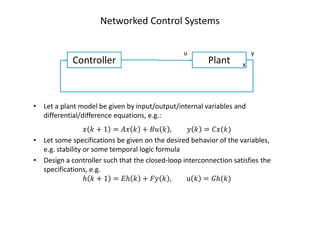
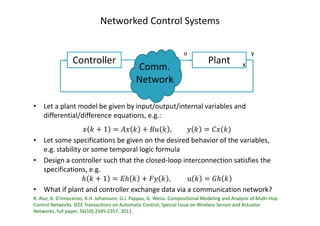
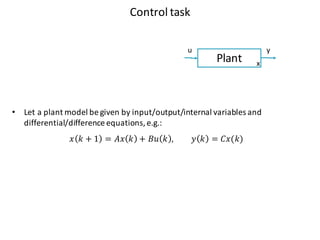
The document outlines the agenda for the 1st DISIM Workshop on Engineering Cyber-Physical Systems held at the University of L'Aquila, Italy, on January 26, 2016. It discusses various topics related to cyber-physical systems, including modeling, control tasks over wireless networking protocols, and the challenges of integrating computation with physical elements. Additionally, it emphasizes the importance of robust and secure design in wireless communication protocols for control applications.


![SEA Group
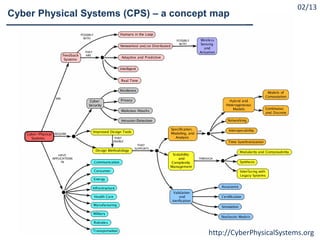
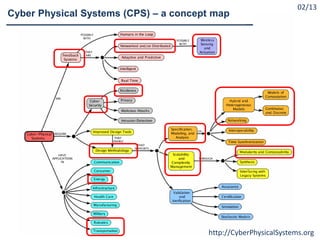
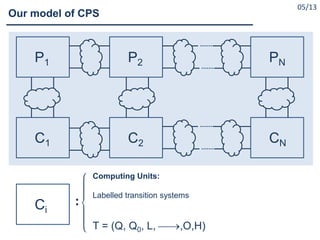
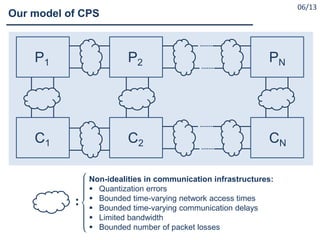
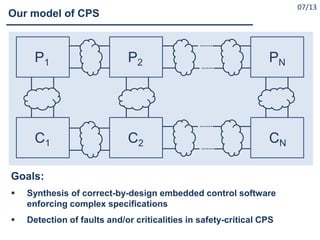
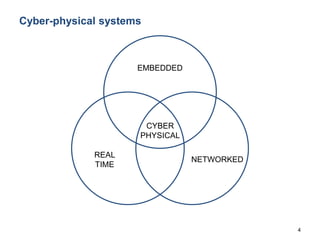
What are Cyber Physical Systems?
Cyber-Physical Systems (CPS) as ``engineered systems that are
built from, and depend upon, the seamless integration of
computational and physical components” [NSF12]
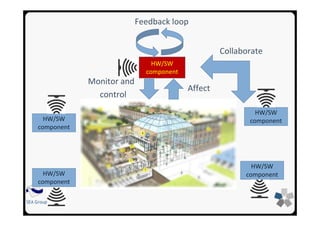
Cyber-Physical Systems (CPS) are integrations of computation
with physical processes. Embedded computers and networks
monitor and control the physical processes, usually with
feedback loops where physical processes affect computations
and vice versa [Lee08]
A cyber-physical system (CPS) is a system of collaborating
computational elements controlling physical entities
[Wikipedia].](https://image.slidesharecdn.com/cpsdisim26-160226105034/85/1ST-DISIM-WORKSHOP-ON-ENGINEERING-CYBER-PHYSICAL-SYSTEMS-4-320.jpg)


![SEA Group
Bibliography
[NSF12] National Science Foundation, Cyber-Physical
Systems Program Solicitation NSF 13-502, October
2012
[Lee08] Edward A. Lee. Cyber Physical Systems: Design
Challenges.Technical Report No. UCB/EECS-2008-8,
January 23, 2008](https://image.slidesharecdn.com/cpsdisim26-160226105034/85/1ST-DISIM-WORKSHOP-ON-ENGINEERING-CYBER-PHYSICAL-SYSTEMS-20-320.jpg)



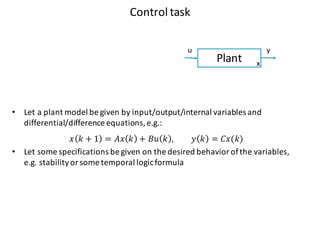
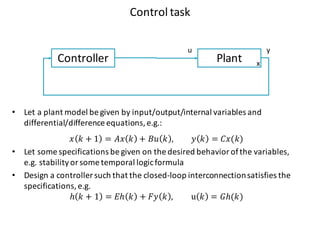
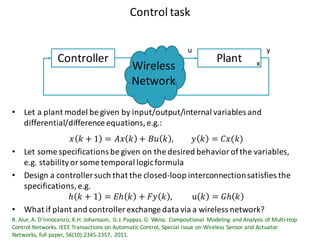
![Paradigm shift towards wireless control architectures
“Removing cables undoubtedly saves cost, but often the real cost gains lie in the radically
different design approach that wireless solutions permit. […] In order to fully benefit from
wireless technologies, a rethink of existing automation concepts and the complete design
and functionality of an application is required.” Jan-Erik Frey, R&D Manager ABB](https://image.slidesharecdn.com/cpsdisim26-160226105034/85/1ST-DISIM-WORKSHOP-ON-ENGINEERING-CYBER-PHYSICAL-SYSTEMS-30-320.jpg)
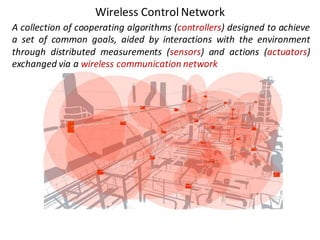



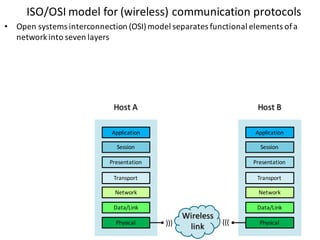
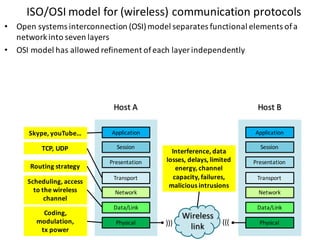
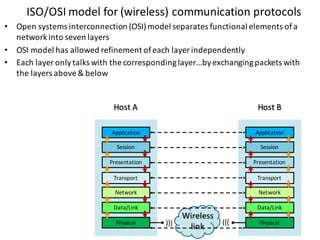
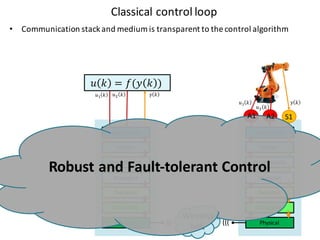
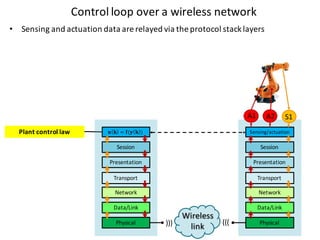
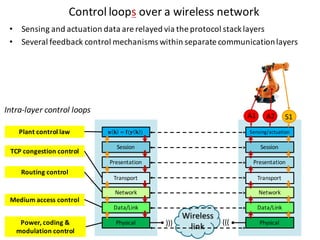
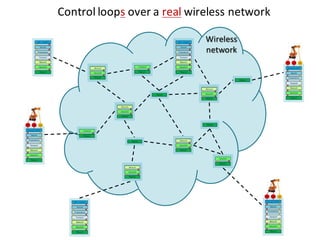

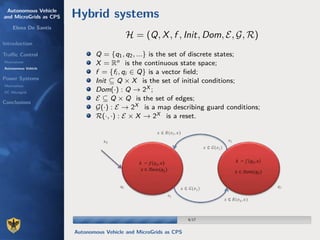
![Handle complexity of CPS via hybrid systems theory
J.Lygeros,S.Sastry,C.J.Tomlin. A game theoretic approach to controller design for hybrid systems. In Proc.
Of IEEE 88(7):949-970, July 2000
• Discrete Variables:
– Heater off: q0
– Heater on: q1
• Continuous Variables:
– Room temperature : x
• Transitions:
– Turn heater ON when the temperature is smaller than 70 degrees: x≤70.
– Turn heater OFF when the temperature is greater than 80 degrees: x≥80.
• Analysis and control of hybrid systems via formal methods:
– Discretize state space: Pola et al. […]
– Discretize trajectories: Yi Deng, A. D'Innocenzo, M. D. Di Benedetto, S. Di Gennaro, A. A. Julius.
Verification of Hybrid Automata Diagnosability with Measurement Uncertainty. IEEE
Transactions on Automatic Control](https://image.slidesharecdn.com/cpsdisim26-160226105034/85/1ST-DISIM-WORKSHOP-ON-ENGINEERING-CYBER-PHYSICAL-SYSTEMS-44-320.jpg)
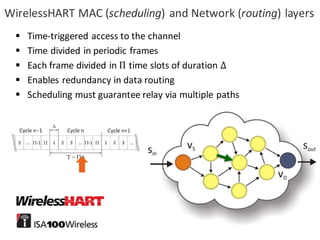
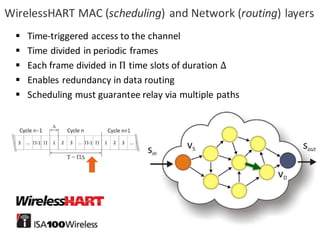
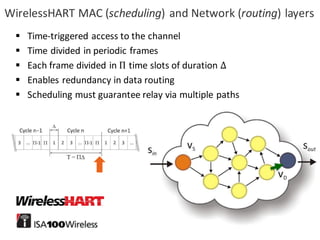
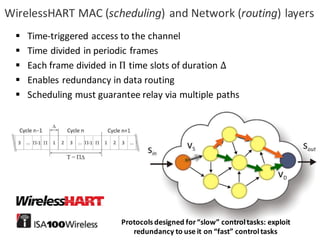
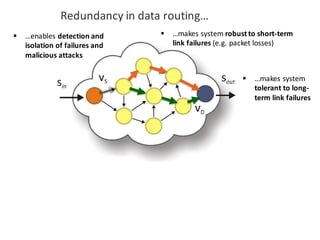
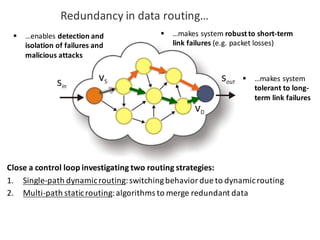
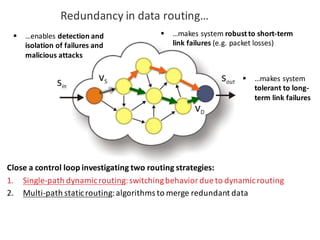
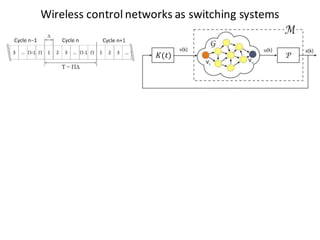
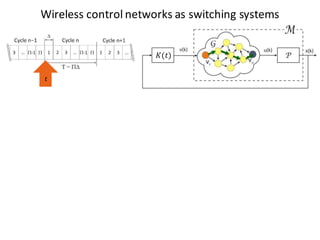
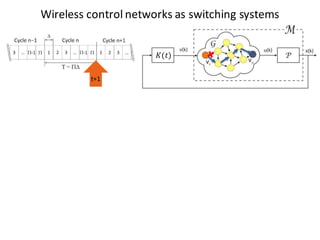
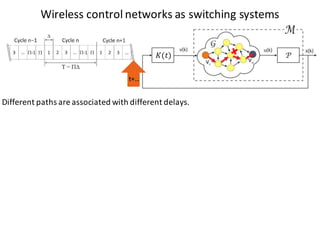
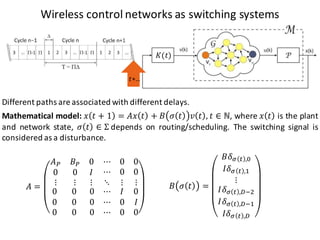
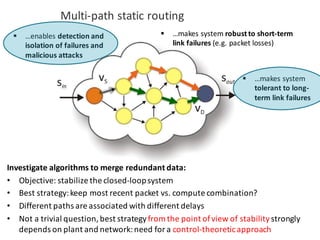
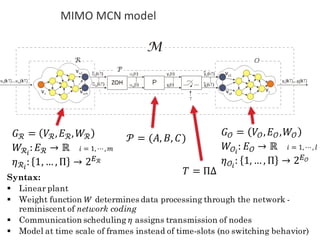
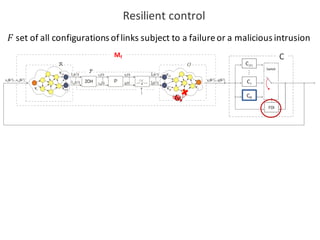
![BANK OF
LUENBERGER
OBSERVERS
𝑓l 𝑘𝑇 = [𝑓l5 𝑘𝑇 , 𝑓l6 𝑘𝑇 ,… , 𝑓l|o| 𝑘𝑇 ]
Observer-based diagonal FDI problem](https://image.slidesharecdn.com/cpsdisim26-160226105034/85/1ST-DISIM-WORKSHOP-ON-ENGINEERING-CYBER-PHYSICAL-SYSTEMS-79-320.jpg)
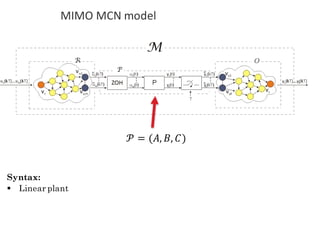
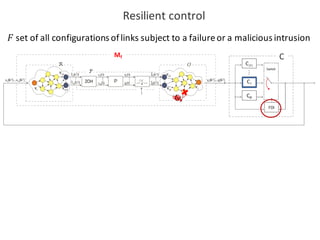
![BANK OF
LUENBERGER
OBSERVERS
𝑓l 𝑘𝑇 = [𝑓l5 𝑘𝑇 , 𝑓l6 𝑘𝑇 ,… , 𝑓l|o| 𝑘𝑇 ]
Observer-based diagonal FDI problem](https://image.slidesharecdn.com/cpsdisim26-160226105034/85/1ST-DISIM-WORKSHOP-ON-ENGINEERING-CYBER-PHYSICAL-SYSTEMS-80-320.jpg)
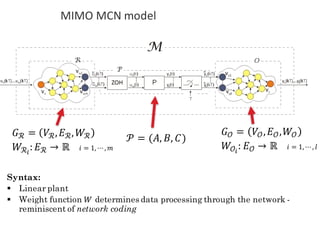
![BANK OF
LUENBERGER
OBSERVERS
𝑓l 𝑘𝑇 = [𝑓l5 𝑘𝑇 , 𝑓l6 𝑘𝑇 ,… , 𝑓l|o| 𝑘𝑇 ]
Observer-based diagonal FDI problem](https://image.slidesharecdn.com/cpsdisim26-160226105034/85/1ST-DISIM-WORKSHOP-ON-ENGINEERING-CYBER-PHYSICAL-SYSTEMS-81-320.jpg)
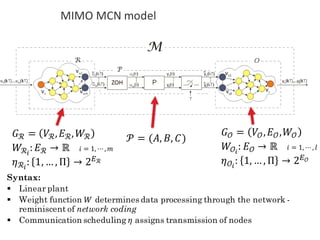
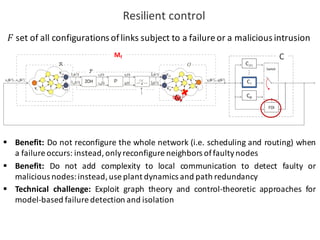
![BANK OF
LUENBERGER
OBSERVERS
𝑓l 𝑘𝑇 = [𝑓l5 𝑘𝑇 , 𝑓l6 𝑘𝑇 ,… , 𝑓l|o| 𝑘𝑇 ]
Observer-based diagonal FDI problem
Derive a common mathematical model for network topology (graph) and plant (LTI system):
exploit structured systems theory that translates LTI system into a graph](https://image.slidesharecdn.com/cpsdisim26-160226105034/85/1ST-DISIM-WORKSHOP-ON-ENGINEERING-CYBER-PHYSICAL-SYSTEMS-82-320.jpg)



![stable control systems
[Automatica-2008]
stable switched systems
[IEEE-TAC-2010]
stable time-delay systems
[SCL-2010]
stable time-varying
delay systems
[IJRNC-2014]
[IJC-2012]
unstable control
systems
[IEEE-TAC-2012]
efficient control
algorithms
[IEEE-TAC-2012]
approximate bisimulation
[Girard & Pappas,IEEE-TAC-2007]
incremental stability
[Angeli,IEEE-TAC-2002]
networked
control systems
[HSCC-2012]
[IEEE-CDC-2012]
[ERCIM News ‘97]
[IEEE-TAC-2016 ?]
Research at DEWS (IAB meeting 2014)
PWA systems
[IEEE-TAC-2014]
networks of control
systems
[IEEE-ACC-2014]
[IEEE-TAC-2016 ?]
decentralized symbolic
control & application to
vehicle platooning
[NecSys 2013]
stable control systems
with disturbances
[SIAM-2009]
09/13](https://image.slidesharecdn.com/cpsdisim26-160226105034/85/1ST-DISIM-WORKSHOP-ON-ENGINEERING-CYBER-PHYSICAL-SYSTEMS-95-320.jpg)
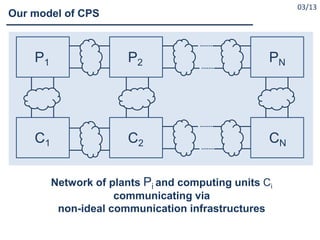
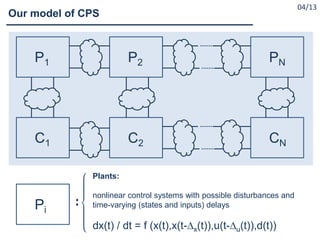
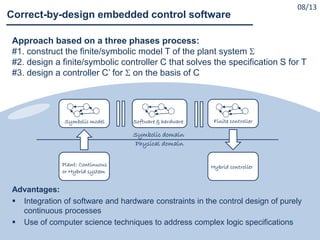
![#1. Construct the symbolic model T of the plant system
Done:
1.1 CPS with one plant and one computing unit communicating via
nonideal communication infrastructure
[Borri et al; HSCC-2012], [Liu et al.; HSCC-2014],
[Zamani et al; IEEE-CDC-2015],]
1.2 CPS with multiple plants and computing units communicating via
ideal communication infrastructure
[Tazaki et al.; HSCC-2008], [Pola et al.; IEEE-TAC-2016 ?]
To be done: 1.1 + 1.2 = ?
Incremental stability notions for CPS
Symbolic models for CPS with multiple plants and computing units
communicating via nonideal communication infrastructure
Correct-by-design embedded control software
10/13](https://image.slidesharecdn.com/cpsdisim26-160226105034/85/1ST-DISIM-WORKSHOP-ON-ENGINEERING-CYBER-PHYSICAL-SYSTEMS-96-320.jpg)
![#2. Design a symbolic controller C that solves the specification S for T
Done: [Borri et al; HSCC-2012]
Model: CPS with one plant and one computing unit communicating via
nonideal communication infrastructure
Specifications: non-deterministic transition systems
To be done:
Extension to symbolic control design with specifications in terms of
Linear Temporal Logic
Extension to symbolic control design for CPS with multiple plants and
computing units communicating via nonideal communication infrastructure
Correct-by-design embedded control software
11/13](https://image.slidesharecdn.com/cpsdisim26-160226105034/85/1ST-DISIM-WORKSHOP-ON-ENGINEERING-CYBER-PHYSICAL-SYSTEMS-97-320.jpg)
![Model: Networks of Finite State Machines
Assumptions:
no continuous and/or hybrid dynamics
ideal communication infrastructure
Done: [Pola et al.; Automatica-2016 ?]
Decentralized observers detecting instantaneously faults/criticalities in CPS
Model reduction via bisimulation theory
To be done:
Extension to CPS with continuous and/or hybrid dynamics and with
nonideal communication infrastructure
Extension to opacity [Mazare et., WITS 2004], i.e. to keep secret a set of
states of an FSM with respect to all possible measurements on the system
Detection of Faults and/or Criticalities in CPS
12/13](https://image.slidesharecdn.com/cpsdisim26-160226105034/85/1ST-DISIM-WORKSHOP-ON-ENGINEERING-CYBER-PHYSICAL-SYSTEMS-98-320.jpg)








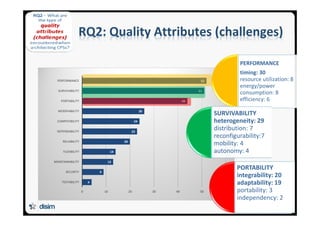
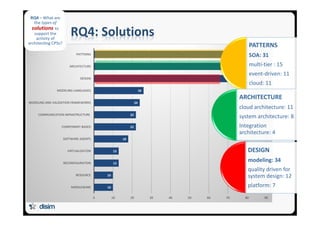
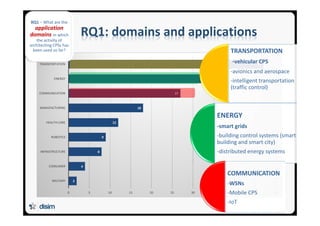
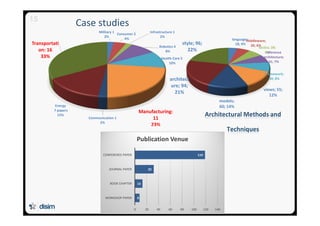

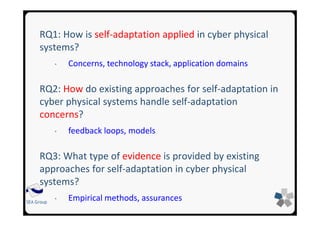
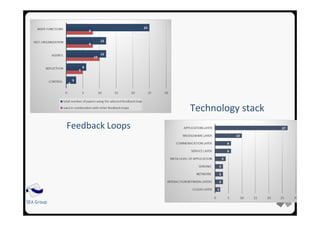
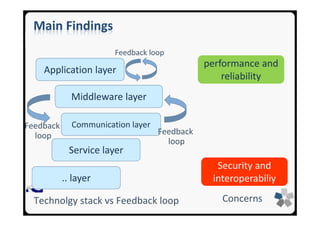


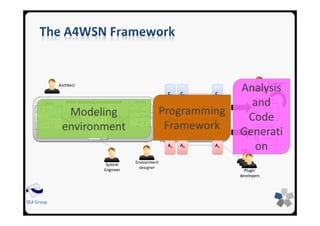








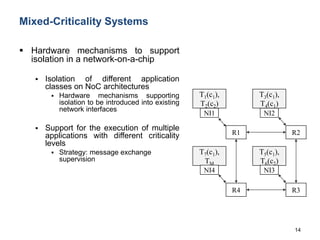

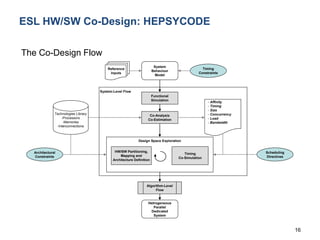



![26
M3 Main Research Projects
EMC2 (Artemis-JU AIPP 2013-621429)
Embedded Multi-Core systems for Mixed Criticality applications in dynamic and
changeable real-time environments
CASPER (H2020-MSCA-RISE-2014)
User-centric MW Architecture for Advanced Service Provisioning in Future
Networks
SAFECOP (ECSEL-JU RIA-2015) [in negotiation]
Safe Cooperating Cyber-Physical Systems using Wireless Communication](https://image.slidesharecdn.com/cpsdisim26-160226105034/85/1ST-DISIM-WORKSHOP-ON-ENGINEERING-CYBER-PHYSICAL-SYSTEMS-166-320.jpg)














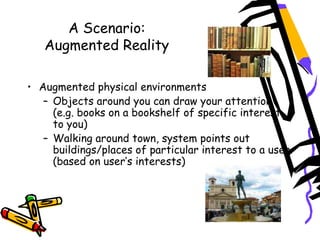



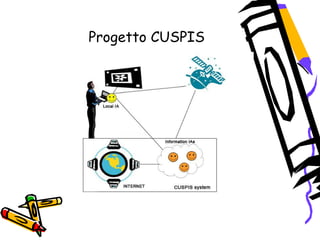








![Che cos'è il contesto?
“L’informazione di contesto può in generale essere
definita come un insieme ordinato multilivello di
informazioni dichiarative riferite agli eventi che si
verificano in un dato luogo e che coinvolgono
oggetti animati ed inanimati” [J. Crowley]
Context-awareness](https://image.slidesharecdn.com/cpsdisim26-160226105034/85/1ST-DISIM-WORKSHOP-ON-ENGINEERING-CYBER-PHYSICAL-SYSTEMS-205-320.jpg)