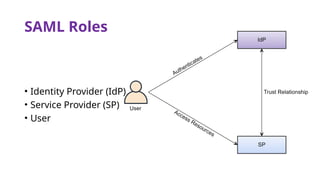
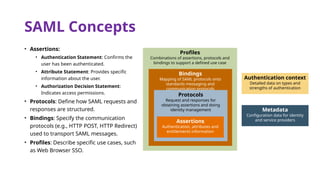
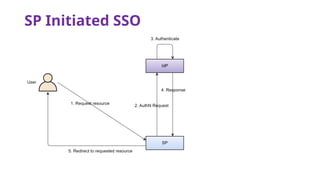
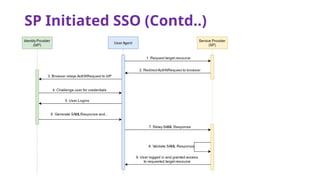
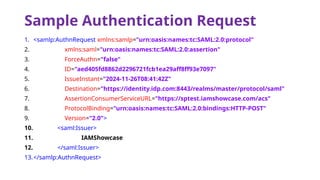
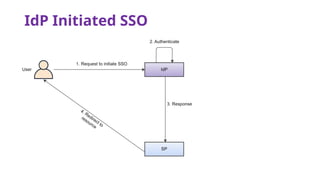
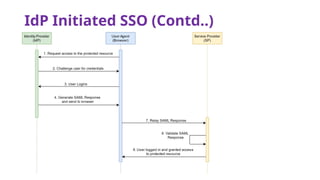
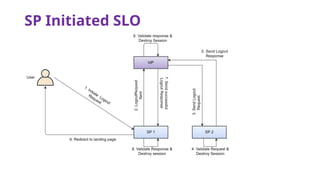
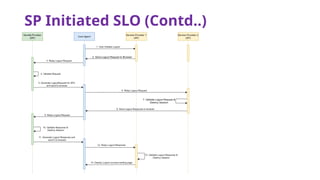
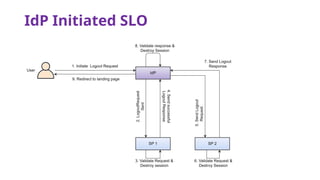
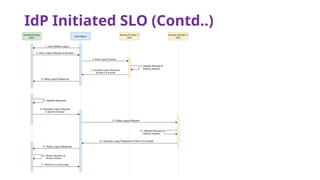
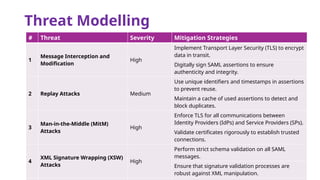
The document provides an overview of SAML 2.0, focusing on its components, workflow, and security considerations for implementing single sign-on (SSO) solutions. It highlights key aspects such as assertions, protocols, bindings, and the roles of identity and service providers. The document also details setup steps for SAML-based SSO, example assertions, security measures, and threat modeling strategies.