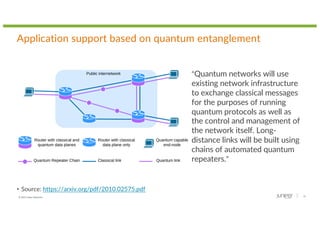
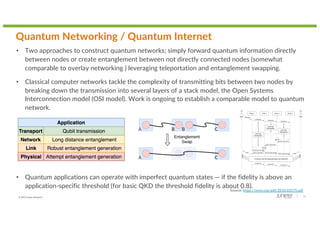
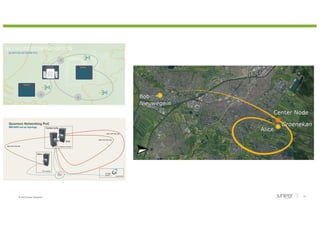
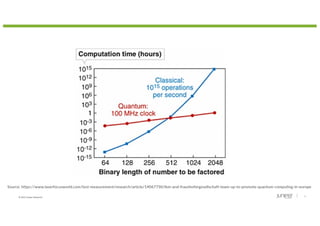
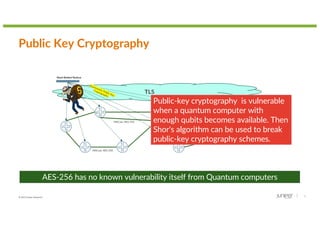
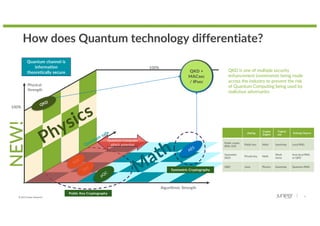
The document discusses the implications of quantum technology on networking, highlighting challenges and advancements in cryptography, specifically addressing vulnerabilities in public key cryptography against quantum attacks using Shor's algorithm. It introduces quantum key distribution (QKD) as a secure method for key exchange, and post-quantum cryptography (PQC) as a promising approach to enhance encryption against future quantum threats. Furthermore, it provides an overview of quantum random number generators and potential applications in various fields, suggesting that a quantum internet may evolve using existing infrastructure for efficient quantum communication.



![© 2022 Juniper Networks 8
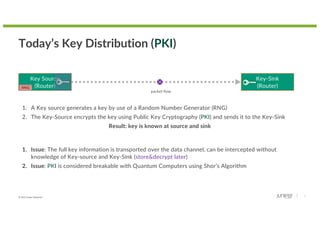
Post Quantum Cryptography (pQC) Key Distribution
1. Issue: [same as today] The full key information is transported over the data channel, can be intercepted without
knowledge of Key-source and Key-Sink (store & much harder to decrypt later)
2. Issue: pQC-PKI is considered resistant against attacks with Quantum Computers using Shor’s algorithm. But there
is no proof that another Algorithm exists that could break the encryption
Key Source
(Router)
Key-Sink
(Router)
packet flow
RNG
1. A Key source generates a key by use of a Random Number Generator (RNG)
2. The Key-Source encrypts the key using pQC-based Public Key Cryptography (PKI) and sends it to the
Key-Sink
Result: key is known at source and sink](https://image.slidesharecdn.com/tracka-04-melchior-juniper-exploringquantumtechnologyfornetworking-220927133253-68257e53/85/Exploring-Quantum-Engineering-for-Networking-by-Melchior-Aelmans-Juniper-Networks-8-320.jpg)
![© 2022 Juniper Networks 9
Quantum Key Distribution (QKD)
QKD-A QKD-B
Quantum Channel
Dark fiber or Satellite
1. Quantum Key Distribution enables two distant devices connected with a Quantum Channel to “distill”
the same information on both devices
Result: key is known at source and sink
1. Advantage: cannot be broken even if the adversary has unlimited computing power. The distribution
mechanism is proven to be information theoretic secure [Wikipedia]
• Quantum state cannot be intercepted without changing it’s state and is detectable
• Quantum state decays fast. It cannot be stored for a long time to decrypt it later
Router Router](https://image.slidesharecdn.com/tracka-04-melchior-juniper-exploringquantumtechnologyfornetworking-220927133253-68257e53/85/Exploring-Quantum-Engineering-for-Networking-by-Melchior-Aelmans-Juniper-Networks-9-320.jpg)
![© 2022 Juniper Networks 10
Quick Intro: Quantum Communication by dummies
• Quantum state of individual photons is any
fraction between 0 and 1
• Photons can be split into two photons jointly
maintaining the properties of the original
photon. P0 = 1 à (p1 + p2) = 1
• The state of photons is unknown until
measured: p1 =?, p2 =?
• Measurement of one photon ‘collapses’ the
state of both: Measuring p1 = 0.3 causes p2 =
0.7 [Remember: (p1 + p2) = 1 ]
• If we measure the state of a photon and know
that it was entangled, the state of the other
photon is known.](https://image.slidesharecdn.com/tracka-04-melchior-juniper-exploringquantumtechnologyfornetworking-220927133253-68257e53/85/Exploring-Quantum-Engineering-for-Networking-by-Melchior-Aelmans-Juniper-Networks-10-320.jpg)