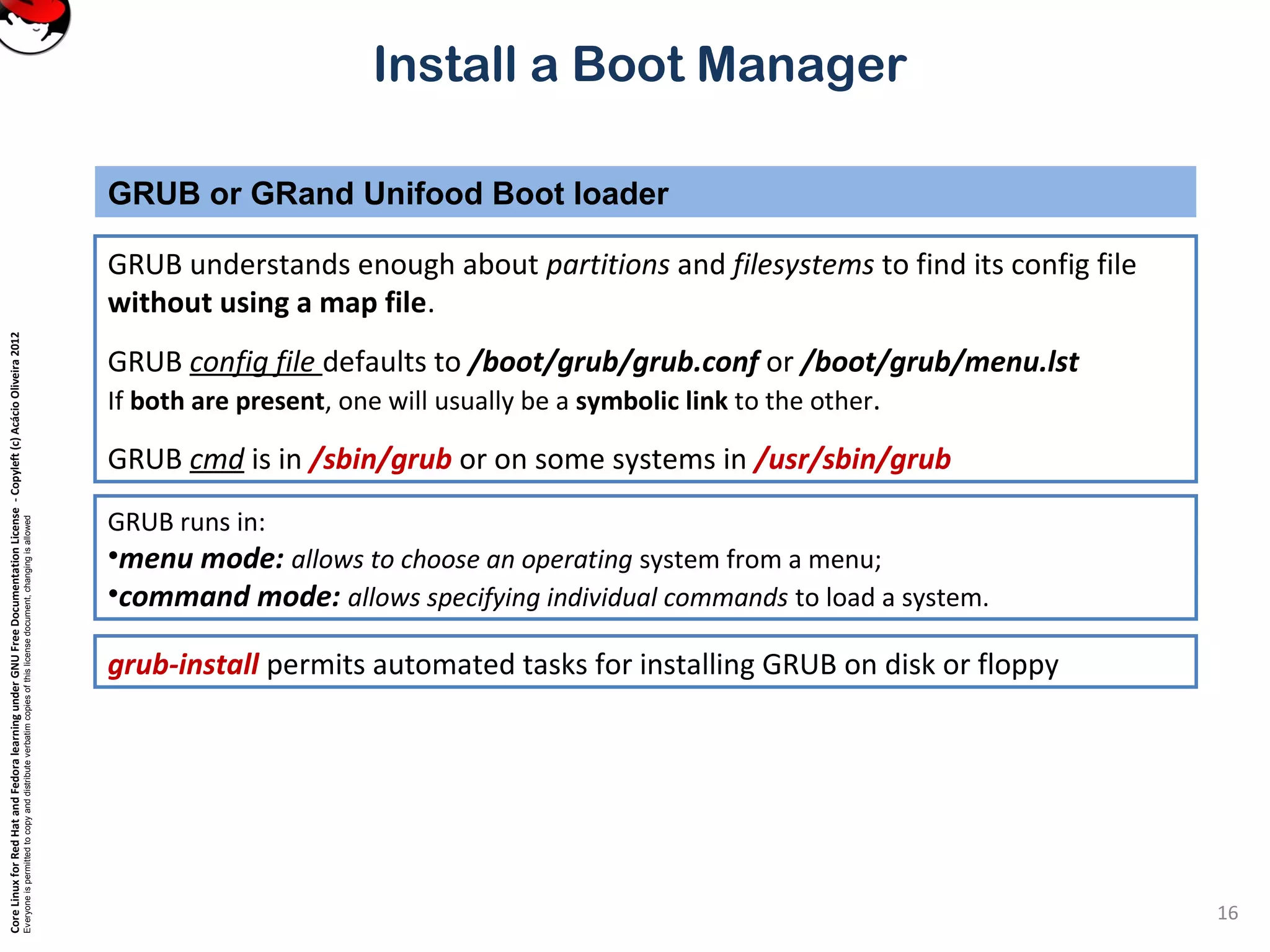
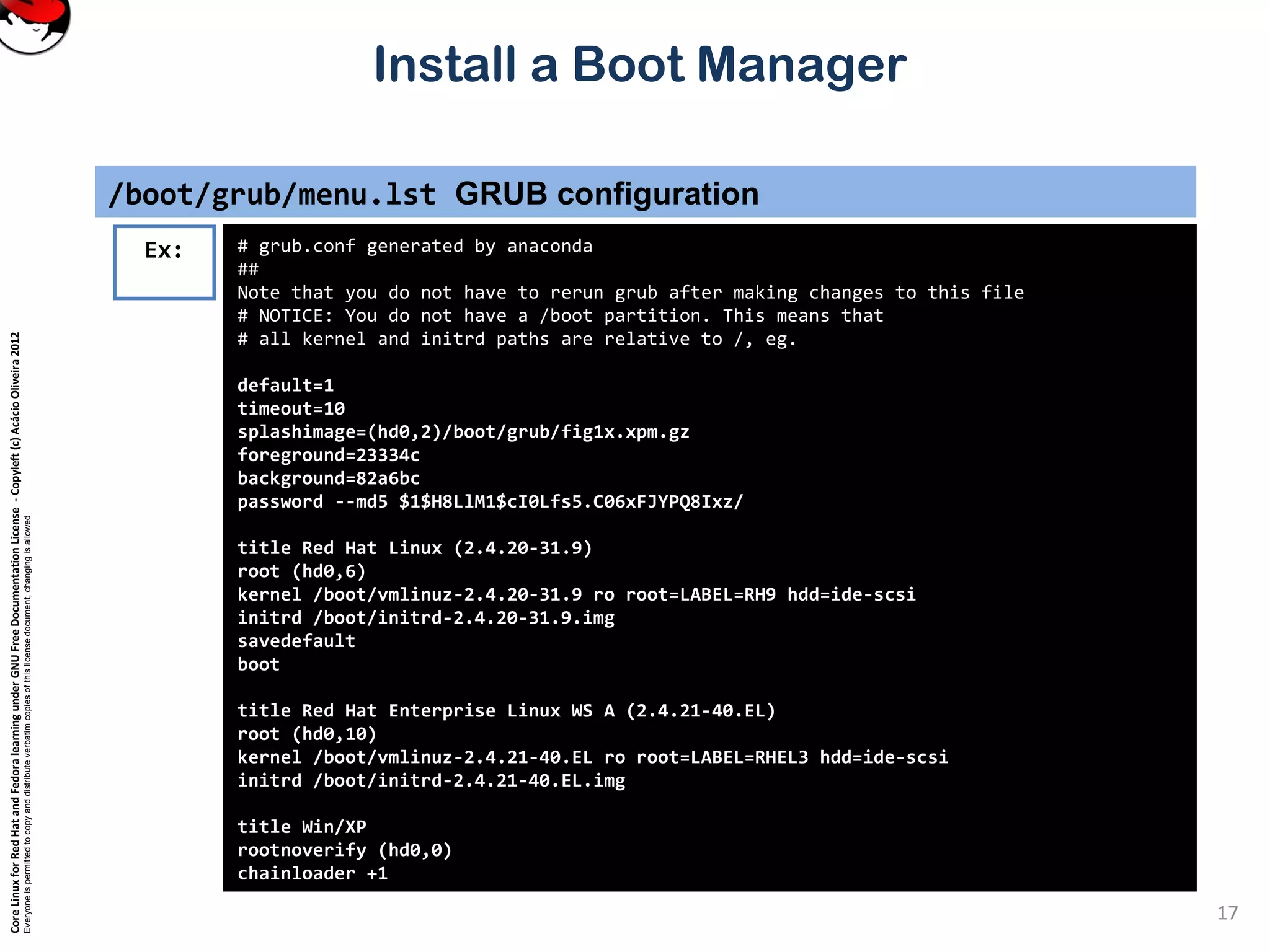
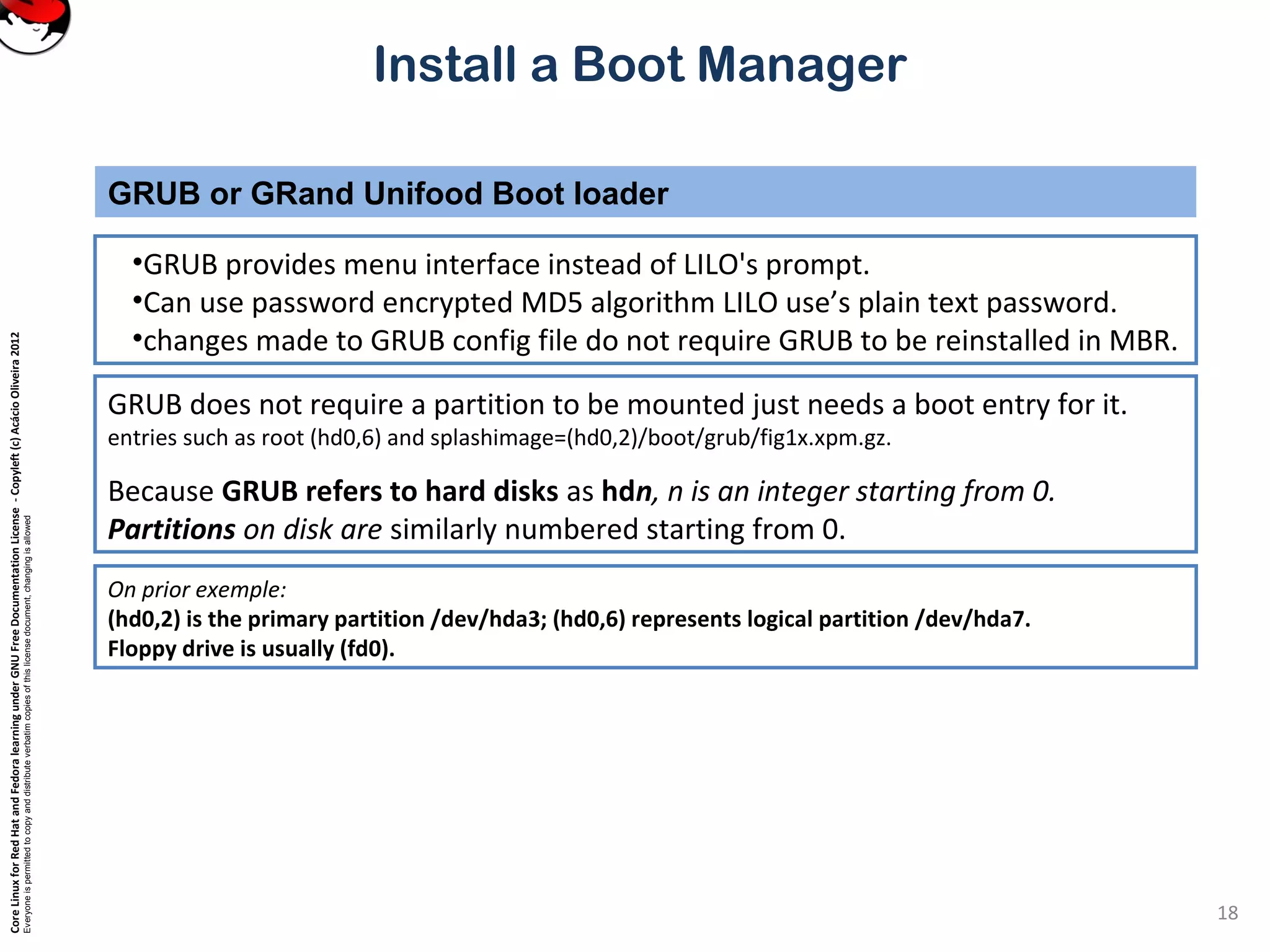
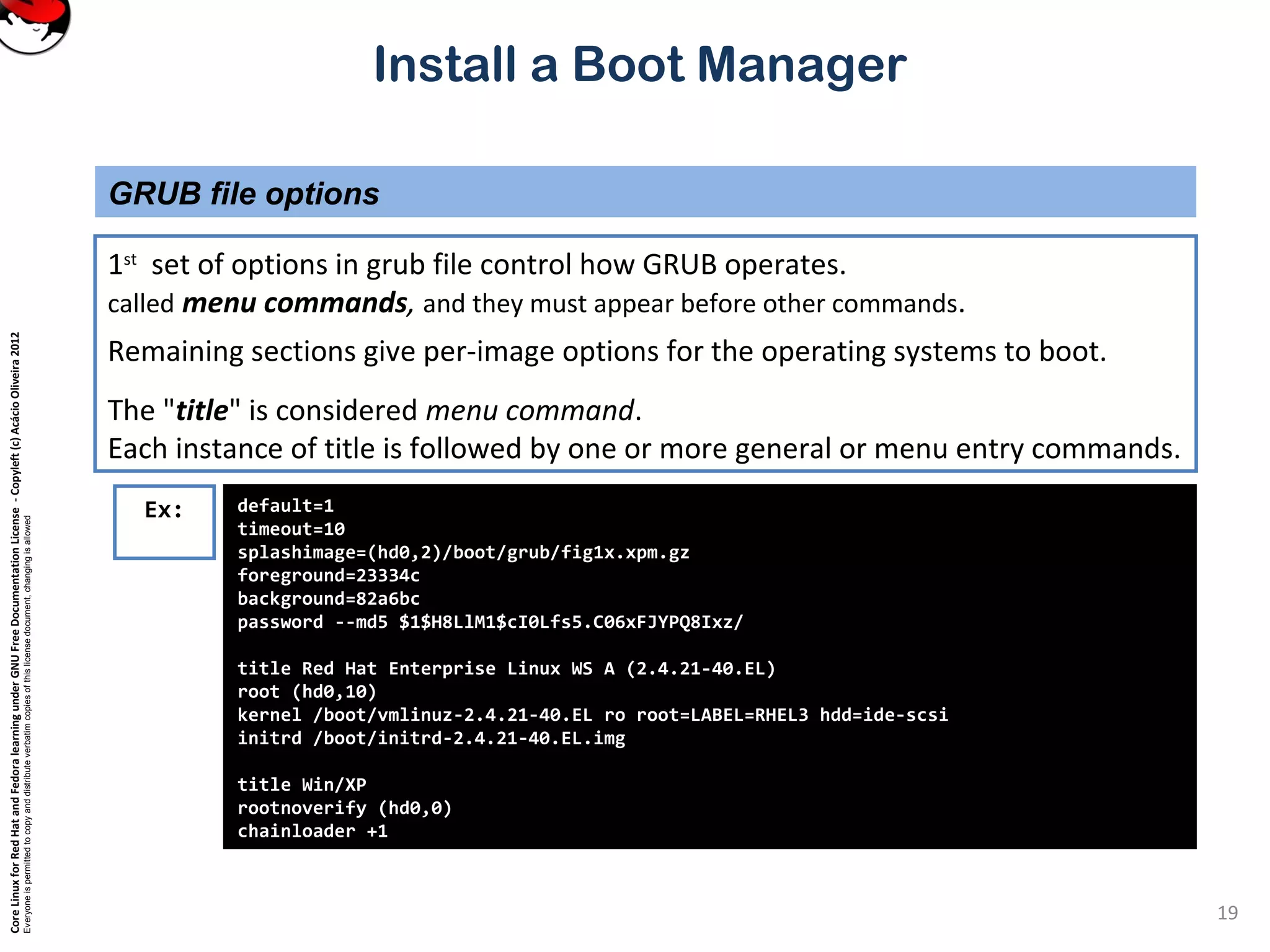
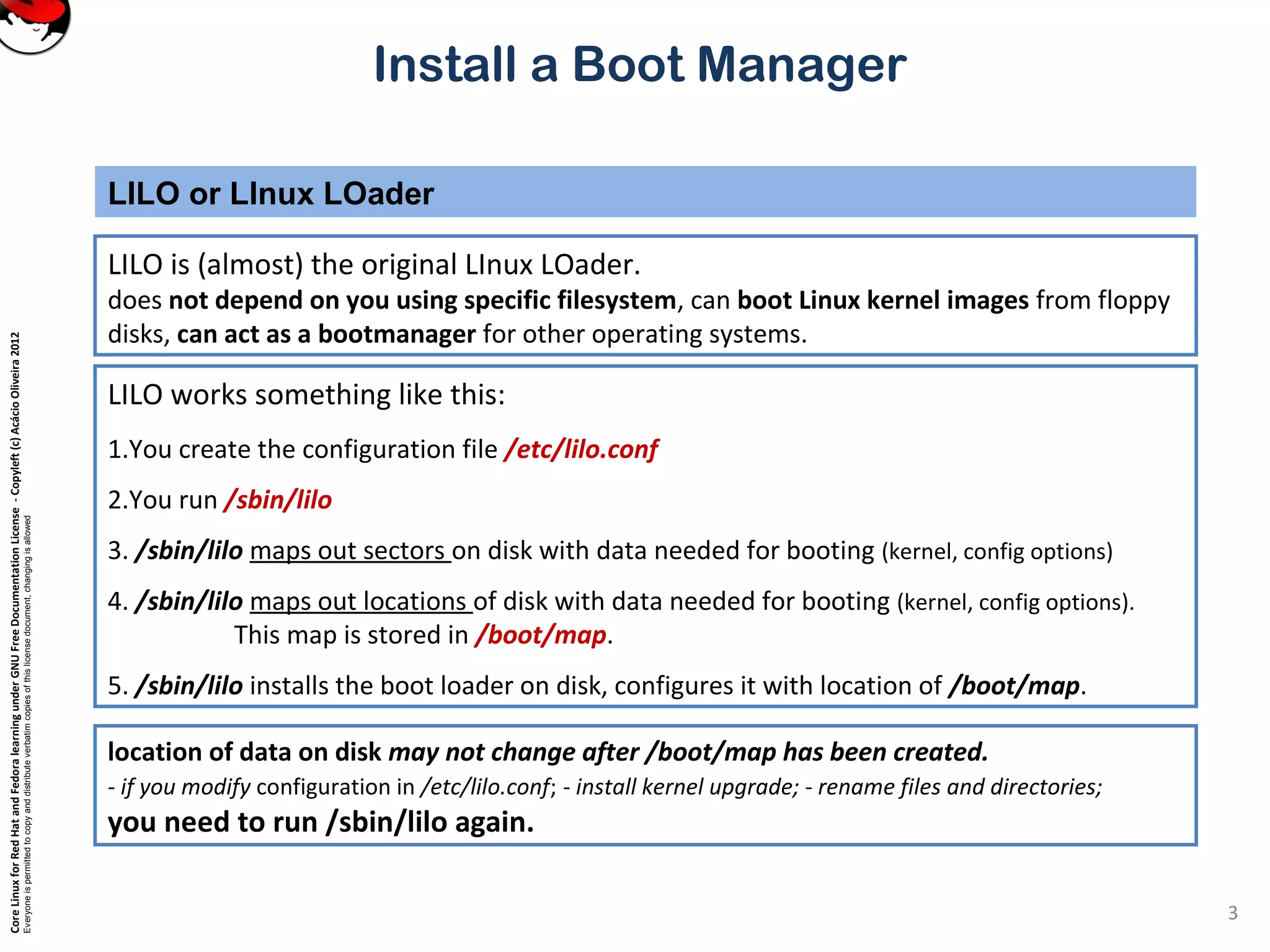
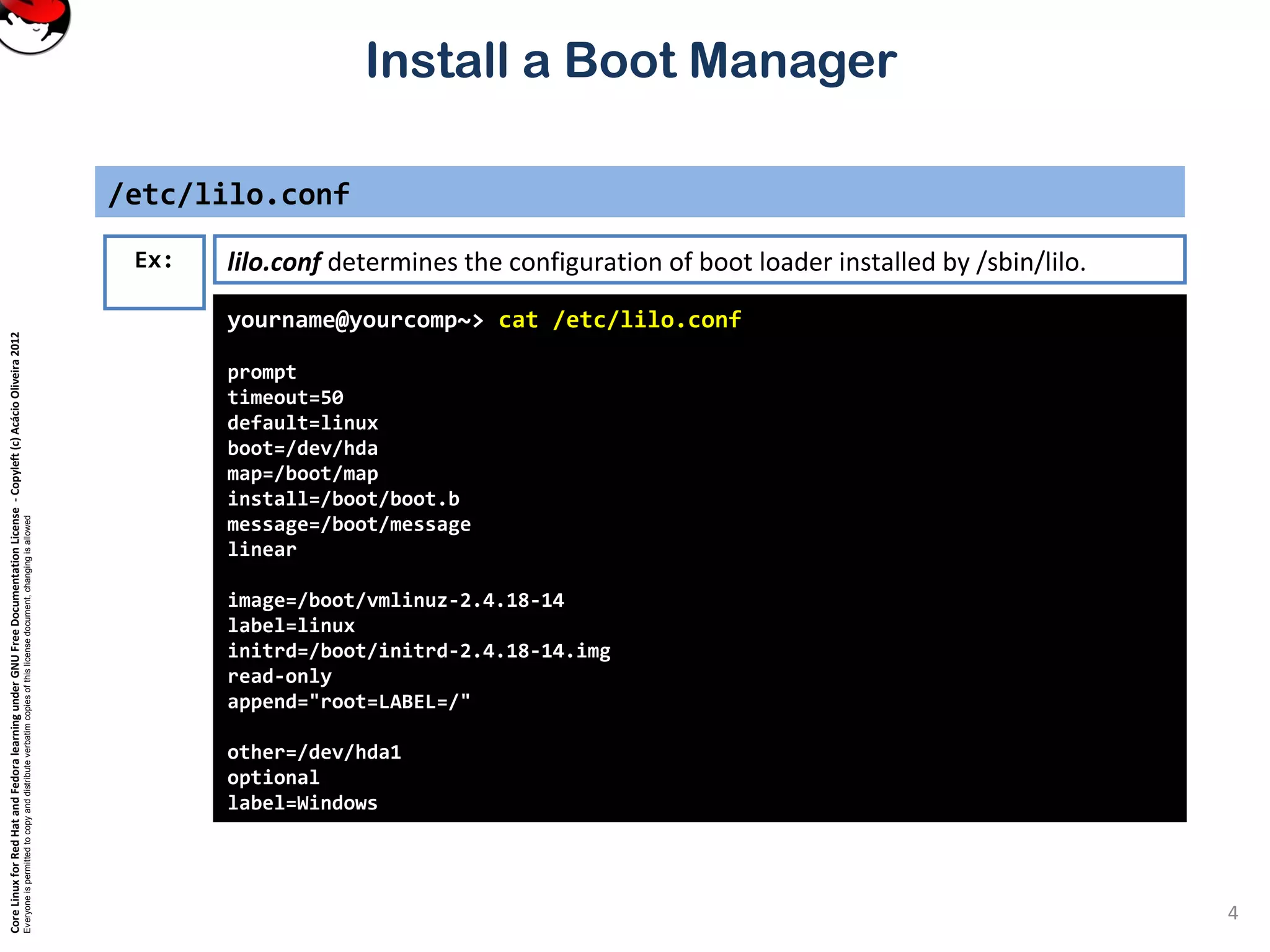
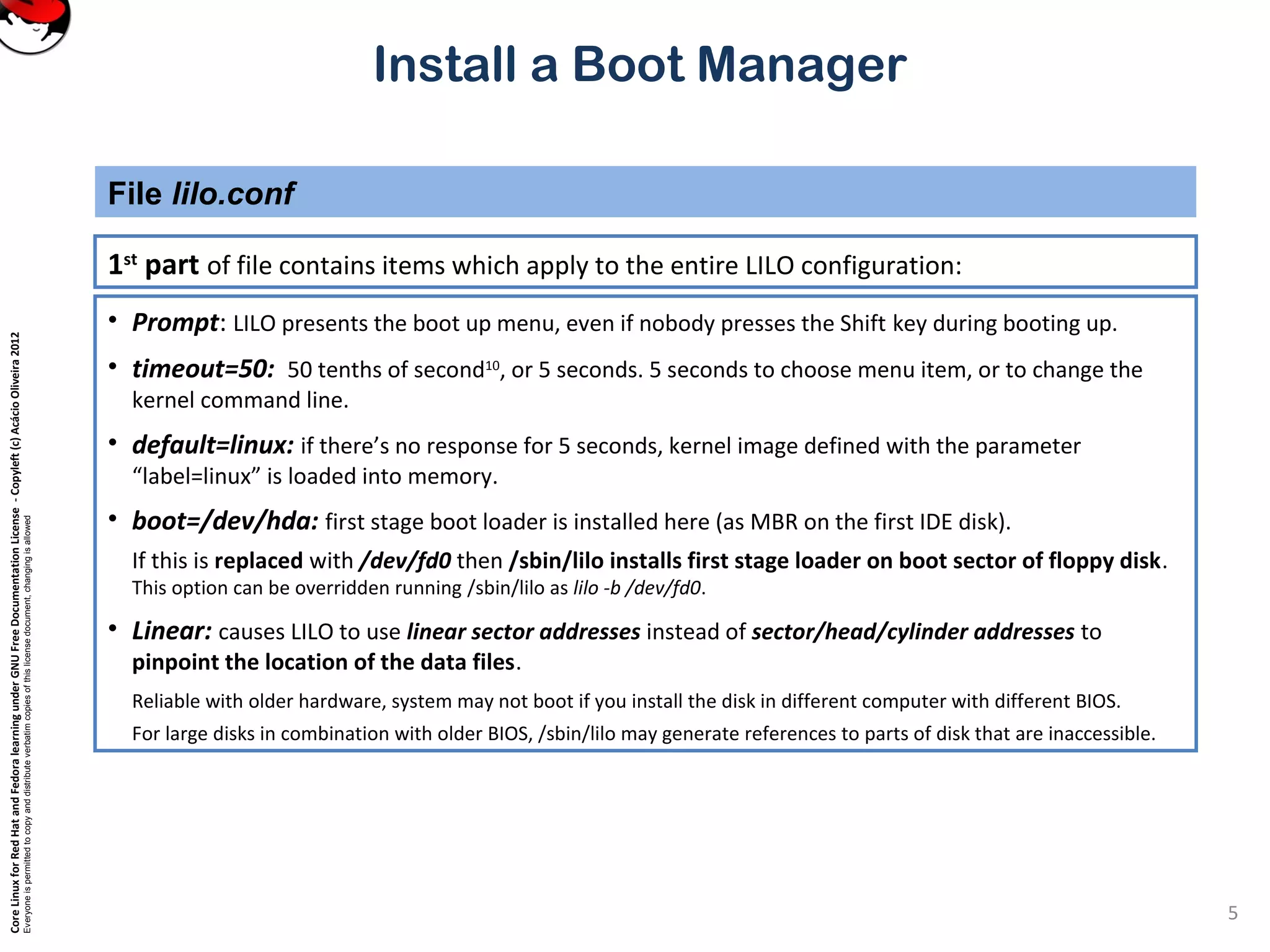
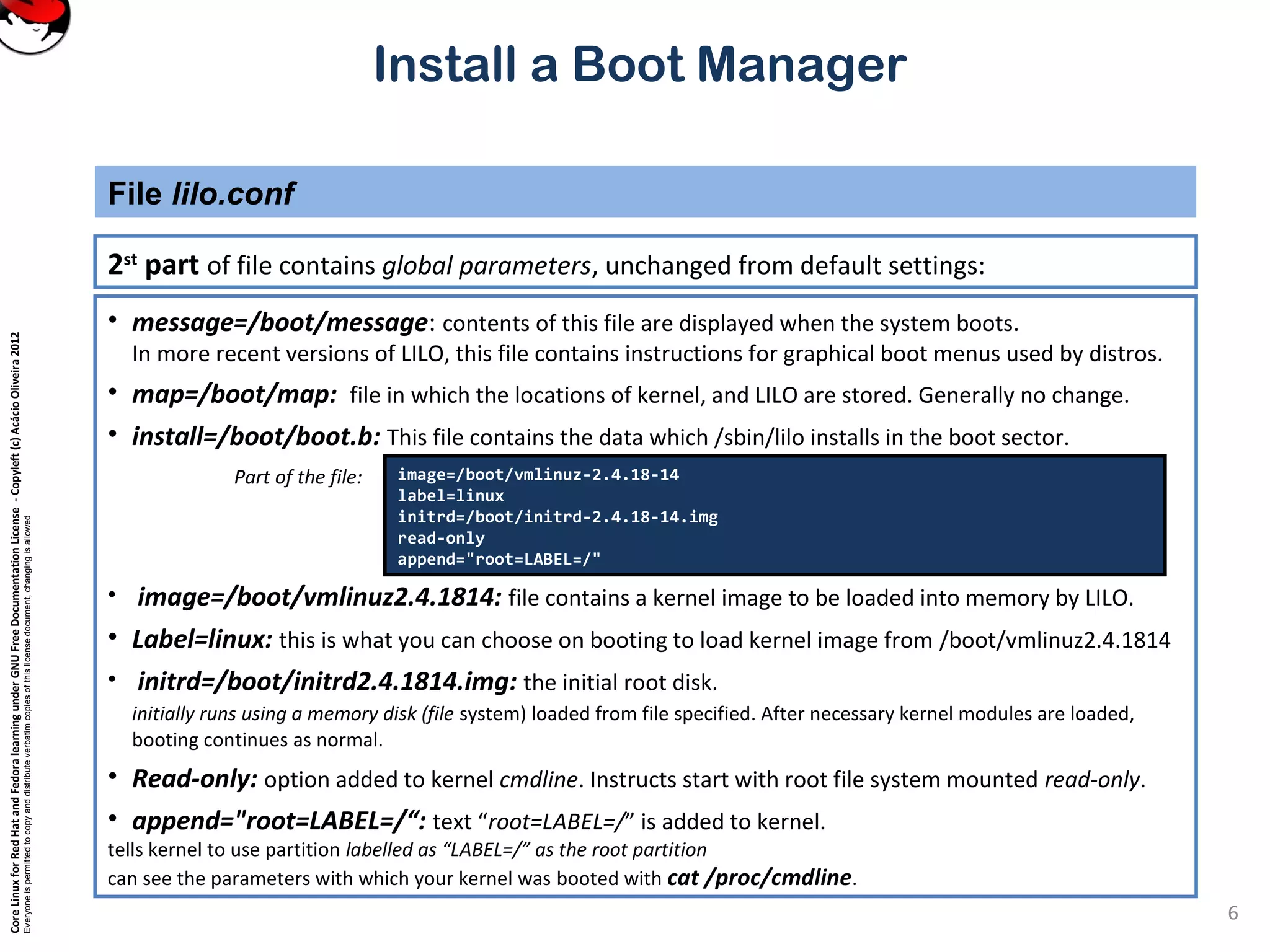
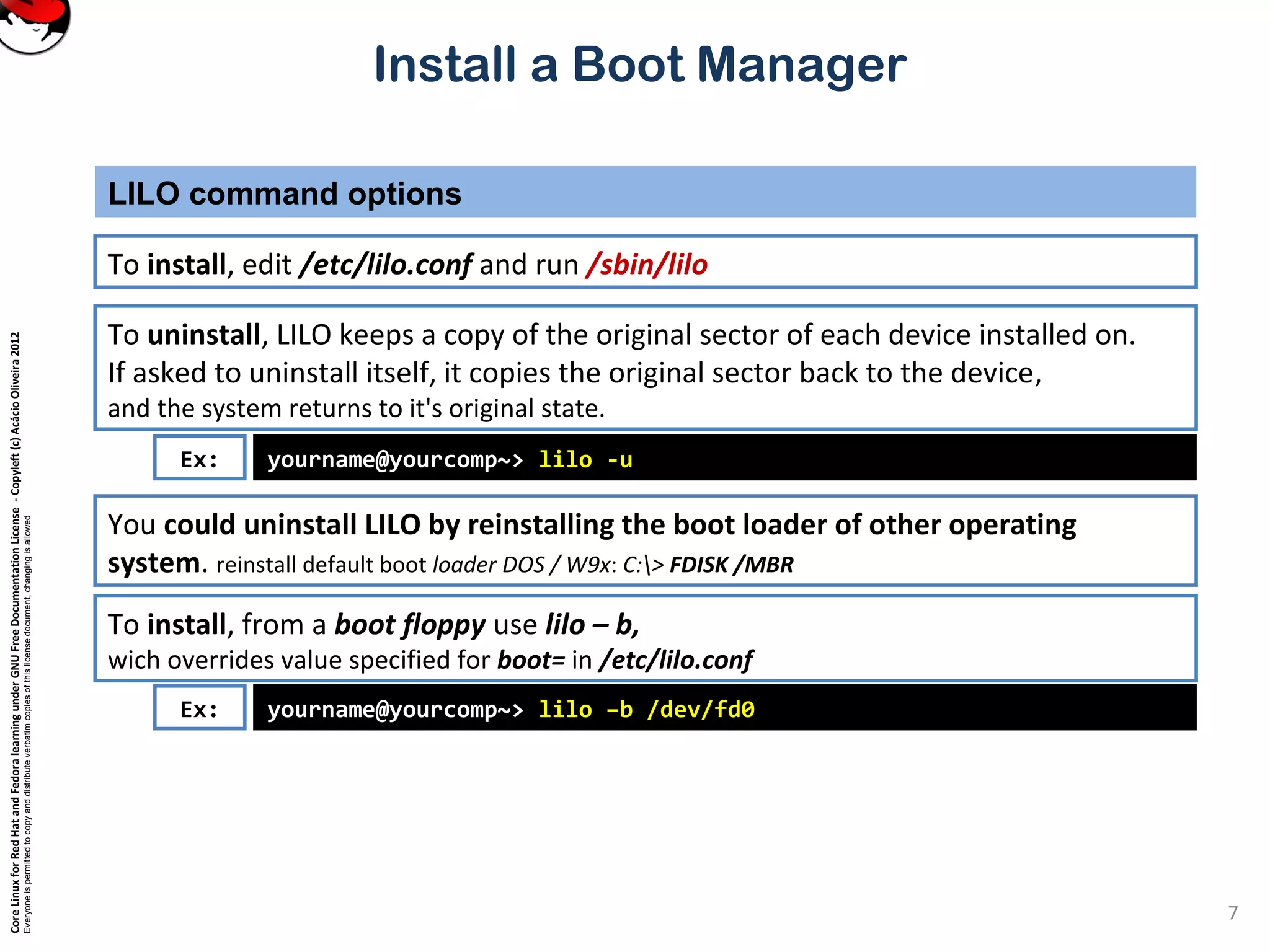
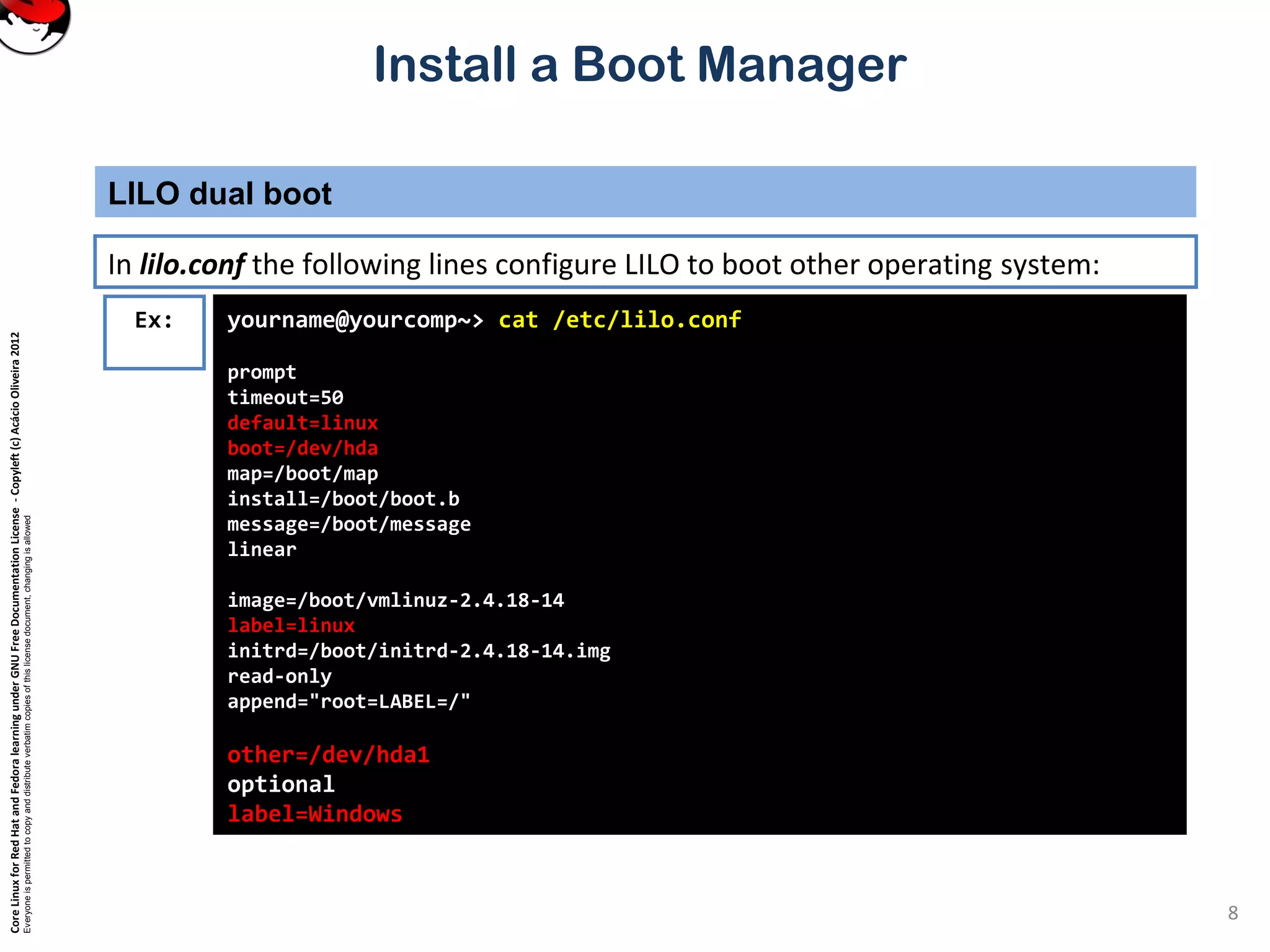
This document provides instructions on installing a boot manager in Linux. It discusses both LILO and GRUB as options. It describes how LILO works, including creating the /etc/lilo.conf configuration file, running /sbin/lilo to install it, and some common configuration options in lilo.conf like boot devices, timeouts, default boots, and dual booting with other operating systems. The document also provides a long example lilo.conf file with explanations of each setting.

![CoreLinuxforRedHatandFedoralearningunderGNUFreeDocumentationLicense-Copyleft(c)AcácioOliveira2012
Everyoneispermittedtocopyanddistributeverbatimcopiesofthislicensedocument,changingisallowed
Install a Boot Manager
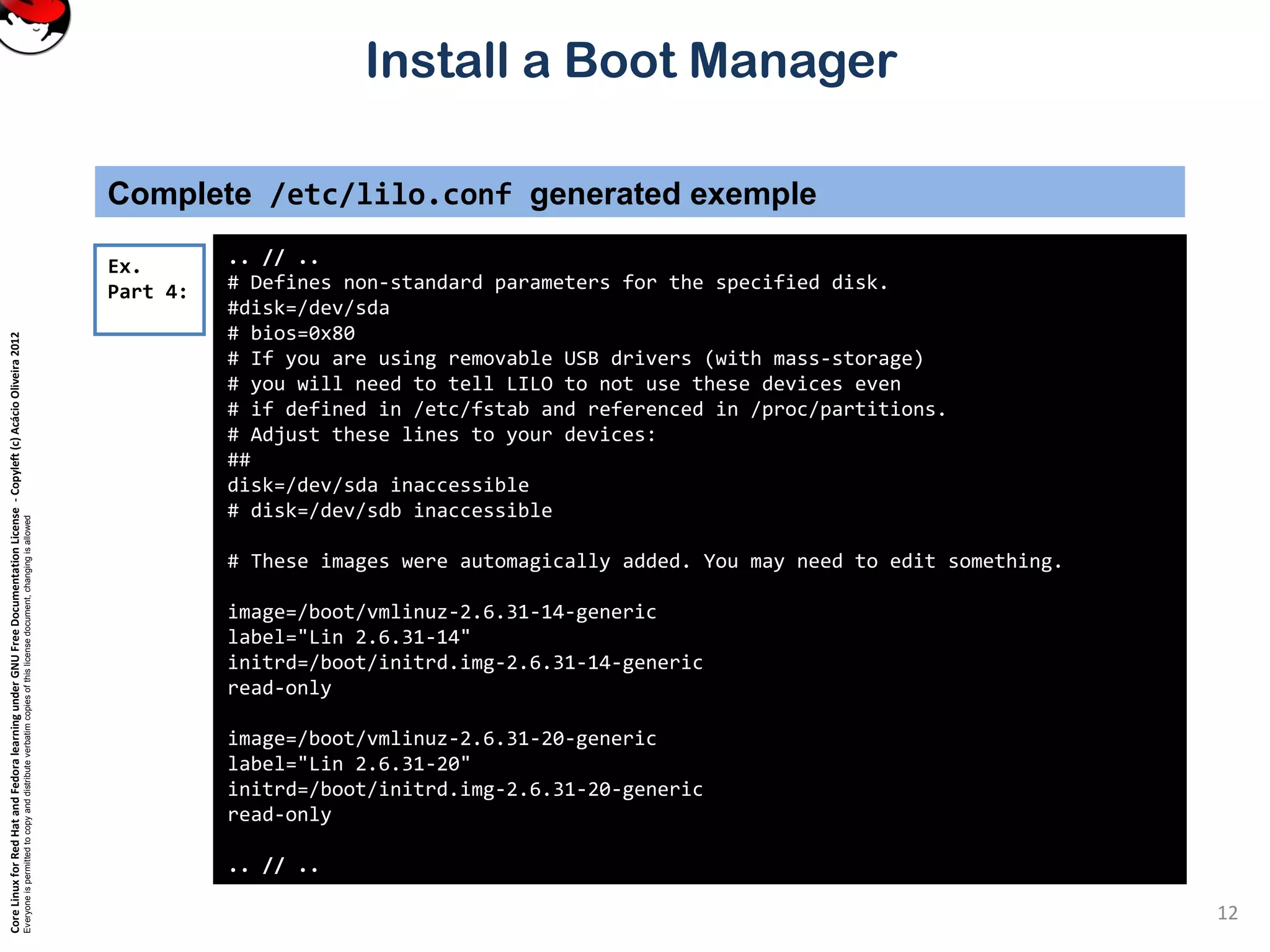
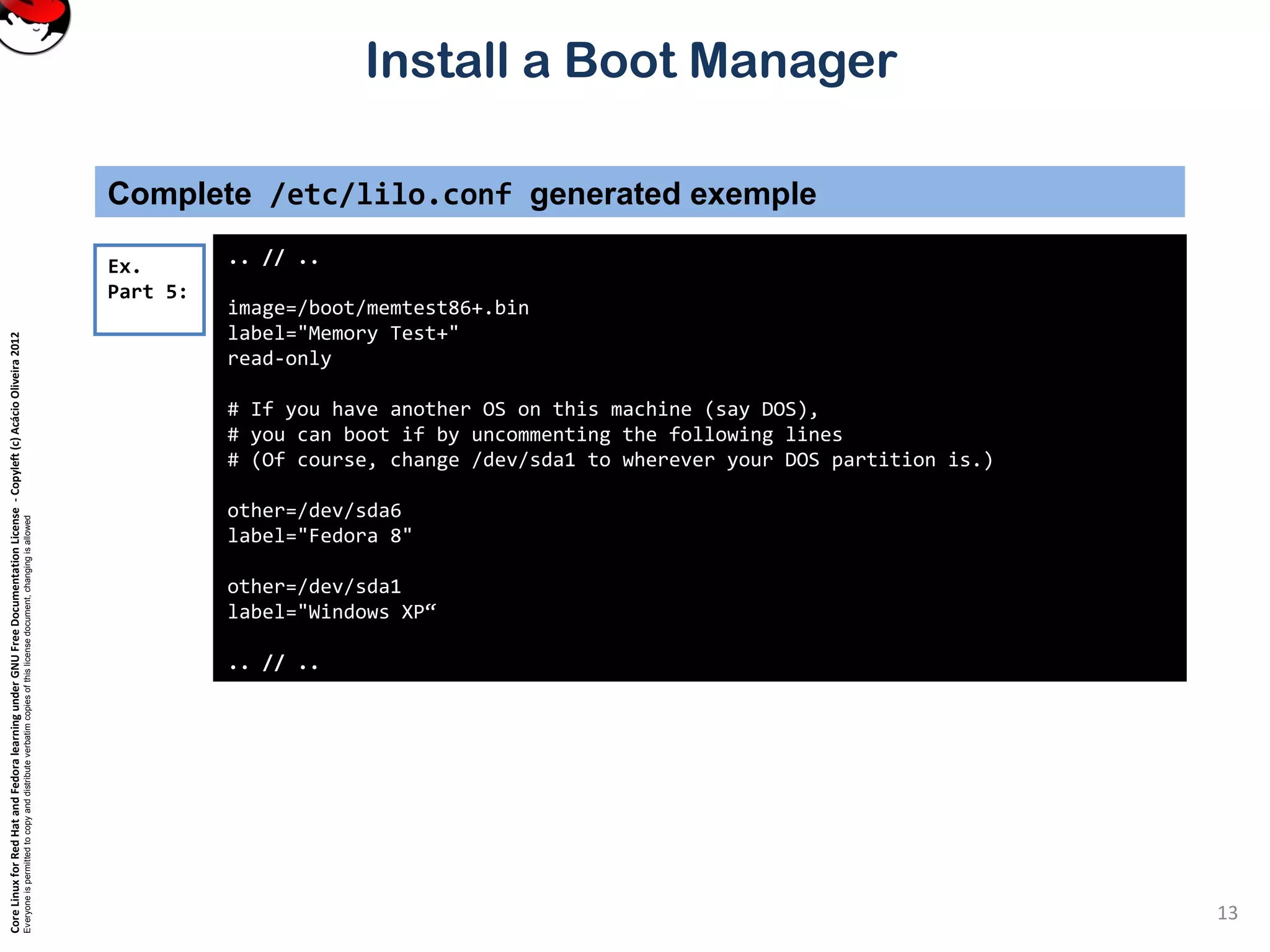
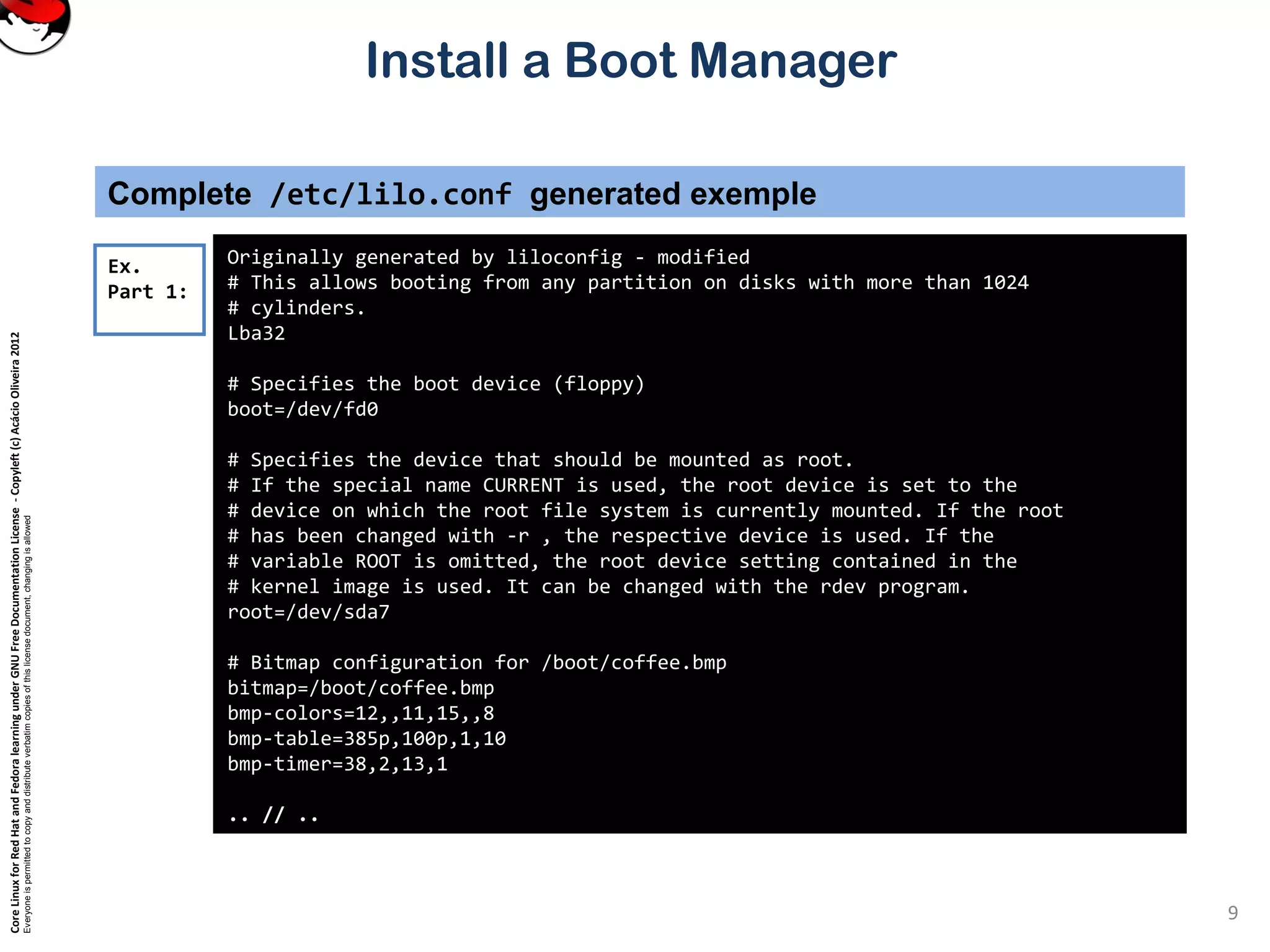
Complete /etc/lilo.conf generated exemple
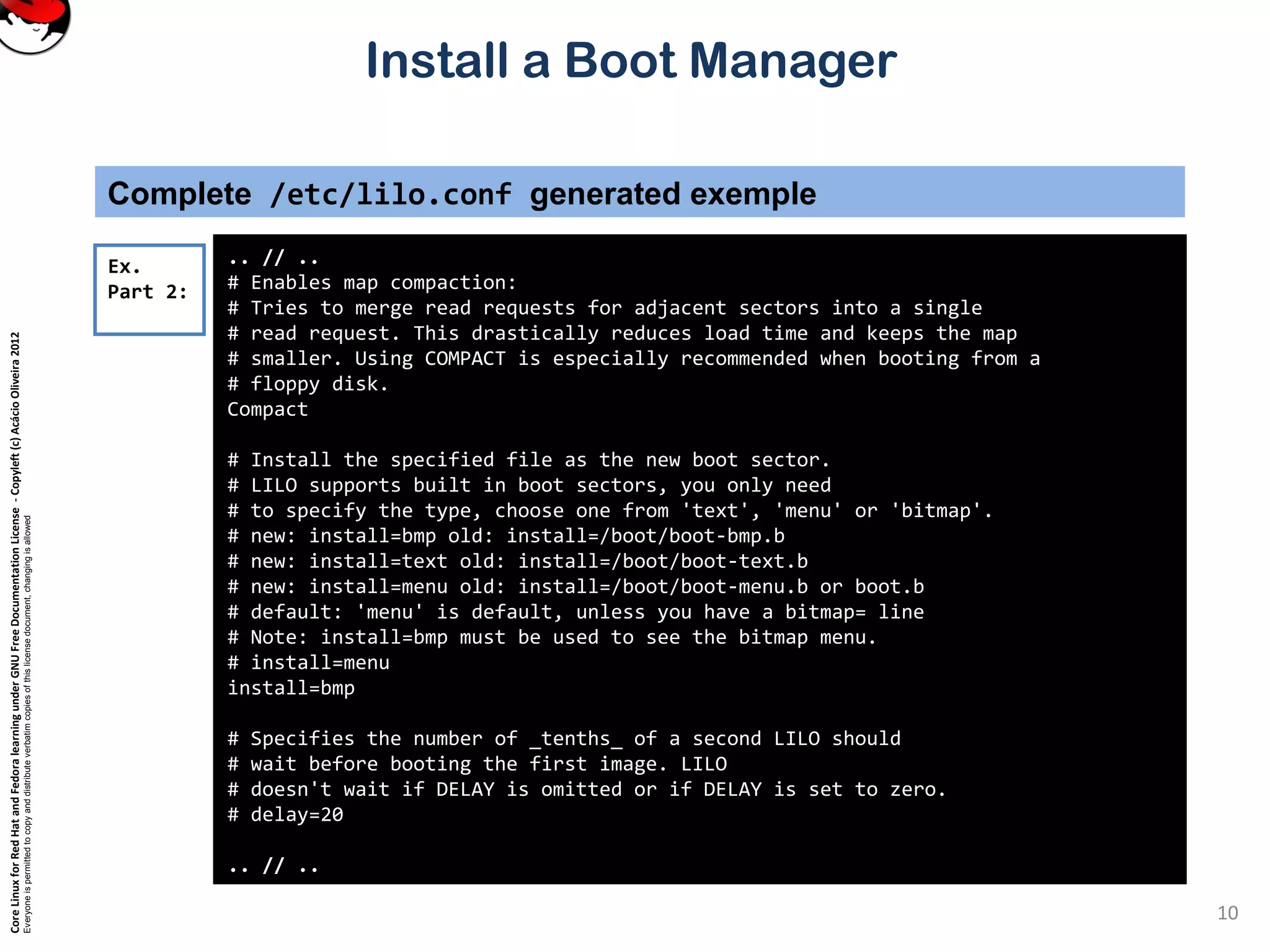
.. // ..
# Prompt to use certain image. If prompt is specified without timeout,
# boot will not take place unless you hit RETURN. Timeout is in tenths of
# a second.
prompt
timeout=200
# Enable large memory mode.
large-memory
# Specifies the location of the map file. If MAP is
# omitted, a file /boot/map is used.
map=/boot/map
# Specifies the VGA text mode that should be selected when
# booting. The following values are recognized (case is ignored):
# NORMAL select normal 80x25 text mode.
# EXTENDED select 80x50 text mode. The word EXTENDED can be
# abbreviated to EXT.
# ASK stop and ask for user input (at boot time).
# <number> use the corresponding text mode. A list of available modes
# can be obtained by booting with vga=ask and pressing [Enter].
vga=normal
.. // ..
Ex.
Part 3:
11](https://image.slidesharecdn.com/odwattmzrh2xwxngdvvl-signature-b02a6c073768d8536fdd50c0a47af6292b168fbd705c8180447bb0b754b59738-poli-141223132228-conversion-gate02/75/101-2-2-install-boot-manager-11-2048.jpg)