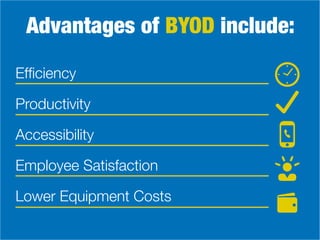
The document discusses the concept of Bring Your Own Device (BYOD) and highlights its advantages such as increased productivity and employee satisfaction, but also mentions potential risks like data breaches. It outlines steps for creating an effective BYOD policy, including defining its purpose, providing training, and establishing access controls. By implementing a BYOD policy, organizations can address security concerns while accommodating employees' desire for familiar technology.