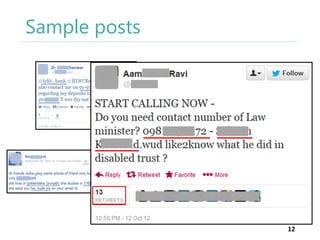
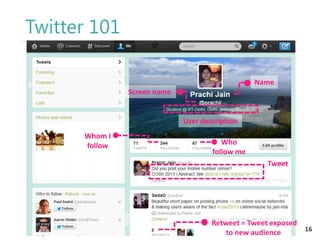
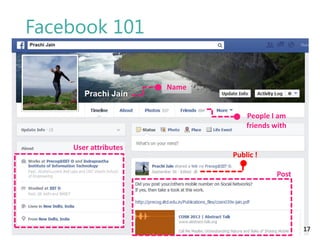
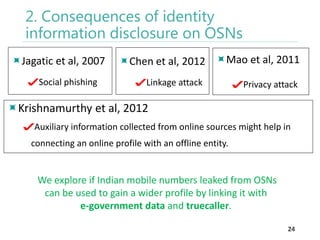
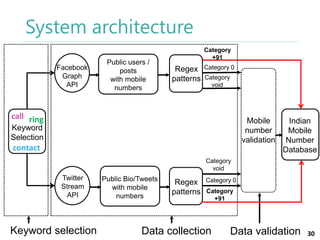
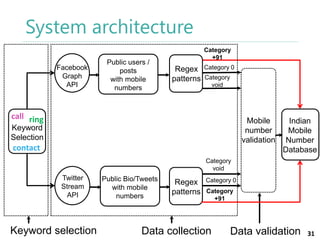
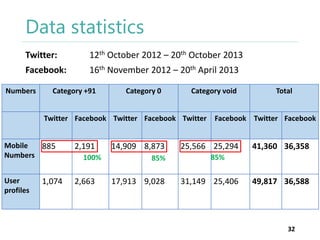
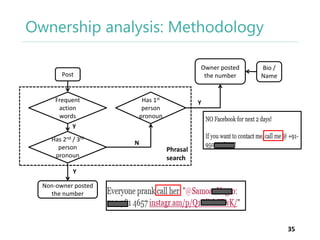
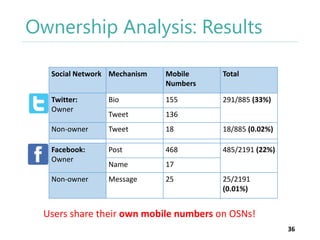
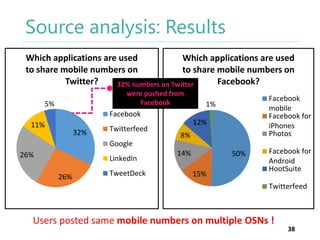
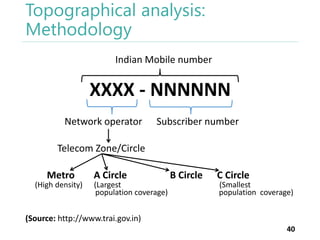
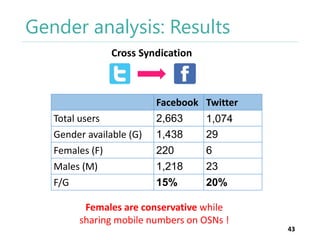
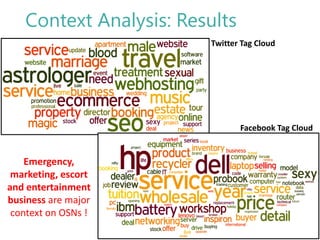
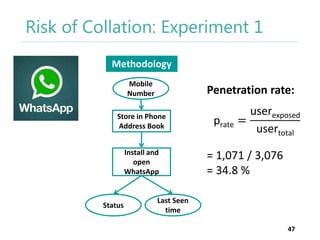
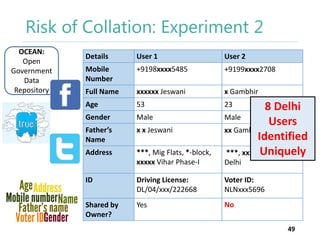
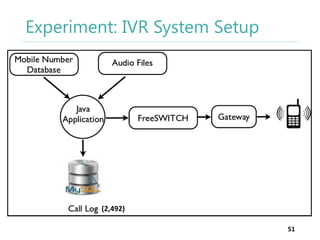
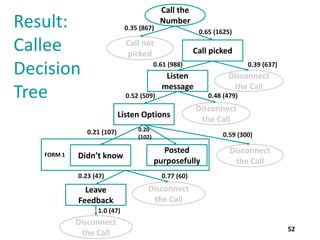
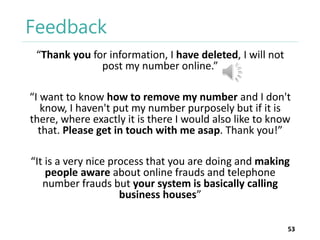
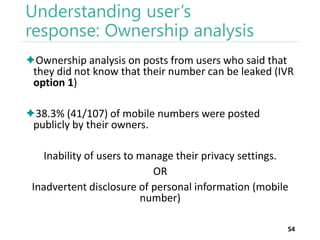
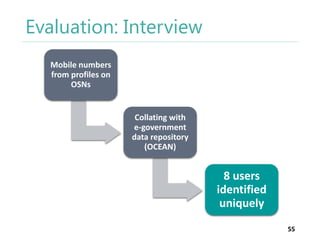
The thesis by Prachi Jain explores mobile number sharing behavior on online social networks, focusing on risks associated with collating owner data from public sources, especially in India. It highlights user-generated content and privacy concerns, noting that users, particularly females, are often unaware of the implications of sharing their mobile numbers publicly. The research proposes a systematic approach to communicate these risks and suggests future technological and awareness strategies to mitigate them.