poster on biometrics
•Download as PPTX, PDF•
1 like•1,581 views
poster presentation on biometrics..
Report
Share
Report
Share
More Related Content
What's hot (20)
Fingerprint recognition system by sagar chand gupta

Fingerprint recognition system by sagar chand gupta
Viewers also liked
Viewers also liked (14)
A completed modeling of local binary pattern operator

A completed modeling of local binary pattern operator
Similar to poster on biometrics
Similar to poster on biometrics (20)
Biometrics clear presentation by Adduri kalyan(AK)

Biometrics clear presentation by Adduri kalyan(AK)
HW 11. List the main modules of a biometric system.A) Sensor M

HW 11. List the main modules of a biometric system.A) Sensor M
Introduction to Biometric lectures... Prepared by Dr.Abbas

Introduction to Biometric lectures... Prepared by Dr.Abbas
Recently uploaded
Recently uploaded (20)
Streamlining Python Development: A Guide to a Modern Project Setup

Streamlining Python Development: A Guide to a Modern Project Setup
08448380779 Call Girls In Diplomatic Enclave Women Seeking Men

08448380779 Call Girls In Diplomatic Enclave Women Seeking Men
Unblocking The Main Thread Solving ANRs and Frozen Frames

Unblocking The Main Thread Solving ANRs and Frozen Frames
Automating Business Process via MuleSoft Composer | Bangalore MuleSoft Meetup...

Automating Business Process via MuleSoft Composer | Bangalore MuleSoft Meetup...
Unlocking the Potential of the Cloud for IBM Power Systems

Unlocking the Potential of the Cloud for IBM Power Systems
Injustice - Developers Among Us (SciFiDevCon 2024)

Injustice - Developers Among Us (SciFiDevCon 2024)
"LLMs for Python Engineers: Advanced Data Analysis and Semantic Kernel",Oleks...

"LLMs for Python Engineers: Advanced Data Analysis and Semantic Kernel",Oleks...
Unleash Your Potential - Namagunga Girls Coding Club

Unleash Your Potential - Namagunga Girls Coding Club
Vulnerability_Management_GRC_by Sohang Sengupta.pptx

Vulnerability_Management_GRC_by Sohang Sengupta.pptx
Transcript: New from BookNet Canada for 2024: BNC BiblioShare - Tech Forum 2024

Transcript: New from BookNet Canada for 2024: BNC BiblioShare - Tech Forum 2024
Artificial intelligence in the post-deep learning era

Artificial intelligence in the post-deep learning era
poster on biometrics
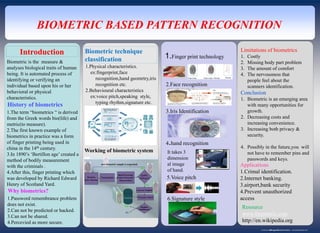
- 1. www.postersession.com BIOMETRIC BASED PATTERN RECOGNITION Introduction 1.The term “biometrics “ is derived from the Greek words bio(life) and metric(to measure). 2.The first known example of biometrics in practice was a form of finger printing being used in china in the 14th century. 3.In 1890’s ‘Bertillon age’ created a method of bodily measurement with the criminals . 4.After this, finger printing which was developed by Richard Edward Henry of Scotland Yard. History of biometrics Why biometrics? 1.Password remembrance problem does not exist. 2.Can not be predicted or hacked. 3.Can not be shared. 4.Percevied as more secure. Biometric is the measure & analyses biological traits of human being. It is automated process of identifying or verifying an individual based upon his or her behavioral or physical characteristics. Biometric technique classification 1.Physical characteristics. ex:fingerprint,face recognition,hand geomrtry,iris recognition etc. 2.Behavioural characteristics ex:voice pitch,speaking style, typing rhythm,signature etc. Working of biometric system 1.Finger print technology 2.Face recognition 3.Iris Identification 4.hand recognition It takes 3 dimension al image of hand. 5.Voice pitch 6.Signature style Limitations of biometrics 1. Costly 2. Missing body part problem 3. The amount of comfort 4. The nervousness that people feel about the scanners identification. Conclusion 1. Biometric is an emerging area with many opportunities for growth. 2. Decreasing costs and increasing convenience. 3. Increasing both privacy & security. 4. Possibly in the future,you will not have to remember pins and passwords and keys. Applications 1.Crimal identification. 2.Internet banking. 3.airport,bank security 4.Prevent unauthorized access Resource www.biometric.com http://en.wikipedia.org