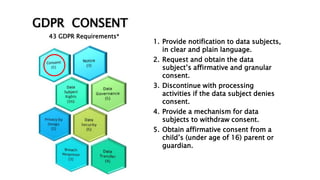
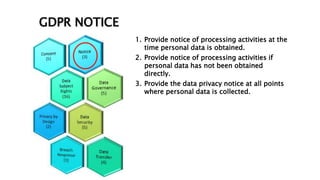
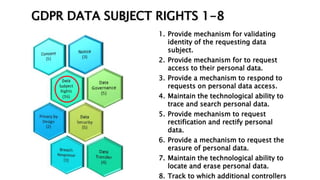
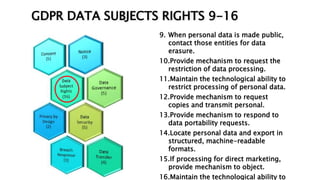
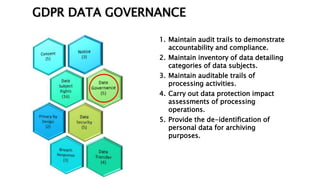
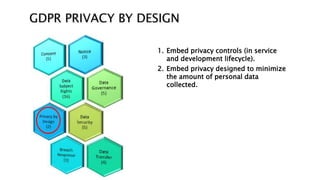
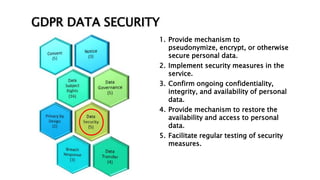
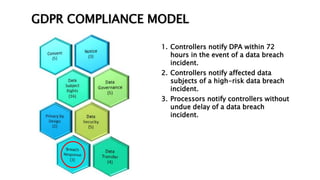
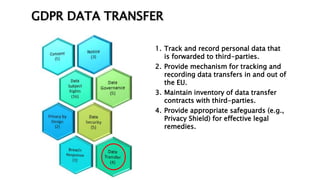
This document provides an overview of the General Data Protection Regulation (GDPR) and outlines steps for compliance. It begins with a disclaimer about the information provided. It then lists resources for learning more about the GDPR and its 99 articles and 173 recitals. The rest of the document outlines key aspects of GDPR compliance, including identifying high and critical risk data, privacy notices, individual rights and redress, lawful and fair processing, privacy by design, data security, and data transfers.