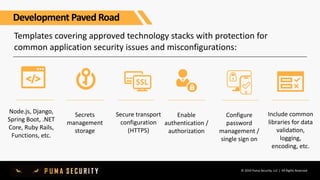
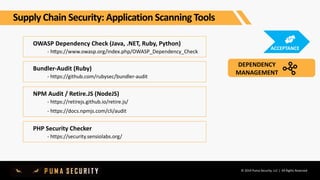
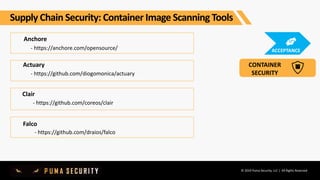
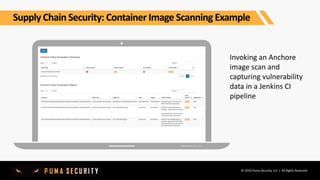
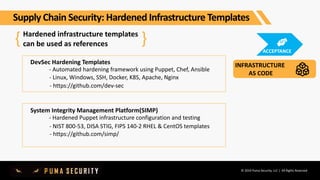
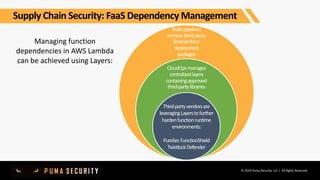
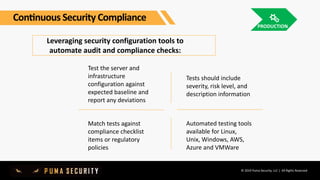
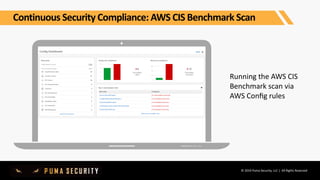
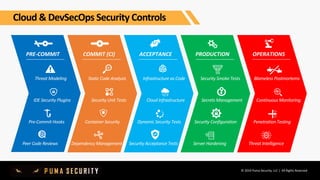
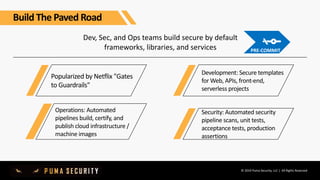
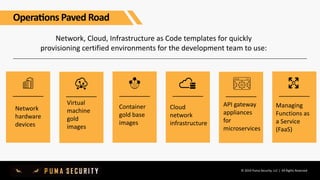
The document outlines key controls and practices for integrating security into DevOps through DevSecOps, emphasizing cloud security and continuous compliance. It discusses various phases such as pre-commit practices, CI/CD security controls, and supply chain security management. Additionally, it highlights tools and techniques for automated security assessments and managing dependencies across development and operational workflows.






![© 2019 Puma Security, LLC | All Rights Reserved
AWS CloudFormation infrastructure paved road example:
1
2
3
4
5
6
7
8
9
10
11
12
13
{ }
LaunchConfiguration:
Type: AWS::AutoScaling::LaunchConfiguration
Metadata:
Properties:
ImageId: !FindInMap [ AWSRegionToAMI, !Ref "AWS::Region", AMI ]
IamInstanceProfile: !Ref InstanceProfile
KeyName: "devsecops"
SecurityGroups:
- !Ref SecurityGroup
UserData:
"Fn::Base64": !Sub |
#!/bin/bash
yum update -y
{ Gold Image }
{ Least privilege }
{ Admin Access }
{ Network configuration }
{ Supply chain security }
Operations Paved Road Example](https://image.slidesharecdn.com/pumasecurity-keystomodernsecuritysuccess-190502142432/85/DevSecOps-Key-Controls-for-Modern-Security-Success-10-320.jpg)