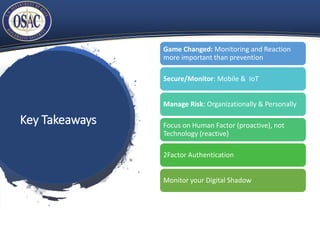
The document provides an overview of cybersecurity trends in 2018 and predictions for 2019, highlighting a significant increase in cyberattacks, particularly through phishing and social engineering methods. Key recommendations include enhancing monitoring and risk management practices, focusing on the human factor in cybersecurity, and the implementation of multi-factor authentication. It also offers actionable steps for improving online safety and resources for further training and tools.


![Looking Back 2018
• A hacker attack every
39 seconds
• 62% of Org had
phishing & social
engineering
• [Since 2013]
3,809,448 records
stolen every day
158,727 per hour 2,645
per minute
• 2018 Billions impacted
by breaches](https://image.slidesharecdn.com/idwgbimonthlysecurityexchange-cyberonlysection-190125211843/85/Idwg-bimonthly-security-exchange-cyber-only-section-3-320.jpg)