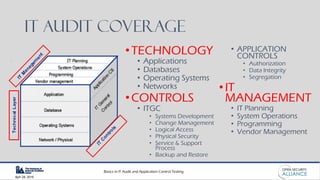
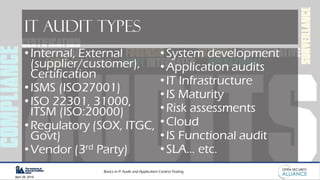
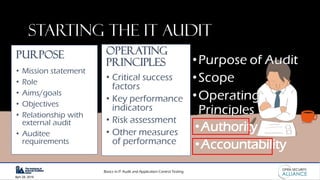
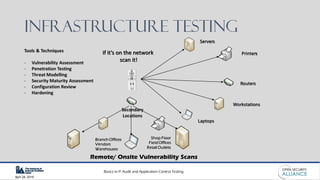
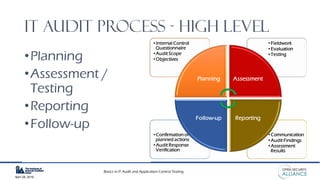
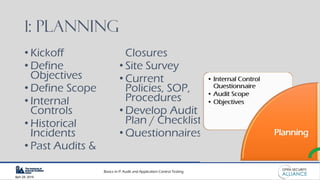
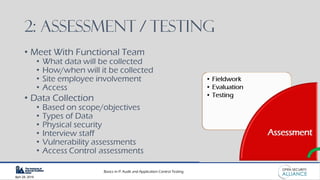
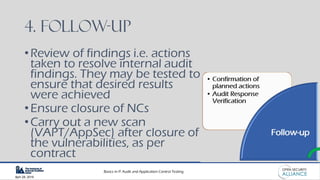
This document is a presentation by Dinesh Bareja on IT audit and application control testing, focusing on essential practices and guidance drawn from the IIA Global Technology Audit Guides. It emphasizes the importance of data protection, risk management, and compliance with standards to ensure security and integrity in IT processes. The document serves as a resource for understanding the scope, types, and steps involved in conducting IT audits.