Embed presentation
Download as PDF, PPTX

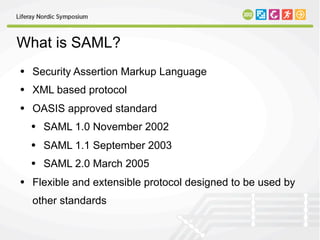

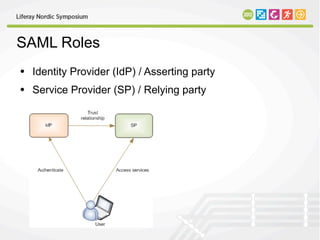





This document discusses SAML (Security Assertion Markup Language), an XML-based standard for exchanging authentication and authorization data between security domains. It describes SAML's advantages like platform neutrality and loose directory coupling. The document also outlines how Liferay supports SAML through an enterprise edition plugin, allowing single sign-on between Liferay and other applications. Key features of the Liferay SAML plugin include identity provider and service provider modes as well as IdP-initiated and SP-initiated single logout.










