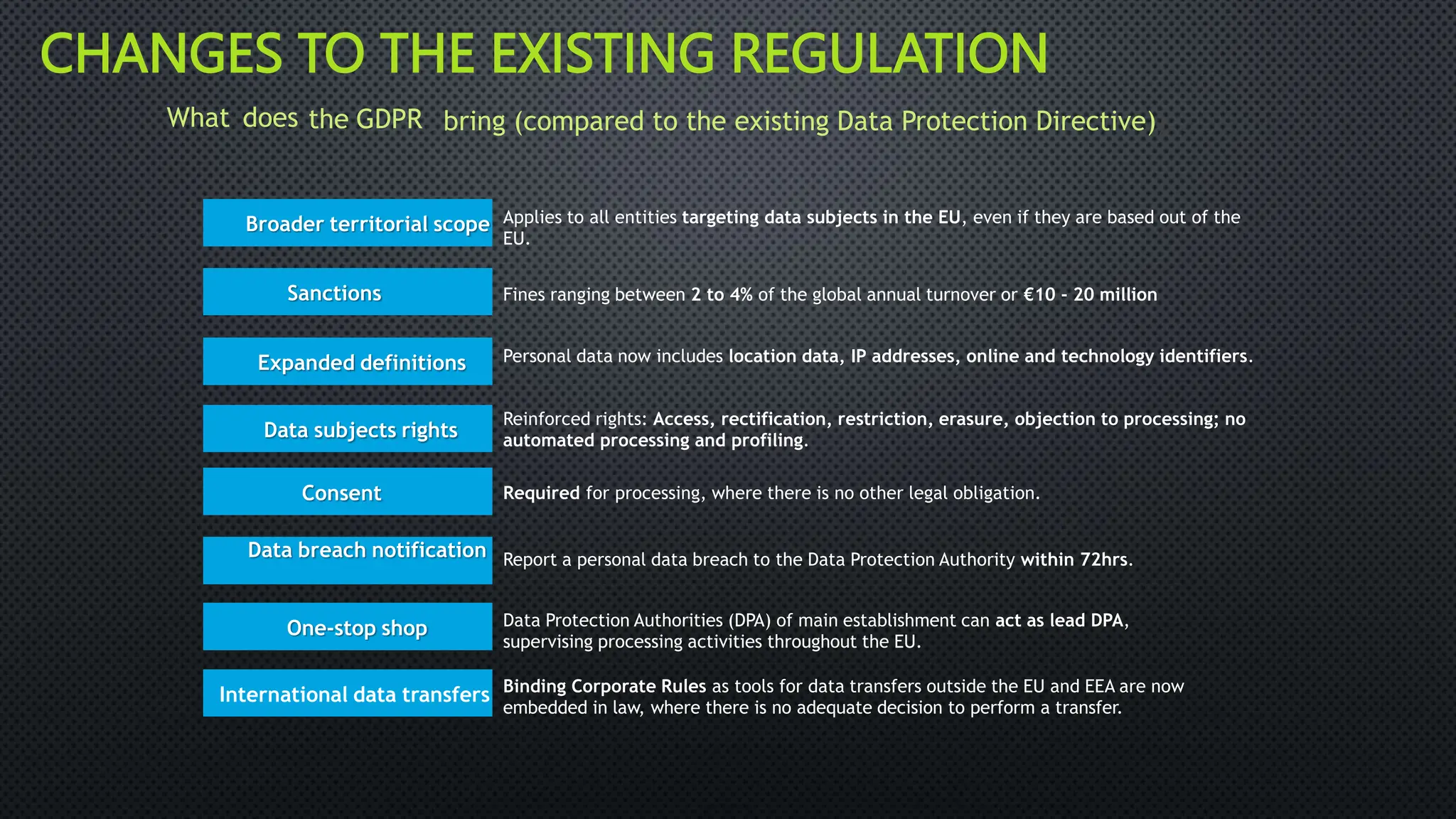
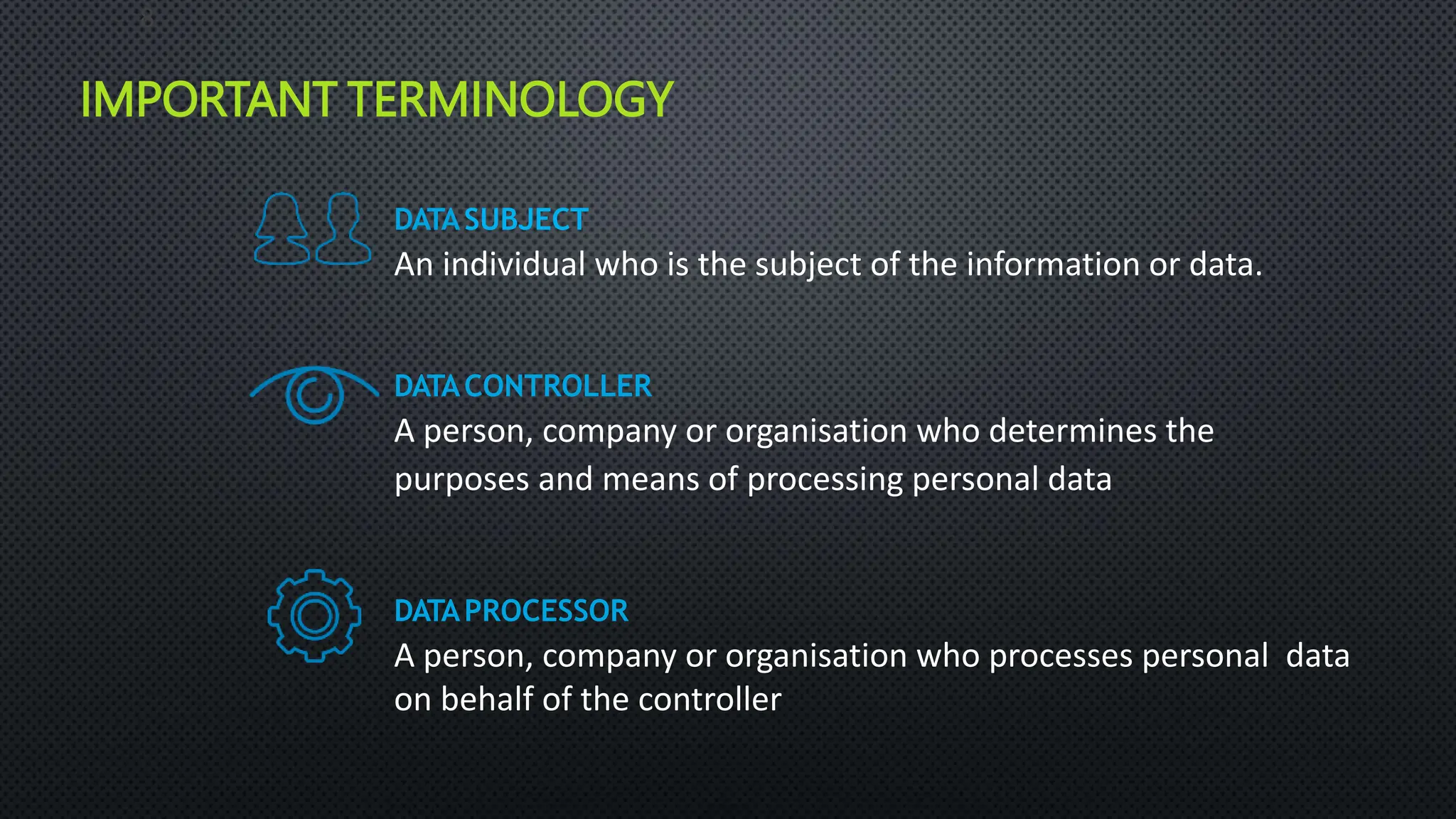
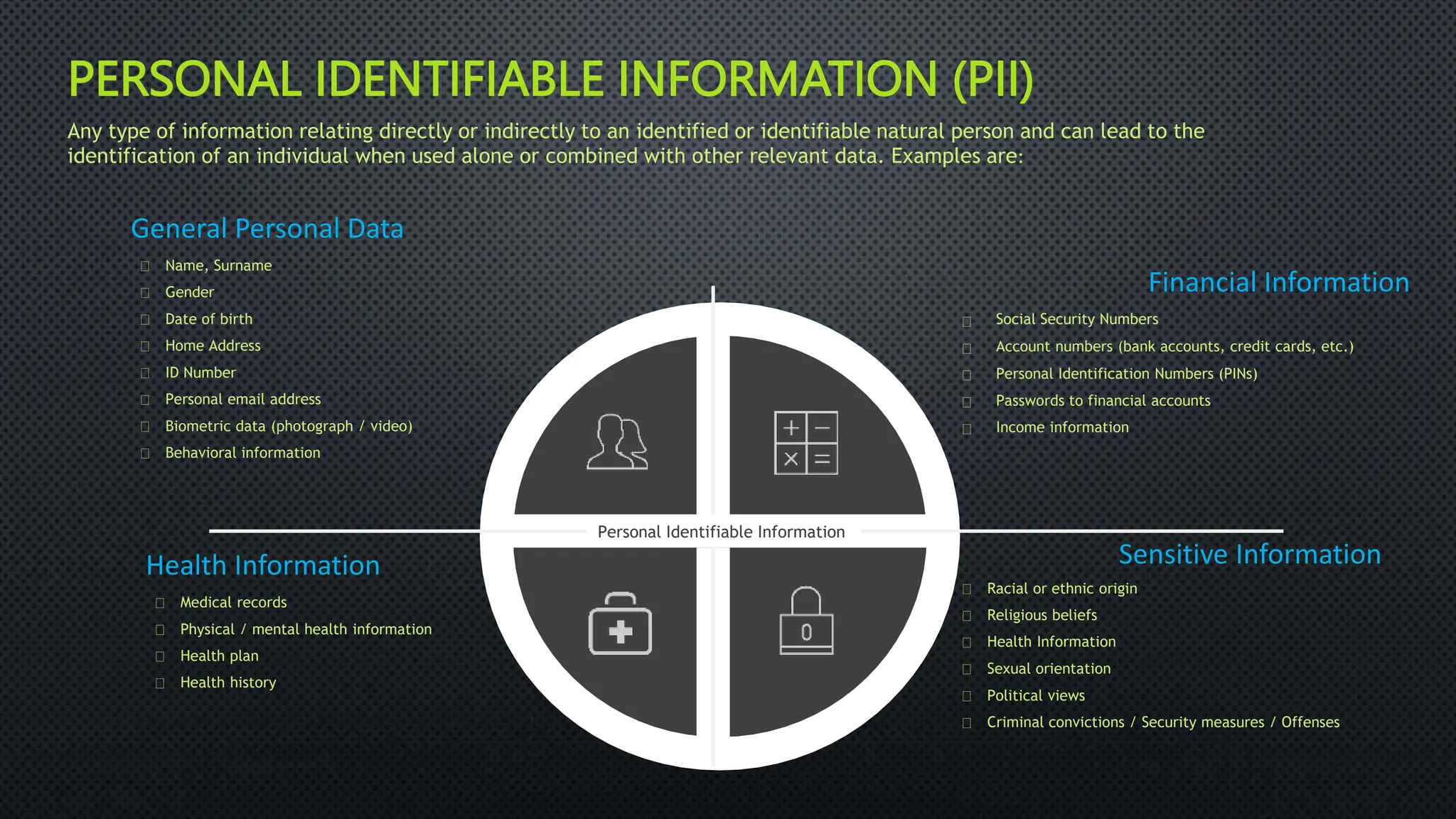
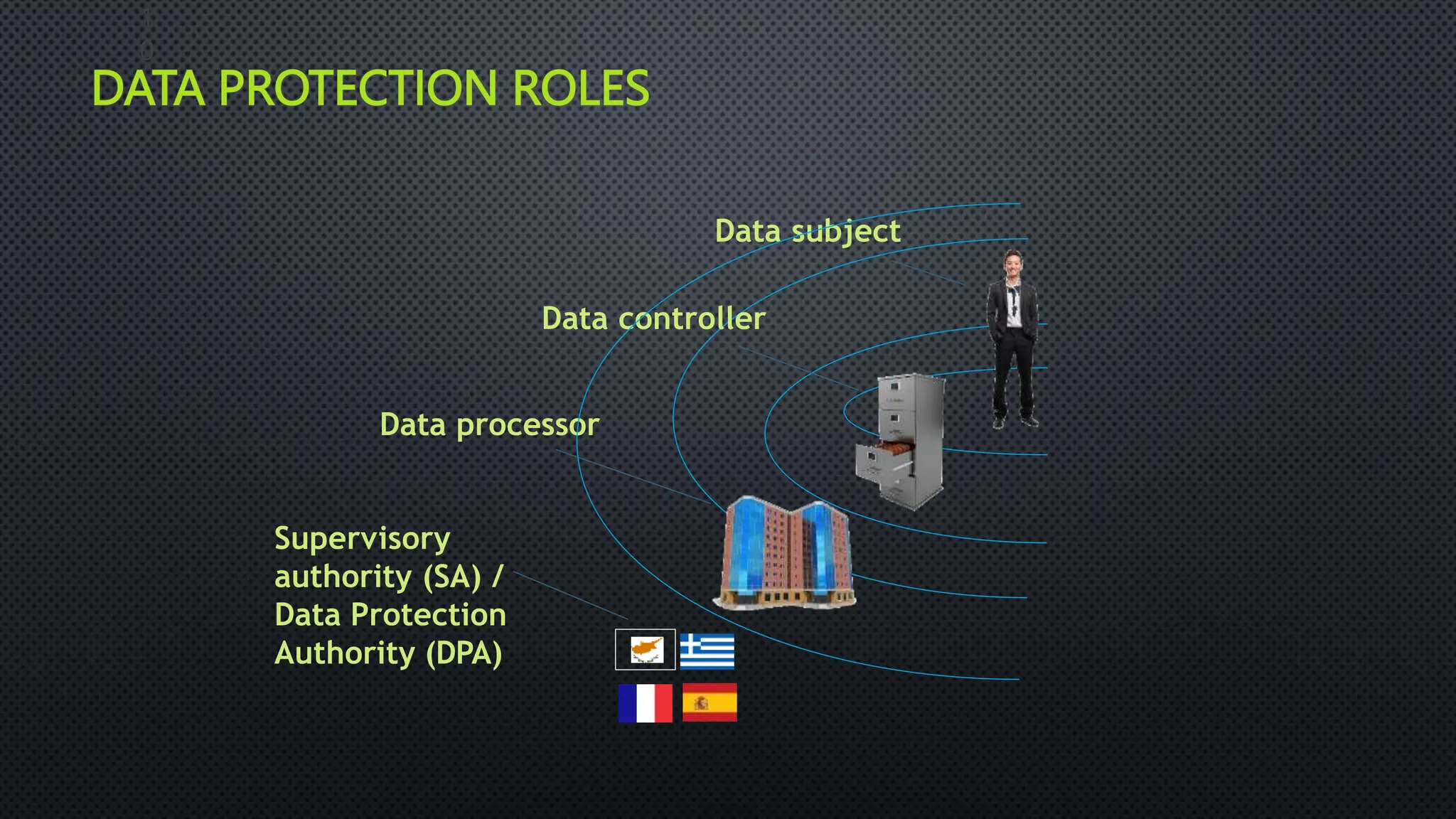
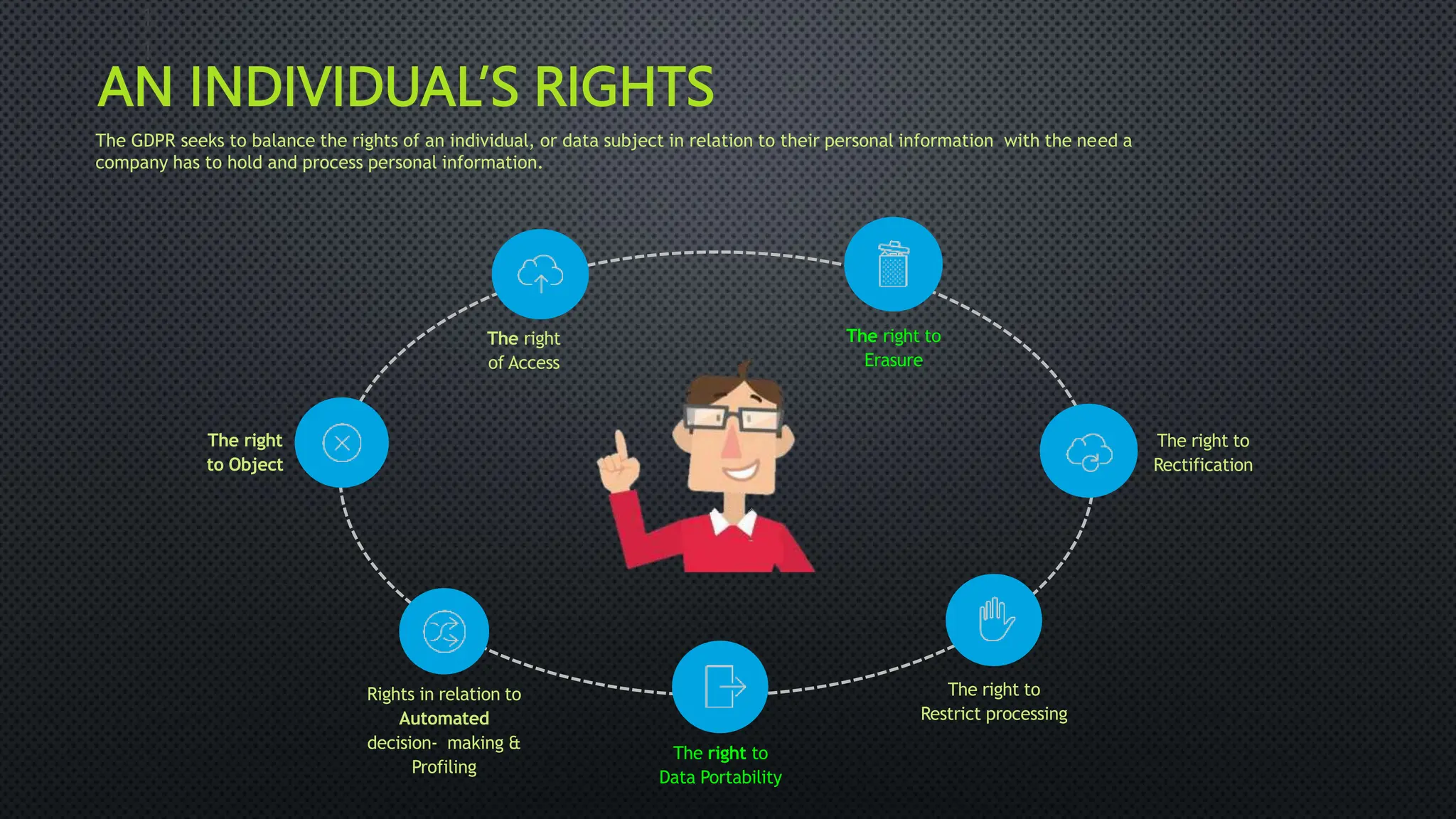
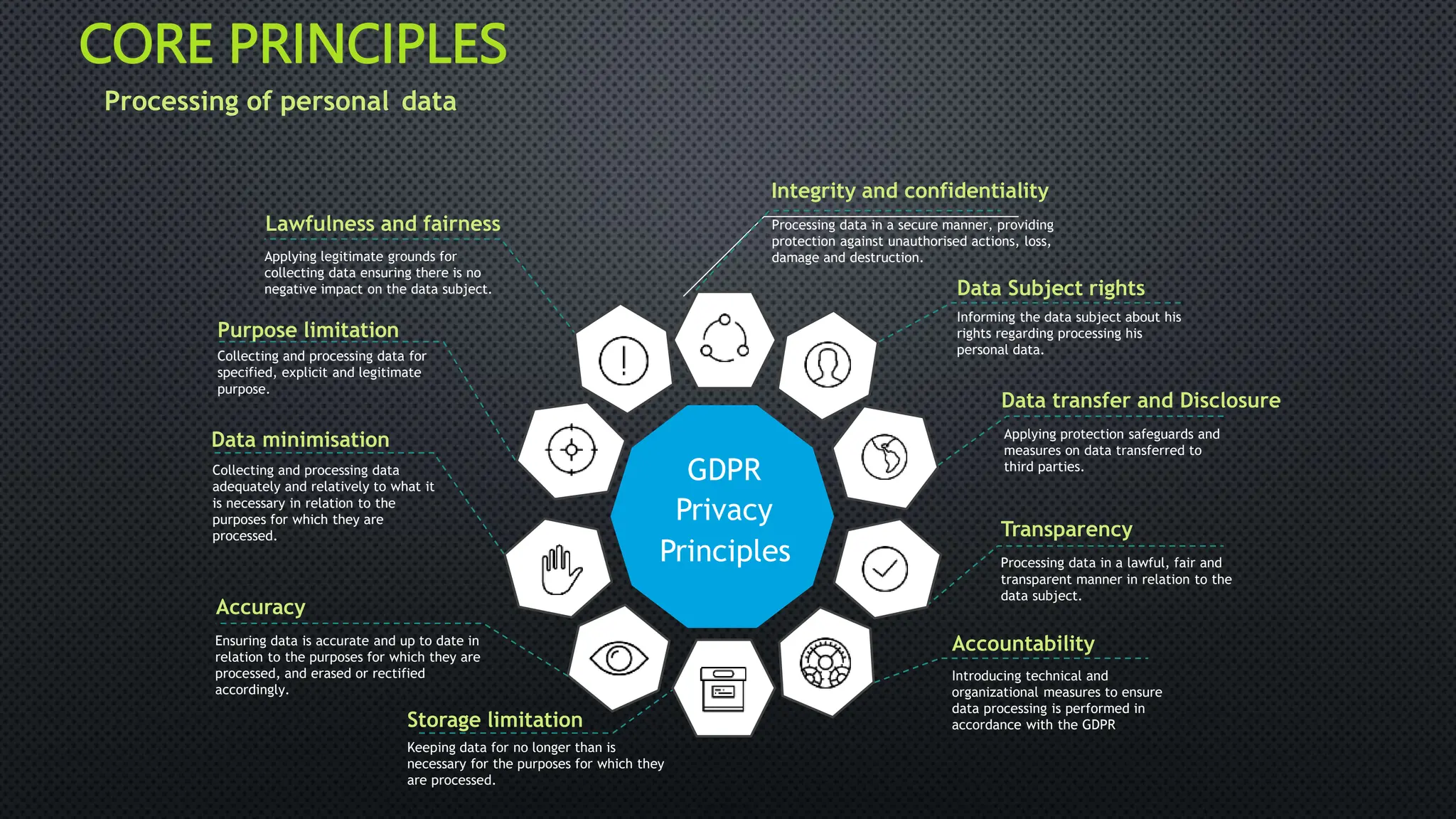
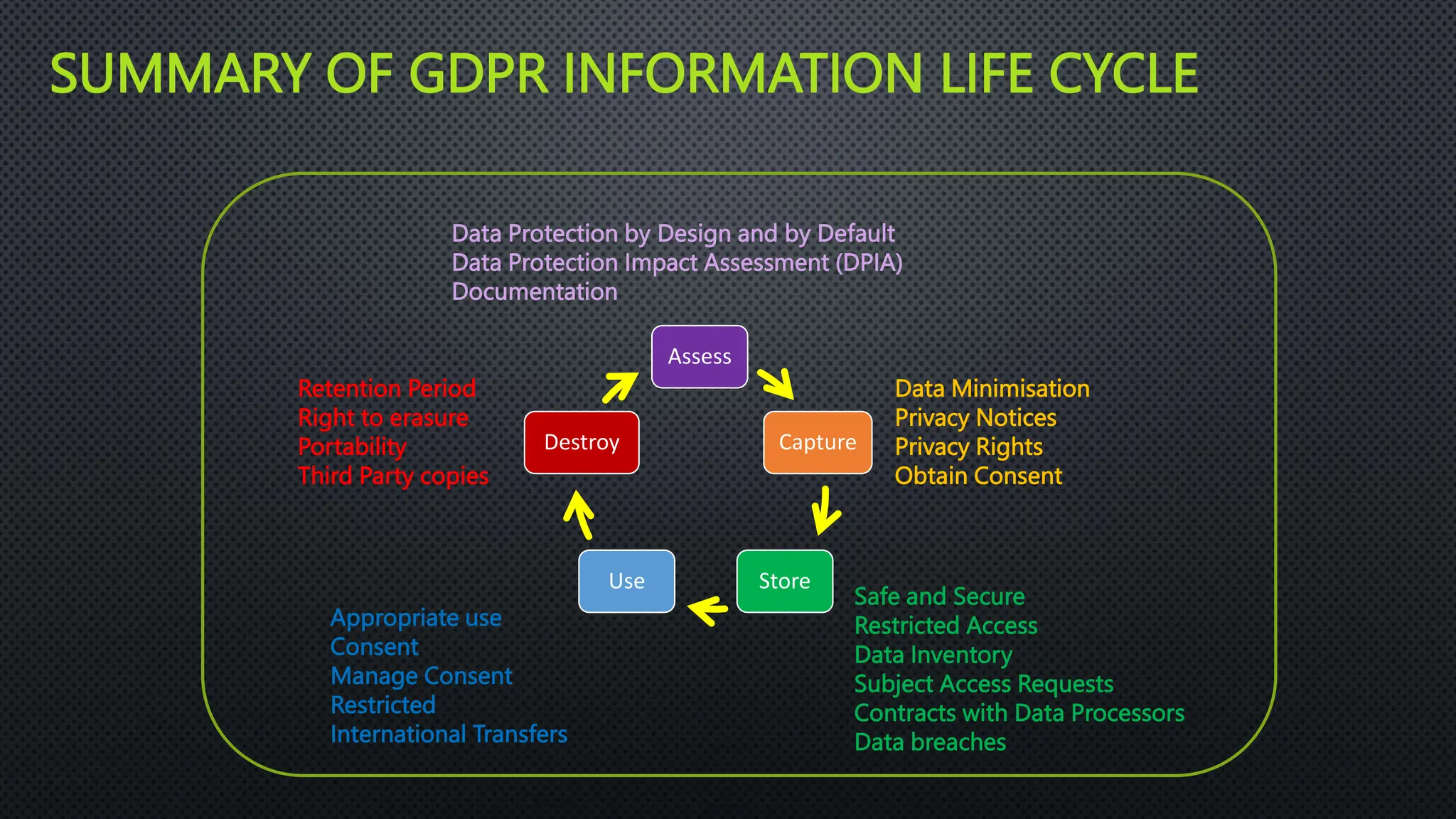
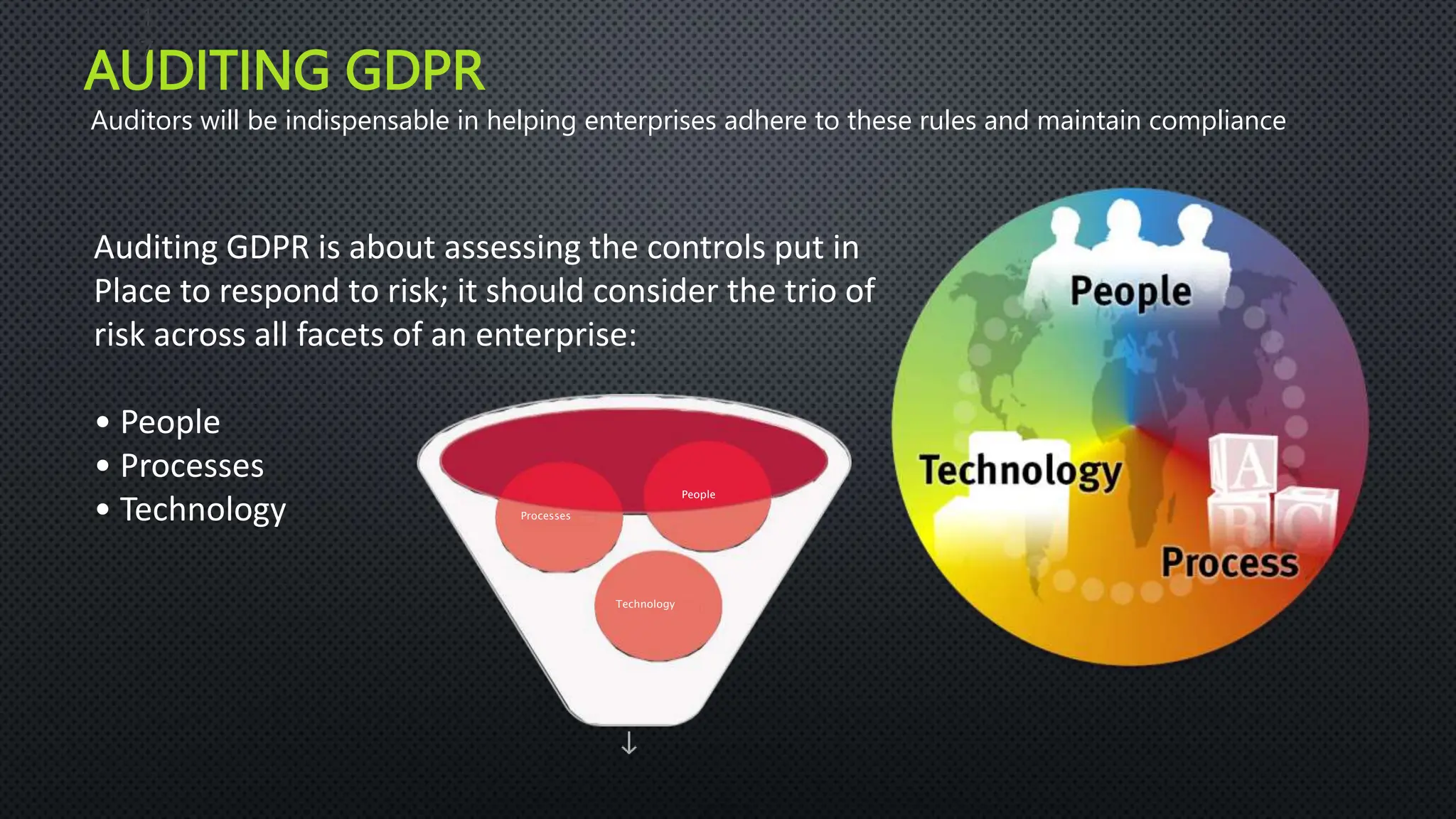
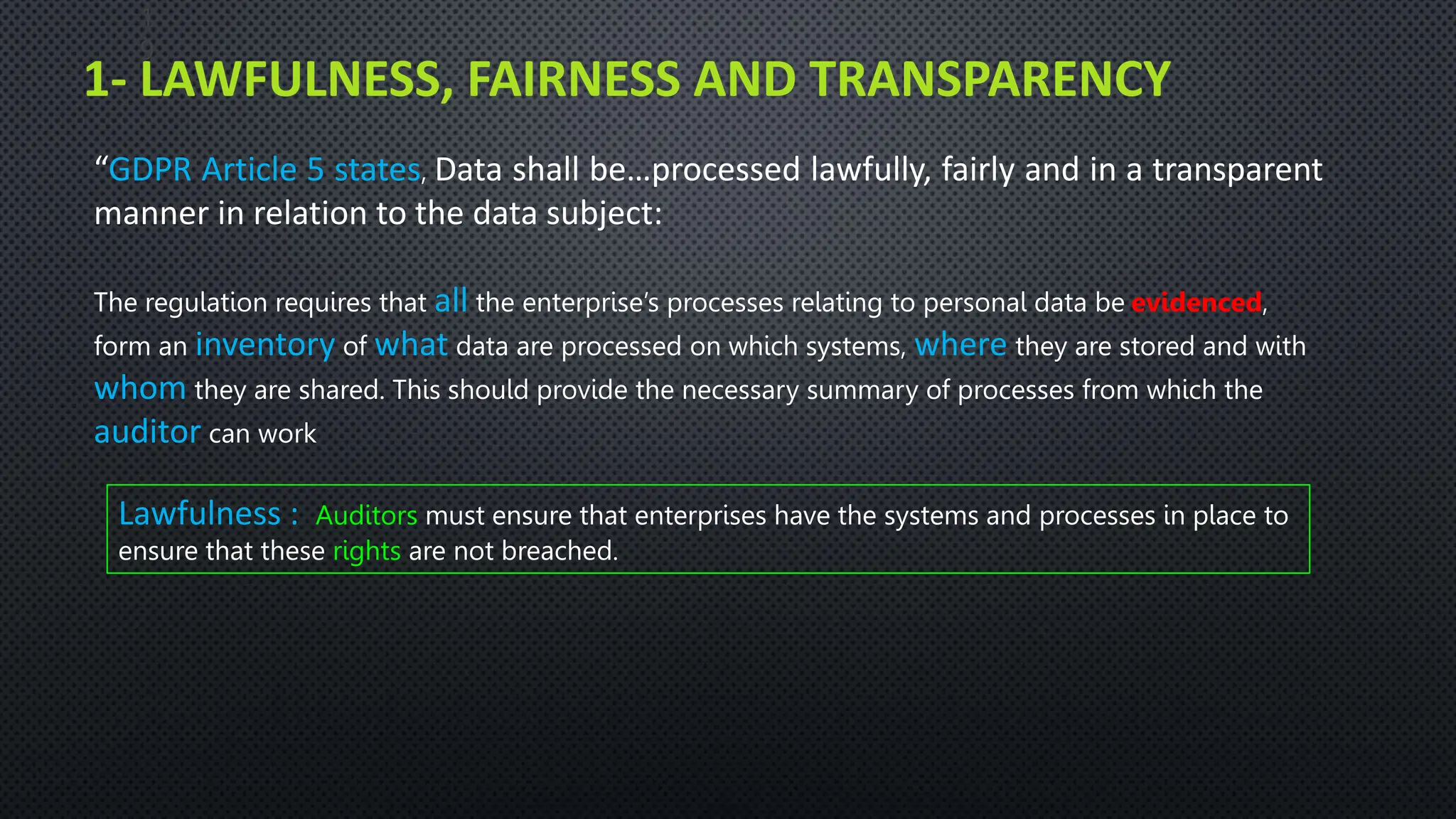
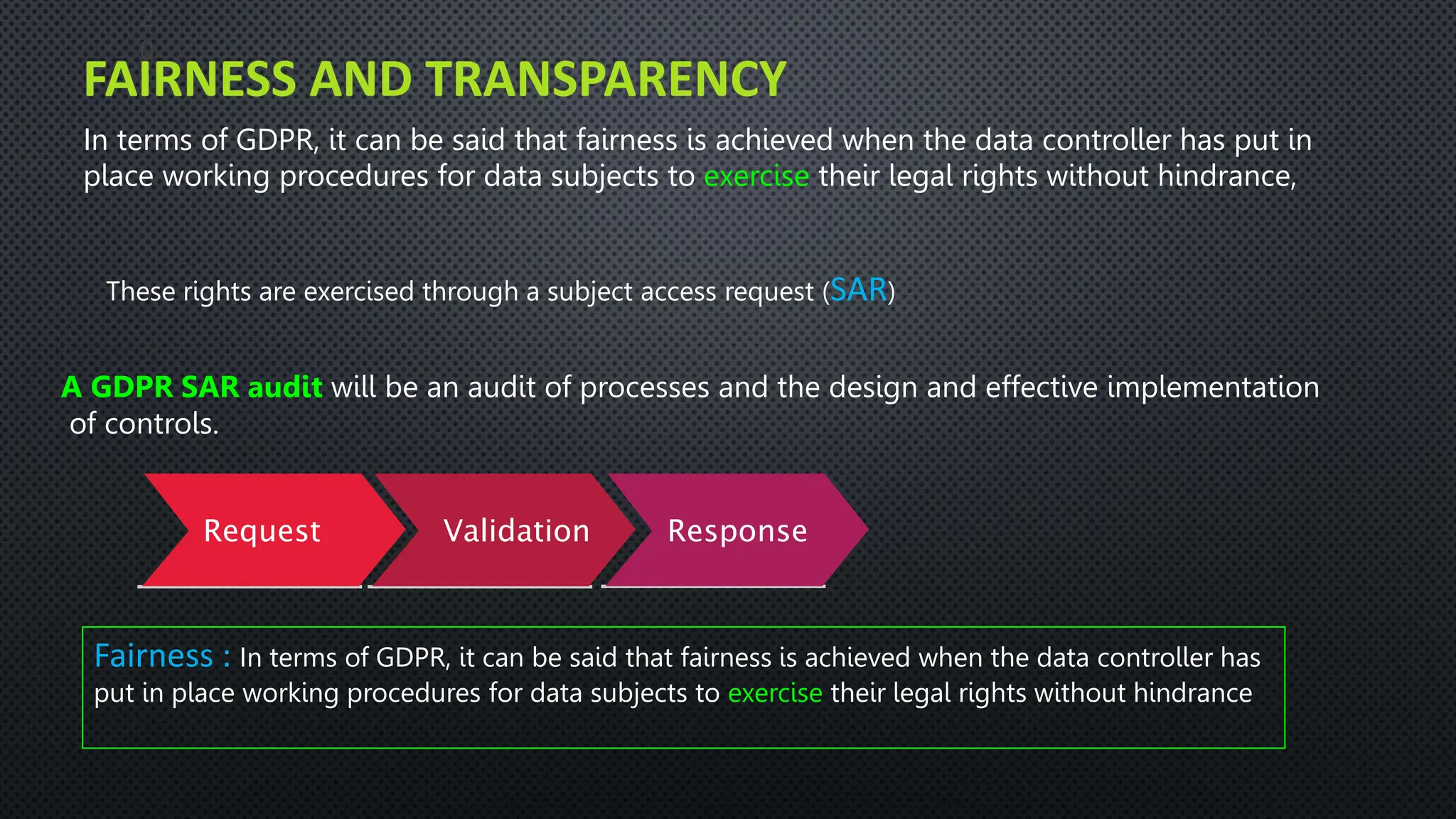
The document outlines the General Data Protection Regulation (GDPR), which aims to enhance data protection for individuals within the EU by establishing standardized data protection laws. It details the rights of data subjects, the responsibilities of data controllers and processors, and the principles and requirements for lawful data processing, including the need for consent, transparency, and security measures. The document also discusses the implementation of GDPR compliance measures, penalties for violations, and the auditing process necessary to ensure adherence to the regulation.