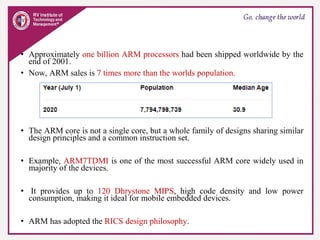
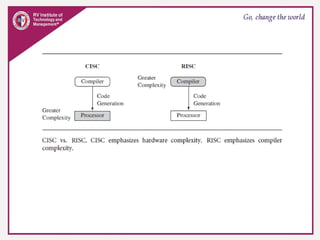
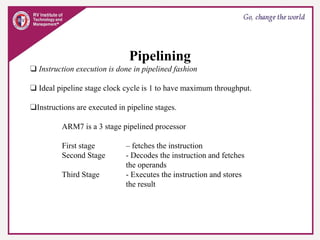
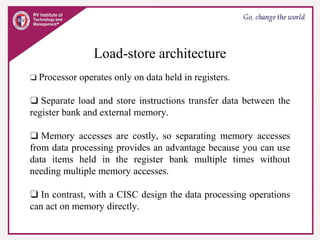
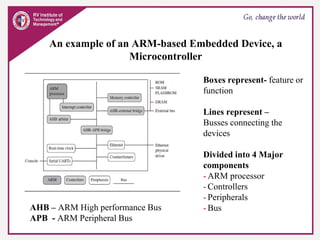
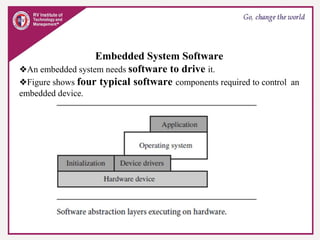
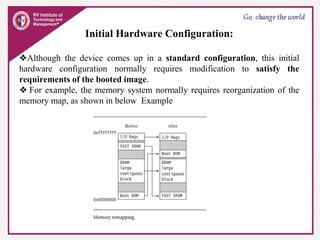
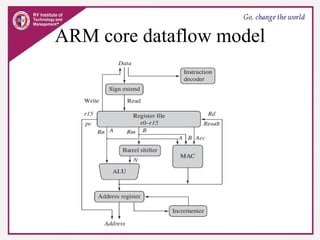
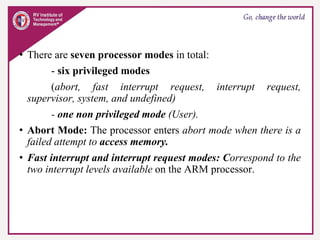
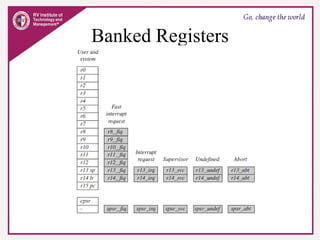
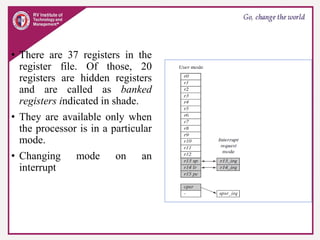
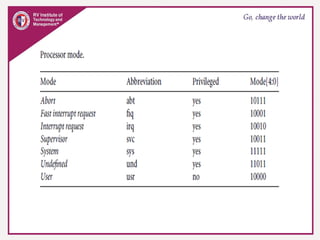
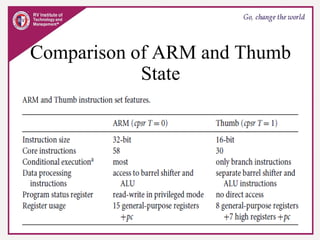
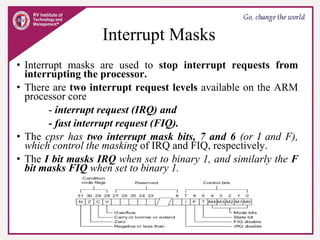
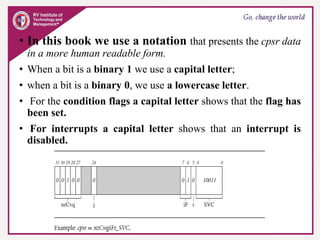
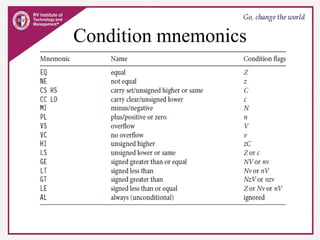
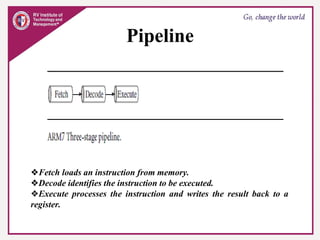
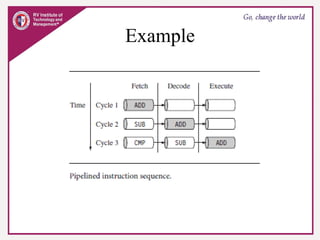
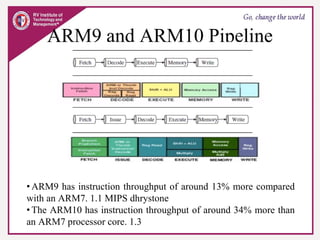
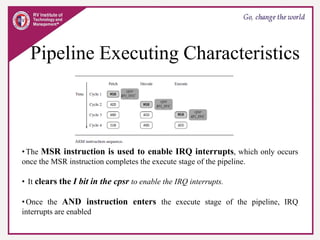
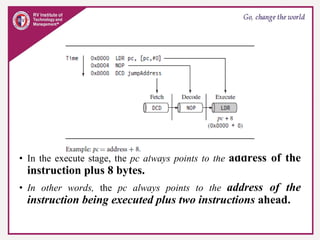
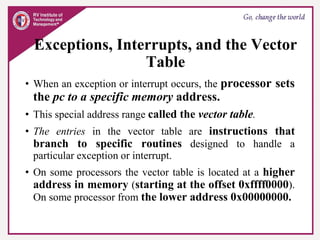
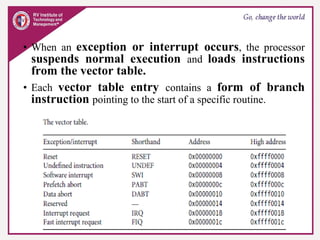
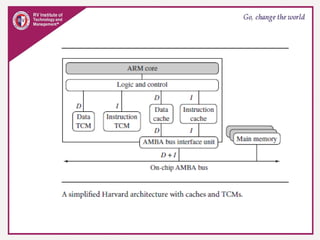
The document provides an overview of ARM microprocessors and embedded systems. It discusses ARM architecture basics, including that ARM is a leading provider of RISC microprocessors used widely in embedded systems. It describes typical components of an ARM-based embedded device including the ARM processor, controllers, peripherals, and bus. It also covers memory, software components like boot code and operating systems, and common applications of ARM processors.