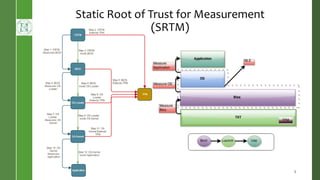
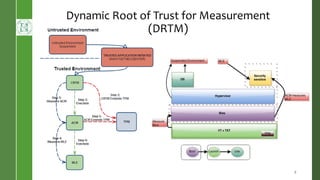
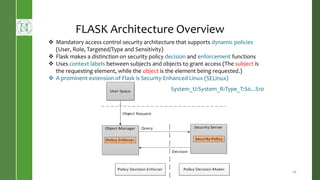
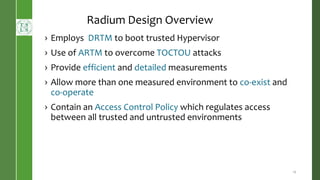
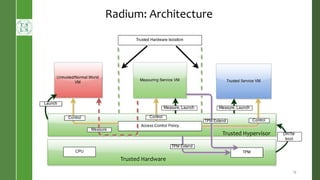
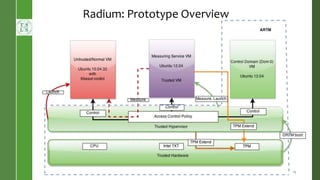
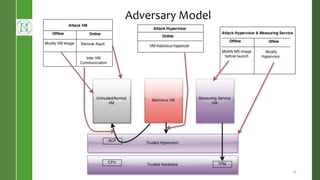
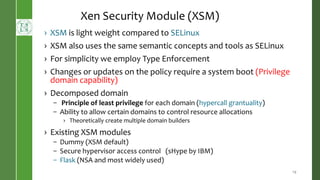
This document presents Radium, a secure policy engine in the hypervisor that aims to provide integrity measurement of computing environments. It discusses defining the problem of trusting computing devices and components. It provides background on technologies like SRTM, DRTM and Flask that are used. The Radium architecture employs DRTM to boot a trusted hypervisor and uses asynchronous root of trust for measurement and a secure mandatory access control policy to regulate access between trusted and untrusted environments. The prototype implementation and evaluation show Radium can provide timely integrity measurements with zero downtime compared to traditional trusted systems. Future work areas include incorporating Intel SGX and improving the minimal trusted computing base of the hypervisor.