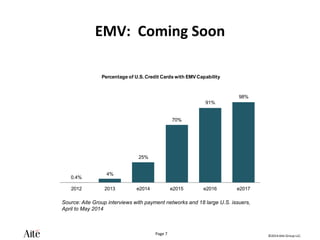
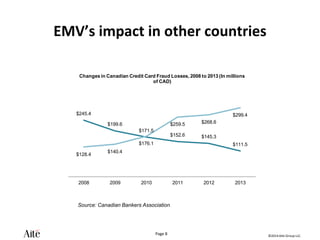
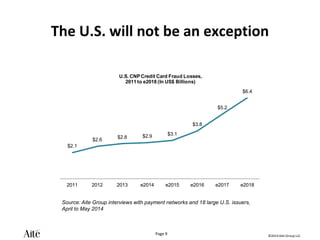
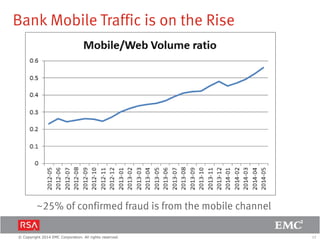
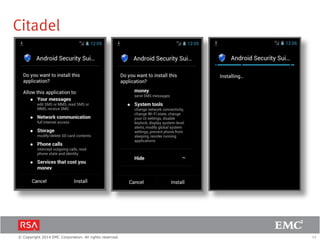
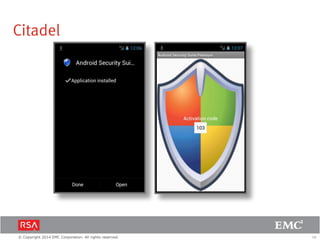
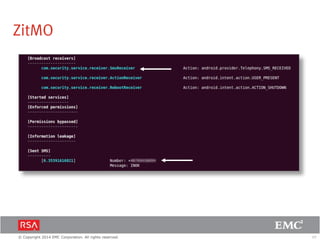
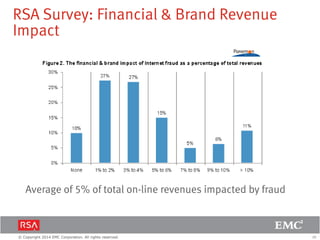
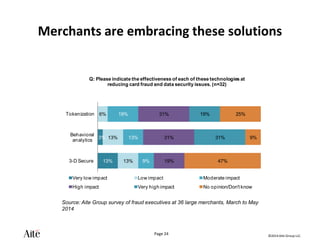
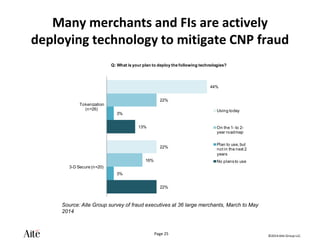
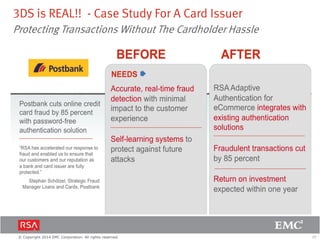
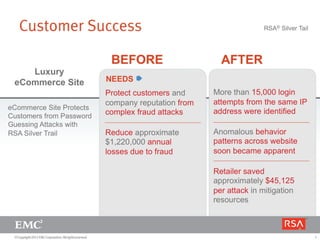
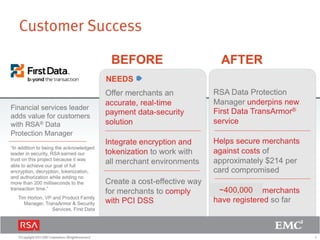
The document discusses the forecast for card and payments fraud, focusing on the adoption of EMV technology in the U.S. and emerging e-commerce fraud trends. It highlights the increasing use of mobile devices for transactions and various methods employed by fraudsters, alongside best practices for securing payment systems. Additionally, it emphasizes the importance of technological solutions, such as tokenization and behavioral analytics, for mitigating card fraud.