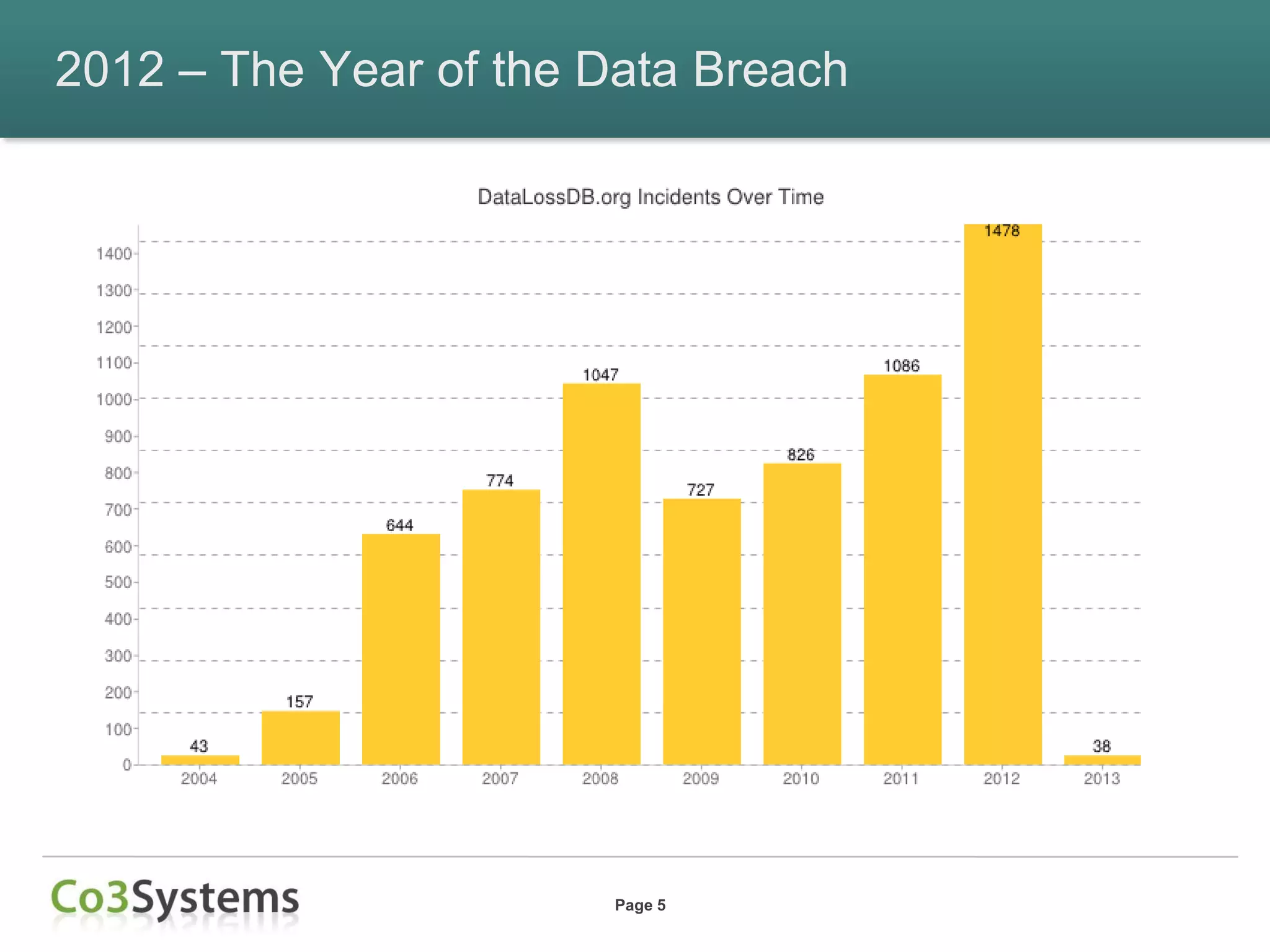
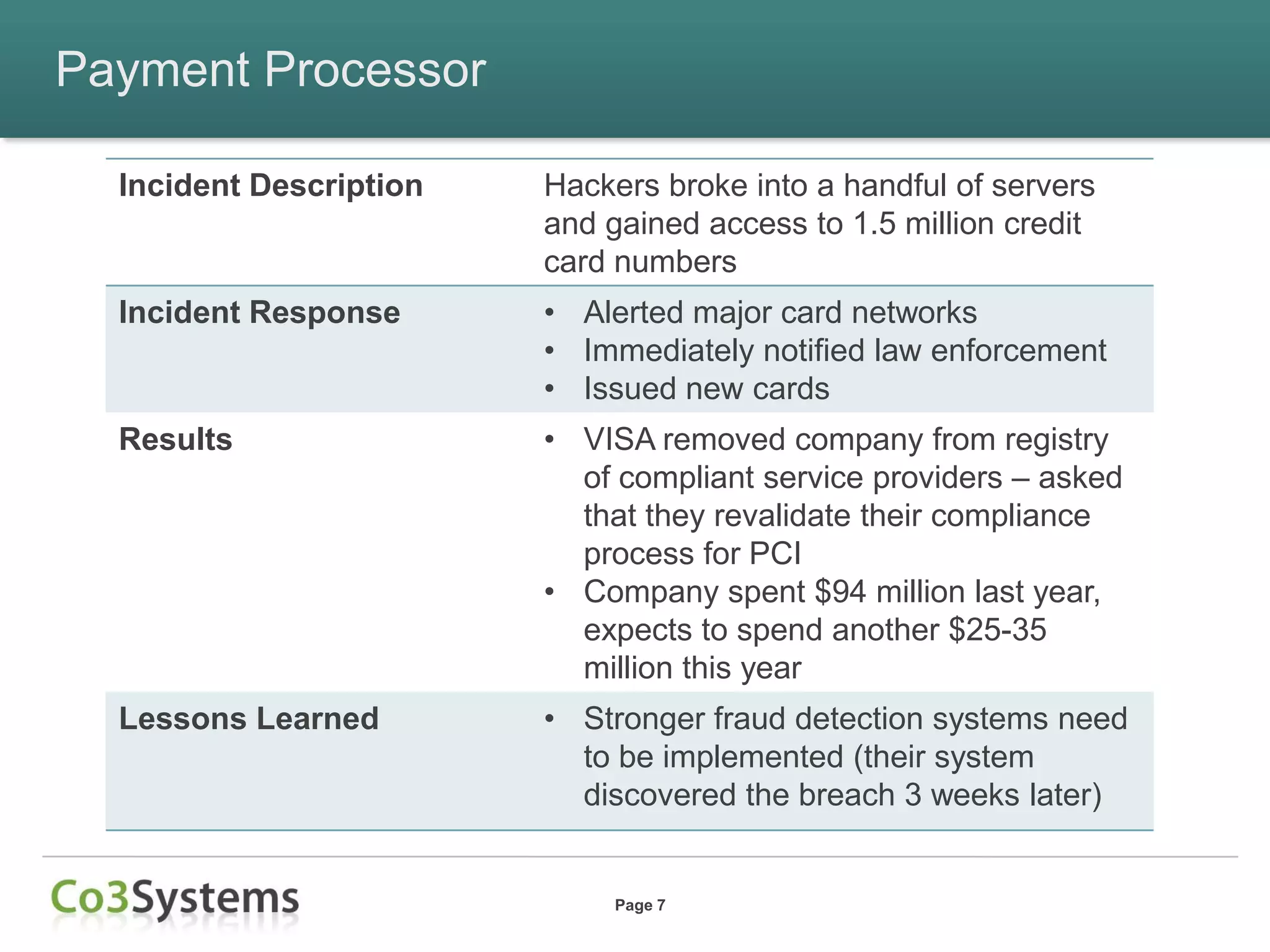
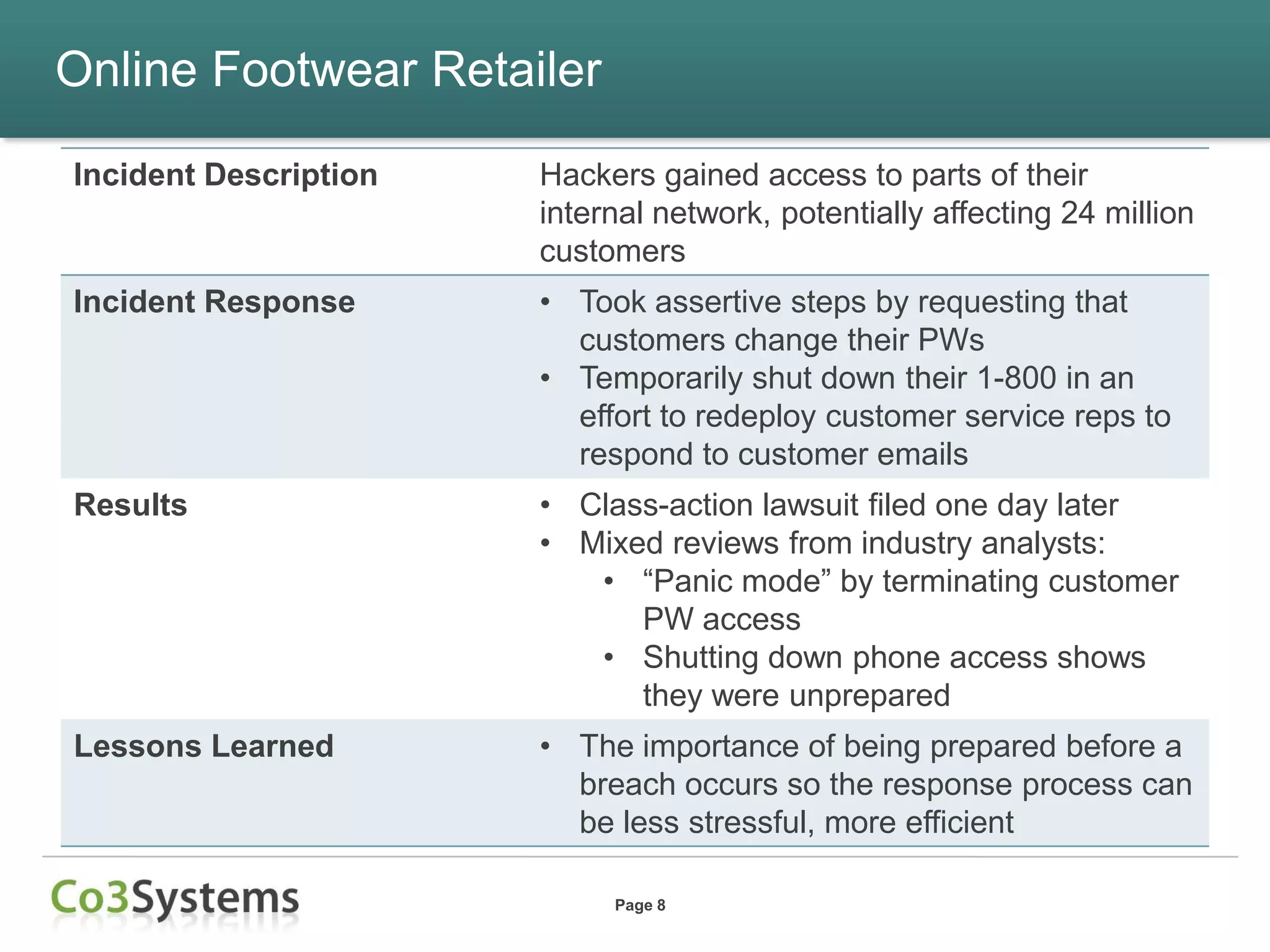
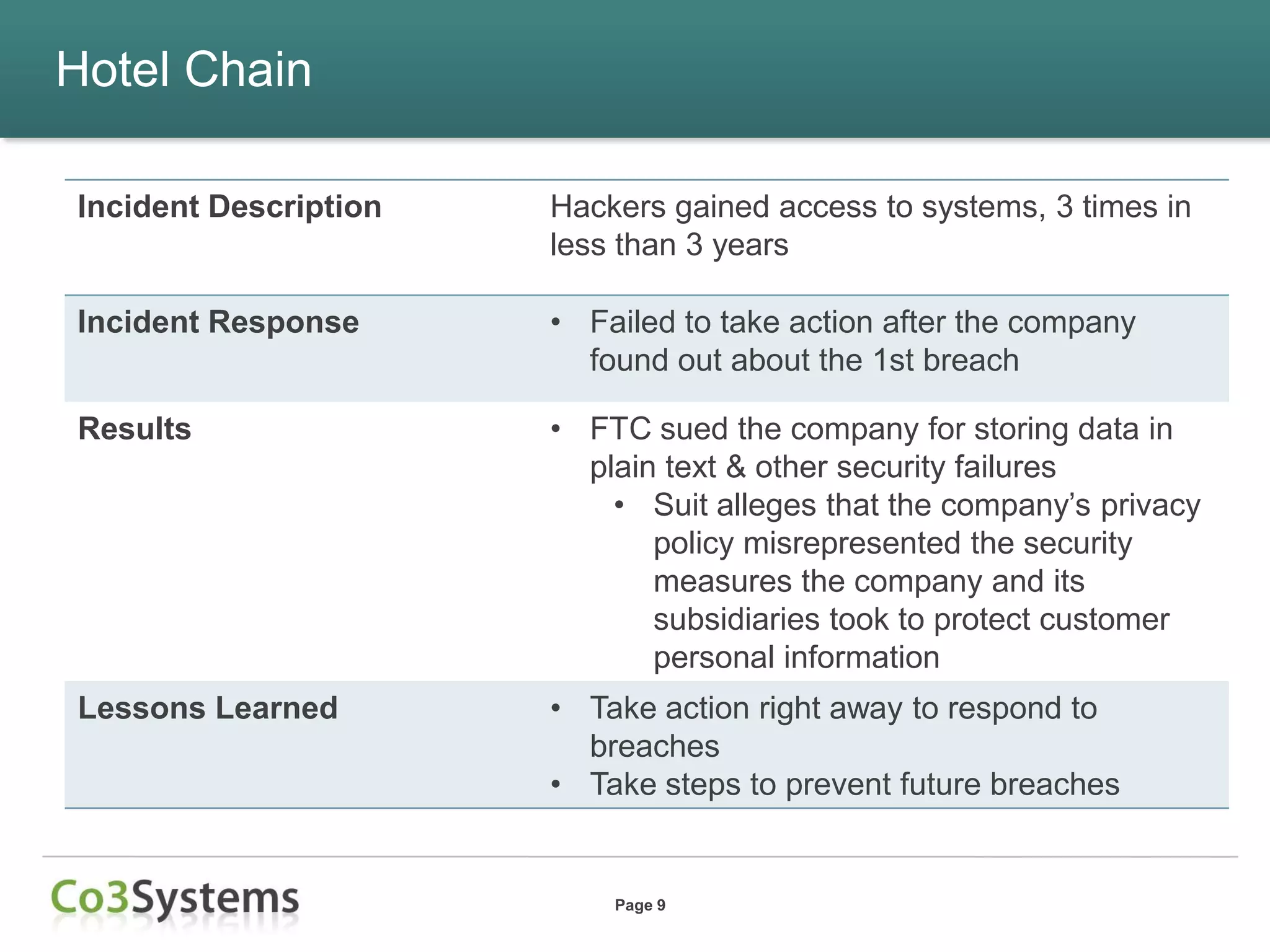
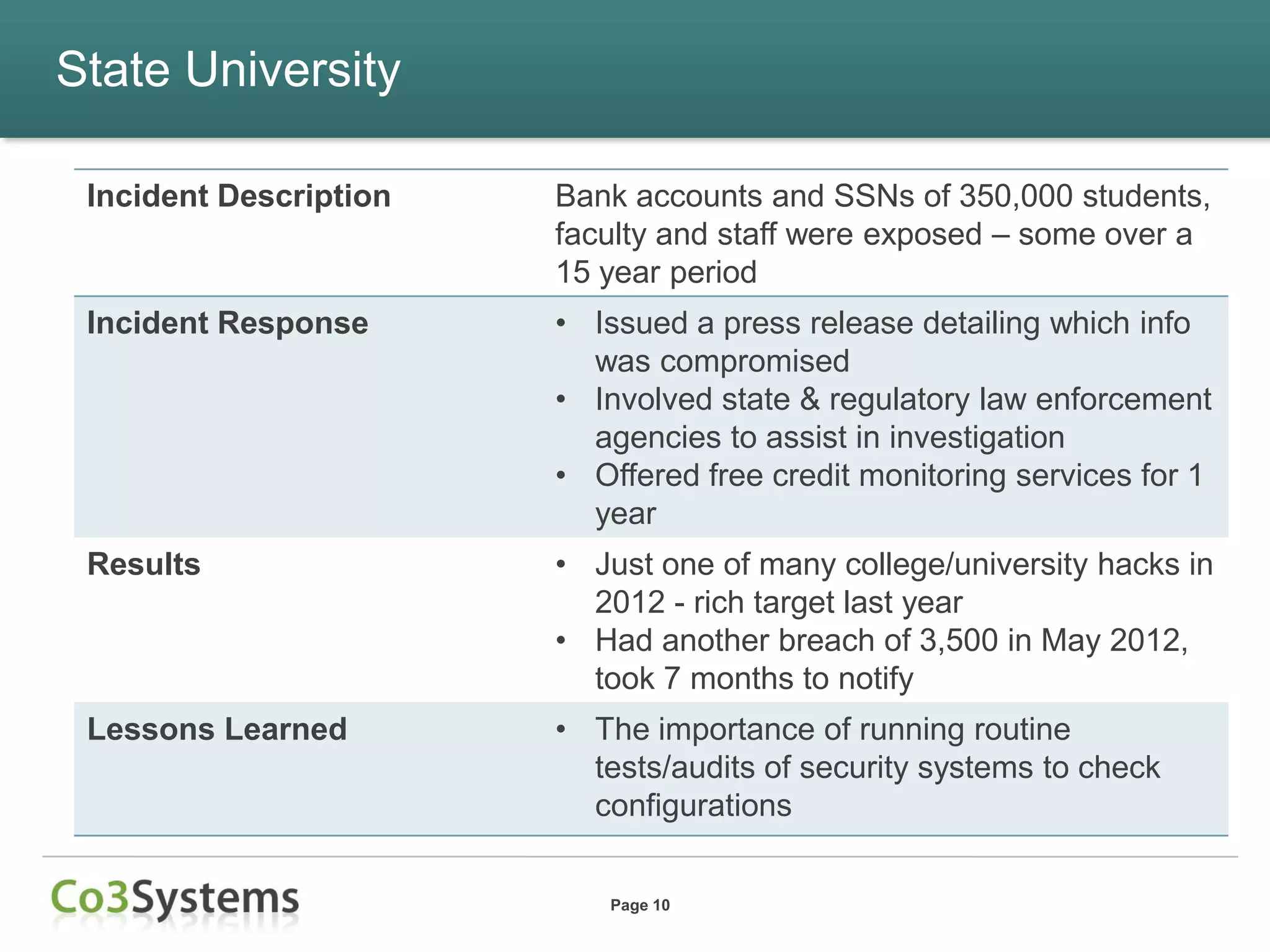
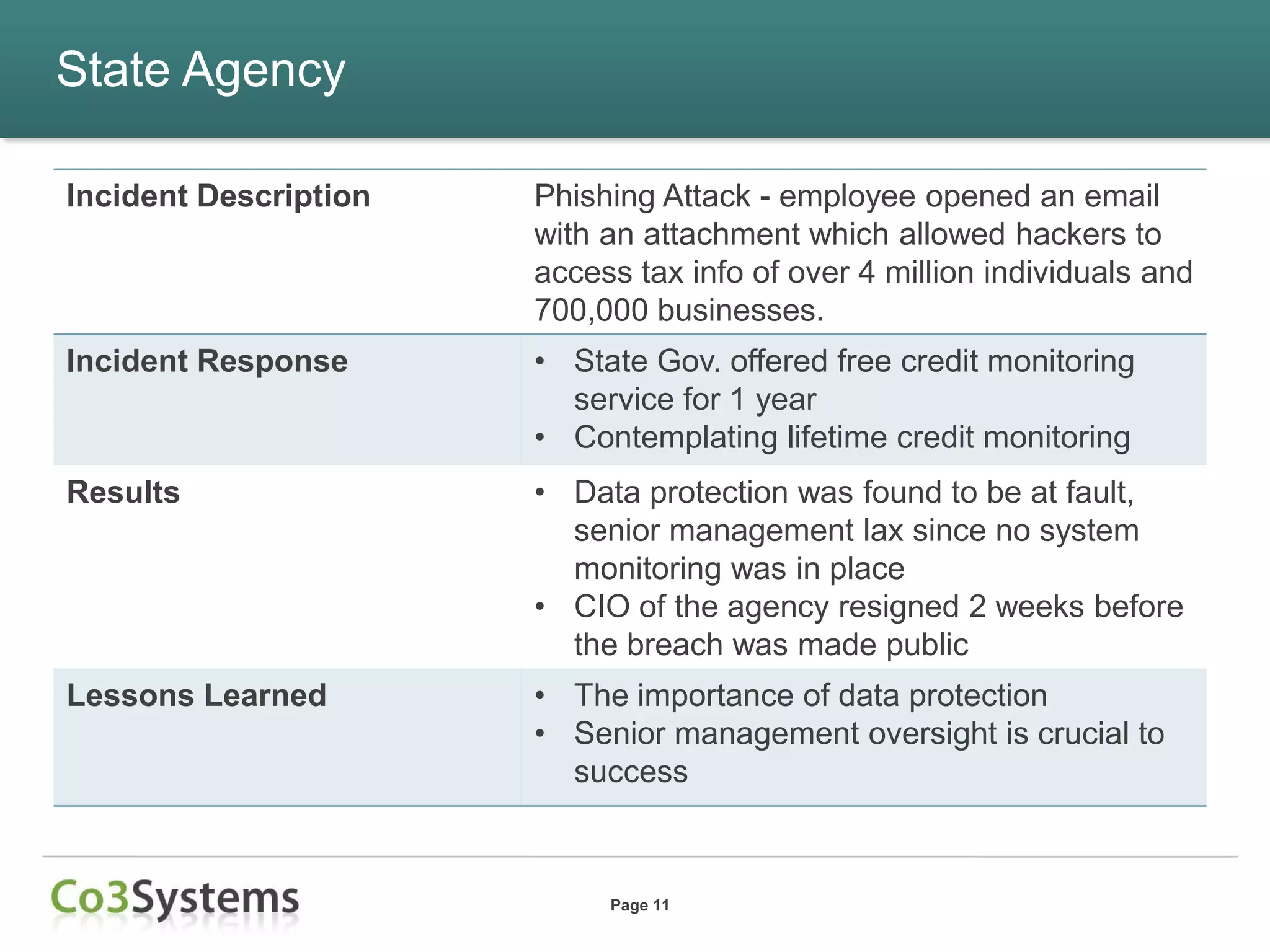
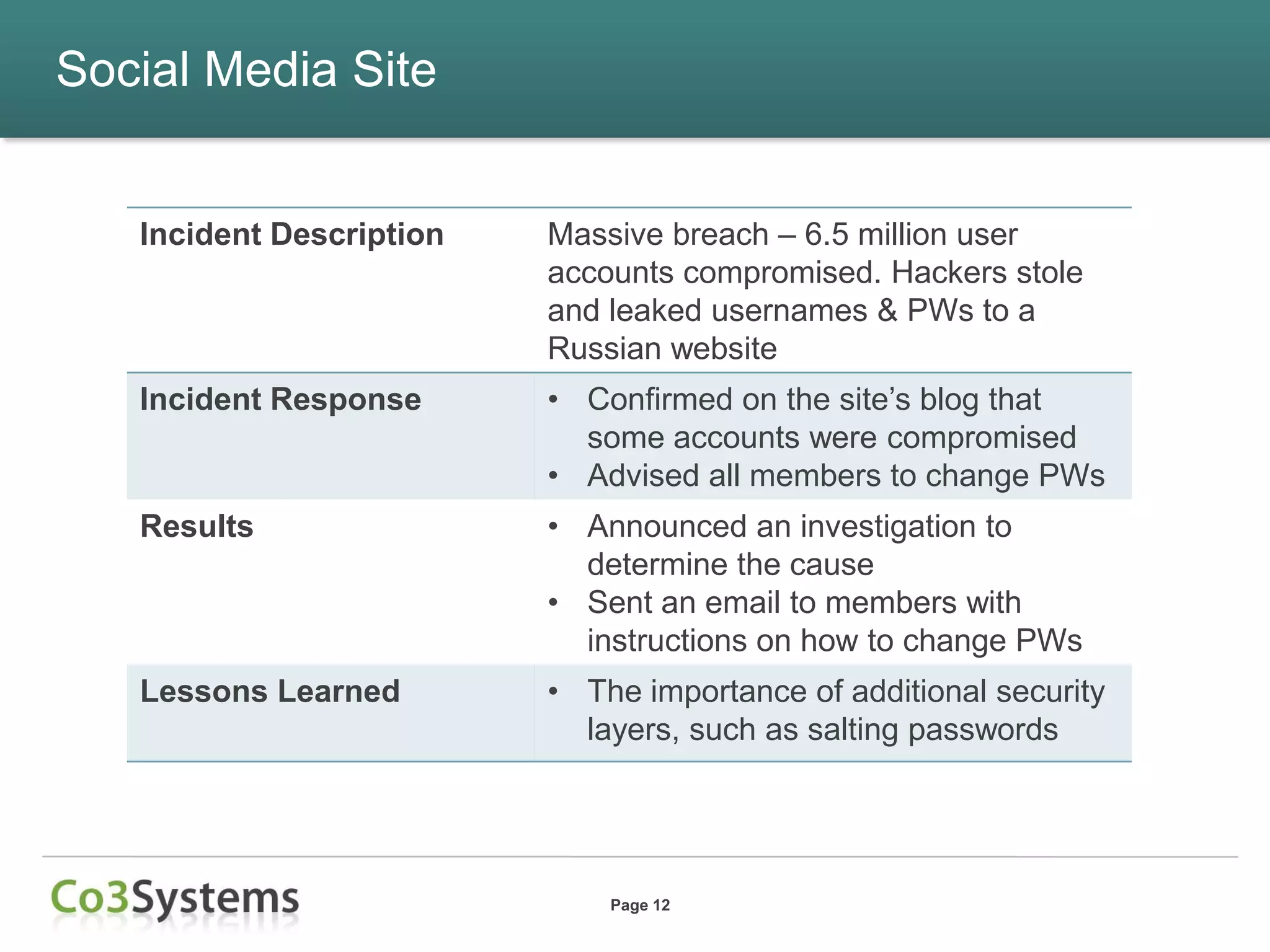
This document summarizes lessons learned from data breaches that occurred in 2012 and provides recommendations for improving security practices in 2013. It discusses several major breaches in 2012 that affected a payment processor, online retailer, hotel chain, university, and state agency. Common lessons identified include the importance of being prepared before a breach occurs, encrypting sensitive data, conducting security audits and testing, and maintaining compliance. The document recommends actions organizations can take before and after a breach to improve security and incident response, such as auditing encryption policies, training response teams, and establishing credit monitoring for affected individuals.