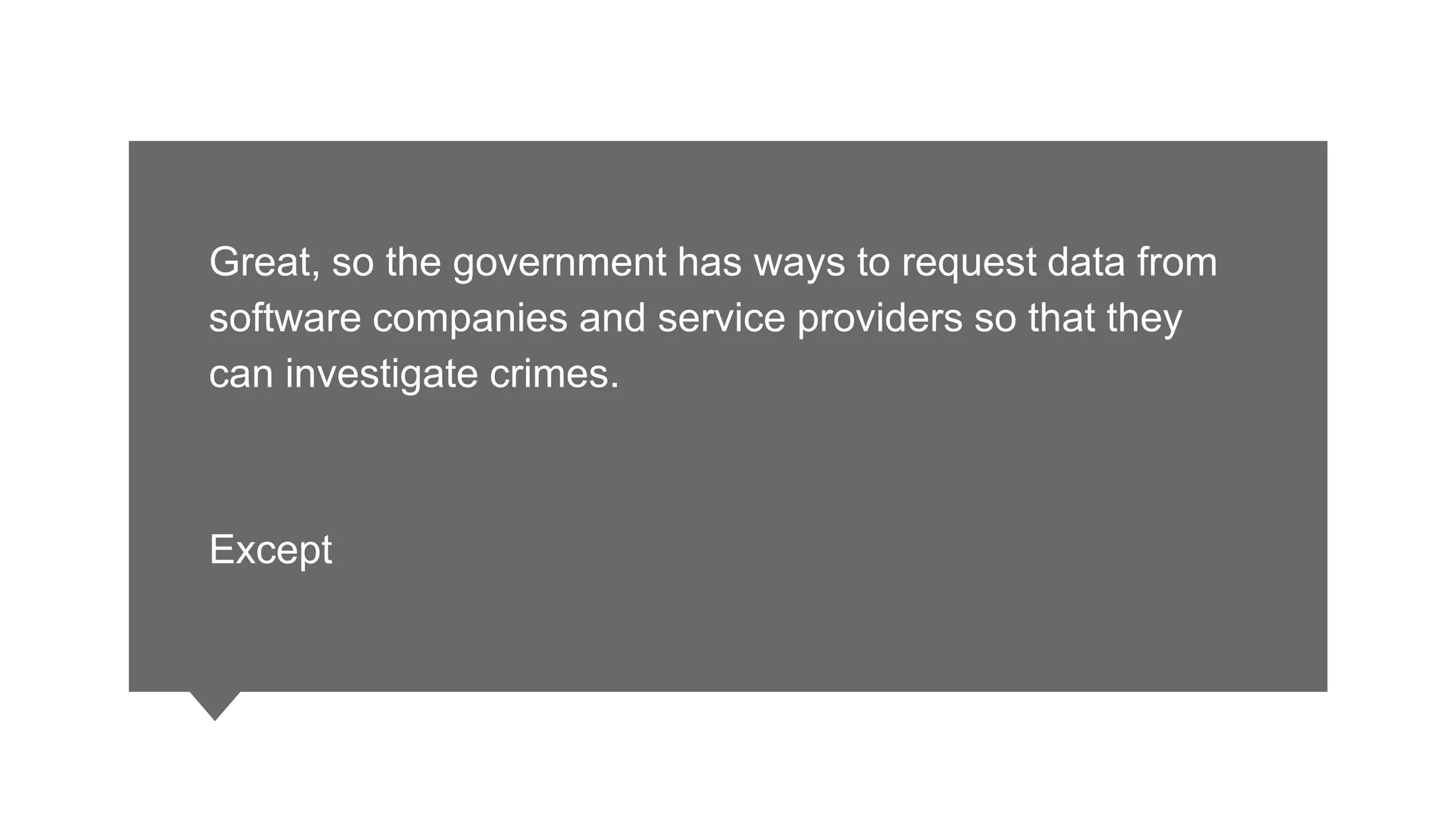
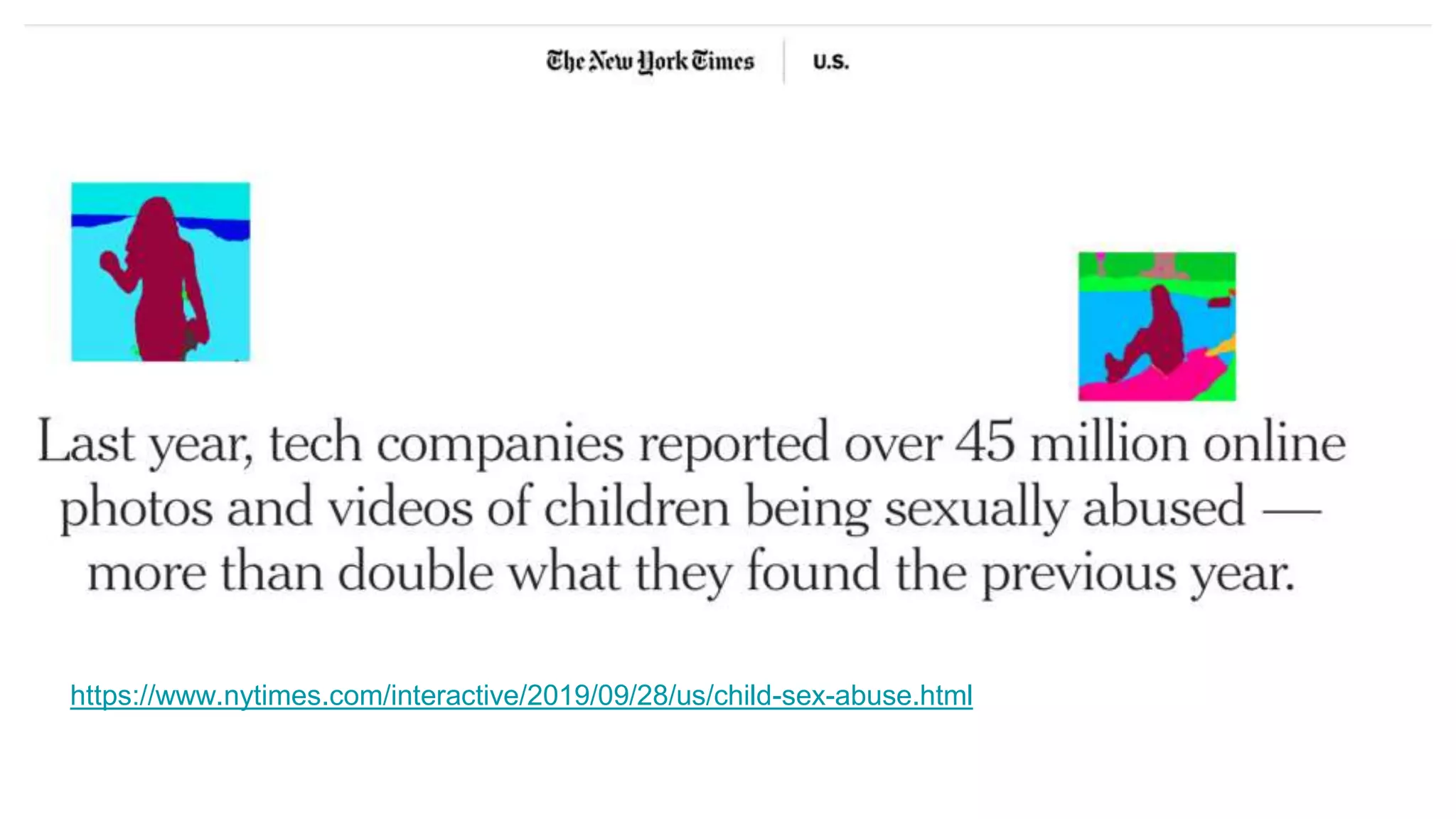
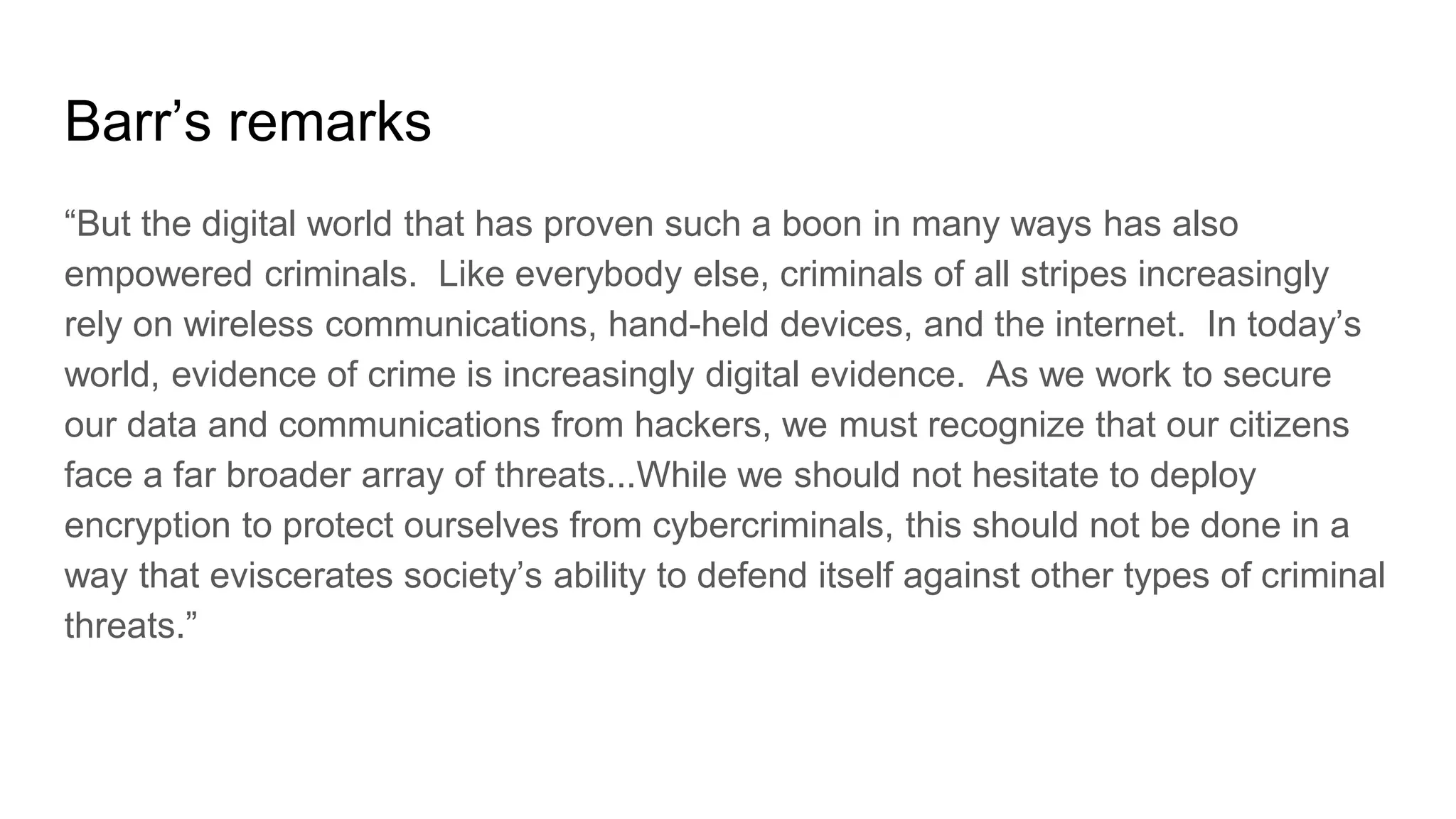
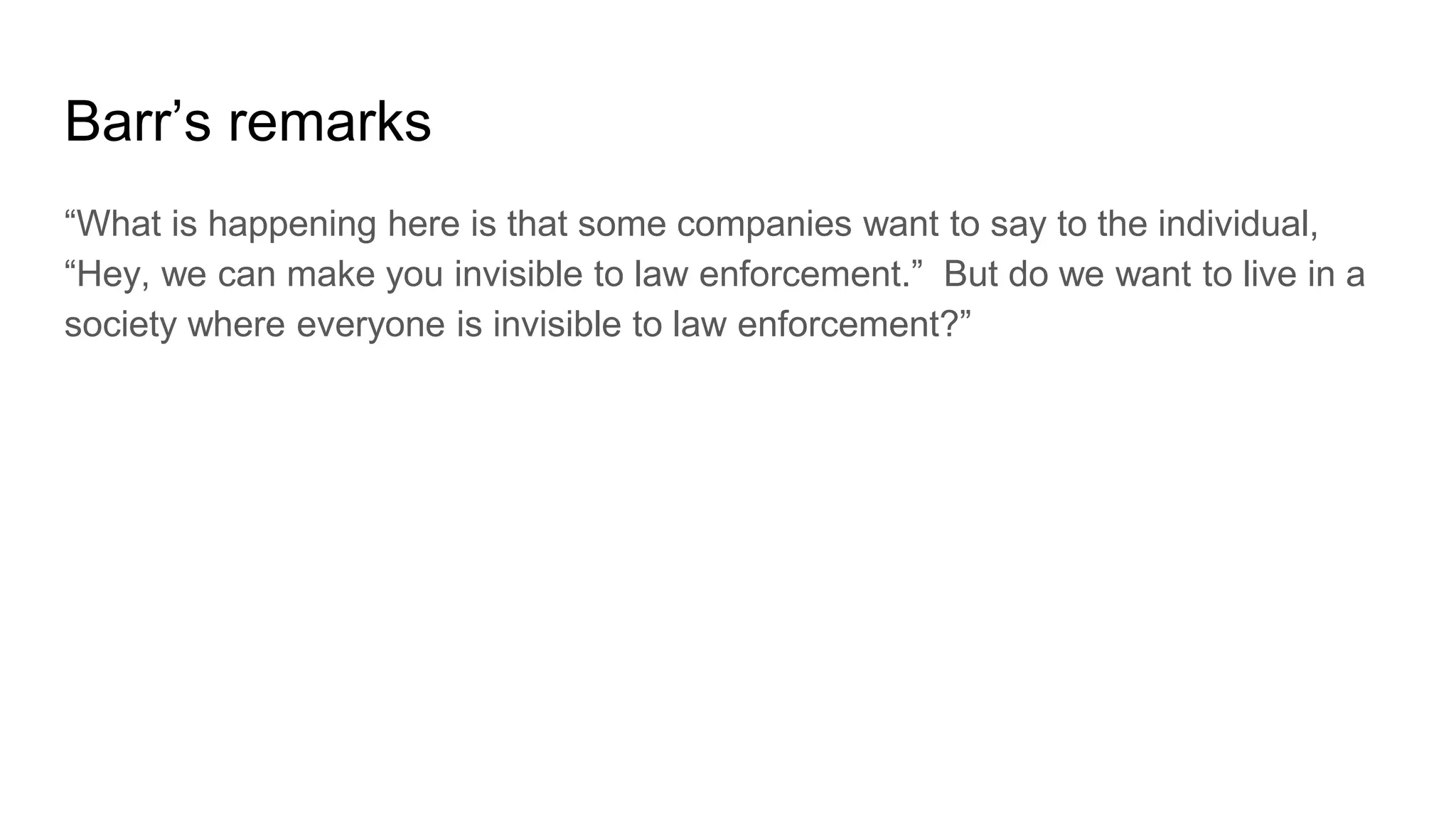
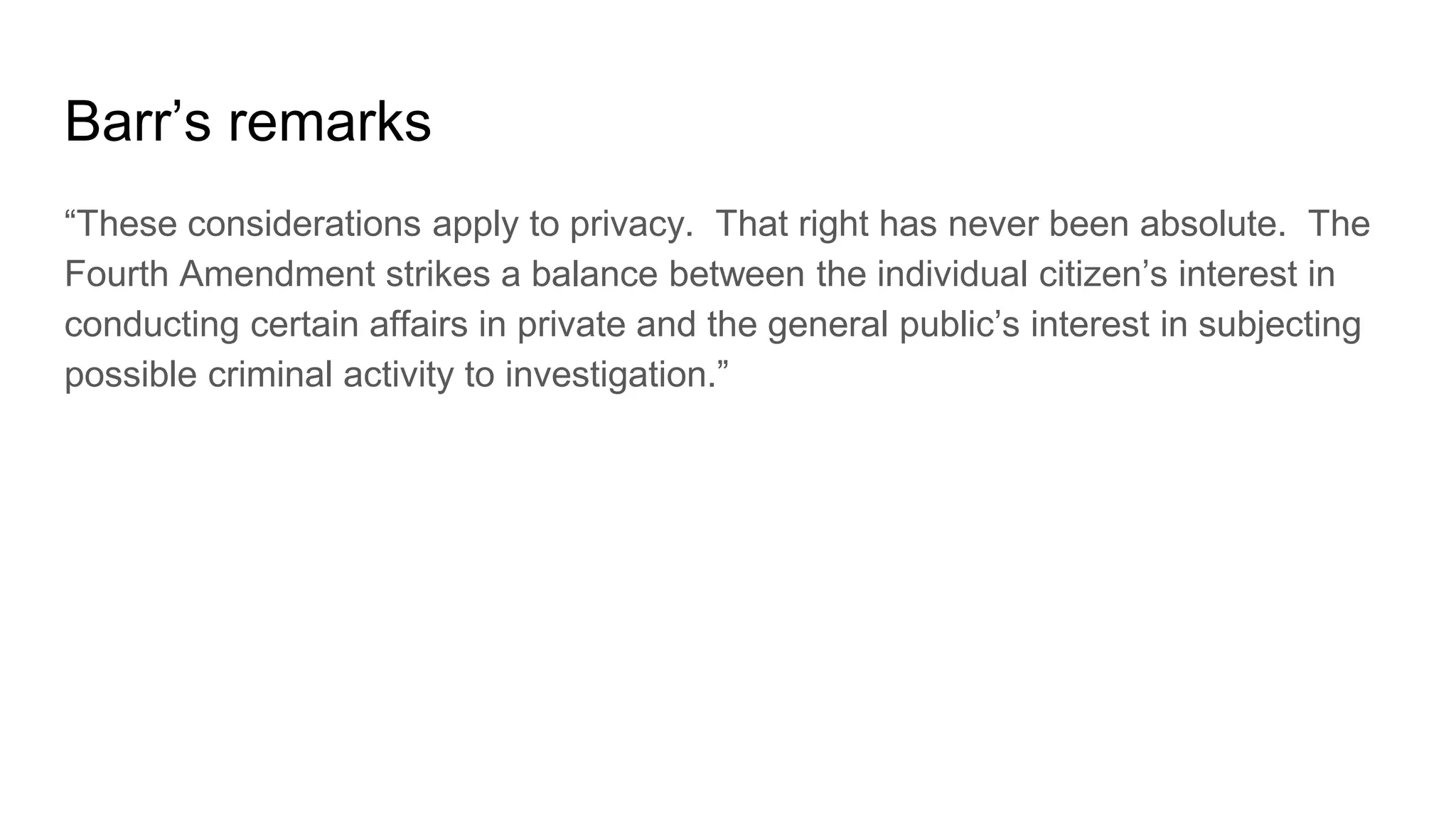
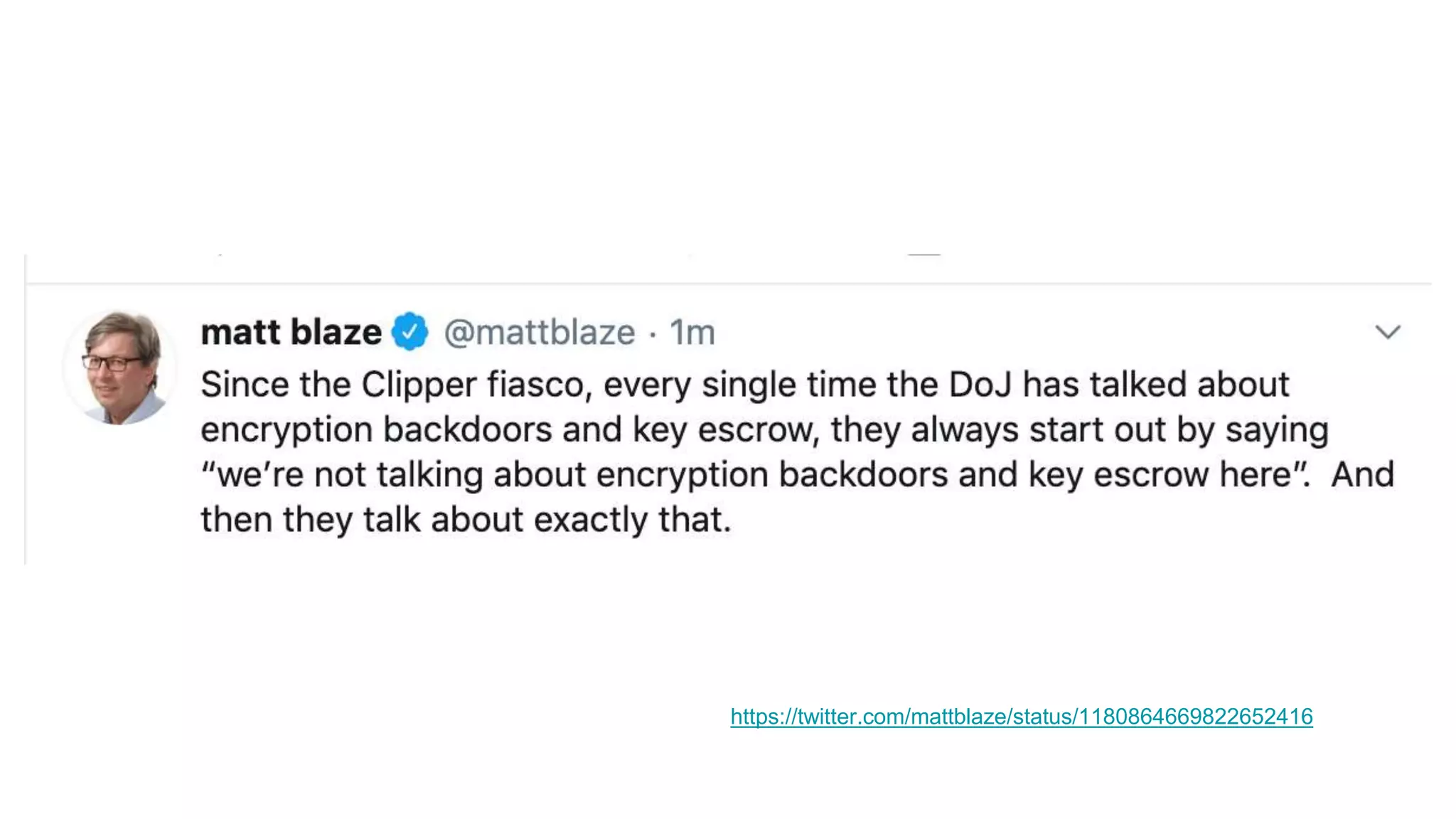
Wendy Knox Everette provides a summary of the history of encryption regulation and debates around law enforcement access to encrypted data. She discusses key cases like Bernstein v. United States and Apple v. FBI. Everette notes ongoing tensions between law enforcement desires for access and technology companies' stance that weakened encryption harms all users. Recent events like attempts to force Facebook to wiretap Messenger and Attorney General Barr's calls for lawful access are also summarized.