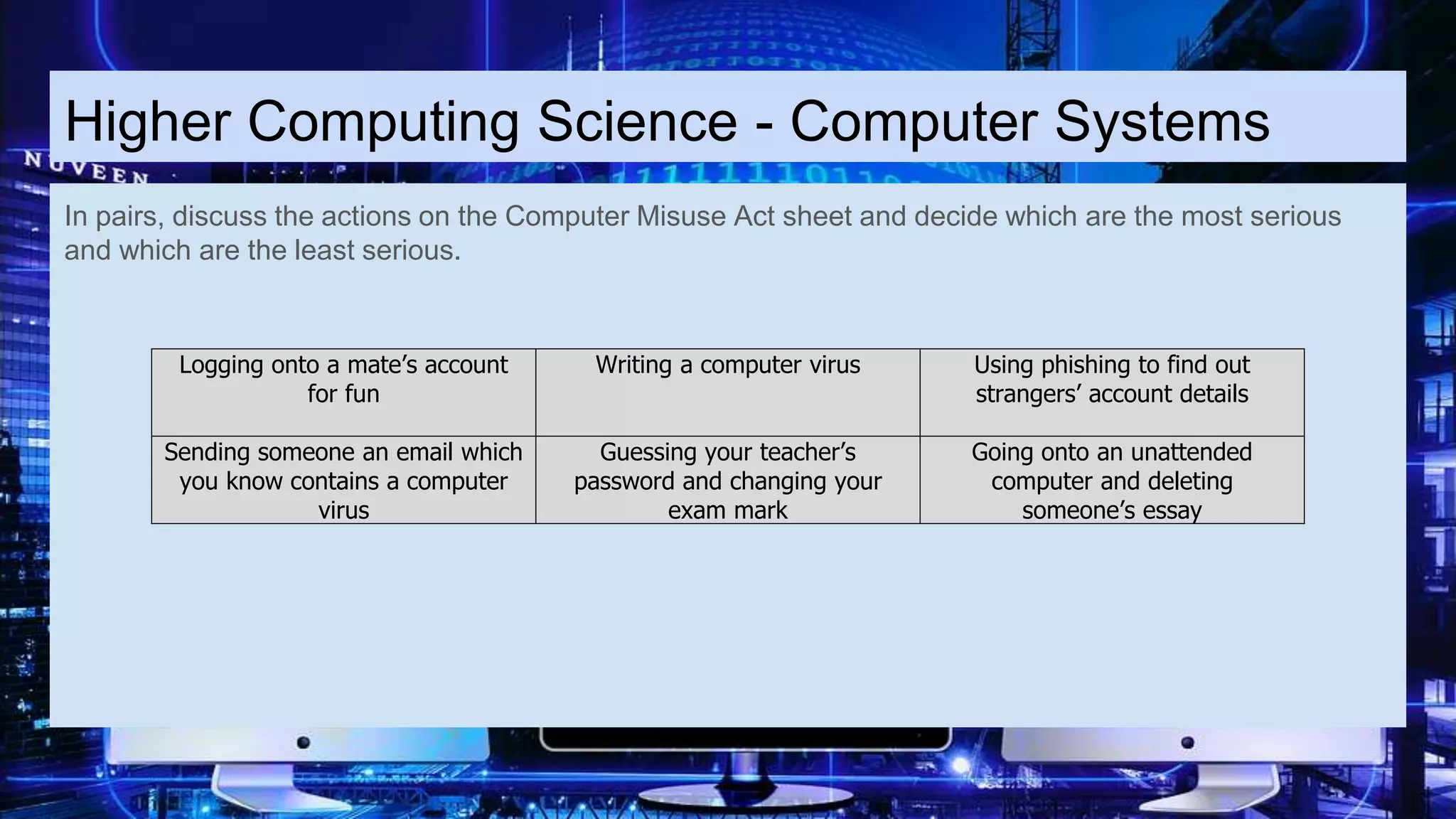
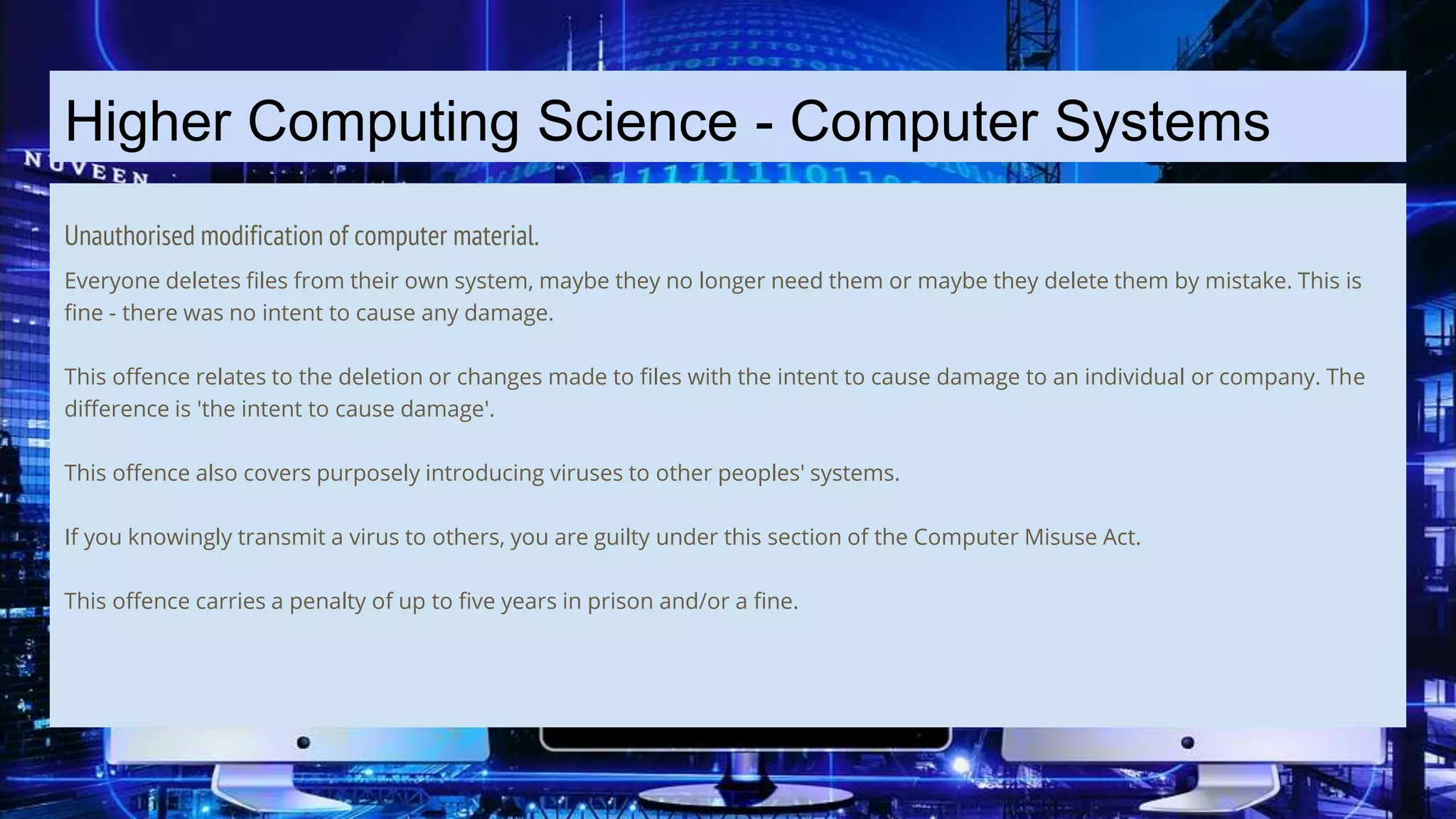
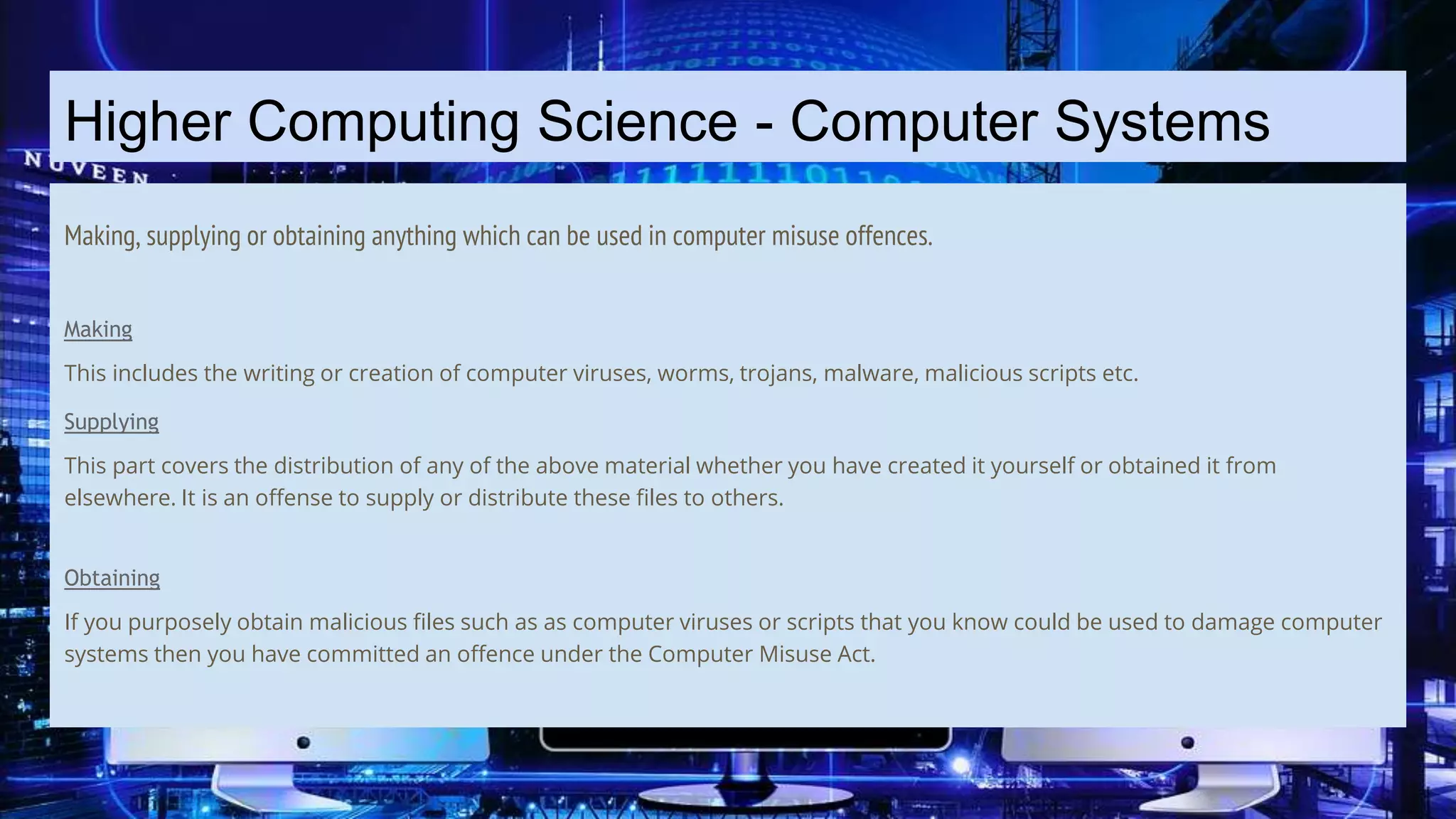
The document discusses the Computer Misuse Act 1990 and its recognition of computer-related offenses. It describes three levels of offenses under the Act: 1) Unauthorized access to computer material, 2) Unauthorized access with intent to commit a crime, and 3) Unauthorized modification of computer material. It also discusses the offense of making, supplying, or obtaining anything used to carry out computer misuse. The document provides details on the types of actions that fall under each offense and the potential legal penalties. It aims to educate on the legality of different types of unauthorized computer access and modification.