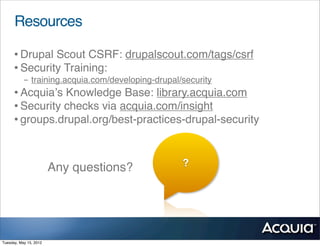
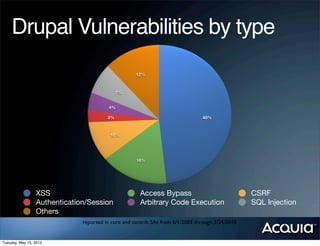
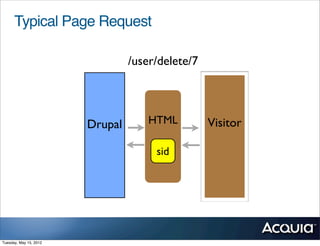
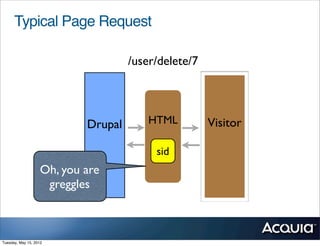
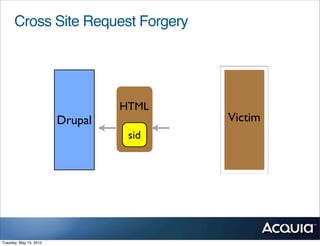
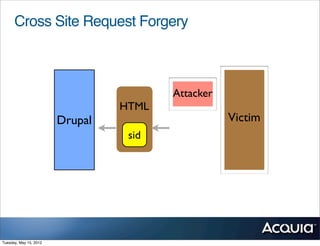
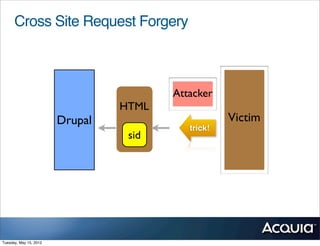
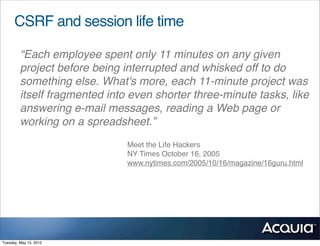
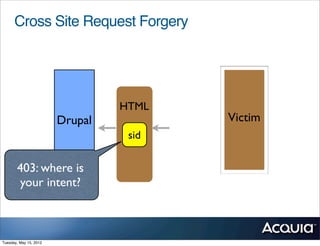
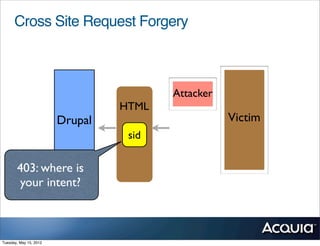
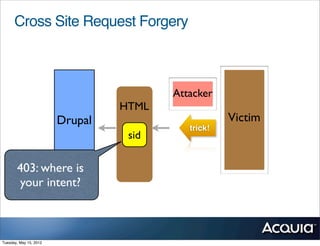
The document discusses protecting a website from cross-site request forgery (CSRF) attacks. It describes how CSRF works by tricking a victim's browser into making requests to a target site on behalf of an attacker. The document recommends using tokens or nonces to validate that requests are intentionally sent by the user and not generated by another site. It also provides resources for learning more about CSRF prevention, security training, and getting security audits for Drupal sites.










![Preventing CSRF
• Just use the form API
Links and Ajax without FAPI:
• Request:
'query' = array('token' => drupal_get_token('my_id');
• Processing:
if (!drupal_valid_token($_GET['token'], 'my_id')) {
• More: http://drupalscout.com/node/20
Tuesday, May 15, 2012](https://image.slidesharecdn.com/20120515acquiabrandedcsrf-120516101429-phpapp02/85/Protect-you-site-from-CSRF-30-320.jpg)